PWN-LINUX技巧总结
LINUX PWN 技巧总结
这是目前使用的方法,用于在Linux操作系统上进行二进制攻击。
- 它被写得像小抄一样,这样既简洁又不会太长。
- 该方法正在用于手工pwn exploit编写开发,没有像AFL等工具的描述。
- 会不时更新这篇文章,添加新的注释。
0. Find suid targets:
1 | find / -perm -u=s -type f 2>/dev/null |
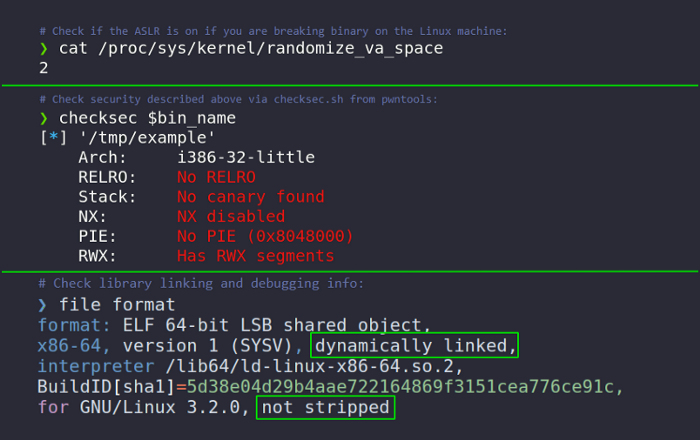
1. Basic binary security checks and some bypasses:
a) ASLR — Partial Overwrite / Info Disclosure / Brute Force
b) DEP — mprotect() / re2libc() / ROP / Egghunter
c) RELRO — GOT overwrite / .fini_array overwrite / .dtors overwrite
d) PIE — Address leak / NOP Slide
e) Stack Canaries — Brute Force / Heap Overflows / Arbitrary Write
f) Architecture — OS 32/64 ?
g) Library linking — Dynamically / statically linked ?
h) Debugging info — Stripped / not stripped ?
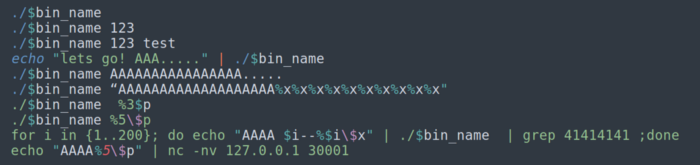
2. Run the binary with:
a) no arguments
b) one argument
c) two and more arguments
d) data on stdin
e) buffer overflow string
f) format string
g) format string in a loop
h) remote format string or buffer overflow
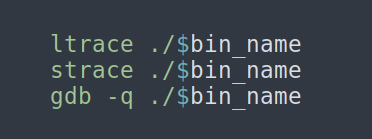
3. Run the binary with:
a) ltrace — library call tracer
b) strace — system calls and signals tracer
c) gdb — The GNU Project Debugger
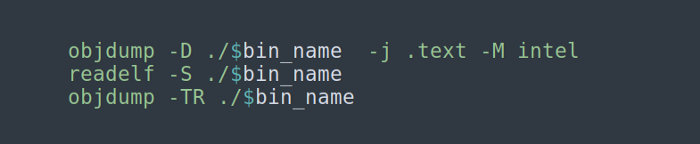
4. Decompile & disassembly of the binary:
a) using IDA / Ghidra / Hopper / Binary Ninja
b) disassembly text section
c) check sections
d) check functions addresses
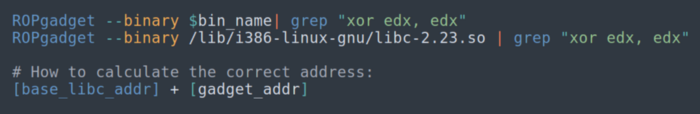
5. Check available ROP gadgets in:
a) the binary itself
b) linked libraries (libc database)
6. TIPS & TRICKS:
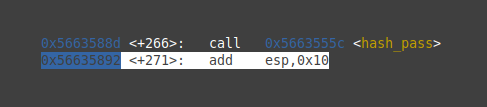
a) Set breakpoint @ instruction after possible vuln():
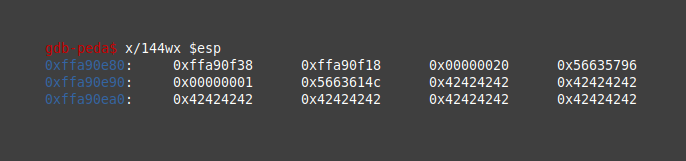
b) Then check how the stack looks like:
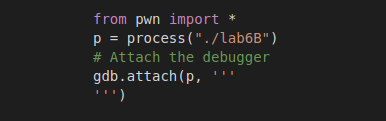
c) You can check it also using pwntools with attached gdb:
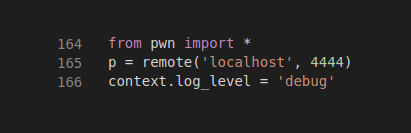
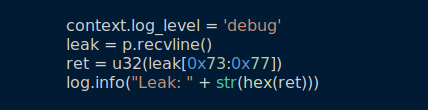
d) Try with debug level using pwntools:
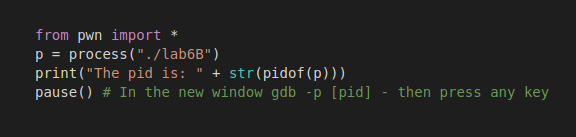
e) Sometimes child process could be easier to exploit — f.e. to get a non-null base code segment:
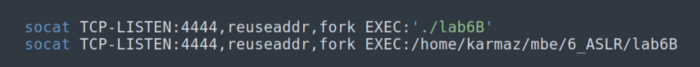
f) If you want to serve the binary using socat:
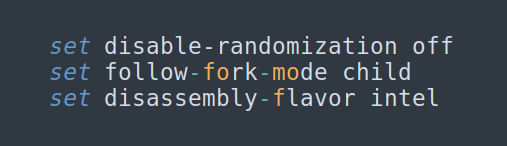
g) Turn ASLR / follow forks / set intel flavor in GDB
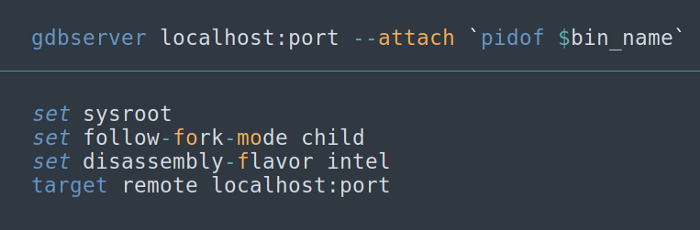
h) Run gdbserver to pwn binary remotely:
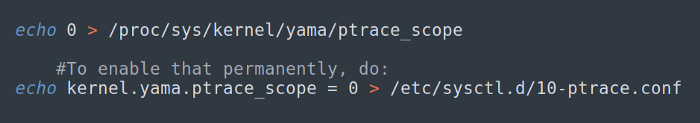
i) “Ptrace operation not permitted”? Sure:
j) Debugging in pwntools:
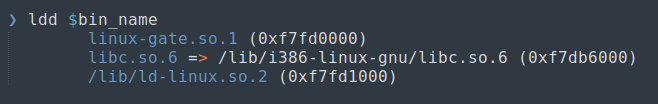
h) Print shared object dependencies:
j) Some basic “instant-win” vulnerable functions:
- strncpy
- gets
- strcpy
- malloc / free
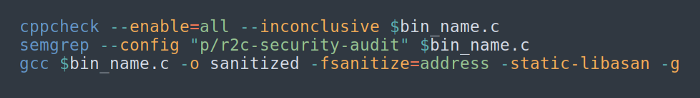
7. Static code analysis tools (for C):
a) cppcheck
b) semgrep
c) gcc
这就是目前的情况, 随着时间的推移,将尝试在本文中添加新的note,很快将使用上面描述的方法和技巧,开始一系列针对各种challenge和machine的攻略。希望你在这里能学到一些东西!
摘自(致敬原作)……
- 浏览medium.com博客每月有次数限制,并且5$收费,故摘录文章。。。
- PWN methodology - LINUX