vulnhub靶机渗透[Tr0ll-1]
名称
名称:Tr0ll: 1
发布日期:2014年8月14日
下载
- Download: http://overflowsecurity.com/files/Tr0ll.rar
- Download (Mirror): https://download.vulnhub.com/tr0ll/Tr0ll.rar
- Download (Torrent): https://download.vulnhub.com/tr0ll/Tr0ll.rar.torrent
描述
Tr0ll的灵感来自OSCP实验室中不断摇曳的机器。目标很简单,获得root权限并从/ root目录获取Proof.txt。不为容易受挫!公平警告,前方有巨魔!难度:初学者类型:boot2root
特别感谢@ OS_Eagle11和@superkojiman自始至终经历了测试!本机应使用DHCP提取IP,如果有任何问题,请与我联系以获取密码以使其正常工作。反馈总是很感激!male
Freenode-Maleus
1 | MD5SUM (Tr0ll.rar): 318fe0b1c0dd4fa0a8dca43edace8b20 |
信息收集
上nmap
1 | root@kali:~# nmap -sV -p- -v 192.168.66.15 |
1 | root@kali:~# nmap -A -p 21,22,80 -v 192.168.66.15 --script=vuln -T4 |
通过枚举,得到了一些有趣的东西:
- 允许匿名FTP登录
- HTTP服务有2个有趣的页面:robots.txt和secret
允许匿名FTP
有一个文件lol.pcap,发现一些文本文件名secret_stuff.txt被推送到FTP服务器。该文件包含文本:
1 | 150 Here comes the directory listing. |
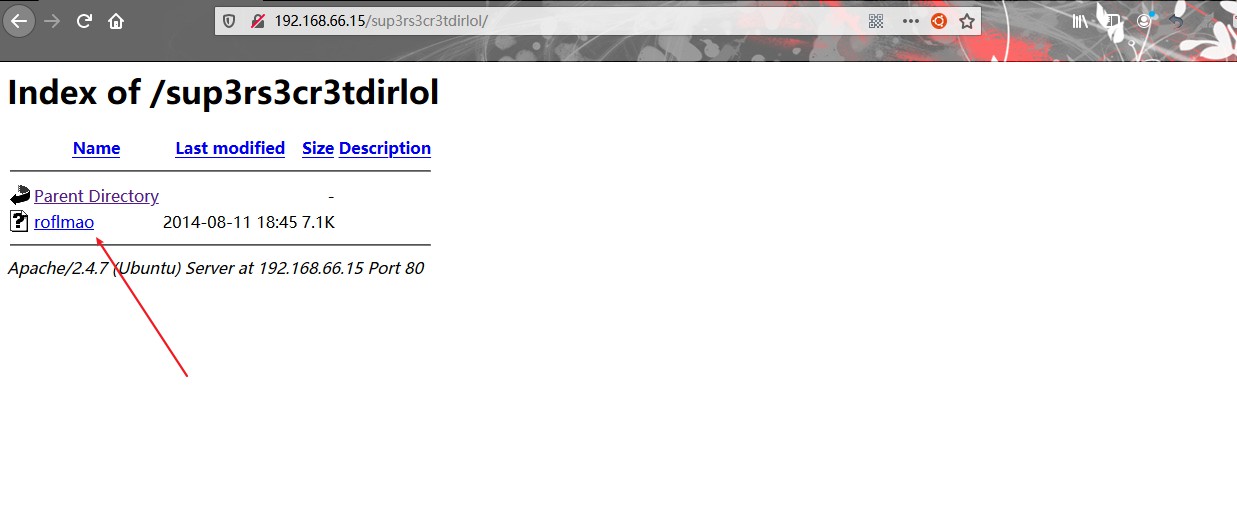
发现在具有该路径的Web服务器中没有什么有用的。回到从PCAP文件获得的文本文件中的消息。注意到sup3rs3cr3tdirlol一直是supersecretdirlol的代名词,然后检查了它是否可以是HTTP服务的URL路径。发现/sup3rs3cr3tdirlol/存在并且包含一个文件。
检查一下文件类型,发现是一个二进制文件。尝试执行它。
1 | root@kali:~/vulnhub/troll# file roflmao |
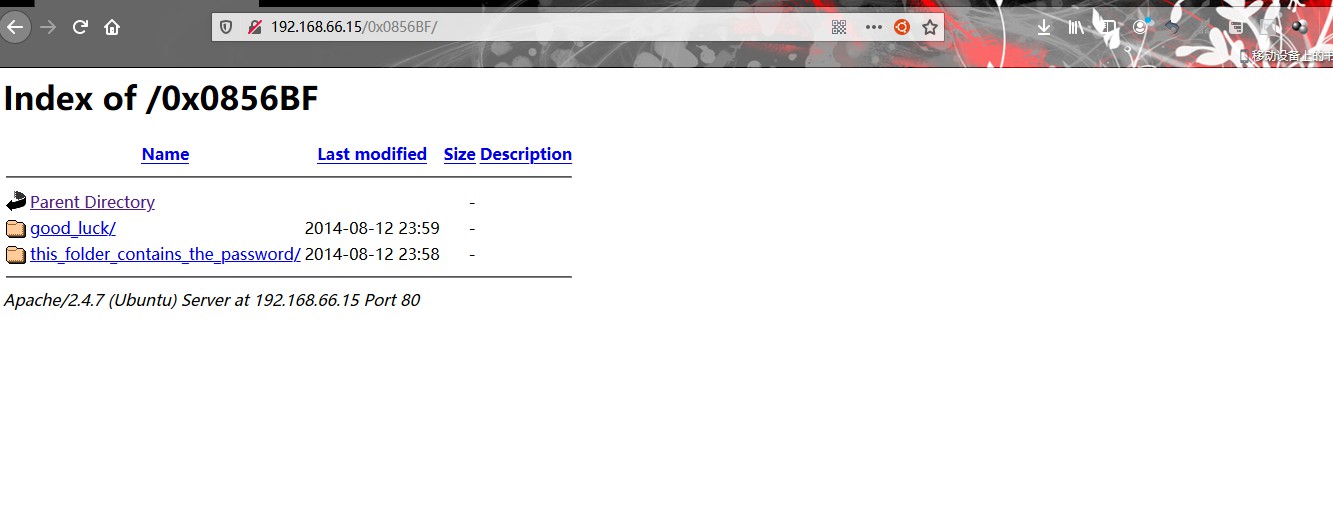
不用逆向二进制文件,因为当二进制文件运行时,没有内存地址0x0856BF。所以尝试再次使用0x0856BF作为HTTP服务中的URL路径。
1 | root@kali:~/vulnhub/troll# ./roflmao |
发现2个web目录
/0x0856BF/good_luck/目录
which_one_lol.txt
包含以下的字段
1 | maleus |
/0x0856BF/this_folder_contains_the_password/目录
Pass.txt
包含以下的字段
1 | Good_job_:) |
利用
这些文件可能是2个用户或密码。首先,将第一个文件用作用户列表,将第二个文件用作密码。
使用hydra爆破
1 | root@kali:~/vulnhub/troll# hydra -s 22 -v -V -L users -P pass -e n -t 1 -w 30 192.168.66.15 ssh |
问题始于用户blawrg,如果hydra无法登录,则主机将阻止Kali的IP。必须更改Kali的IP,然后才能开始尝试新用户。爆破完成,但是没有用户可以登录。
注意到包含Pass.txt的目录是this_folder_contains_the_password。这可能意味着某些情况,因此再次尝试使用Pass.txt作为密码,但溢出后可以使用密码WTH!登录。
1 | [RE-ATTEMPT] target 192.168.66.15 - login "vis1t0r" - pass "" - 16 of 20 [child 2] (0/0) |
成功登录
1 | root@kali:~# ssh overflow@192.168.66.15 |
提权
登录后,尝试找到该flag,但找不到。由于overflow是低权限用户,因此必须提权并找到root flag,然后再访问更多目录。
- 已经检查crontabs,并且没有文件可写。
- tmp目录为空
我开始在var/中检查world可写文件。没有有趣的文件,但是只有一个。
1 | $ l_path=var/*/*;while [ "$l_path" != / -a "$l_path" != . ]; do ls -ld $l_path; l_path=$(dirname -- "$l_path");done; |
检查var/log/cronlog
1 | $ cat var/log/cronlog |
这是cron job,每2分钟运行一次。如果可以修改cleaner.py并让系统做点什么,那么就可以升级overflow的权限。但是首先,必须找到cleaner.py。
1 | $ find / -name cleaner.py 2>/dev/null | grep "cleaner.py" |
查看cleaner.py
1 | $ cat /lib/log/cleaner.py |
找到了python文件,它是可写的。
- 修改cleaner.py
通过向帐户溢出添加sudo su 权限来修改了cleaner.py。当执行bash命令sudo su时,会得到root shell。
1 | overflow@troll:/$ cat /lib/log/cleaner.py |
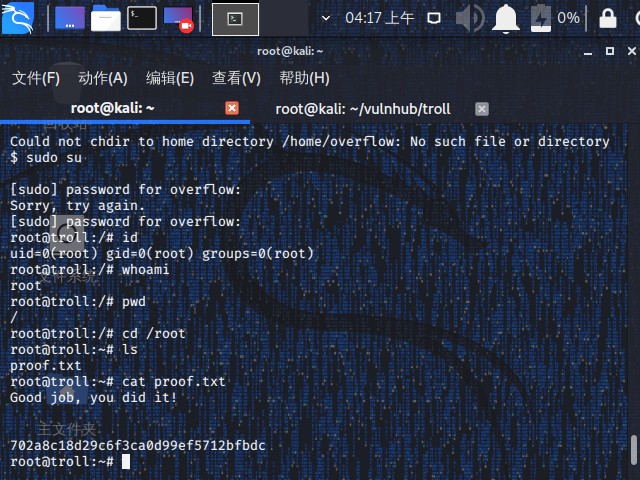
等待2分钟…。靶机将我踢了出去,再次登录并可升级为root。
1 | $ sudo su |
提权2
linux 内核提权
参考Linux-Kernel-3.13.0-3.19-Ubuntu-12.04/14.04/14.10/15.04-‘overlayfs’-Local-Privilege-Escalation
- CVE : CVE-2015-1328
1 | /* |
过程太简单在这里就不多写文演示了
知识点总结
- ftp匿名登录
- hydra爆破ssh密码
- cron job + world writeable py脚本提权
- CVE-2015-1328 linux内核提权
Game over
不好意思,这次还是没有找到希腊某位大佬的傻瓜式一键通关脚本,i am so sorry about this…It’s a pity…

The end,to be continue…